Given the nature of the underground, it shouldn’t be a surprise that even traditional criminals communicate and even sell their wares via these underground forums. Is it an evolution of cybercrime or just a case of birds of a feather sticking together? Let’s take a closer look.
A popular offering: vehicle modifications
While monitoring the cybercrime underground, we observed a number of advertisements peddling vehicle toolkits to potential customers. These kits allow users to bypass (physical) security mechanisms put in place by car vendors, allowing a user to perform administrative tasks such as updating and reprogramming the Engine Control Module (ECM), which makes engine decisions based on sensor information and performance. The updated versions of the firmware in the advertisement feature the ability to bypass the immobilizer, a security device that prevents the vehicle from running unless the correct key is used. The module costs about 450 USD.
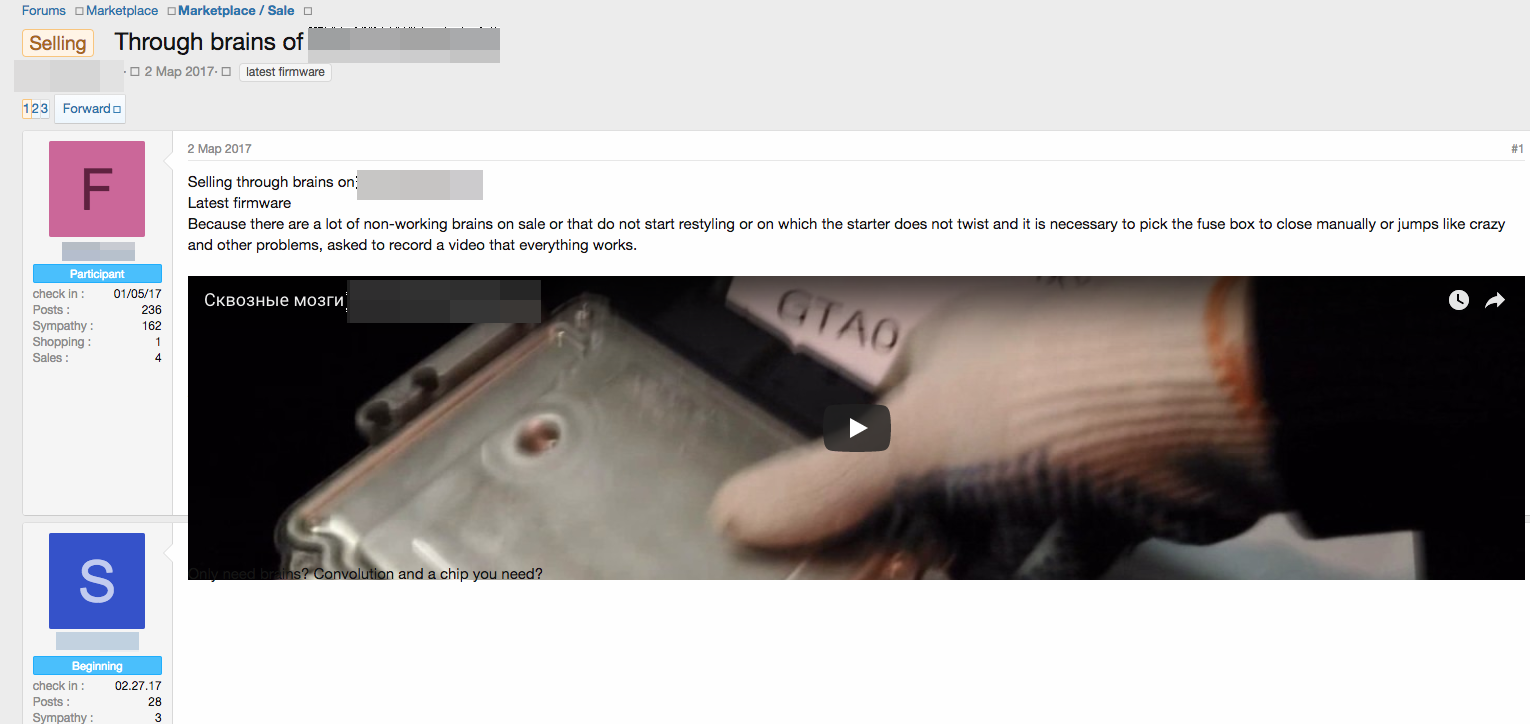
The same forum thread mentions several other auxiliary tools, including a “Universal Ignition key”, which is sold for about 75 USD. This tool allows its user to open, start (and effectively steal) a car in about a minute by bypassing standard security and alarm mechanisms during or after the theft. Attackers have been seen to sell both physical keys and electronic key fobs in their advertising videos. In the case of electronic key fob theft, this works by spoofing the signal of a legitimate key fob to allow its user to enter and steal the vehicle.
While these tools require physical presence to implement the attack, it is important to highlight two aspects. First, the same attack can, in theory, be performed remotely, provided there is a vulnerable entry point as demonstrated by previous research efforts that wirelessly access the CANBUS using an exploit in the car’s entertainment system. Second, since the ECM is essentially the “brain” of the engine, malicious functionalities could be included in the “kits” sold, for example, to tamper (even silently, as we had shown last year) with in-vehicle features, ultimately endangering human lives. Cybercriminals are known for leveraging pirated copies or cracks for paid software as a malware distribution vector, and it's certainly possible for them to abuse connected cars in a similar manner. End users may be tempted to “upgrade” the factory-supplied firmware on their vehicles to bypass official repair services, as seen in the case of John Deere tractors that were “hacked” with Ukrainian firmware.
What we see here is that the synergy between physical crimes and cybercrime can lead to hybrid types of cyber-enabled attacks, including on-demand attack services with various objectives — for example, blackmailing high profile figures — or simply to threaten human lives. Our analysis of criminal services in the deep web back in 2015 revealed several cases of on-demand crime services (including assassination).
Automobiles are ideal for this type of attack because they have relatively long lifecycles combined with a limited capability of remotely updating hardware or firmware at scale. As long as vulnerability patches are not that easy to distribute or install, the targets will remain exploitable, presenting a very visible target for cybercriminals. This industry is moving towards internet-connected vehicles or even self-driving cars, which requires more sensors, information exchange between vehicles, “smart” roads, and intelligent transportation systems infrastructure in general, which expands the attack surface. The industry is stepping into the IIoT world, where attackers can exploit unaddressed vulnerabilities remotely.
The author of the forum post below offers a variety of services — both cyber and physical — across a variety of underground forums, including stolen or lost passports, car alarm system dongles, and SIM card recovery services, among others.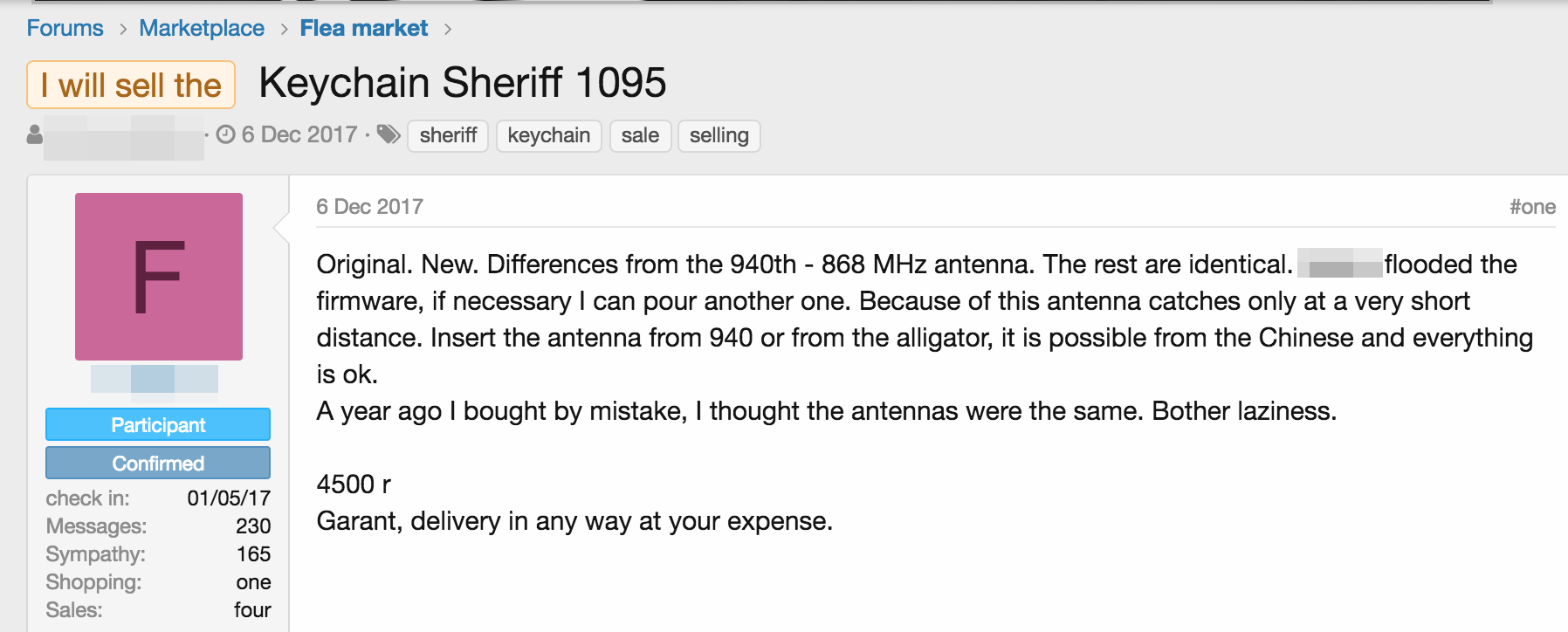
In addition, the user offered other products and services such as patched radio sets that can wiretap police and emergency services communication, as well as suppress alarm systems and garage-door openers. While listening in to police scanners isn’t illegal per se, today’s police departments often encrypt their scanners, often when they are digital in nature. These products may be capable of decrypting these encrypted police communications, which is illegal in some jurisdictions. The forum poster even offered to burn a car for a reward in a thread discussion titled “how to punish a neighbour.”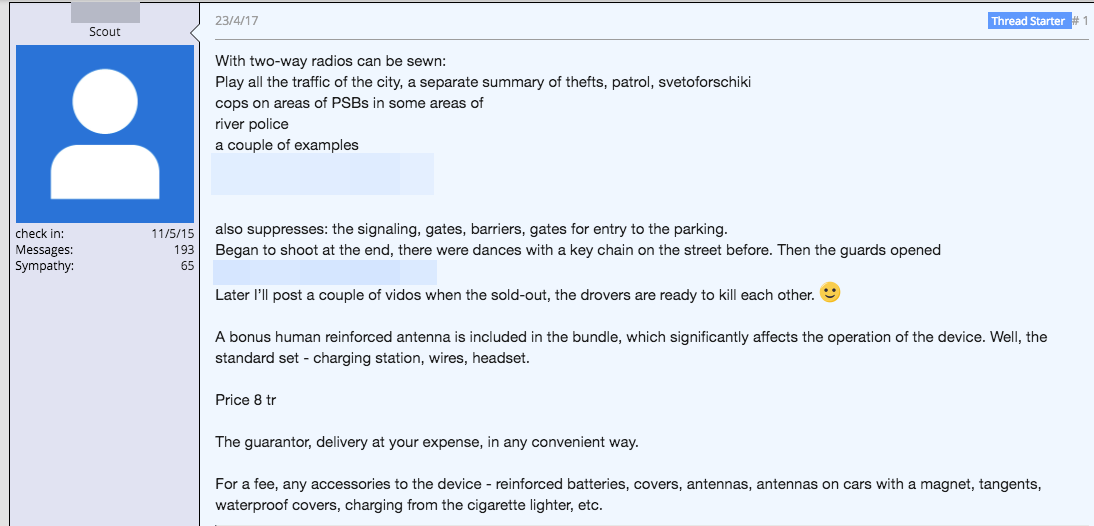
Physical crime subcategories in underground forums
Many cybercrime forums now contain either dedicated threads or even subcategories related to physical crime, such as vehicles, which include the sale of devices that can intercept signals and open door locks for a dozen major car manufacturers, as well as fake documentation and code grabbers.
Interestingly, sellers on these forums rarely mentioned cars directly and usually resorted to using slang terms, most likely to avoid providing damning evidence to police and law enforcement agencies. These terms might not even be remotely connected to what they’re referencing (for example, “Siberian Cheese” refers to freshly stolen cars from Siberia; it's not a type of dairy product from Eastern Russia). An unsuspecting reader might wonder why an underground forum hosts cheese connoisseurs.
Other examples of physical crime in the underground
Close ties between cybercriminals and traditional (non-cyber) actors are visible in other markets. Travel related services, which can be classified as internet or internet-enabled crime, is one of the major monetization markets in the underground. The crimes can even be more sinister in nature; as a recent example, a police investigator was threatened and later killed while looking into the activities of a group that used hacked accounts to steal money from railroad and airline companies.
Conclusion
The near future should see a further rise in threat actors who delve in both traditional crime and cybercrime, as well as an increase in physical crime services being peddled in platforms that are traditionally for internet-enabled crime.
The reason is two-fold: first, cybercriminal groups are becoming increasingly professional, even rivaling traditional organized crime groups (OCG) in both scope and ambition. Many cybercrime groups are expanding towards physical crime for additional revenue streams, while traditional crime groups are recognizing cybercrime's profit potential, and are starting to set up their own operations to deal with the digital side of law-breaking.
Second, the continued emergence of the internet of things (IoT) is blurring the line that separates what exists in the digital realm and the real world, blurring the line that differentiates traditional criminals and cybercriminals as well.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One