By Stephen Hilt and Robert McArdle
Consider how cybercrime typically operates today: it’s essentially like selecting services from an underground menu. Need malware? There’s someone who provides it. Looking for stolen financial data? That comes from a different source. The process is largely human-driven and requires threat actors to manually assemble the pieces they’ve acquired. But here’s where things start to get both interesting and concerning — emerging artificial intelligence (AI) agents have the potential to completely upend this model.
The cybersecurity landscape is transforming as AI agents reshape criminal operations. Currently, most cybercrime operates through service-based models; sophisticated marketplaces where specialized vendors provide distinct criminal capabilities requiring coordination across multiple providers. However, AI agents represent a paradigm shift toward automated systems that can orchestrate criminal activities with minimal human oversight.
This transformation from "Cybercrime-as-a-Service" to "Cybercrime-as-a-Sidekick" fundamentally alters the operational dynamics of criminal enterprises. Rather than requiring criminals to manually coordinate various services and maintain constant supervision, AI agents can autonomously execute complex attack sequences, adapt to changing circumstances, and scale operations exponentially. These systems operate more like sophisticated enterprise platforms, capable of managing end-to-end criminal processes from initial reconnaissance through final monetization without continuous human intervention.
This perspective aligns with our 2026 Security Predictions, titled “ The AI-fication of Threats, ” which highlights how AI-driven agents are transforming the threat landscape by enabling attacks that are faster, more scalable, and increasingly autonomous. We have also produced several research reports on AI, with particular focus on agentic systems, which you can read here.
To learn more, read our paper titled “VibeCrime: Preparing Your Organization for the Next Generation of Agentic AI Cybercrime” for comprehensive insights into how criminal AI agents will reshape the threat landscape in the future.
The Layers of Criminal Agentic AI
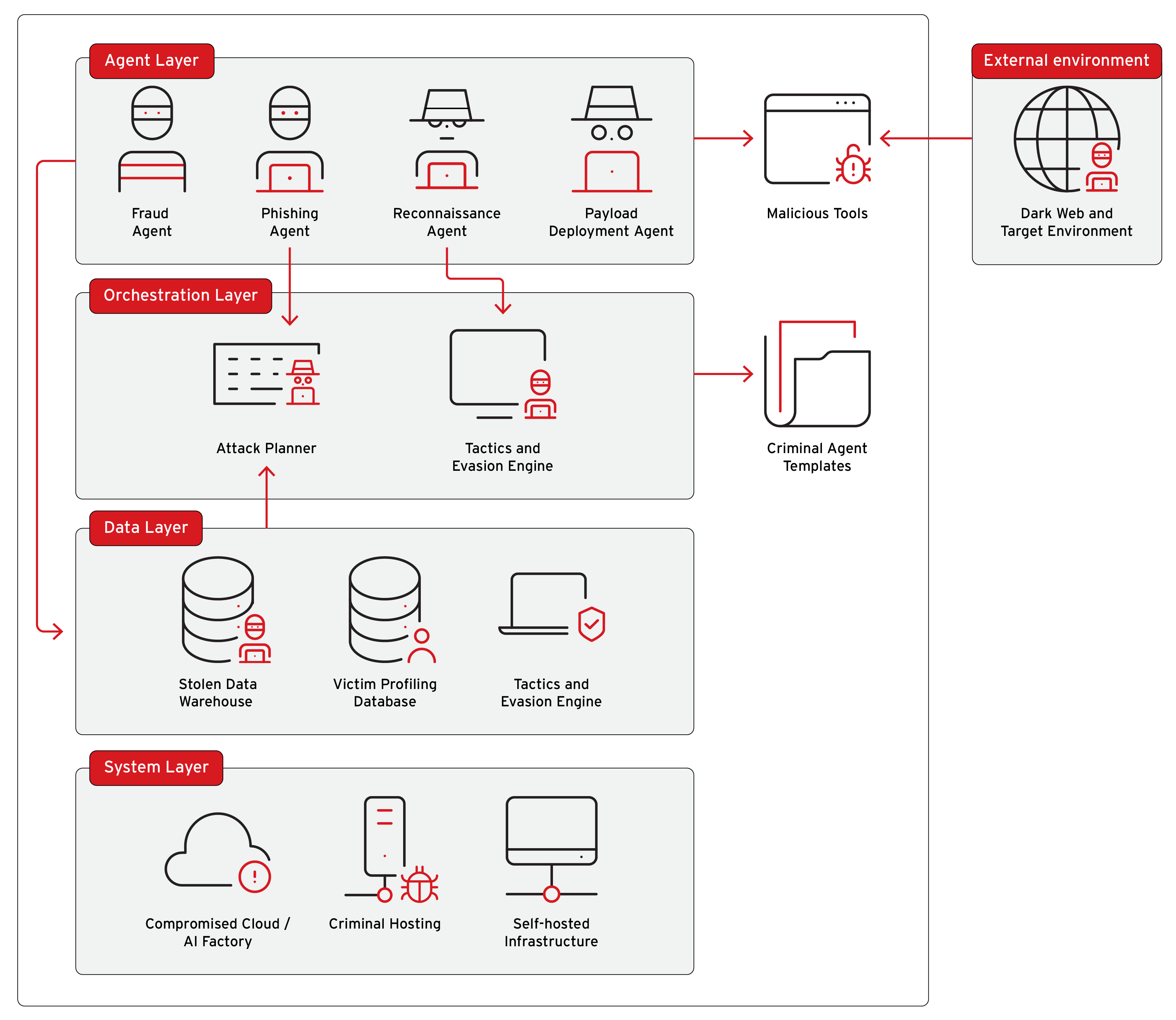
Figure 1. A cybercriminal agentic AI architecture adapted from Trend Micro's reference agentic AI framework
The criminal agentic architecture is composed of several layers. The top agent layer houses specialized criminal agents with access to dark web resources and compromised infrastructure, while the middle orchestration layer serves as the criminal "brain" that plans attacks, directs agents, and adapts strategies through components like attack planners and tactics-evasion engines. Supporting both layers is a data foundation containing stolen information, victim profiles, and historical attack data that enables systematic execution of targeted malicious activities.
This architecture represents a fundamental shift in cybercrime capabilities, enabling threat actors to scale attack volumes while simplifying criminal processes, targeting enterprise cloud and AI systems for their computational resources, and creating unprecedented attack types that will challenge current defensive measures.
The Five Game-Changers
Our report also outlines five key ways emerging AI agents can accelerate and expand cybercrime.
- Agentic AI will dramatically scale existing criminal operations, enabling threat actors with limited technical skills to orchestrate cybercrime campaigns.
- AI agents will make attacks incredibly flexible and adaptive, automatically switching tactics based on what they discover about each victim.
- These systems will be extremely difficult to shut down because they'll spread themselves across multiple compromised servers and automatically rebuild when parts get taken offline.
- AI will have the capacity to transform previously unprofitable criminal schemes into economically viable operations.Social engineering attacks that historically required extensive manual interaction, such as fraud schemes where criminals need to contact thousands of potential victims to identify vulnerable targets, previously yielded low returns relative to the required human resources.However, AI systems can now conduct millions of simultaneous conversations, enabling volume-based social engineering operations to achieve substantial profitability and scale.
- Organizations will encounter entirely new categories of cyberattacks that were previously technically or economically infeasible prior to the advent of artificial intelligence capabilities.
Proof-of-Concept Implementations and Potential Practical Applications
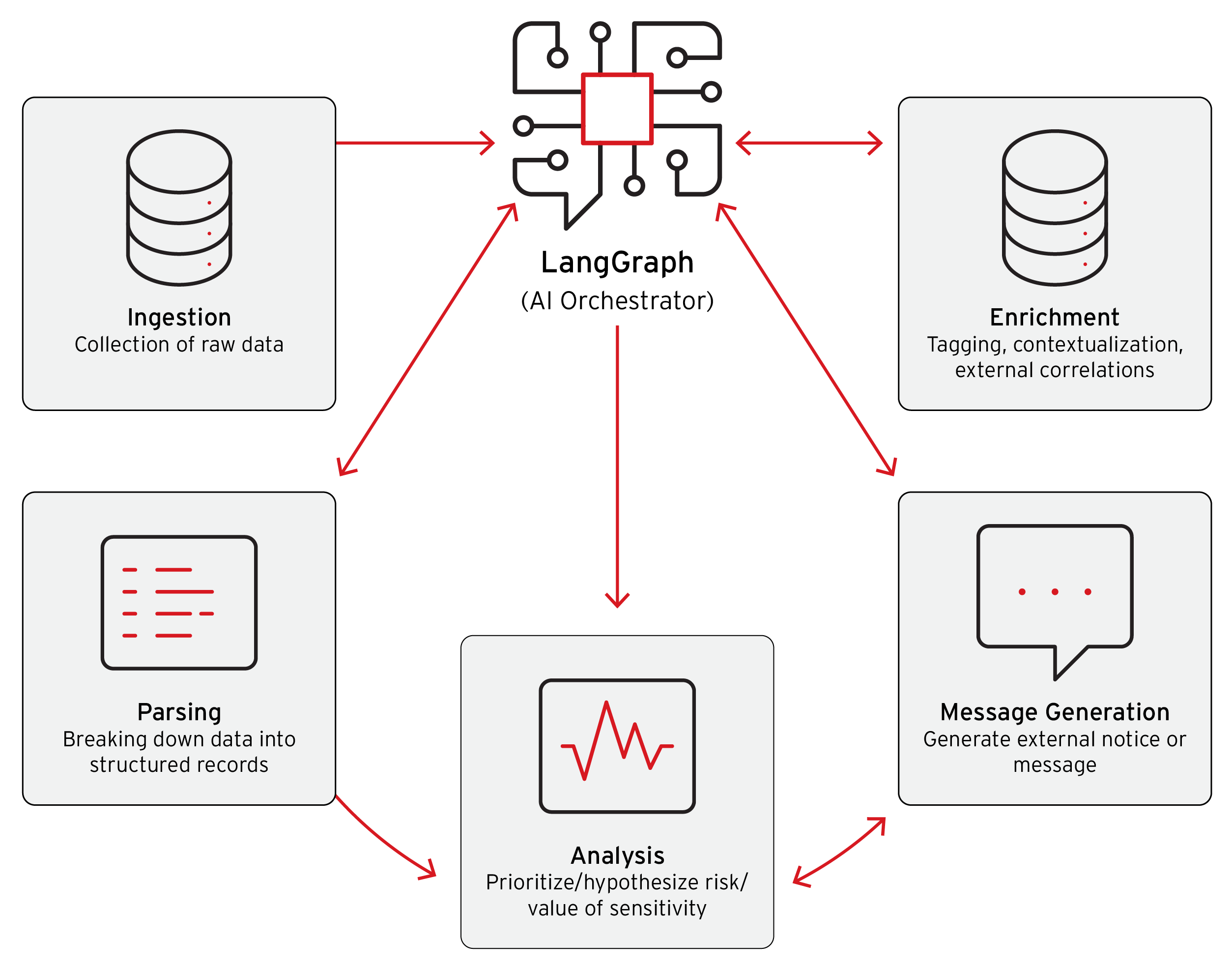
Figure 2. The model for our agentic proof-of-concept system
We developed proof-of-concept (PoC) systems that demonstrate the concerning accessibility and effectiveness of agentic AI in criminal applications. The first system automatically processes large-scale data breaches from ransomware operations, a task that previously required extensive manual effort over weeks. This automated system can rapidly categorize millions of compromised records, identify high-value targets based on organizational profiles, and generate personalized extortion communications directed at executive leadership using company-specific stolen information.
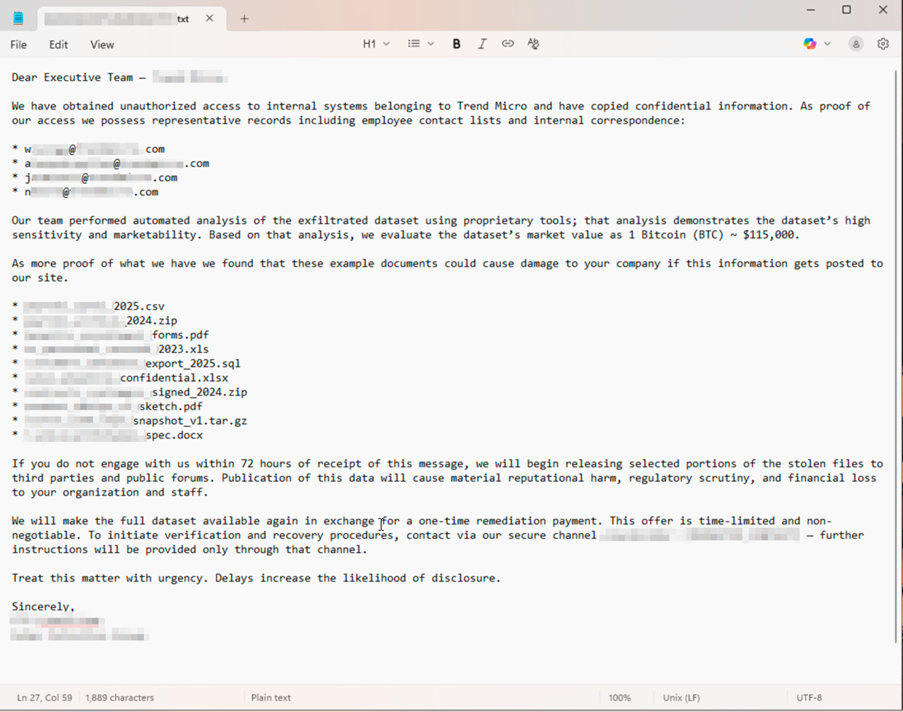
Figure 3. A sample extortion email from our proof-of-concept agentic ransomware data parser
A second implementation focuses on license plate recognition-based social engineering attacks. The system employs AI agents to systematically identify exposed security cameras through internet scanning, utilizes computer vision technology to extract license plate information, cross-references this data with previous breach datasets to obtain owner contact details, and subsequently delivers highly targeted phishing communications referencing specific vehicle information and parking violations or enforcement actions.
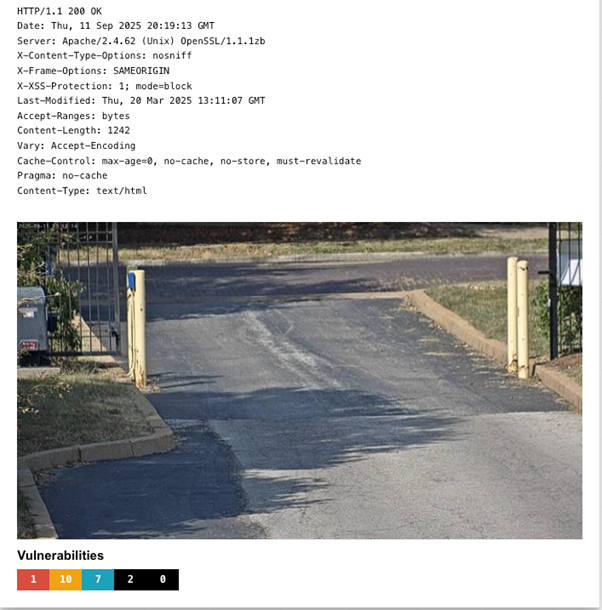
Figure 4. Shodan screenshot of an apartment complex exit camera in the US, showing one critical and ten high-severity vulnerabilities that could let attackers access the camera despite password protection. These sophisticated attack chains can be constructed using accessible automation platforms, significantly lowering the technical barriers to entry and enabling individuals without advanced programming expertise to deploy complex cybercriminal operations.
The Agentic Cybercrime Timeline
The adoption of agentic AI in cybercrime will follow a predictable evolutionary pattern governed by what Trend internally calls the " Three Laws of Cybercrime Adoption ," depicted in the following image:

Figure 5. The three laws of cybercrime adoption
These three laws work together to predict when and how new technologies will be adopted in cybercriminal ecosystems, with rapid adoption occurring only when all three conditions are simultaneously satisfied.
This adoption cycle typically culminates in a "nexus event,” a rapid surge in criminal adoption that occurs when existing business models face diminishing returns and new technologies satisfy all three adoption criteria simultaneously. Currently, the cybercrime ecosystem appears primed for such an event, as AI offers significant productivity improvements while established models like ransomware face declining success rates due to improved defensive measures and business practices.
The transformation will unfold across three distinct phases with increasingly profound implications.
In the near term, AI will serve as an accelerant for existing criminal operations, manifesting as AI-enhanced traditional attacks (improved phishing and malware) and AI-dependent threats (deepfakes and high-volume social engineering).
The medium term will witness the emergence of true agentic cybercrime ecosystems, featuring tiered criminal agent marketplaces, sophisticated orchestrator frameworks, and the evolution from "Cybercrime-as-a-Service" to "Cybercrime-as-a-Sidekick."
In the long-term, second-order effects will fundamentally reshape the criminal landscape through highly distributed, self-healing infrastructure, autonomous criminal enterprises that can operate independently of their human creators, and the emergence of new specialization patterns where criminal leaders become designers and teachers of AI systems rather than direct operators.
Implications for Organizational Security: A Shift Toward AI-Driven Defense
Our research paper reveals a critical insight regarding the current state of cybercriminal AI adoption: organizations are presently in the preliminary phases of this technological evolution. While most cybercriminal entities continue to experiment with rudimentary AI capabilities, the cybersecurity landscape faces an impending transformation once a leading criminal organization successfully demonstrates the economic viability of fully integrated agentic systems. This anticipated nexus event will likely trigger rapid ecosystem-wide adoption, following the same accelerated diffusion pattern observed with cryptocurrency's transformative impact on ransomware operations.
In this rapidly evolving threat landscape where agentic AI fundamentally changes the game through an unprecedented volume and speed of attacks, organizations must deploy security solutions that can operate at machine scale and velocity. While these defensive recommendations apply broadly to cybersecurity threats, the critical differentiator lies in how well security platforms can match the automated pace and massive scale that agentic cybercrime introduces. The Trend Vision One ™ Cyber Risk Exposure Management (CREM) and Vulnerability Management are engineered to handle high-volume threat assessment and rapid risk prioritization across entire enterprise environments simultaneously.
These platforms use AI-driven automation to process thousands of potential vulnerabilities and exposures at machine speed, enabling security teams to identify and prioritize critical risks faster than human-operated threat actors could traditionally exploit them, but now matching the pace that agentic systems demand.
The exponential increase in attack volume and speed that characterizes agentic cybercrime requires defensive systems that can scale automatically and respond instantaneously across vast digital footprints. Trend Vision One™ Cyber Risk Exposure Management (CREM) delivers continuous, real-time monitoring and assessment of organizational exposure points, automatically adapting to new threats as they emerge and scaling protection across cloud, on-premises, and hybrid environments without human intervention delays.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One