Steering Clear of Security Blind Spots: What SOCs Need to Know
 View infographic of "Steering Clear of Security Blind Spots"
View infographic of "Steering Clear of Security Blind Spots"
As technologies continue to evolve and expand, organizations experience a technological paradox: Their increasing interconnectivity means that they simultaneously become more distributed. Case in point, robust cloud and networking technologies support today’s widespread adoption of hybrid and remote work arrangements, allowing employees all over the globe to work remotely full time or at least part of the time.
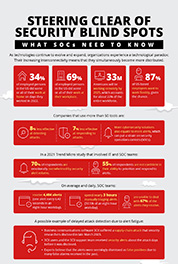
34%
of employed persons in the US did some or all of their work at home on days they worked in 2022.
Source:
US Bureau of Labor Statistics
69%
of employed persons in the US did some or all of their work at their workplace.
Source:
US Bureau of Labor Statistics
32.6M
Americans will be working remotely by 2025, which accounts for about 22% of the entire workforce.
Source:
UpWork
87%
of US-based employees want to work flexibly, given the chance.
Source:
McKinsey & Company
The popularity of these work models has powered the proliferation of modern and distributed systems. Unfortunately, the widespread adoption of such complex infrastructures inadvertently widens the attack surface that cybercriminals can compromise using increasingly sophisticated ransomware attacks and social engineering scams.
To counter this, companies have started deploying cybersecurity tools — lots of them — to keep their data and systems protected against evolving threats and risks. In the process of doing so, however, organizations unintentionally create silos that cause bigger and costlier problems.
On average, organizations use 45 different cybersecurity solutions, with many companies deploying even more security tools than that. Despite the number of tools, security is not a matter of quantity over quality: It has been reported that teams that use more than 50 tools are 8% less effective at detecting attacks and 7% less effective at responding to them.
More cybersecurity solutions also equate to more alerts, which can put a strain on security operations centers (SOCs). Voluminous information, false positives, and alerts — including gray alerts — can lead to SOC teams experiencing alert fatigue and escalated employee burnout.
In a 2021 Trend Micro study that involved IT and SOC teams:
70%
of respondents are emotionally overwhelmed by security alert volume.
55%
of respondents are not confident in their ability to prioritize and respond to alerts.
Source: Trend
In the 2023 State of Enterprise DFIR survey, 54% of digital forensics and incident response (DFIR) teams revealed that they feel burned out at work, while 64% stated that alert and investigation fatigue contributed to their feeling stressed.
Alert fatigue ensues when global security operations centers (GSOCs) drown in a constant barrage of data. The sheer volume of data, coupled with non-stop false positives, can muffle crucial alerts and leave a negative impact on the effectiveness, accuracy, and well-being of SOC members.
On average and daily, SOC teams:
receive 4,484 alerts (one alert every 6.42 seconds in an eight-hour workday).
spend nearly three hours manually triaging alerts (37.5% of an eight-hour workday).
are unable to deal with 67% of the alerts they receive.
Source: Help Net Security
Alert fatigue can have very costly and reputation-damaging consequences for organizations. Take the case of business communications software 3CX, which suffered a supply-chain attack that security researchers disclosed in late March 2023. Based on cybersecurity experts’ analyses of the attack, 3CX users and the 3CX support team seemingly dismissed security alerts about the attack days before it was disclosed, potentially because they assumed these were false positives, owing to the fact that they had received many of those in the past.
This article will help SOC teams minimize burnout and focus their attention, time, and energy on what’s important — potential security blind spots or attack surfaces that can cause big and expensive headaches for organizations.
SECURITY BLIND SPOTS CISOs NEED TO CATCH SIGHT OF
Thwarting siloes and burnout is challenging but feasible
SOC burnout is anything but a new phenomenon, and as environments become more complex and threats become more pervasive, advanced, and wide-ranging, SOCs that are tasked with detecting, assessing, and mitigating these attacks will continue to be overwhelmed and overworked.
Admittedly, solving the SOC burnout problem is no easy feat. Corporate leaders would need to actively communicate and collaborate with SOC teams to relieve stress, determine realistic metrics and action items, and identify barriers for productivity.
Organizations would also need to invest in security solutions that can support their SOC teams to deal more effectively with stressful and time-consuming aspects of the job that can be automated, such as reporting and sifting through troves of information and alerts, so that they can shift their focus on analyzing and mitigating threats.
Trend Vision One™, a cloud-native security operations platform that serves cloud, hybrid, and on-premises environments, can help SOC teams break down silos and improve their security posture. Trend Vision One combines attack surface risk management (ASRM) and extended detection and response (XDR) in a single console to effectively manage cyber risk across your organization, arming it with powerful risk insights, earlier threat detection, and automated risk and threat response options.
Trend Vision One delivers the broadest native XDR sensor coverage in the cybersecurity market. The platform’s native-first, hybrid approach to XDR and ASRM benefits security teams by delivering richer activity telemetry — not just detection data — across security layers with full context and understanding. This results in earlier, more precise risk and threat detection and more efficient investigation.
While tackling the SOC burnout problem remains challenging, organizations can still be empowered to focus on improving communications and workflows and providing their SOC teams with tools that put visibility and automation at the forefront.
Visibility challenges in hybrid
and multi-cloud environments
The cloud enables organizations to keep infrastructure costs relatively lower while empowering them to focus on innovation. Today, organizations are largely dependent on hybrid environments (composed of private and public cloud services) and multi-cloud environments (composed of cloud services from different providers). According to a study from 451 Research, 98% of enterprises use or plan to use at least two cloud providers, while 31% use four or more.
Although these cloud implementations have many benefits such as increased efficiency, having multiple cloud environments running simultaneously can lead to visibility challenges, including evolutionary threats and misconfigurations. This year, a Japanese car company disclosed that a cloud misconfiguration has led to the exposure of the car location information of 2.15 million customers in a 10-year period.
According to Illumio’s Cloud Security Index: Redefine Cloud Security with Zero Trust Segmentation report, 47% of all data breaches originated in the cloud — a substantial statistic considering that 98% of organizations host sensitive data such as financial information, critical company data, and PII there.
Aside from misconfigurations, cloud environments are not exempt from software vulnerabilities. In April 2023, security researchers reported on a Google Cloud Platform (GCP) vulnerability that could have allowed malicious actors to permanently hide a malicious and undetectable application dubbed “GhostToken” inside a victim’s Google account. This app can allow cybercriminals to read victims’ Gmail accounts, access Google Drive and Google Photos files, and track Google Maps locations.
Meanwhile, Google Workspace, a collection of cloud computing and collaboration tools that had more than 3 billion users is also being actively targeted by cybercriminals. A recent Mitiga report shares that free Google Workspace accounts, which lack visibility into logging activity for Google Drive, can be abused by cybercriminals to surreptitiously steal company data.
Security at the seams
The problem of “security at the seams” also occurs in multi-cloud environments. Security at the seams refers to how security risks arise at the meeting points of individual cloud services when they connect to one another, to servers, or to services. Although each cloud service is designed with security in mind, organizations need to ensure that their critical data moves across their different cloud implementations in a protected manner. They also need to ensure that the applications that will have access to their multiple clouds remain as secure as possible.
As for organizations relying on applications that use APIs and are hosted on different clouds, they could experience difficulty tracking and managing both public and private APIs. The 2022 API Security Trends Report showed that on average, large enterprises (with over 10,000 employees) had 25,592 APIs. Such a large number of APIs, which are used by apps to communicate and share data, can greatly increase an organization’s attack surface, especially if a company’s API inventory includes abandoned and outdated APIs.
When cybercriminals exploit vulnerable APIs, they gain access to and siphon off potentially sensitive data, including employee and customer personally identifiable information (PII). Early this year, T-Mobile reported that cybercriminals stole 37 million postpaid and prepaid customer data — including names, billing addresses, emails, phone numbers, and dates of birth — by exploiting an API.
Cloud skills gap, complexities, and configuration issues
The cloud empowers organizations to gain a competitive edge, but it comes with many complexities that require skilled talent that is hard to come by. The Voice of the Enterprise: Cloud, Hosting & Managed Services, Cloud Skills 2022 survey shares that 44% of organizations in its study find it challenging to bring in and hire qualified candidates.
It’s no secret that the lack of qualified personnel leaves businesses susceptible to attacks. Based on the Cyber Workforce Study 2023 report, 35% of organizations’ security teams have “no or minimal knowledge” in cloud security. This is concerning since Palo Alto Networks reported that 80% of security exposures can be found in cloud environments.
Without qualified professionals at the helm, cloud configuration issues will likely abound — a risk that businesses are aware of. A 2023 Cloud Security Alliance (CSA) report states that 43% of organizations list misconfigurations as their top security concern. In a 2021 report, we discussed the top 10 Amazon Web Services (AWS) and Microsoft Azure services with the highest misconfiguration rates with regard to the implementation of Cloud Conformity rules and discovered that certain rules had 100% misconfiguration rates.
Organizations also need skilled professionals to handle complex and distributed cloud environments that are composed of numerous and different security stacks, policy engines, controls, and asset inventories.
Compliance concerns
Companies that belong in critical sectors need to comply with stringent regulatory standards, guidelines, and laws to ensure that the data that resides in and is processed in the cloud is kept secure at all times. Unfortunately, not all companies have a good handle on their cloud governance, and it’s a major concern for businesses. According to a CSA report, 57% of organizations are worried about the regulatory compliance of their cloud projects.
Take the case of financial organizations. To provide fast, consistent, and reliable online services to their customers, they would need to take advantage of cloud services. However, financial companies that handle troves of personal and financial information need to ensure that their cloud service providers (CSPs) have compliance certifications to protect massive amounts of critical data. These certifications include the Payment Card Industry Data Security Standard (PCI DSS), an information security standard that aims to reduce financial fraud, and the System and Organization Controls 2 (SOC 2), which are internal reports that aim to give users insights on risks associated with outsourced services. When these organizations use different cloud services and providers, staying compliant will depend on their ability to have visibility and control over diverse data sources.
The abuse of generative AI tools
The abuse of artificial intelligence (AI) technologies, particularly generative AI, in malicious attacks has been of great interest to security researchers and CSOs. In our previous reports, we discuss this misuse in novel attacks such as pig butchering, virtual kidnapping , and harpoon whaling.
With generative AI tools, malicious actors can craft legitimate-looking emails for phishing attacks. On top of using AI for phishing content, researchers have also recently discovered that AI chatbots can be easily duped via an indirect prompt injection attack, which involves hackers planting a prompt on a webpage in zero-point font. When a user interacts with the AI chatbot that has ingested the compromised webpage, this activates the prompt and enables the hackers to convince users to share personal information, such as users’ real names, without raising suspicion. This attack can then lead to identity theft. While the loss of personal data is no small matter, corporate information theft is alarming as it can lead to costly data breaches.
Currently, organizations are beginning to understand just how dangerous this technology can be in the wrong hands. In a survey that involved 500 senior IT leaders, 71% presume that it’s possible for generative AI to “introduce new security risks to data.”
Attacks on emails and messaging platforms
It is projected that by 2026, there will be 4.73 billion email users around the world — an 11% increase from 2022’s 4.26 billion email users.
Given the continued reliance of organizations on email for business continuity, it remains a favored attack vector by cybercriminals. A recent Deloitte study found that a staggering 91% of all cyberattacks start with emails that belie their malicious intent. For their part, businesses are aware that cybercriminals use emails for ill intent. According to the 2023 State of Email Security (SOES) report, three out of four IT security leaders from global companies expect that email-based attacks will have serious consequences for their business.
Malicious actors are constantly upping the ante when it comes to launching email attacks, including exploiting email-forwarding flaws to conduct forwarding-based spoofing. This attack compromises tens of thousands of vulnerable domains, including financial service companies, news organizations, and US governmental bodies. With this attack, cybercriminals can send malicious emails purporting to come from legitimate organizations, thereby increasing their chances of fooling a larger number of victims.
Cybercriminals are also keen on compromising widely used enterprise communication and collaboration platforms, such as Slack and Microsoft Teams. Early this year, it was reported that attackers stole employee tokens to gain access to Slack’s GitHub private code repositories. In June 2023, researchers shared that a Microsoft Teams bug allows external sources to send files to an organization’s employees, which could potentially allow cybercriminals to introduce malware into an organization’s files. Microsoft Teams is also being abused in a phishing campaign that distributes and installs the DarkGate malware.
Shadow IT and Shadow AI
Shadow IT, which happens when employees access corporate data using personal or unsanctioned devices, applications, and services, continues to hinder enterprises from achieving full visibility. This is especially true since work environments have completely changed because of the global pandemic and the expansive number of internet-of-things (IoT) and industrial internet-of-things (IIoT) devices: In 2022, 41% of employees “acquired, modified, or created technology outside of IT’s visibility.”
Now that generative AI has entered the Shadow IT game — a phenomenon called Shadow AI — it’s going to be even more difficult for SOC teams to secure the entire corporate environment from threats and risks. Even though organizations are discouraging and restricting their employees from using generative AI at work, a large number of the workforce uses it at different capacities. According to research conducted by Dell, 71% of survey respondents have used generative AI at work.
Network problems
Organizations need to support multi-cloud and hybrid setups that require the ability to efficiently connect distributed offices, employees, and cloud deployments. On top of that, organizations with systems that require advanced capabilities, such as metaverse projects and virtual desktop infrastructures (VDIs), need a robust network infrastructure. Malicious actors can take advantage of organizations’ network complexity to launch tried-and-tested attacks, such as exploiting network vulnerabilities and launching distributed denial-of-service (DDoS) attacks.
For example, vulnerabilities that abuse Server Message Block (SMB) version 1, or SMBv1 in short, still abound today, despite SMBv1 being decades old and strongly recommended to be disabled. A recent Armis report also found that 74% of enterprises today still have at least one asset in their network that’s vulnerable to the EternalBlue exploit, which is an SMBv1 vulnerability and the moving force behind massive ransomware attacks such as WannaCry.
Meanwhile, DDoS attacks are still widely used, as evidenced by the 7.9 million DDoS attacks launched in the first half of 2023 alone, according to the 1H2023 DDoS Threat Intelligence Report. Last month, tech giants Google, Amazon, and Cloudflare were hit by large-scale DDoS attacks that were enabled by an HTTP/2 weakness.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One