Best Practices: Ransomware
 No business or user is too big or too small for ransomware. In 2016, it cost victims over US$1 billion in losses. As far as impact is concerned, look no further than the WannaCry and Petya outbreaks that affected thousands. Affected hospitals had to turn away patients or shut down their emergency wards. Car manufacturing plants had to stop production, and power grids were disrupted.
No business or user is too big or too small for ransomware. In 2016, it cost victims over US$1 billion in losses. As far as impact is concerned, look no further than the WannaCry and Petya outbreaks that affected thousands. Affected hospitals had to turn away patients or shut down their emergency wards. Car manufacturing plants had to stop production, and power grids were disrupted.
Indeed, as ransomware further evolves, so should the IT/system administrators and information security professionals who protect their organization’s crown jewels; end users must be equally proactive, and defense in depth must be practiced to combat them.
Here are some best practices for mitigating ransomware.
Regularly back up your files
Ransomware capitalizes on fear—the fear of getting locked out of your machine, losing access to mission-critical or personal data, or disrupting business operations. Eliminate the data kidnapper's leverage by regularly backing up your files. Practice the 3-2-1 rule by creating three backups in two different formats with one stored offsite. When backing up your data, ensure its integrity. Backups are only valuable if they're accessible. Periodically test your backups to check that they're readable. Simplify (and document) your backup procedure so that authorized staff can easily retrieve them when needed.
Keep your programs and operating system updated
Many file-encrypting malware take advantage of vulnerabilities to get into the system. WannaCry, for instance, had a worm-like propagation via the EternalBlue exploit, allowing it to spread like wildfire across networks.
Patching and keeping the OS and its software/programs updated can effectively thwart attacks that exploit security flaws. For zero-day exploits and vulnerabilities whose patches may be unavailable, consider virtual patching.
Securely use system components and administration tools
Cybercriminals are increasingly abusing legitimate utilities and system administration tools to install and execute malware. This modus operandi provides bad guys efficiency, convenience, and stealth.
Ransomware is no different. Petya made use of PsExec, while many fileless malware misuse PowerShell. Master boot record-wiping ransomware HDDCryptor used freeware and commercially available software.
Mitigate these kinds of attacks by enforcing the principle of least privilege. Restrict and limit exposure by granting end users enough access or privileges to accomplish a task or run an application. Disable unnecessary and outdated protocols and programs that can otherwise give attackers entry points into your systems.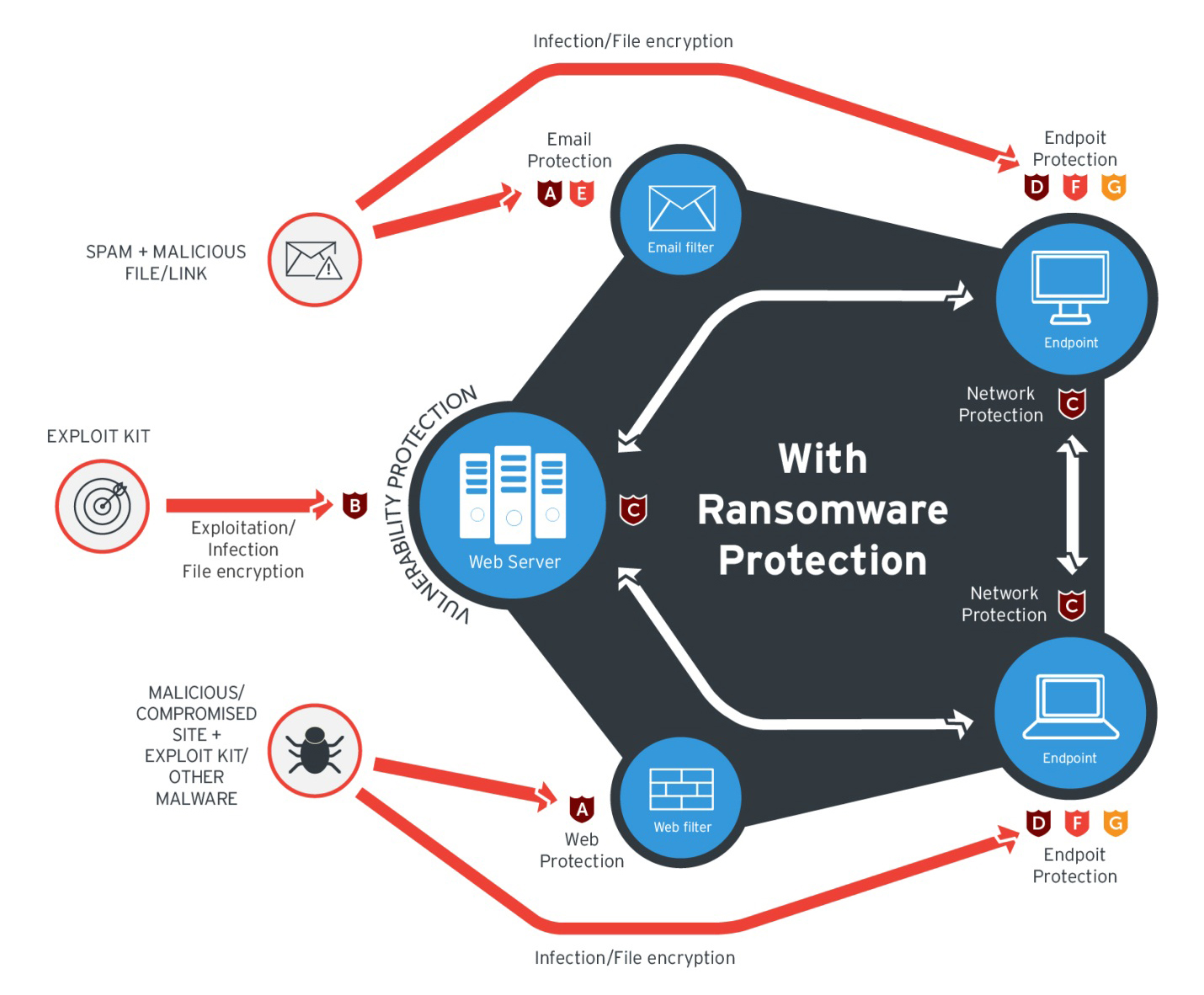
Multilayered defense against ransomware
Protect the network and servers
Protecting the network against ransomware is a must as these threats leverage infected networks to communicate with their command and control (C&C) servers and propagate to other systems within the network share. Firewalls and intrusion detection and prevention systems help pinpoint, filter, and block malicious network traffic and activity. They also provide forensic information that can help detect incursion attempts and actual attacks.
SAMSAM, Crysis, and the Linux-based Erebus ransomware demonstrated that servers should also be defended. A single, vulnerable machine is sometimes all it takes to infect systems and servers within the network. Keep the servers patched and updated. Strengthen your remote desktop credentials against brute-force attacks. Implement multi-factor authentication and lockout policies. Utilize encrypted channels to prevent attackers from snooping on your remote connections.
There are also other approaches you can consider. Network segmentation not only mitigates local traffic congestion; it also improves security by allocating only the resources specific to the user, which significantly diminishes ways for attackers to move laterally within the network.
Data categorization can accomplish the same thing. Classifying data not only makes access more efficient but also determines their value within the organization. Ultimately, these solutions can help mitigate any damage incurred from a breach or attack.
Deploy application control and behavior monitoring
Protect the endpoint by implementing whitelist-based application control, which prevents unknown or malicious programs such as ransomware from executing within the system. Behavior monitoring works in the same vein, blocking anomalous modifications or unusual behaviors in the system. If a malware attempts to delete shadow copies, for instance, behavior monitoring can detect and tag it as a possible ransomware infection.
Enable your sandbox
IT/system administrators can further quarantine ransomware through a sandbox or similar virtual environments. A sandbox should be configured in a way that mirrors the actual configurations of your organization’s systems to better simulate the impact of a suspicious file.
The sandbox shouldn’t just have the ability to contain. It must also be able to analyze the multifarious routines and behaviors of the malware to help identify the obfuscation or evasion tactics that these threats use.
Secure your gateways
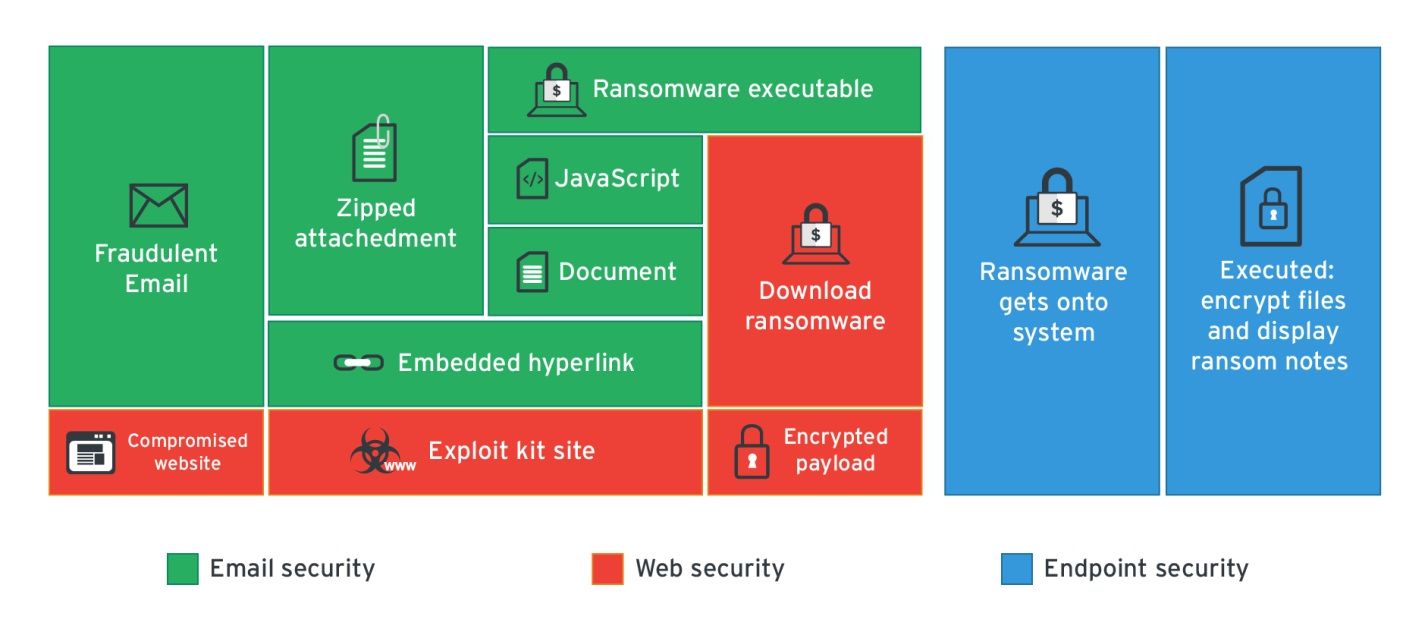
The email gateway continues to be ransomware’s top infection vector. Stop these threats dead in their tracks by thwarting their arrival tactics. Deploy tiered security mechanisms against email-based ransomware and adopt best practices against socially engineered spam emails. The same discretion should be applied to the web gateway: employ URL categorization, delete unused browser plugins, and ensure that third-party components (i.e. Java, Flash) are up-to-date.Cultivate a security-aware culture
Cybercriminals need only hack the weakest link for which no patch is available: the human factor. Social engineering is a staple tactic for many ransomware vectors, and it’s equally important that organizations foster a security-aware workforce. Go beyond regulatory compliance. Develop and constantly fine-tune your proactive incident response and remediation strategies. A culture of cybersecurity in the workplace is just as important as the technologies that stop them.
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Proactive Security: The Role of Exposure Management and Detection-Response Capability
- The Trend Micro Underground Series
- The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity
- Stay Ahead of AI Threats: Secure LLM Applications with Trend Vision One
- Slopsquatting: When AI Agents Hallucinate Malicious Packages
 Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration
Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity
The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity