-
Additional Security Layers
-
Credential Phishing
-
BEC Trends
-
Abused File Types
-
Malware
-
Advanced Email Security
Of all infection vectors, email remains one of the most consistently used platforms in cybercrime because of how easily it can be abused. Apart from being a staple communication and collaboration tool, email is effortless and cheaper (if not cost-free) to distribute. The convenience it affords to cybercriminals puts enterprise environments using email services in a potentially precarious situation — they can be susceptible to fraud, spying, information theft, and spoofing, among other attacks.
In 2018, Trend Micro™ Smart Protection Network™ security infrastructure detected and blocked over 41 billion email threats. The overwhelming increase in the number of phishing attacks and spam campaigns, as well as cybercriminals’ constant bundling of email with various types of malware, contributed to this huge total. The proliferation, not to mention persistence, of these threats should remind organizations to look into all types of countermeasures to efficiently protect their systems and networks.
Additional Cybersecurity Layer Still Necessary for Blocking High-Risk Email Threats
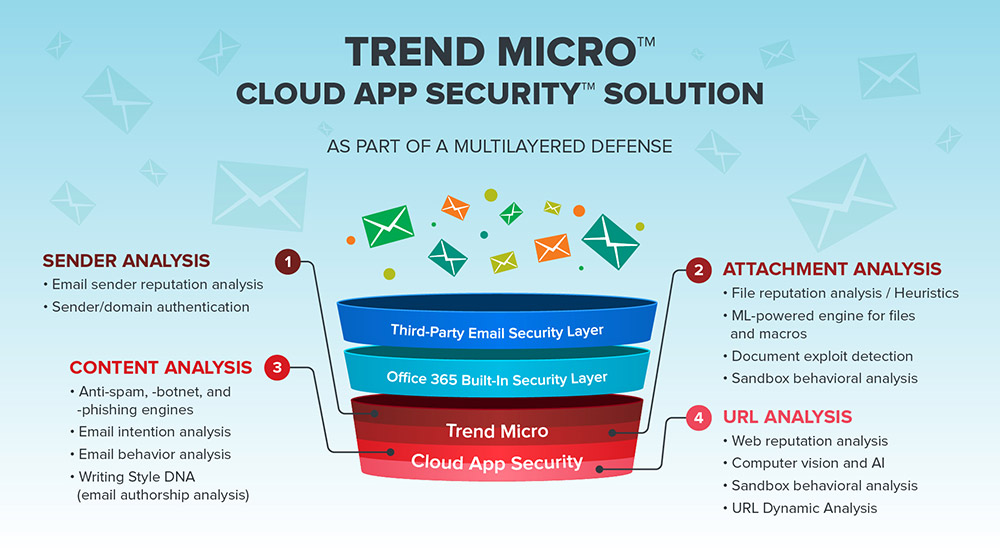
The Trend Micro™ Cloud App Security™ solution provides advanced protection for cloud email and file sharing applications such as Microsoft® Office 365™ Exchange™ Online, Google Drive™, OneDrive® for Business, and SharePoint® Online platforms, ensuring that organizations’ assets, especially their data, are secured and used in a transparent manner. It serves as an additional layer of protection after emails and files have passed through the said cloud applications’ own security filters. It uses machine learning (ML), sandbox malware analysis, and other cybersecurity technologies to defend systems against business email compromise (BEC), phishing, spear phishing, whaling, ransomware, and other advanced email threats.
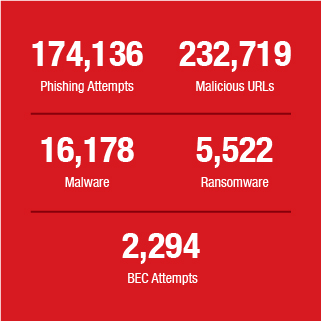
Cloud App Security caught even more threats in 2018 than in the previous year, detecting and blocking a total of 8,920,792 high-risk email threats.

Some businesses that use email services such as Office 365 rely on built-in security filters while other businesses add one or more third-party security solutions for added protection against threats. The 2018 threat data shows how Cloud App Security helps businesses with existing email security, whether built-in or standalone, by detecting and blocking high-risk threats missed by previous security layers.
The case of a large company in the logistics industry, which has 80,000 Office 365 users, illustrates the point. Cloud App Security detected and blocked more than half a million additional phishing emails, among other threats (see flip cards for the complete list). These high-risk threats were detected after they passed through Office 365 built-in security filter and Office 365 Advanced Threat Protection (ATP), an add-on service. Another example is a large company in the hospitality industry that has 120,000 Office 365 users. This company, which used a third-party email security gateway, had additional email threats blocked by Cloud App Security in the hundred thousands (see flip cards for the complete list).
Businesses using Cloud App Security as the only supplementary layer were also further protected. A large company in the internet industry, which has 10,000 Office 365 users, and a small business in the information industry, which has 115 Office 365 users, also had additional detections (see flip cards for the complete list).
*Hover to flip to the breakdown of threats detected by Cloud App Security
*Tap to flip to more details on additional threats detected by Cloud App Security







A multilayered cybersecurity strategy is truly vital in the connected age because, whatever the size of the business, the chances are high that they will run into threats that can be tenacious in tearing apart cyber defenses. In 2018, we saw new tricks and trends in email attacks designed to serve this purpose, and at the same time, familiar but notorious banking trojans, backdoors, and ransomware continued to abuse email to deploy attacks. To provide organizations a comprehensive view of the email threat landscape, we look at these notable occurrences as well as recommend countermeasures to adopt to defend against advanced email threats.
Credential Phishing Tactics Increasingly Target Office 365 Users
Credential phishing has continued to flourish because of cybercriminals’ continuous efforts to produce new variations of attack. Cloud App Security data showed that credential phishing attacks are still widely deployed: It accounted for 40 percent of the total high-risk email threats detected in 2018.
Credential phishing accounted for 40 percent of the 8.9 million high-risk email threats detected by Cloud App Security in 2018.
Last year, new credential phishing attack variations struck the headlines when security researchers found them targeting Office 365 users. Cloud App Security was able to detect phishing emails that attempted to harvest the account credentials of Office 365 users via similar schemes.
The email below, which was detected in October, posed as an account termination notice from Office 365. In the scheme, an email notification is sent to users informing them that they have requested to terminate their corporate email account. The email also advises users that if this supposed termination was an error, they can cancel it by clicking an embedded link at the bottom part of the email. Once the link is clicked, they are led to a phishing page that impersonates an Office 365 login screen. The users’ Office 365 credentials will be stolen if they attempt to log in.

The popularity of Office 365 has positioned it as an attractive target for cybercriminals. The credential phishing email shown above, which was detected by Cloud App Security, poses as an Office 365 notification email.
Aside from this account termination scheme, other types of phishing tactics aimed at Office 365 users also emerged. In December, fake non-delivery reports (NDRs) were deployed to phish Office 365 user credentials. Uncovered by Xavier Mertens, Senior Handler of the Internet Storm Center (ISC), the NDR emails contained malicious URLs that, when clicked, directed the user to a bogus Office 365 login page.
In January 2019, the U.S. Secret Service also shared information regarding phishing attacks that specifically target organizations using Office 365. According to the Secret Service, spear-phishing emails that seem to link to an encrypted document were spotted. Users that click on the link are asked to enter their email account credentials via a fake Office 365 login request form that appears legitimate. Attackers gain access to the email accounts of users who fall for the scheme.
BEC Persists and New Trends Arise
BEC attempts accounted for 1 percent of the total detections. This percentage may seem small in comparison to other threat types detected by Cloud App Security, but BEC should not be overlooked: The Federal Bureau of Investigation’s (FBI) July 2018 public service announcement (PSA) on BEC stated that BEC scams have already caused US$12.5 billion global losses as of 2018, with an average exposed loss of US$159,000 per incident.
BEC attempts accounted for 1 percent of the total high-risk email threats detected by Cloud App Security in 2018.
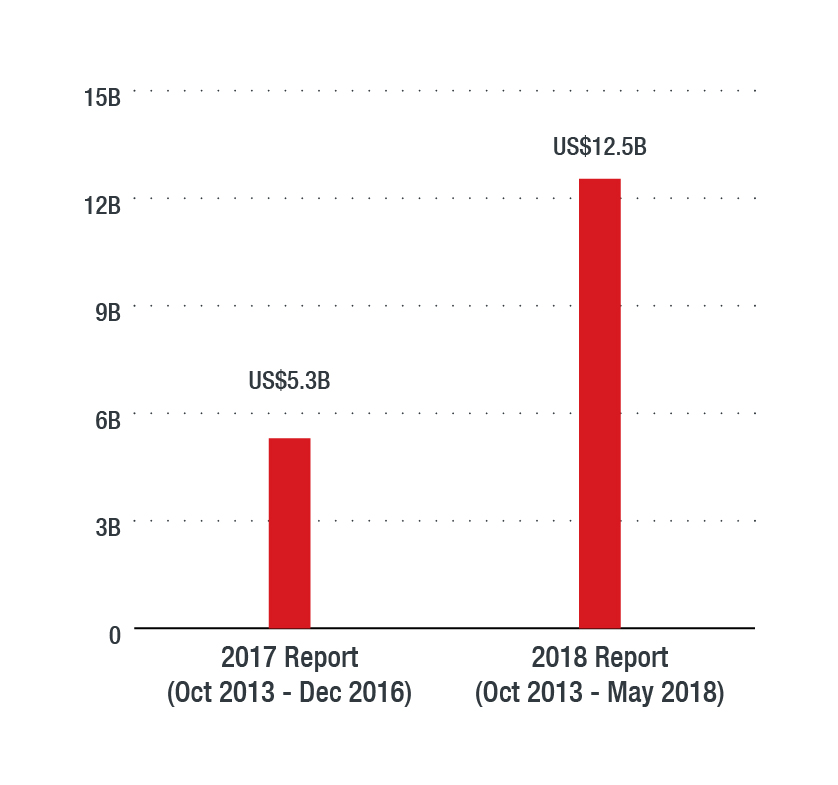
According to the FBI, since 2013, global losses to BEC reached US$12.5 billion in 2018 — a 136.4 percent increase from the reported total in 2017.
Aside from the aforementioned global losses, the same PSA also highlighted that the real estate sector was increasingly being targeted by BEC scammers. May 2018 recorded the highest number of BEC real estate victims since 2015. The bureau reported that victims that have participated in all levels of transactions — from title companies, law firms, and real estate agents to buyers and sellers — were tricked with spoofed emails that manipulated them into changing payment type and/or payment location to a falsified account set up by the BEC scammer/s. As seen in the BEC sample, this is a common deception tactic among BEC scams and not just in real estate ones.
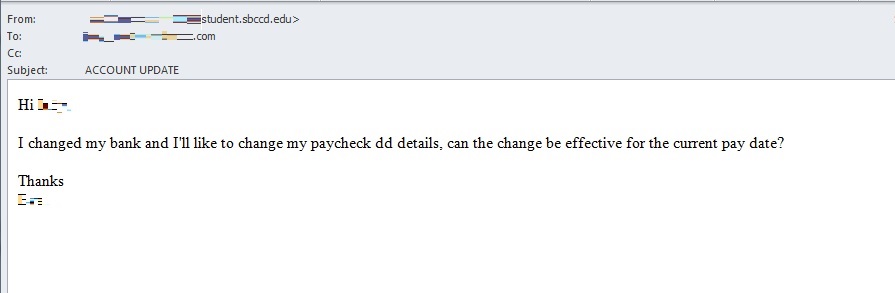
Sent using an email address with a suspicious domain, this BEC email impersonating an executive requests a change in banking details.
In what appears to be a product of masterful social engineering, BEC scammers were also reportedly using “domestic money mules” in real-estate-related scams; these money mules were recruited via confidence or romance scams. After grooming these victims, scammers will trick them into opening accounts that will only be used for a short term, presumably to avoid being tracked by the authorities.
In October 2018, the FBI also released a PSA on the increased number of BEC complaints that involved victims being tricked to purchase gift cards. In this BEC scam, a cybercriminal posing as a person in authority may send a spoofed email, phone call, or text to a victim, requesting to buy gift cards for personal or business purposes. Additional requests for wire transfer payments were observed in some incidents.
Between January 2017 and August 2018, a total of 1,164 BEC gift card complaints have been recorded, with adjusted losses of US$1,021,919. Notably, the number of recorded complaints between January 2017 and August 2018 showed an over 1,240-percent increase — an indication that BEC gift card scams are on the rise.
Cybercriminals Expand File Types Abused to Evade Detection
As detection methods continue to advance, cybercriminals also continue to devise new evasion methods to keep up. Some of these methods can be complex. For example, the use of fileless threats, which can come from macro codes embedded in seemingly benign file attachments and launched through legitimate tools like PowerShell. Others can be as simple as the abuse of a rarely used file format.
Our researchers came across spam campaigns that utilized old-yet-rarely-used file types to disguise malware attachments. This method can take advantage of such file types’ structure to evade certain kinds of detection techniques (for example, signature-based detection), or to attempt to bypass an outdated or nonflexible security filter.
One example is the .ARJ file format, which the Trend Micro Smart Protection Network architecture detected in thousands of malicious files last year. After analyzing a spam sample that carries an .ARJ file, our researchers found that, after the file is downloaded to a device, it can drop and launch an executable file.
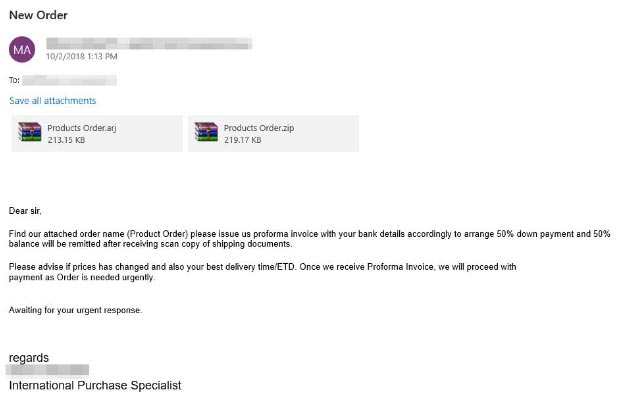
A spam sample that uses an .ARJ file hides under the guise of a purchase order.
We also observed a spam campaign that abused .IQY files. For this particular campaign, approximately 500,000 spam samples were detected. Notably, the choice to utilize the rarely used .IQY file type is just one of the multiple techniques deployed by this campaign. In addition, once the .IQY file is opened, Dynamic Data Exchange (DDE) and PowerShell will also be abused subsequently, with the final payload delivering either a backdoor or a trojan. This proves that, while using a different file type may be simple, when combined with other techniques, it can create a multifaceted attack that can put users and organizations at a higher risk of infection.
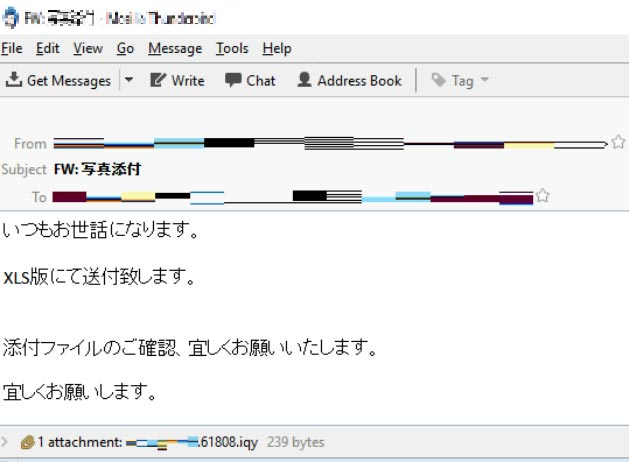
A spam sample using an .IQY file. The Japanese subject reads “Photo attached” while the message body reads “Always thank you for your help. I will send it in XLS version. Please check attached file, thank you. Thanking you in advance.”
Apart from .ARJ and .IQY, we also observed cybercriminals experimenting on file types such as .Z, .PUB, and SettingContent-ms.
Email Still Favored by Attackers for Delivering Notorious Malware Variants
Data from Cloud App Security shows that malware accounted for 12 percent of the total high-risk email threats detected in 2018. While there are a variety of malware distribution techniques, ranging from abusing internet of things (IoT) devices, app marketplaces, and vulnerabilities to using exploit kits and malicious websites, email remained a popular choice for cybercriminals who are operating behind notorious malware families.
Malware accounted for 12 percent of the high-risk email threats detected by Cloud App Security in 2018.
Case in point: Emotet, a five-year-old malware described by the United States Computer Emergency Readiness Team (US-CERT) as one of the most destructive and costly malware affecting governments and the private and public sectors. Found with notable multilayer operating mechanisms, Emotet is predominantly delivered via email and uses financial-related email subjects to deceive recipients. Trend Micro Smart Protection Network data placed Emotet as the seventh most detected malware family globally in 2018.
Meanwhile, the GandCrab ransomware made headlines last year when spam campaigns were spotted distributing its v2.1 variant in April. GandCrab resurfaced in August, with its v4.3 variant being delivered to South Koreans via phishing emails in Hangul. Trend Micro Smart Protection Network data showed GandCrab as the second most detected ransomware family in 2018.
Other notorious malware families that rely on email as their primary infection vector also made notable appearances last year. Trickbot was found with a new PoS malware feature and a password grabber module (pwgrab32) that steals access from several applications and browsers, such as Microsoft Outlook, Filezilla, WinSCP, Mozilla Firefox, Microsoft Edge, and Google Chrome. URSNIF, on the other hand, was used by cybercriminals in a highly sophisticated scheme where hijacked email accounts send the trojan as part of or as a reply to an ongoing email thread. Email users may have difficulty spotting this scheme because of cybercriminals’ use of a legitimate email thread.
Counter Advanced Email Threats With Computer Vision, Writing Style DNA, and Machine Learning
As email threats continue to multiply and become more complex, organizations should be able to set up a multilayered cybersecurity defense to address the risks that email threats pose.
Cloud App Security has the capability to enhance the built-in security of email services like Office 365 by using ML in detecting suspicious content in the message body and attachments, sandbox malware analysis, document exploit detection, and file, email, and web reputation technologies. This security solution detects advanced malware hidden in Office 365 or PDF documents, maximizes cloud efficiency learned from years of experience protecting Microsoft Exchange and SharePoint environments, and scans files shared by remote colleagues, clients, and mobile devices to ensure threats are barred from using OneDrive or SharePoint to migrate.
In 2018, two new advanced features were introduced into Cloud App Security to help businesses stay protected from high-risk and advanced email threats.
The first is Writing Style DNA, an ML-powered technology that can help detect email impersonation tactics used in BEC and similar scams. It uses ML to recognize the DNA of a user’s writing style based on past emails and then compares it to suspected forgeries. The technology verifies the legitimacy of the email content’s writing style through an ML model that contains the legitimate email sender’s writing characteristics.
The second technology is a feature that combines artificial intelligence (AI) and computer vision in order to help detect and block attempts at credential phishing in real time, especially now that more schemes continue to use legitimate-looking fake login webpages to deceive email users. After suspected phishing emails go through sender, content, and URL reputation analyses, computer vision technology and AI will quickly examine the remaining URLs to check if a legitimate login page’s branded elements, login form, and other website components are being spoofed.
These technologies, alongside other features, embody not only the advancement of Cloud App Security but also its agility and flexibility in defending against email threats — regardless of the number and level of sophistication — and make Cloud App Security a smart choice to integrate into a multilayered cybersecurity defense.
However, an effective cybersecurity strategy doesn’t only consist of multiple layers of cybersecurity protection. It also needs workforce cybersecurity awareness so that no security holes can be accidentally opened for cybercriminals to exploit. In addition to employing security solutions, organizations can inform employees of best practices against email threats and help them become more vigilant by deploying our free phishing simulation and user training service.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One