The Linux Threat Landscape Report
Linux is prevalent in many computing environments, including personal computers, servers, mobile devices (via Android), embedded systems, and particularly in cloud environments. According to web technology survey provider W3Techs’ usage statistics for operating systems and web servers, Linux is the foundational operating system for over 81% of websites measured. As of 2021, it was estimated that around 90% of public cloud workloads ran on Linux. In terms of web servers, Linux also dominated with a significant market share as many popular web servers’ software, such as Apache and Nginx, run on Linux. Amazon Web Services (AWS) hosts large numbers of Linux-based systems. Due to the high demand for cloud infrastructure services, Google Cloud and Microsoft Azure also offer Linux-based virtual machines.
According to the Linux Foundation’s Linux Kernel History Report (published in 2020), the Linux kernel is now finding its application in products that require safety and security. This includes various devices, from medical equipment to autonomous vehicles and spacecraft. The annual increase of Linux contributors (comprised of individual and organizational programmers who work on the kernel) and commits (sets of changes made to a Linux-based project by an author) highlight the development process and impact of the continuous improvement of the processes in and by the community, with the report clocking an average of over 10 commits per hour.
These numbers not only solidify the dependability and continued expansion of the operating system’s use, the application of the infrastructure also emphasizes the need to establish the appropriate security and safety levels to fend off critical threats and attacks.
With its widespread adoption across personal computing, enterprise servers, and cloud infrastructures, Linux is an increasingly attractive target for malware, exploits, and social engineering, among others. To help organizations and guide their respective security teams, we analyzed the trends, techniques, patterns, and data relevant to the abuse of the operating system last year. We dissect the different sections and vectors of Linux that were commonly abused by cybercriminals and attackers.
Myth: “Isn’t Linux Immune to Malware?”
Contrary to the belief that Linux is immune to malware, several types, such as ransomware, cryptocurrency miners, web shells, and rootkits have been used to target Linux systems. We break down the malware types and their commonly exploited vulnerabilities:
- Ransomware: While less common than its Windows counterparts, Linux ransomware is not unheard of. From the first quarter of 2022 to 2023, our Midyear Security Report cited that our sensors detected a 62% increase in Linux ransomware attack attempts. One such example is the KillDisk ransomware that targeted financial institutions. Ransomware often exploits vulnerabilities related to outdated software, poor system configurations, or phishing attacks. Regular software updates, careful email handling, and robust backup strategies are critical defenses against ransomware attacks.
- Cryptocurrency miners: Cryptominers commonly exploit the same vulnerabilities as ransomware, exploiting misconfigurations and gaps in cloud environments due to the availability of vast resources. A recent example of attacks involved a malicious XMRig cryptocurrency miner that abused gaps found in public-facing Linux-based applications, as well as incorporating a competition-killing capability and CHAOS remote access trojan (RAT) as part of its arsenal, among other tools.
- Web shells: These malicious scripts installed on a server provide a powerful interface to control the server and network. After successfully exploiting web application vulnerabilities like SQL injection, file inclusion, or command injection flaws, these scripts are often abused as part of the arsenal. For instance, threat actors have used the China Chopper web shell for years to maintain access and control over compromised Linux servers.
- Rootkits: These stealthy malware typically require kernel-level access to function, so they often exploit vulnerabilities that allow privilege escalation. Once installed, a rootkit can manipulate system calls and logs to cloak its activity, making detection and removal difficult.
Commonly exploited vulnerabilities across these malware types usually fall into a few categories:
- Unpatched software: Keeping software and systems up to date is crucial, as many infections and attacks exploit known vulnerabilities in outdated software.
- Misconfigurations: Poorly configured systems and applications provide easy entry points for malware. For example, systems left with default credentials or open, unsecured ports can be prime targets for entry and abuse.
- Unsecure code: Web shells, in particular, often exploit unsecure coding practices in web applications.
- Phishing and social engineering: These techniques deceive users into installing malware or revealing credentials.
While Linux has a reputation for having a robust security system, it's far from invincible. Awareness and proactive management are vital to maintaining a secure Linux environment. Regular patching, secure configurations, secure coding practices, user education, and deployment of security solutions can contribute to a strong defense against Linux malware.
What Malware Types Targeted Linux Systems?
Here are the foremost malware types that targeted Linux systems in 2022 according to Trend SPN:
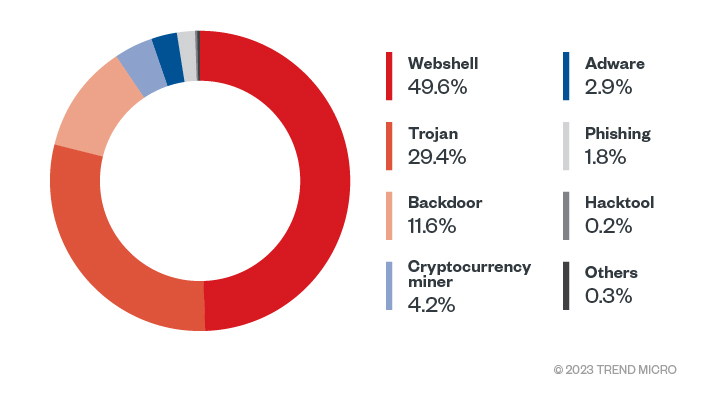
Figure 1. Top malware types that targeted Linux OS in 2022 (Data taken from Trend SPN)
We noted the high prevalence of web shells, with the most detected families being:
- Backdoor.PHP.WEBSHELL.SMMR
- Backdoor.ASP.WEBSHELL.GIFJMB
- Backdoor.Python.WEBSHELL.AC
- Backdoor.PHP.CHOPPER.PIQGIV (also known as China Chopper)
Given that China Chopper is a dated web shell, it is interesting to see a fair volume of detection. While we observed fewer detections in cryptocurrency miners for the year, we saw the highest detections for Coinminer.Linux.MALXMR.SMDSL64 as the prevalent miner family.
Though we saw a slight decline in ransomware incidents in 2022, it remains a prevalent threat for organizations. Despite being a dated malware accompanying other types of threats, Nemucod emerged as a prevalent tool accompanying various ransomware families in the past year. A trojan known for downloading files that could potentially harm the computer it infects, our telemetry analyses linked Nemucod to downloading other malware such as equally dated ransomware variant Teslacrypt.
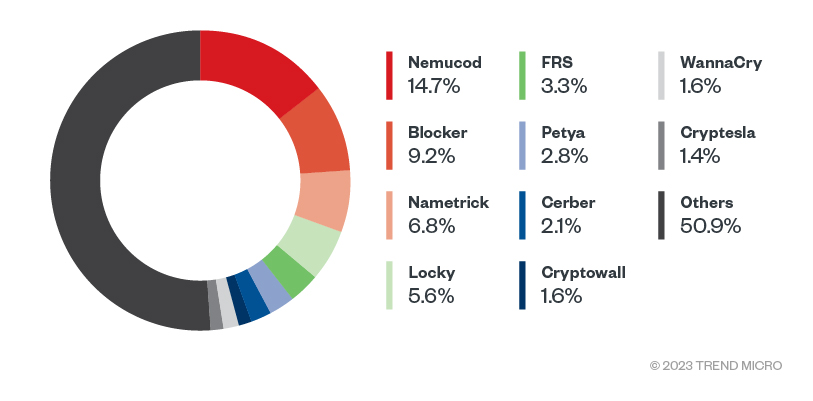
Figure 2. Top 10 ransomware families targeting Linux OS in 2022 (Data taken from Trend SPN)
Noting the high numbers of these dated ransomware families and tools, we believe this is due to cybercriminals’ automation of these old ransomware tools and families, as well as the presence of previously abused security gaps that remain unpatched to date. Much like the possible reasons for the inclusion of dated vulnerabilities among the ranking gaps in 2022 (discussed in the next section), we recommend that businesses implement patches and fixes especially for legacy systems.
Another noteworthy ransomware worth mentioning is IceFire ransomware, detected in 2022 and documented to target Linux-powered enterprise networks. In early 2023, IceFire reportedly abused the IBM Aspera Faspex file-sharing software vulnerability CVE-2022-47986 for remote code execution (RCE).
Though Clop ransomware is not on the top 10 list, it is worth noting that the ransomware gang recently gained attention for targeting organizations by exploiting the MOVEit Transfer zero-day vulnerability (CVE-2023-34362). And despite the momentary decrease in activity due to the arrests of the gang members in Ukraine in 2022, the group’s overall number of deployments went unabated. Three other noteworthy ransomware families that made news headlines for their respective attacks in 2022 to the early months of 2023 were ransomware families Conti, Akira, and Abyss Locker. These ransomware families’ deployment activities and changing techniques targeting Linux systems show how quickly threat actors can pivot and weaponize security openings to make a profit.
Moreover, we note that some Windows- and Android-based malware families also made the top list, which means that Linux servers are acting as a storage or command-and-control (C&C) server for Windows and Android malware. In recent months, we observed advanced persistent threat (APT) groups abuse BPF (Berkeley Packet Filter) filters for the installation of backdoors due to the improved use of BPF and its nature of its abuse being harder to detect. This type of component abuse presents a novel challenge to security teams as the inclusion of BPF bytecode in malware samples poses significant obstacles in detection, blocking, and analysis.
From the perspective of defending against malware threats and attacks, we also observed organizations now opt for the red team exercises focused on learning and working with tools now available to improve their in-house cyber security posture (compared to completely relying on security solutions). Tools and training platforms such as KnowBe4 and Atomic Red allow companies to keep up with the constantly evolving threat landscape and are now becoming a more mainstream consideration as part of in-house security trainings.
Top Vulnerabilities
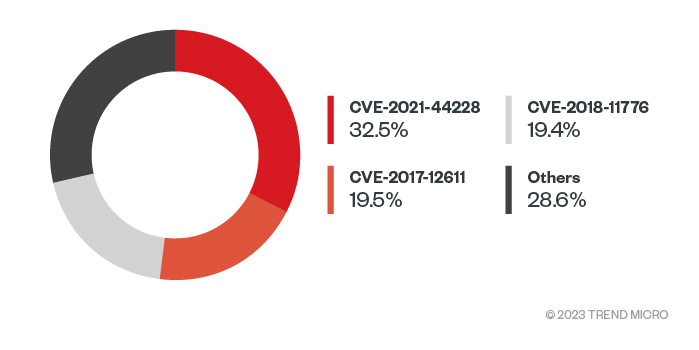
Figure 3. Top three most exploited vulnerabilities in 2022 (Data taken from Trend Cloud One)
Analyzing our telemetry for the most abused vulnerabilities in the wild, the most prominent Common Vulnerabilities and Exposures (CVEs) that we observed listed the following security gaps exploited for threats and attacks:
- CVE-2021-44228, also known as the Apache Log4j vulnerability, has a severity score of 10 in the Common Vulnerability Scoring System (CVSS)
- CVE-2017-12611 and CVE-2018-11776, both Apache Struts vulnerabilities
- CVE-2022-26134, a zero-day vulnerability in Atlassian Confluence server and data center with a critical rating of 9.8
- CVE-2018-15473, an OpenSSH vulnerability that affects all Linux and Unix platforms
Specific applications on Linux platforms have become prime targets for malicious actors as these applications have vulnerabilities that make them susceptible to various types of attacks. Based on our collected data, WordPress emerged as the most frequently targeted application. Additionally, a significant rise in the exploitation of zero-day vulnerabilities, specifically CVE-2021-44228, CVE-2021-45046, and CVE-2021-45105 in Apache Log4j, have captured the attention of attackers. We also saw a rise in the exploitation of Zoho Manage Engine and Magento.
We also noted some old security gaps (CVE-2013-4671, CVE-2013-4670, and CVE-2013-1617) making it to the top 10 of most exploited vulnerabilities in the last year. Aside from the possibility of computers and/or legacy systems still being in use and remaining unpatched, the inclusion of these old vulnerabilities can be the result of automated attacks and vulnerability scanners’ activity still catching and attempting to break through.
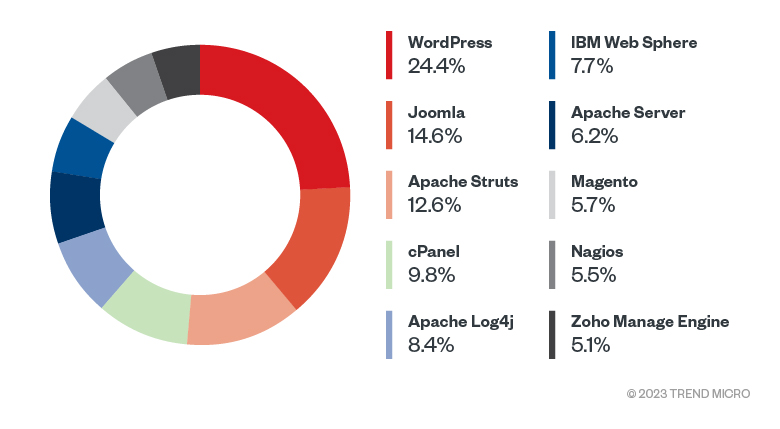
Figure 4. Top 10 most targeted applications in 2022 (Data taken from Trend Cloud One)
Based on this telemetry, there could be several reasons why WordPress, Joomla, and Apache Struts have been the most targeted applications in the past year, among other possible factors for their respective vulnerabilities:
- Use of outdated core software
- Use of outdated plugins or themes
- Use of weak credentials
- Delay in the path cycle
Other applications like Apache Log4j and Zoho Manage Engine also attracted threat actors' attention. Vulnerabilities found in open-source libraries create a wider threat landscape as they are used in multiple products, and the Apache Log4j vulnerability dubbed Log4Shell, is an example of such a case.
Web-Based vs. Non-Web-Based Attacks
Linux attacks are dominated by web-based attacks, in contrast to Windows. Web attacks, such as SQL injection, cross-site scripting (XSS), server-side request forgeries (SSRF), and other security compromises, are aimed at web resources. Conversely, non-HTTP attacks focus on specific application protocols like FTP (File Transfer Protocol), DNS (Domain Name System), SSH (Secure Shell Protocol), SMB (Server Message Block), or SMTP (Simple Mail Transfer Protocol).
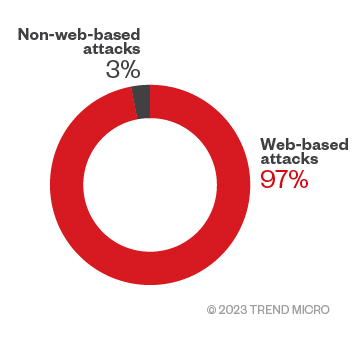
Figure 5. Comparison of web-based and non-web-based attack distribution in 2022 (Data taken from Trend SPN)
Of all the attempts detected by our sensors, most of the network traffic attacks we logged were web-based, and only a small number belonged to other protocols. A large chunk of hits were for OWASP-categorized techniques, followed by triggers for attacks like brute force attacks. We also observed specific vulnerabilities being exploited in large numbers.
Attacks Leveraging Protocol Anomalies
We also observed HTTP traffic that violated the HTTP protocol specification. HTTP protocol event anomalies can manifest as unusual HTTP requests or response patterns, non-standard headers, invalid encoding, or very large requests. Threat actors can exploit these anomalies for various purposes, including:
- Exploiting vulnerabilities
- Conducting denial-of-service (DoS) attacks
- Evading detection and obfuscating activities
- Performing reconnaissance and gathering information
- Carrying out protocol-level attacks
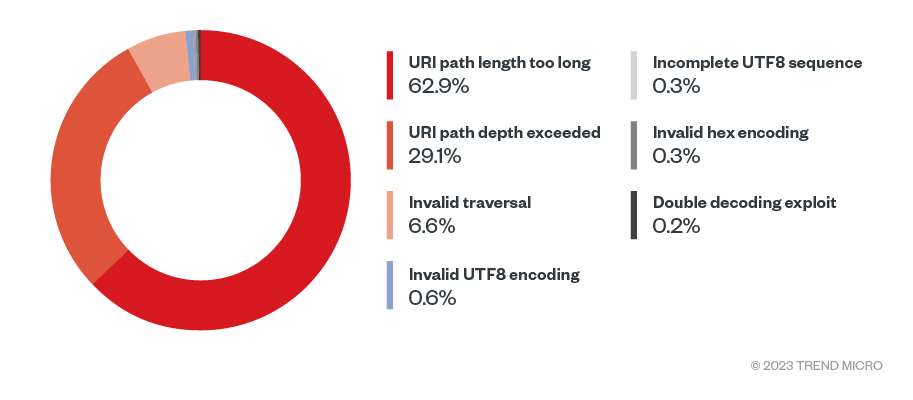
Figure 6. Unique HTTP protocol event anomalies that ranked in 2022 (Data taken from Trend SPN)
The event anomaly “URI path length too long” stands out, likely made through malicious activities by intentionally sending requests with excessively long URI paths. Attackers might attempt to exhaust server resources, trigger server-side vulnerabilities, or cause DoS conditions. Similarly, an attacker can use anomalies like “Invalid UTF8 encoding,” “Incomplete UTF8 sequence,” “Invalid hex encoding,” and “Double decoding exploit” to bypass validation logic implemented in web applications. By taking advantage of these anomalies, attackers can manipulate or deceive the validation mechanisms, and potentially gain unauthorized access or execute malicious actions. Another use of these techniques is to evade security mechanisms such as web application firewalls or Intrusion Prevention Systems (IPS).
OWASP Top 10
Open Worldwide Application Security Project (formerly Open Web Application Security Project) or OWASP listed their Top 10 most critical apps and threats, and we identified the listed risks and threats for 2022 identifying with our telemetry related to the OWASP Top 10 2021 list.
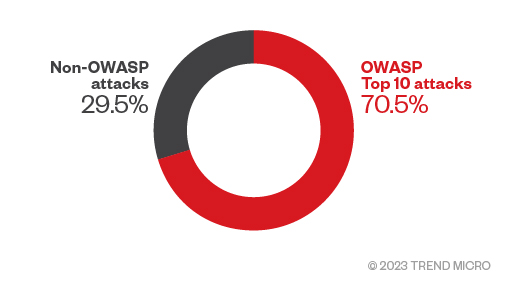
Figure 7. The percentage of OWASP Top 10 attacks and non-OWASP attacks in 2022 (Data taken from Trend SPN)
Web threats are not only restricted to the OWASP category; our sensors also show that some non-OWASP security risks are also prevalent. With OWASP-listed attacks, although injections (A03—Injection) have dropped to third place in OWASP’s Top 10 due to the native and transparent implementation of protections (in the frameworks or new languages), our sensors track it as the most exploited category of web application vulnerabilities. This category encompasses different injection vulnerabilities such as:
- SQL injection
- Command injection
- Object Relational Mapping (ORM)
- LDAP
- Expression language (EL) or Object Graph Navigation Library (OGNL) injections
- Cross-site scripting (XSS)
We further break this down to determine that cross-site scripting is the highest contributor to security risks, with WordPress and Grafana contributing the most to this category, followed by observed increases in SQL injection, directory traversal, and command injection. For insecure deserialization, we found PHP framework Laravel, FasterXML JSON library, Ruby on Rails, and Oracle WebLogic Server as the top targeted applications for this security risk.
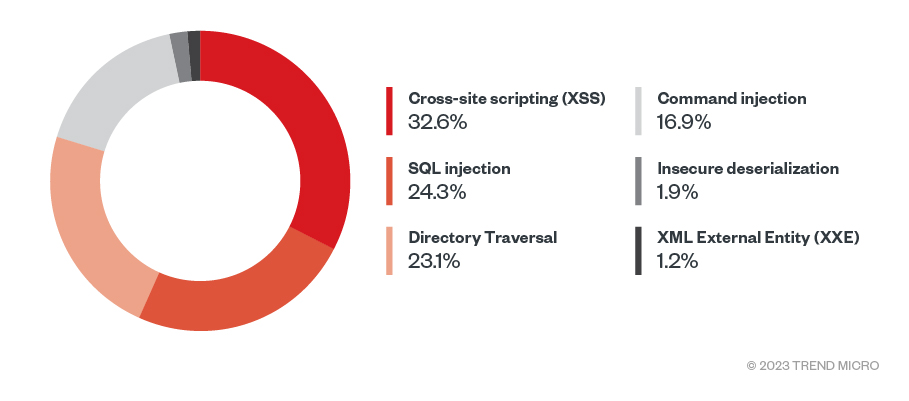
Figure 8. Top OWASP security risks in 2022 (Data taken from Trend Cloud One)
This is followed by Broken Access Control (A01), which — in OWASP’s list — jumped from fifth to first place. This is due to the increase in cloud computing and API usage and because this type of vulnerability is hard to detect with automated tools. While cloud computing and API use have been steadily increasing over time, we note the potential space for analysts to ask why this risk caught illicit activity interest to warrant the far leap from fifth to first, or at which point the cybercriminal business models in place were suddenly deemed to have sufficient return on investment. Adding to the burden for detection tools and mechanisms are the varied ways by which applications can be created and deployed, the lack of standard, and the requirements for manual testing.
In third place of top OWASP security risks is based on unsecure designs (A08 – Software and Data Integrity Failures), a newly identified risk category emphasizing design flaw-related risks. Despite the ongoing conversations in the community about DevSecOps and shifting left, developers and security teams should team up in prioritizing the secure design patterns and its integrity for reducing vulnerabilities in the structure. This new category underscores the need to design applications with security at the forefront.
The OWASP framework focuses on identifying and addressing the vulnerabilities specific to web applications such as SQL injection, XSS, insecure direct object references, and more. The remaining detected threats fall into the non-OWASP category, representing a diverse range of security risks such as:
- Brute-force attacks
- Denial of service (DoS)
- Remote code execution (RCE)
- Distributed denial of service (DDoS)
Here is a further breakdown of the top OWASP and non-OWASP security risks:
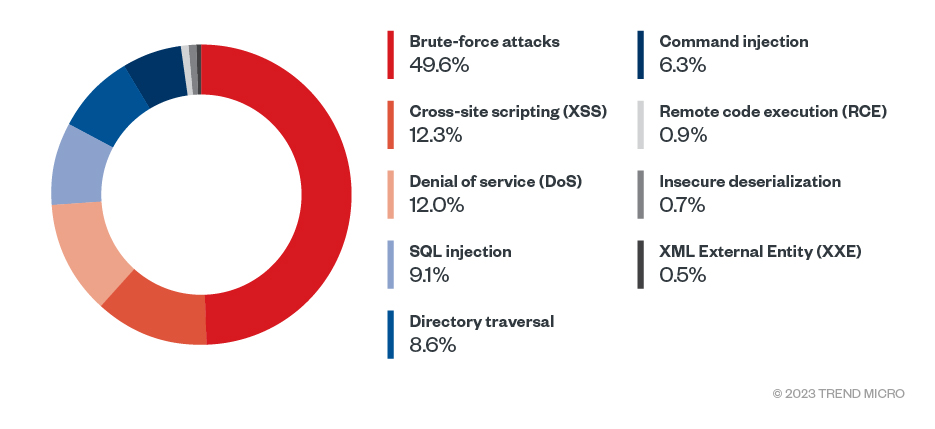
Figure 9. Comparison of the top specific OWASP and non-OWASP threats in 2022 (Data taken from Trend Cloud One)
Brute-force attacks are highly prevalent, surpassing any other OWASP Top 10 security risk in frequency. Given the nature of brute-force attacks, the sheer volume of these events is significant. In addition, DoS and RCE are other security threats in the non-OWASP category.
Linux systems usually only require a shell console; administrators and users do not open a browser to actively work on these servers. A server would contact malicious sites only when it is infected. Compared to the volume of observed events in Windows systems, we observed far fewer events for web reputation events from Linux systems.
Despite the smaller numbers, we still see a difference in the detection and protection reputation services provide as some of the events directly indicate the presence of a breach, communication to a command and control (C&C) center, or contact with suspicious or unexpected services.
Malicious actors leverage compromised systems to download tools and malware, aiming to infect other systems within the environment. To mitigate these risks, Trend Micro products equipped with Web Reputation Services (WRS) plays a crucial role in carefully scrutinizing URLs to prevent users and systems from accessing potentially dangerous websites. Here is the categorical detection of malicious URLs on Linux platforms:
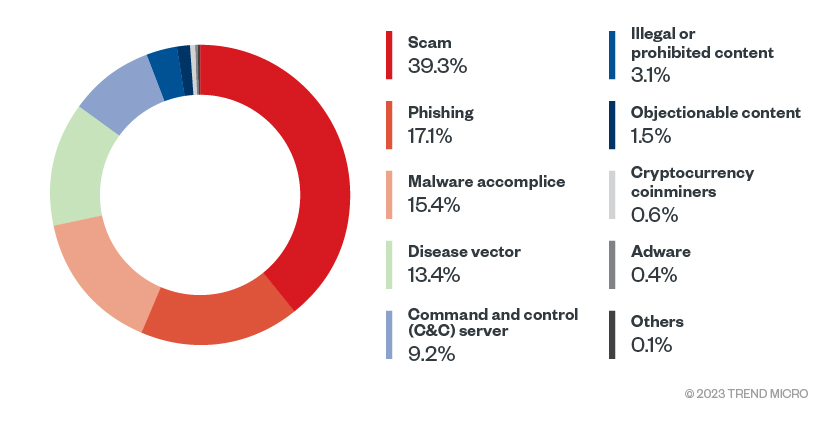
Figure 10. Distribution of threat type detection targeting Linux systems (Data taken from Trend WRS. Find Trend WRS’ filtering categories
for a reference on the classification of threats.)
Our sensors’ data provides insights into the distribution of diverse threat categories such as phishing, scams (defined by attempts to defraud a person or group after gaining their confidence and/or trust), command and control (C&C) servers, malware accomplices (sites used by malicious programs for distribution, including hosting upgrades or storage of stolen information), and disease vectors (URLs that serve as entry points for the distribution of malware, viruses, or other harmful software).
We observed a few noteworthy threats from this telemetry data such as:
- A few threat attackers were reusing expired legitimate domain names, like “tracker[.]web-cockpit[.]jp,” to launch web skimming attacks and bypass the detections.
- The WRS telemetry data also showed that threat actors were using look-alike domains to lure the users. This deception that leads users to download malware can also be used for phishing and social engineering techniques. Below is a list of a few look-alike domains used for scamming and phishing purposes:
- github[.]trendmicr[.]com
- googe[.]com
- yotube[.]com
- ww17[.]yuotube[.]com
- zippo-amazon[.]com[:]80
- We also observed threat actors were actively using out-of-band application security testing (OAST) tools like interact.sh or Portswigger to identify the vulnerable applications. We observed the OAST domains in our telemetry data below:
- oast[.]pro
- oast[.]site
- oast[.]online
- oast[.]fun
- oast[.]me
We also observed threat actors using GitHub to deploy cryptocurrency miners such as github[.]com[:]443/xmrig/xmrig/releases/download/v6.17.0/xmrig-6.17.0-msvc-win64.zip.
Containers have revolutionized the software industry, offering a lightweight, flexible, and scalable way to package and deploy applications. Docker and its Linux-based containers have become a staple in DevOps, powering everything from microservice architectures to cloud-native applications.
However, with the growing adoption of containers comes an urgent need to understand and mitigate their security implications. Containers are built from images that bundle an application and its dependencies. Docker's public registry DockerHub hosts millions of these images, including official and community-contributed versions.
The most popular official images on DockerHub often include base operating systems like Ubuntu, Alpine, and CentOS, and typical application environments like Node.js, Python, and MySQL. While the convenience and standardization of these images are undeniable, they are not without security risks. A common issue is including unnecessary tools or libraries in an image, which can increase the attack surface. For example, an image might consist of compilers, debugging tools, or documentation files not required for the application to function. These extra components make the container larger and provide potential entry vectors for attacks.
Another significant concern is the continued use of outdated or vulnerable software. Given the rapid pace of software updates and vulnerability disclosures, an image can quickly become obsolete and expose users to security risks. Studies have shown that many images on DockerHub contain known vulnerabilities, often because they are based on outdated base images. After scanning the top 20 most downloaded official images from DockerHub, here is a summary of the top 10 most vulnerable images in use to date:
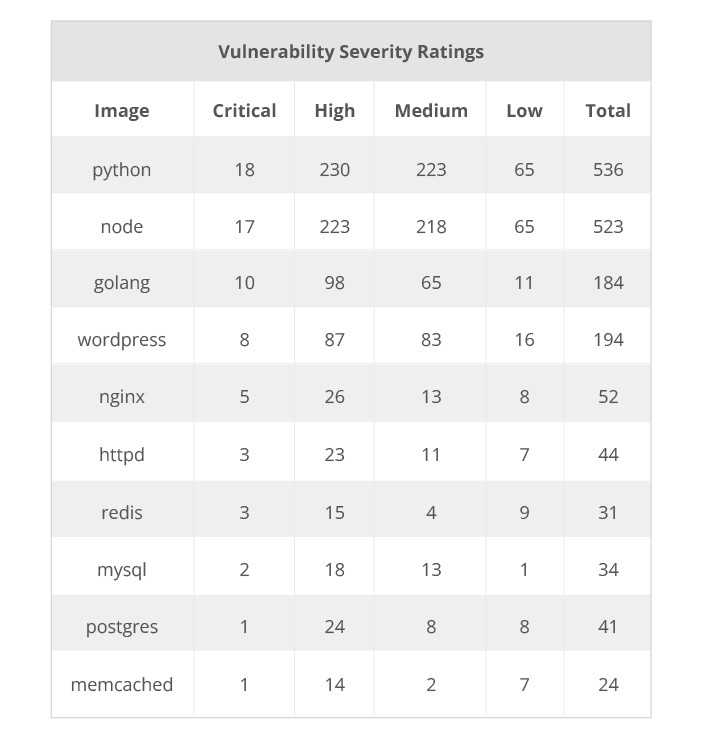
Table 1. The 10 most vulnerable official images from DockerHub
As we can see from the table above, the most popular official images from DockerHub have at least one critical vulnerability, and even more highly rated gaps with Python, Node, and Golang images as having the most number of openings, respectively. This is still very similar to our analysis from 2021, prompting insights that there have been little movement or changes since then.
There are several best practices for maintaining container security to defend against threats that might abuse these vulnerable images:
- Use minimal base images. Reduce the attack surface by using a minimal base image that only includes what is necessary to run applications.
- Regularly update images. Regularly update images to include the latest security patches. This practice is particularly crucial for images based on dynamic distributions like Ubuntu where packages are frequently updated.
- Scan images for vulnerabilities. Tools like Docker's own Docker Scout, or open-source projects like Clair and Grype can scan Docker images for known vulnerabilities. Integrate these tools into the continuous integration/continuous deployment (CI/CD) pipeline to catch security issues before they reach production.
- Implement the principle of least privilege. Docker containers run with root privileges by default, meaning a process that escapes the container could have root access on the host machine. Wherever possible, containers should run as non-root users and with only the necessary capabilities.
- Use Linux security modules. Use Linux security modules like AppArmor, SELinux, and seccomp, which provide mandatory access control to confine what a container can do.
While containers and the popular official images from DockerHub have made it easier to deploy applications, they also carry significant security considerations. However, in understanding these risks and implementing best practices, you can take full advantage of the power and convenience of containers while maintaining a secure environment.
Linux allows organizations to maximize their utilization of cloud environments and drive their digital transformation initiatives. Given the system’s widespread use and popularity, understanding its threats is even more crucial to secure systems properly, particularly against pervasive threats and attacks. More researchers and analysts are encouraged to look into the security posture of Linux as adoption is expected to increase in the coming months, and to explore the potential positive and negative effects of its integration with AI-powered systems.
The information and practical attack instances highlighted in this report aim to provide a sound understanding of the risks surrounding Linux systems. Organizations must prioritize the security of Linux workloads, considering its deep integration into everyday computing, notably as a crucial component of cloud infrastructures and the ever-growing different internet of things (IoT) to deploy new applications and services.
Organizations and individual developers must consistently adhere to security best practices. These include adopting a “security by design” methodology, implementing layered virtual patching or vulnerability shielding, practicing the principle of least privilege, and adherence with the shared responsibility model.
Customers of Trend Vision One™ are protected from the threats targeting Linux systems, servers, cloud infrastructure, endpoints, and deployments as it supports diverse hybrid IT environments, automates and orchestrates workflows, and delivers expert cybersecurity services. Security teams can simplify and converge organizations’ security operations to manage the growing attack surface, eliminate gaps to reinforce existing solutions, consolidate and integrate operations across enterprise systems, and harness threat intelligence with critical insights.
For the growing number of attacks specifically aimed at the increasing Linux-based cloud migration, adoption, and integration, enterprises can benefit from multilayered security solutions such as Trend Cloud One™, a security services platform for cloud builders. It provides automated protection for cloud migration, cloud-native application development, and cloud operational excellence. Trend Cloud One™ breaks down silos to secure business-critical applications, which includes:
- Cloud One - Workload Security: runtime protection for workloads
- Cloud One - Container Security: automated container image and registry scanning
- Cloud One - File Storage Security: security for cloud file and object storage services
- Cloud One - Network Security: cloud network layer IPS security
- Cloud One - Application Security: security for serverless functions, APIs, and applications
- Cloud One - Conformity: real-time security for cloud infrastructure — secure, optimize, and comply
- Cloud One - Open Source Security: visibility and monitoring of open-source vulnerabilities and license risks
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One