Safe and Smart Connections: Securing IoT Networks for Remote Setups

On the topic of securing the internet of things (IoT), setups focus typically on the “things” or devices available on the market today. However, while there is no denying that connected devices introduce security challenges, the network (in its role of creating a secure IoT environment) is of equal importance.
During this period of work-from-home (WFH) arrangements, there is an increased demand on networks as remote operations have created greater dependence on the IoT. Subsequently, now is a good time to re-examine the security of networks. In short, rather than focusing on securing individual devices that can compromise a network, users should also secure the network to minimize threats across several devices.
Networks and IoT security
Vulnerabilities in IoT devices are a reality that users must contend with. The more devices are on a network, the more challenging it is to keep track of and prevent threats that could leave the environment compromised. To protect IoT devices from being used to launch attacks like distributed denial of service (DDoS), users must always apply best practices when using such devices.
It’s also worth remembering that the market is filled with competing manufacturers who make devices that have varying levels of security and lifespans. Some devices are designed for offices and businesses, while others are for homes or regular consumers. Both types, nevertheless, are likely to have security measures that are limited to their processing capabilities.
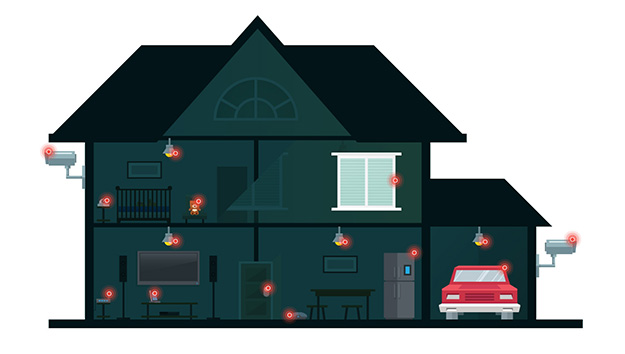 Figure 1. A smart home can contain several devices with varying levels of security
Figure 1. A smart home can contain several devices with varying levels of security
A secure network can provide an added layer of security that can encompass all the devices connected to it. Network security can minimize threats and somehow afford users a singular and levelled ground from where they can implement security measures amidst the uneven security capacity of IoT devices.
How to ready networks for IoT
For most setups, their networks already existed before the IoT was introduced into them. In re-examining network security, it is also good to review what makes networks ready for integrating IoT devices, as well as which weak points still need to be addressed.
Here are a few considerations before adding or creating an IoT environment for any setting:
Upgrade the network to take on a higher bandwidth. The influx of endpoints will take up resources that a network might be unable to provide. Failure to account for an increase in IoT devices that are added to the network and that constantly exchange data could cause connection problems in the future. Enterprises, in particular, should plan beforehand how to best allocate their bandwidth, pinpointing which divisions would need more and when.
Check pre-existing endpoints on the network. Users must also check the security of devices that are already part of the network before adding IoT devices or creating an IoT environment. Endpoints like computers or smartphones could also be weak links, especially if these devices are relatively dated or have missed significant updates. These endpoints should also be checked for compatibility with new devices that are going to be added to the network, as keeping abreast of possible compatibility issues could help with managing these additions.
Keep network policies updated. Enterprises also need to prepare and update their network policy. Employees of an enterprise who are constantly on the network should always stay conscious of the implications of more endpoints being added to the network. Updated network policies should therefore include new security requirements such as the management of user authorization, rules for “bring your own devices” (BYOD), and policies for WFH arrangements.
Network for IoT-related risks
With the basics covered, users and integrators can look to the next phase, which involves not only protecting networks from IoT-related risks, but also using network-level security as a tool to contain and minimize such threats. IoT devices can place networks at risk, but networks can also be used to prevent these risks from materializing with the proper security measures.
The following are some considerations to effectively mitigate IoT-related risks and threats:
Deploy network-level security. It’s important to keep in mind that IoT devices work within the network. While some devices might communicate to external systems and the public cloud, most communicate with other devices that are also within the same network. Should any of these devices communicate corrupt signals, enterprises that do not conduct monitoring within the network would not be able to detect these devices. Network-level security, on top of perimeter defense, can help prevent such occasions.
Create separate networks. Another way that users can minimize the risk of IoT-related attacks is by creating a separate independent network for IoT devices and another for guest connections. In WFH scenarios, users can also opt to put company-issued devices like laptops in a separate network or make them undiscoverable by other devices in the home. A segmented network can help isolate intruders or infections that come from vulnerable devices. For both enterprise and home settings, having a separate guest network would also be helpful in preventing more openings for cyberattacks and malware.
Utilize routers’ security features. Since routers play an important role in networks, it is also crucial to get to know and utilize the security features on these devices. For example, in relation to the preceding tip, many routers have a built-in feature that allows users to create a guest network that uses different credentials from the main network.
Aim for better visibility over the network. Visibility is key for users in ensuring the safety of their network. Even in enterprise environments, guests can connect smart devices to the enterprise’s network without the immediate knowledge of security officers. Enterprises must have the necessary tools on their network to monitor these connections. Additionally, these tools are necessary not only to determine which connections are necessary or risky, but also to take action before threats are realized.
Monitor for baseline and abnormal device behaviors. Part of gaining visibility over the network is monitoring for abnormal behaviors. While this involves understanding each device, knowing what unusual behavior would look like makes it easier to spot potential device takeovers or infections as communicated over the network.
Remove anonymous connections. Each connection to the network must be identified or named. Reducing or removing anonymous connections by labelling each device accordingly can help users and integrators to better monitor their network and pinpoint possible unwanted connections. It would also be much easier to identify problem devices that need to be taken off the network.
Use the network to enforce policies. Security solutions that afford visibility and control over the network help users to enforce the policies that were implemented before the integration of IoT devices. Using the power of the network, they can remove anonymous connections or connections that go against set policies.
Choose devices wisely. While network solutions can help fill security gaps created by uneven security from numerous devices, they are not meant to be a singular solution. Therefore, users should be particularly discerning when choosing their devices. For instance, users are advised to conduct some research and prepare for the different features and types of devices in the market today. Additionally, once they’ve chosen a device for them to connect, it is recommended that they stay updated on the device’s latest vulnerabilities that are often disclosed by vendors.
Take the role of administrator of things seriously. IT experts who are in charge of an enterprise’s network security have limited control in securing WFH setups. This is why users or “administrator of things” at home need to know both the duties of their role and how essential this role is, especially in this current reality of prolonged WFH arrangements.
Figure 2. Different features of IoT home devices can connect to the office network
Home and Enterprise Networks
There are many vantage points that users can take when tackling the issue of IoT security. The network offers one such vantage point from which defenses can be fortified to make up for potential security gaps. Since the recent rise in WFH arrangements, the need for stronger network security has once again been highlighted — not just for enterprises alone — but also for home users. At the same time, IoT security has also been pushed to the forefront as enterprises grapple with remote operations.
By understanding the power of networks in IoT security and implementing device best practices, users can continue to use these technologies in traversing both the changing demands and the blurring division between enterprise and home networks.
For a multilayered defense, users can employ comprehensive protections such as the Trend Micro™ Security and Trend Micro™ Internet Security solutions, which offer effective safeguards against threats to IoT devices through features that can detect malware at the endpoint level. Connected devices can also be protected by security software such as the Trend Micro™ Home Network Security and Trend Micro™ Home Network Security SDK solutions, which can check internet traffic between the router and all connected devices. Lastly, the Trend Micro™ Deep Discovery™ Inspector network appliance can monitor all ports and network protocols for advanced threats and protect enterprises from targeted attacks.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One