 Download Outside Looking In: How a Packet Reflection Vulnerability Could Allow Attackers to Infiltrate Internal 5G Networks
Download Outside Looking In: How a Packet Reflection Vulnerability Could Allow Attackers to Infiltrate Internal 5G Networks
By Salim S. I.
5G technology has been instrumental to the digital transformation of the industrial sector in the age of the Internet of Things (IoT), making it possible for a modern-day factory to have multiple devices connected simultaneously through its own 5G network. But in spite of the productivity and market opportunities they offer, 5G networks aren’t immune to cyberattacks.
In our recent joint research effort with CTOne and the Telecom Technology Center (TTC), the official advisory group to Taiwan's National Communications Commission and Ministry of Digital Affairs, we look into ZDI-CAN-18522, a packet reflection vulnerability in the UPF of 5G cores (5GC). The absence of any authentication mechanisms in the GTP-U protocol between base stations and the user plane of 5GC enabled us to take advantage of ZDI-CAN-18522 in 5GC UPFs and compromise 5G devices connected to internal networks.
ZDI-CAN-18522, which scores an 8.3 on the Common Vulnerability Scoring System (CVSS), would allow cybercriminals from external networks to exploit the GTP-U and attack connected 5G devices. We tested attack scenarios on 5GCs from two commercial and two open-source vendors and found that all— were at risk of these possible attacks as a result of this vulnerability.
Private enterprise 5G network deployments may have different topologies: Certain topologies leave the UPF interface exposed to the Internet, and consequently, are within reach of threat actors on external networks. By exploiting ZDI-CAN-18522, a cybercriminal could still access 5G IoT devices — even if these are protected behind firewalls, Network Address Translation (NAT), and in isolated environments — through an exposed 5GC interface.
An Expanded Attack Surface
In 5G networks, every user device has at least one GTP tunnel to send or receive data traffic that is transferred through these tunnels between the 5GC, which is on the cloud, and a base station. The user plane of 5GC identifies GTP tunnels by way of a 32-bit tunnel endpoint identifier (TEID), which makes up part of the GTP's header; 5G user devices also have individual TEIDs for uplink and downlink.
Through tunneling, the contents of a GTP packet — which is created by appending a GTP header to the original packet — can be sent unmodified across subnets. So long as its TEID is valid, a GTP packet can be sent to a to a 5G user device from anywhere: Cybercriminals could send multiple pings with different TEIDs in the GTP packet to the target IP, banking on smart guessing to match one of the TEIDs with the IP.
The lack of encryption in the GTP-U protocol, in effect, makes the 5GC interface itself a potential entry point for threat actors, as GTP-U tunneling exposes an enterprise’s private subnets to access from external networks (Figure 1). This security flaw is exacerbated by the fact that many 5GC vendors don't have built-in mechanisms that would enable the UPF to verify that packets are sent from trusted sources, as this isn't a mandatory feature under the 3rd Generation Partnership Project (3GPP) standards.
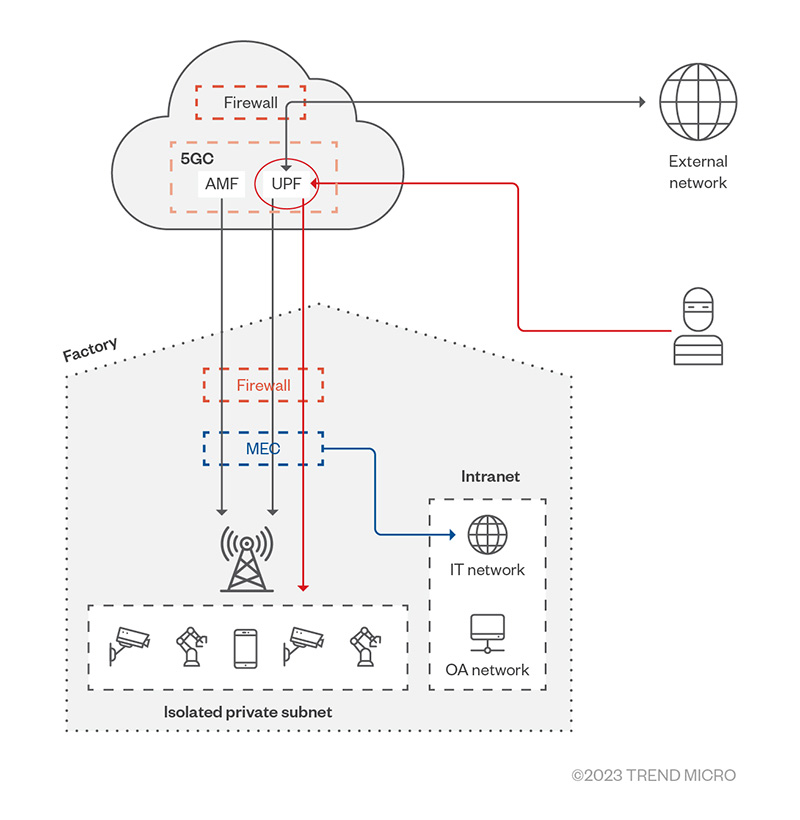
Figure 1. An attacker from an external network can access a private network through a factory’s
Potential Attack Vectors
Over the course of this research, we identified the following attack vectors that threat actors may use to infiltrate 5G networks via this vulnerability:
Downlink
In one attack scenario, we discovered that an attack packet — one wherein a user device’s IP is set as its destination and an Internet IP as its source — can be encapsulated in a GTP packet and sent to the UPF (as shown in Arrow 1 of Figure 2). After looking up its TEID, the UPF decapsulates the packet and sends it to a user device (Arrows 2 and 3). The user device then replies to the Internet IP (Arrows 4, 5, and 6); if the attacker has set the Internet IP to their own, this is how they could establish a two-way connection with the device (Figure 3).
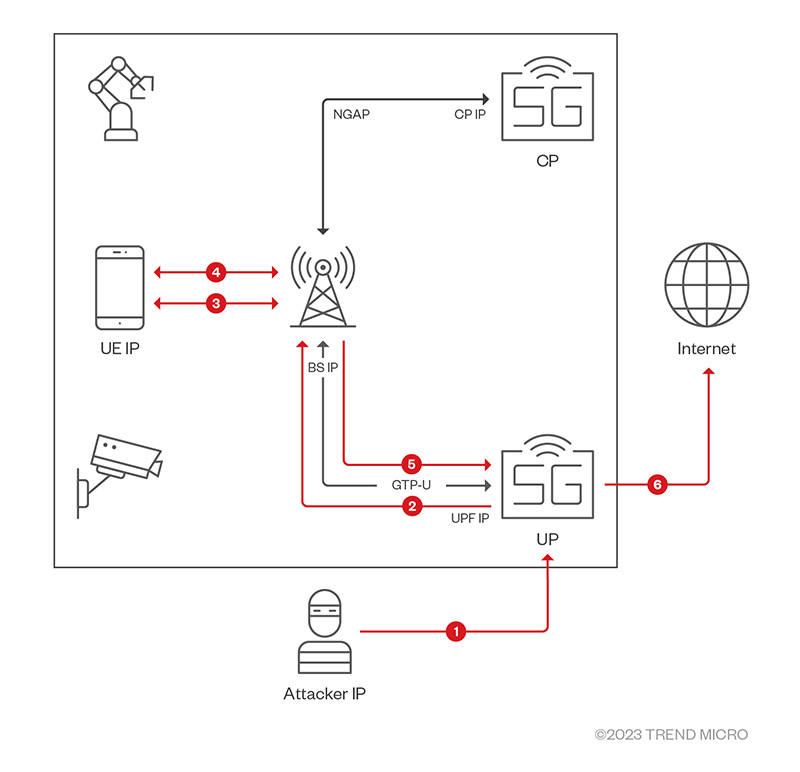
Figure 2. A cyberattack in which the attacker establishes a downlink connection with a 5G user device
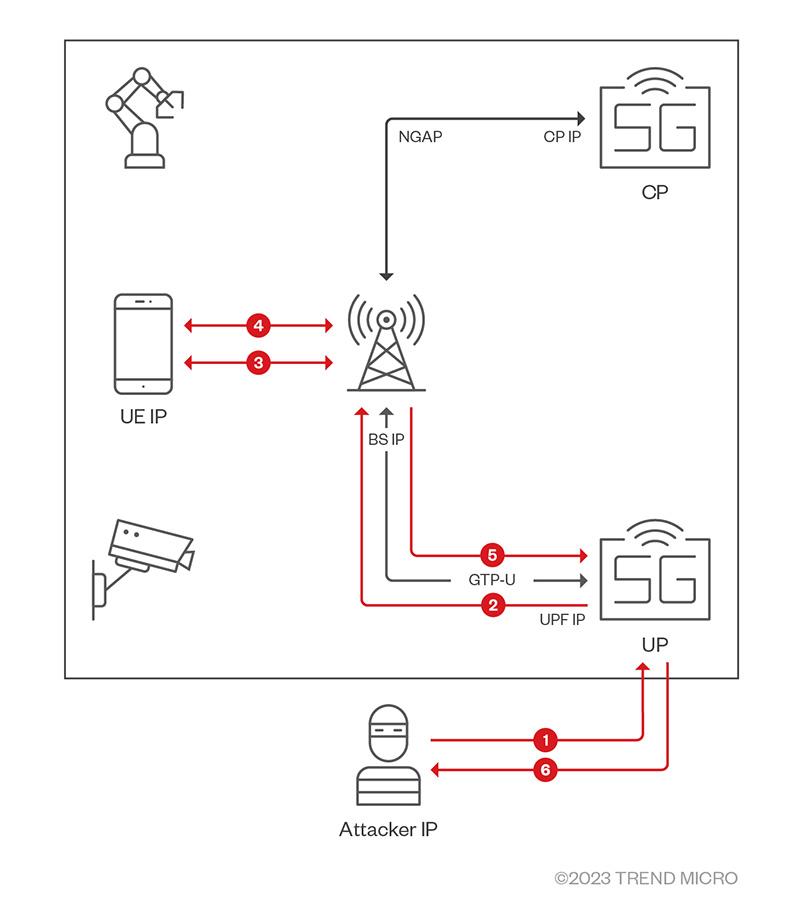
Figure 3. The attacker establishes a two-way connection with 5G user devices
Uplink
Another kind of attack involves an attacker making a packet – this time, with a user device’s IP as the source and an Internet IP as the destination – that’s encapsulated in a GTP packet. This is sent to the UPF (as shown in Arrow 1 of Figure 4), which then looks up the TEID, decapsulates the inner packet, and forwards it to the Internet IP (Arrow 2). The Internet server replies to the user device, sending it the packet through the 5G network (Arrows 3, 4, and 5).
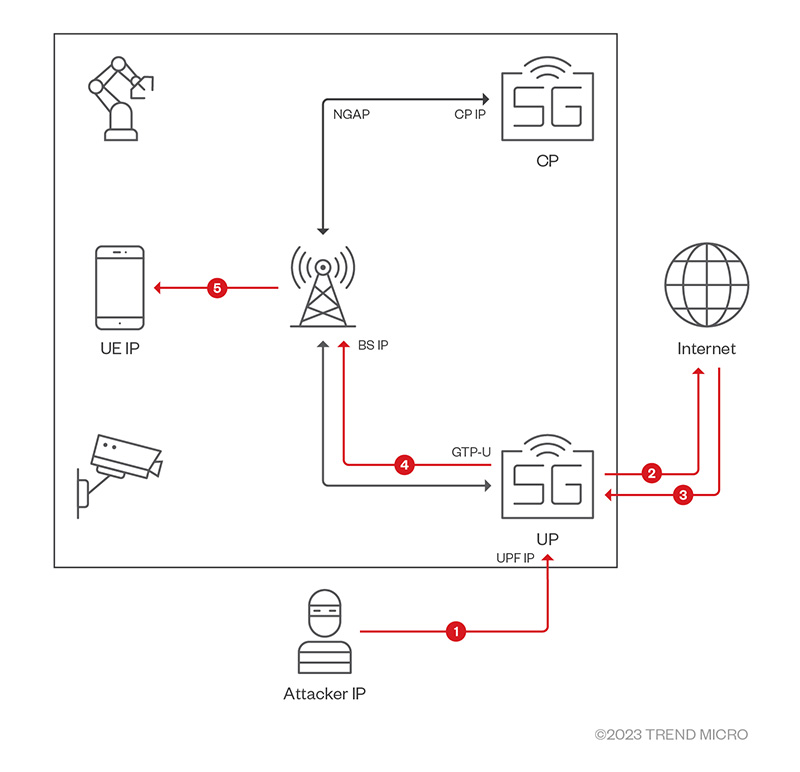
Figure 4. A cyberattack in which attacker establishes an uplink connection on behalf of a 5G user device
Mitigating 5G Security Risks
As manufacturing sites become more connected, so do attackers’ entry points grow more complex. Defending against emerging threats to networked factories requires a proactive and comprehensive security strategy. Shore up their defenses against security flaws like ZDI-CAN-18522 with the following defensive strategies:
- As suggested by the GSM Association (GSMA), enterprises can use Internet Protocol Security (IPsec) to protect GTP. This, or other similar secure tunneling mechanisms between base stations and the 5GC, can help deter man-on-the-side (MoTS) attacks.
- Enterprises can also reduce their attack surface by using an external security device capable of IP cross-checking, as this is not offered by many commercial 5GC vendors.
Multilayered security solutions such as Trend Vision One™, a cybersecurity platform, can help businesses protect their infrastructure. Trend Vision One provides enterprises with a holistic view of their attack surface and streamlined detection and response that’s adaptive to ICS and 5G. It assesses their risk exposure and automatically deploys controls to mitigate those risks, leading to fewer, higher-fidelity alerts that free up security teams to work on strategically important tasks.
As more companies adopt private 5G networks for their low latency, large bandwidth, and high-density capabilities, they will need to protect their factory environments from potential cyberattacks. To this end, Trend Micro's ICS/OT Security offers solutions that are built on exhaustive threat intelligence and expertise from Zero Day Initiative, TXOne Networks, and Trend Micro Research. Its suite of IT-, OT-, and CT-integrated solutions enable early threat detection and response while cutting down on monitoring complexity, empowering manufacturers to better defend their industrial IT ecosystem.
About CTOne
CTOne, a global cybersecurity leader in communication technology, offers enterprise cybersecurity solutions for next-generation wireless networks. A subsidiary of Trend Micro, CTOne enables digital transformation and strengthens the resilience of communication technology.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One