Bogus Business Direct Notification Leads to Backdoor
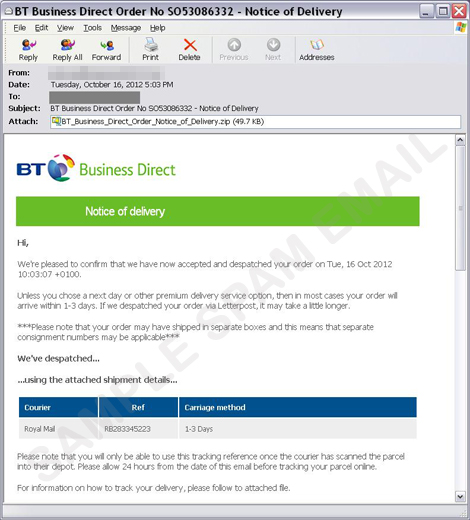
Cybercriminals often use tried and tested tactics to trick users into installing malware. Case in point, the recent spam run purports to come from Business Direct and informs users about a product they ordered online. The said spammed message has a .ZIP attachment, which supposedly contains additional information. Of course, when users opened the .EXE attachment, the malware is executed. Trend Micro detects this as BKDR_ANDROM.AS. These tactic are longer new yet it remains effective.
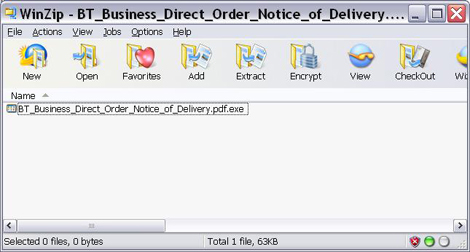
Figure 1. Screenshot of the .ZIP file attachment
BKDR_ANDROM.AS can connect to certain malicious URLs to receive commands from a remote attacker. As such, user systems may be compromised. In addition, it can also download files, which can further cause infection to the system.
Users are strongly advised to be wary of bogus notifications even if these came from supposedly known sources. It is also best to contact the organization and verify if the email message is legitimate or not. Trend Micro Smart Protection Network detects this spam as well as the malicious file.
- ENGINE:
- PATTERN:9280
