by Ryan Flores, Stephen Hilt, and Akira Urano – Trend Micro Research
The world population is expected to reach 9.8 billion in 2050, according to a study published in 2017 by the United Nations Department of Economic and Social Affairs. The same study also shows that regions across the globe had a recent rise in life expectancy. To provide for this steadily growing and longer–living population, the amount of food that is being produced today needs to be roughly doubled by 2050, preferably without converting any more land into farmland. This puts a considerable burden on the food production industry to produce more food more efficiently but with less environmental impact. To meet expectations, farmers, growers, producers, and food processers are using high-tech tools and systems to optimize production conditions, reduce waste, and make efficient use of available resources.
However, the adoption of new technology also brings challenges. There has been a growing concern that the devices and software used in food and agriculture pose significant risks to both enterprises and customers. In 2015, the U.S. Department of Homeland Security already identified cybersecurity as a key issue in this sector, and outlined a plan for reducing sector-specific risks. These concerns continue to grow, and considering the potential fallout — from food safety issues that could affect the lives of consumers to crop and livestock sabotage that could ruin an enterprise — it is undeniable that cybersecurity needs to be a bigger priority for people and organizations involved in the food production industry.
The Role of the IoT in the Food Production Industry
The food production industry is already using the internet of things (IoT) to help make production more efficient. As a prime example, farms and other such sites are often remotely located and crops are grown far from where a farmer operates, just as fish pens can be in the middle of the sea, miles offshore. Remote monitoring devices with wireless mobile connectivity removes the physical need for visiting and supervising sites.
Food production involves not only the growing and production of food items, but also storage, processing, waste management, and other tasks. The IoT is also used in most of these activities: Connected devices and systems can help manage large tracts of land, track and feed large herds of animals, maintain specific storage environments, and more. As base technologies used in the IoT (e.g., sensors, boards, antennas, and batteries) become cheaper, and cellular data connectivity becomes ubiquitous in rural and agricultural areas, we foresee wider adoption of the IoT in this industry in the near future.
The IoT can be used in food production in a variety of ways:
- Precision agriculture. Precision agriculture is a method of farm management that takes into consideration the inter- and intra-field variability of both soil and crop. Sensors collect soil and crop data, and then various automated systems analyze the information and supply the appropriate amount of water or fertilizer to the crops. Farming machines with auto-steering capability, such as driverless tractors, use real-time kinematic (RTK) positioning data and variable-rate technology to apply the optimal amount of fertilizers, pesticide, and irrigation to a particular position.
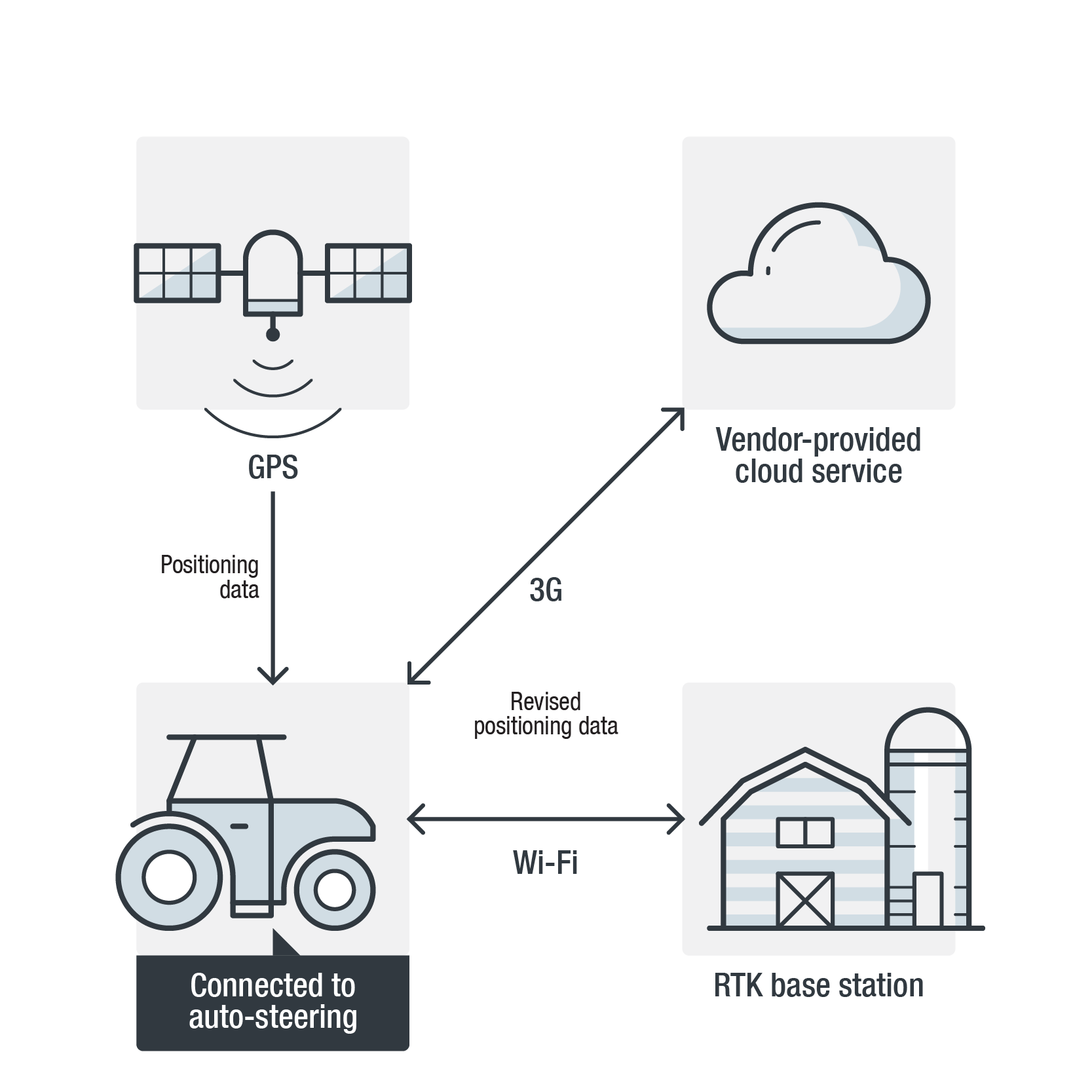
Figure 1. Overview of a driverless tractor setup - Aquaculture. Aquaculture is the farming of aquatic organisms such as fish, shrimp, shellfish, and seaweed. A 2013 study published by the Agriculture and Environmental Services Department of the World Bank projects that aquaculture will supply over 60 percent of fish for human consumption by 2030. This means that seafood production will be mainly dependent on “human-controlled” aquaculture in a few years’ time. In general, there are two types of aquaculture: open systems, which are commonly found in open seas, and closed systems, which can be seen in ponds or water tanks. For both types, technology is needed to monitor and maintain water quality, turbidity, temperature, salinity, water current, pH, and dissolved oxygen.
- Livestock. Livestock is the breeding and growing of animals for consumption. The IoT helps in maintaining suitable environmental conditions and in monitoring animals’ health conditions. Automated tracking, weighing, and feeding systems enable growers to track animals with minimal human intervention.
- Storage. Harvested produce needs to be stored (sometimes for months) in farms or a depot facility while waiting for distribution and consumption. The IoT helps in monitoring and maintaining temperature and humidity in storage silos in order to prevent spoilage and contamination.
- Waste treatment. In food and agriculture, a lot of waste may be contaminated by fertilizer chemicals or organic matter in animal waste, crop residue, or irrigation water. This needs to be disposed of, processed, or recycled into something productive. One of the most common ways of reusing waste is to turn it into biogas, which can then power farms, facilities, or small communities.
- Food processing. After harvesting or slaughter, food needs to be cleaned, processed, and prepared for storage, cooking, or consumption. Consequently, many food processing machines are used, such as cutting machines, fryers, ovens, and smokers. Some of these pieces of equipment are fully automated and would only need to be monitored by the operator for errors or issues in food processing.
- Food safety. Food and agriculture organizations have to manage the enforcement of proper food production, including handling, processing, and preparation. There are also the different regulations that enterprises need to comply with. To help, some system vendors offer dedicated systems to support the requirements for good agricultural practice (GAP) and hazard analysis critical control points (HACCP) and to reduce manual documentation. Compromised records, whether arising from unintentional disclosure or as a result of a cyberattack, can affect the integrity of data, which in turn can be integral to public health and safety concerns.
Cybersecurity Risks and the Impact of an Attack
Agriculture started in specific environments where farming was possible. But with the help of technology, people were able to expand optimal growing environments into regions where it was not previously feasible. The same is true for different forms of livestock. But as an unfortunate consequence, attackers who wish to sabotage the food production process can simply alter the environmental conditions to destroy crops or even kill livestock. In February 2015, for instance, US$1.7 million worth of chickens were killed when a disgruntled contract grower tampered with the temperature settings of the chicken houses in a farm in South Carolina, U.S.A. And in July 2018, 1,200 pigs died in an automated pig barn in the Netherlands when a temperature alert was ignored.
The use of the IoT in food production is undeniably beneficial, but there are critical cybersecurity issues that cannot be overlooked. Since IoT-related threats are relatively new to this industry, many people and organizations are not prepared for or even aware of the industry-specific risks:
Exposed internet-connected systems
IoT systems in food production are used to control and maintain the parameters of a growing environment within very narrow thresholds. A small deviation from the threshold — as can be caused by a cyberattack — can have a catastrophic impact on the system itself and wide-ranging effects on the livestock or agricultural areas maintained by the system.
In our research, we used Shodan data to survey vulnerable systems online. We found that there were a number of exposed systems within the food production industry (see Tables 1 and 2). Such systems are connected to the internet through virtual network computing (VNC), using the default port and without password authentication. In effect, anyone on the internet can connect to these systems and manipulate them remotely.
| Category | Number of unique IP addresses |
| Aquaculture (water management) | 107 |
| Storage | 22 |
| Feeding | 14 |
| Biogas plant | 14 |
| Food processing | 7 |
| ISOBUS tractor | 4 |
| Biomass plant | 3 |
| Cannabis farm | 3 |
| GPS base station for tractor | 2 |
| Brewery | 2 |
| Irrigation management | 2 |
| Silo management | 2 |
| Ventilation control for poultry | 2 |
| Waste treatment | 1 |
| Weather monitoring | 1 |
| Refrigeration system | 1 |
| Farm management | 1 |
| Aquaculture (oxygen generator) | 1 |
| Total | 189 |
Table 1. Exposed systems
| Country | Number of unique IP addresses |
| United States | 108 |
| Germany | 17 |
| Portugal | 10 |
| Thailand | 9 |
| Italy | 5 |
| India | 4 |
| Argentina | 3 |
| Australia | 3 |
| Brazil | 3 |
| South Korea | 3 |
| New Zealand | 3 |
| Spain | 3 |
| France | 2 |
| Greece | 2 |
| Puerto Rico | 2 |
| Taiwan | 2 |
| Others | 10 |
Table 2. Breakdown of exposed systems by country
 Figure 2. ISOBUS tractor
Figure 2. ISOBUS tractor
 Figure 3. Silo management system
Figure 3. Silo management system
 Figure 4. Irrigation system
Figure 4. Irrigation system
Figure 5. Aquaculture system
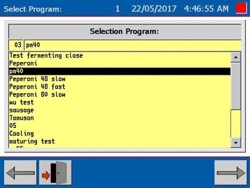 Figure 6. Food processing machine (for cooking sausages)
Figure 6. Food processing machine (for cooking sausages)
All of these exposed systems allow anyone to connect and read the data without authentication. However, there are some systems that require a username and password if any of the parameters or set points are modified or if any commands are issued. Having this type of additional authentication for any modification at least gives a small amount of security to prevent tampering and unauthorized modification.
Apart from VNC, we also found some exposed web user interfaces that are connected to food and agriculture systems (see Figures 7 and 8). In some cases, as in the VNC examples, the control panels are accessible without password authentication. But even if a username and password are required to gain access to the system, it is possible to compromise the system using existing exploit codes from publicly available sources.
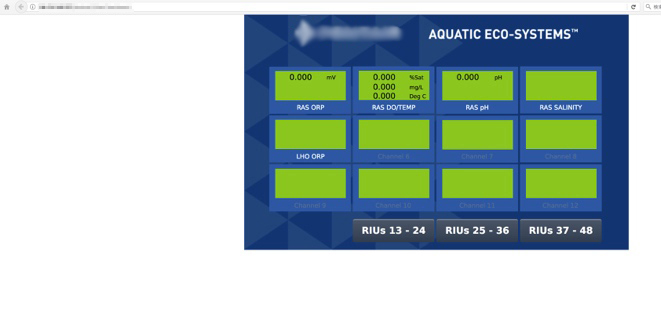 Figure 7. Web-accessible control panel for an aquaculture system
Figure 7. Web-accessible control panel for an aquaculture system
(in addition to VNC remote access to the same system) Figure 8. Wireless router connected to farming devices
Figure 8. Wireless router connected to farming devices
Exposed internet-connected systems
Exposed records for food safety compliance
Some vendors provide automated recording of activities on food production systems in order to comply with regulations and guidelines, and they can generate documents to submit to food regulation authorities or customs agencies if needed. The information comes from daily input by producers or by automated feed from devices and sensors into databases or cloud services. Any falsification of data in these systems, erroneous data from sensors, or data compromise due to a cyber incident affects the integrity of the documents and makes it unsuitable for proper audit and tracing. Tracing in particular is important in case of food safety issues where authorities need to identify a specific cause. Any modification of information makes the investigation more difficult and corrupts food safety processes.
Given the sensitive nature of this information, it is a risk for any of these systems to be unsecured. However, we also found exposed HACCP systems online. For example, the specification sheet for a piece of software used to store HACCP data (see Figure 9) indicates not only internet connectivity, but also the use of a remote access tool. This means that users of such systems are likely to connect them to the internet (primarily for receiving online support from the vendors), which opens up another avenue for attackers to access the systems remotely.
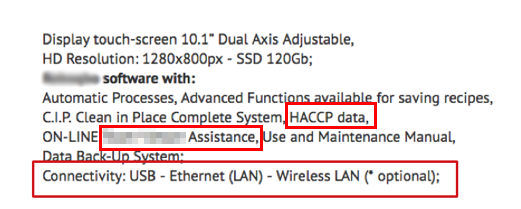 Figure 9. Sample specification sheet showing features related to HACCP and internet connectivity
Figure 9. Sample specification sheet showing features related to HACCP and internet connectivity
Exposed records for food safety compliance
Unsecured RTK base stations
As previously mentioned, precision agriculture uses advanced positioning technologies, commonly RTK on top of global navigation satellite system (GNSS) in order to get the millimeter-level accuracy achieved by having a fixed base station for triangulation. This requires receivers to be placed out in the field, and since some data-dependent services might be needed, these devices normally have internet connectivity through cellular service. Most of the time, the devices can be remotely managed through an embedded web server. Using a web interface, the farmer or operator can configure the base station or receiver, download logs, and perform routine maintenance.
This setup also means that positioning receivers are accessible via the internet. In fact, our quick Shodan search for receivers from a popular navigation system vendor (performed on Sept. 12, 2018) identified 92 such receivers.
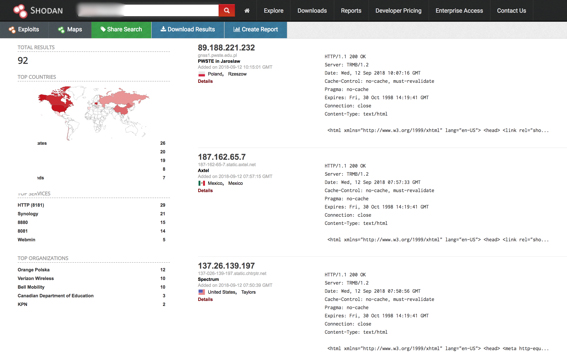 Figure 10. Exposed base stations using receivers from a popular navigation system vendor
Figure 10. Exposed base stations using receivers from a popular navigation system vendor
Further investigation revealed that 10 percent of the identified receivers do not have any authentication, meaning anyone who knows the receivers’ IP addresses can read and modify their data and settings. Also, independent research has verified that majority of these devices have default credentials.
Unsecured RTK base stations
Online farm management platforms
As the various phases of food production become increasingly digitized and interconnected, the need arises for a central management platform for viewing, managing, and controlling data. Major vendors offer platforms for managing the various aspects of farm management and operation. These platforms allow the farmer-operator to perform various tasks, such as drawing field maps and defining field borders; creating, deploying, and syncing farm jobs; performing real-time inventory of equipment use and status; managing crop seeding, growth, and harvest inventory; and viewing crop and yield history.
All of this data is valuable to individual farmer-operators. It is therefore vital for them to keep their farm management accounts secure. While we have not seen any phishing attacks aimed at these platforms (yet), the potential impact of a compromised administrator account is devastating. Not only would the attacker have access to critical data, but he would also be able to tamper with equipment or even sabotage a whole planting season.
Online farm management platforms
Other security risks
Unintended consequences on downstream systems
Any vertical in the food production industry consists of many players. In farming, there must be water, electricity, waste water treatment, seed, fertilizer, and equipment vendors. If any of these roles is compromised, then the whole supply chain and ecosystem are at risk.
Unpatched common operating systems and applications
Many displays and controls on farming and food production equipment are just small computers or tablets running off-the-shelf operating systems (OSs) such as the Microsoft® Windows® and Android™ platforms. Any security vulnerability discovered on the base OS will consequently affect devices running the same OS.
Other security risks
Solutions and Recommendations
We have identified the security risks farmers and operators should be aware of, and highlighted the possible impact of a cyberattack against IoT systems used in the food production industry. At the very least, a successful attack could result in monetary losses, and at worst, it could compromise the food safety of an entire population.
To address the pressing need for tougher cybersecurity in food production, we lay out these recommendations for producers and vendors in this industry:
For farmers, growers, producers, and food processers
- Securing remote access. Remote access and remote monitoring are perhaps the number one reason that the IoT is being adopted in various areas of food production. Thus, the equipment used to connect to the internet needs to be secured. Most equipment used to connect to the internet involves a modem with a cellular data connection. Due diligence should be taken in determining the make and model of the modem, and checking for default credentials and changing them.
The protocol used for remote access and monitoring needs to be secured as well. For web access, the connection used should be via secure HTTP (https) if supported. For common protocols used to remotely access an IoT device or system, unique usernames and strong passwords should be set up for authentication. Also, it should be confirmed with vendors whether there is any maintenance account built in on the device or system. Some vendors have software installed with default credentials for remote support should the owner or operator need assistance. These accounts can be avenues for remote access and their existence should be clarified with the vendors. - Being cautious of phishing. Knowledge of how social engineering works is imperative. Social engineering emails, particularly those with seemingly innocuous but actually malicious links or attachments, must be quickly spotted, reported, and discarded. Also, the browser address bar should always be checked to ensure that the site being accessed is from a legitimate domain.
- Patching. Since most IoT vendors in the food production industry are not yet mature in their software development cycle, there is a possibility that a patch may not be created even if a vulnerability is discovered. Patch deployment may also be challenging for farmers and operators as the devices that need patching may need physical access out in the field. However, patching is still a vital process in securing systems and should be part of the security practice if and when patches are made available by vendors.
- Installing security software on endpoints. Since IoT adoption in food production consists mostly of single-purpose or low-power devices, integrating security software into them is not a viable option. The endpoints used to connect to those devices (e.g., desktops, laptops, tablets, and mobile phones), however, are more feature-rich and can be infected by malware or can simply display phishing emails or sites. Security software should be installed on these endpoints to lower the risk of account compromise and unauthorized access.
- Choosing vendors and products with security in mind. Preference should be accorded to vendors that implement secure coding practices, have security built into their products, and have regular patch and deployment cycles.
- Reviewing OEMs. Vendors should review original equipment manufacturers (OEMs) and work with their partners on implementing best security practices, securing development life cycles, and exploring patch deployment options.
- Implementing patch cycles. As the demand to push products and become first to market dwindles, the demand to maintain and secure deployed devices will soon follow. IoT vendors should think of ways to develop and deploy critical security patches when needed, and to also build the patching mechanism into the newer products that they will ship.
- Hardening IoT device security. A lot of the current security issues with IoT devices may be attributed to poor configurations or just the absence of security. Simple security-hardening measures such as requiring users to configure new usernames and passwords during setup will go a long way. The same is true for remote access credentials. Also, applications installed by default should be checked for existing vulnerabilities and should have secure configurations when shipped.
- Restricting read-and-write access. Not all forms of access and actions carry the same security risks. For example, being able to view the readings of a sensor has far less security consequence than being able to define or alter set points. It is recommended to have various account types in an IoT system and have at least two types of users: one user with access only and another with read-and-write access. A third user type can be created with the additional “admin” privileges of being able to modify device and system settings as well as manage user accounts.
The food production industry is becoming more and more dependent on the IoT as population growth, not to mention the recent rise in life expectancy, pushes for higher food demand. New technology is being integrated into many aspects of production, helping maximize efficiency and safety. In particular, the IoT is helping in the gathering and analysis of different forms of data, providing proprietary information and valuable insight to farmers, growers, producers, and food processers.
As the reliance on the IoT grows, people and organizations in the industry have to recognize that securing the technology afforded by the IoT should be of high priority. Ideally, considering the impact a cyberattack or an act of sabotage could have, securing IoT devices and systems in the food production industry should get the same level of attention as the protection of the physical spaces and assets in a tract of farmland.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One