.EGG Files in Spam Delivers GandCrab v4.3 Ransomware to South Korean Users
By Donald Castillo
We discovered spam mails abusing EGG (.egg) files to deliver the GandCrab v4.3 ransomware (detected by Trend Micro as Ransom_GANDCRAB.TIAOBHO). EGG is a compressed archive file format (like .zip) that is widely used in South Korea. Additionally, the operators behind the spam mails appear to be specifically going after South Korean users, as evidenced by the use of Hangul in the spam mails’ subject, body, and filename attachment.
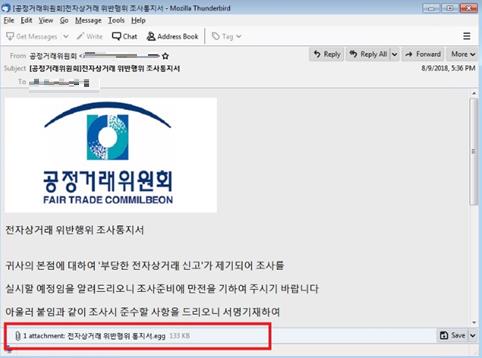
Figure 1. Spam mail sample from the campaign. The subject reads “[Fair Trade Commission] Notice of Investigation of Violation of E-Commerce Transaction” in English.
The spam mail is under the guise of an investigation on an “e-commerce transaction” violation. In English, an excerpt from the email body roughly translates to “'Unfair e-commerce notification' has been filed against your head office, I will let you know that I am going to do it.” Meanwhile, the attached EGG file is named “Notification of e-commerce violation.” It’s important to note that files in EGG format can only be decompressed by ALZip.
Infection chain
We first observed the spam mails on August 7, 2018. In our analysis of the samples, the attached EGG (TROJ_GANDCRAB.TICABAK) contains three files: two shortcut .lnk files (LNK_GANDCRAB.E) that are disguised to appear as documents, and an .exe file that will disappear once the user decompresses the EGG file. Within the .lnk files, “VenusLocker_korean.exe” is inscribed, which could mean that the VenusLocker group was behind the distribution of spam mails.
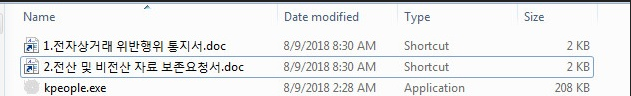
Figure 2. Content of the EGG file
If the user was tricked into decompressing the EGG file and subsequently opens either of the two .doc-disguised .lnk files, the hidden file, which is actually the GandCrab malware, executes. Upon connecting to its C&C server, the GandCrab v4.3 ransomware will encrypt files in the infected machine.
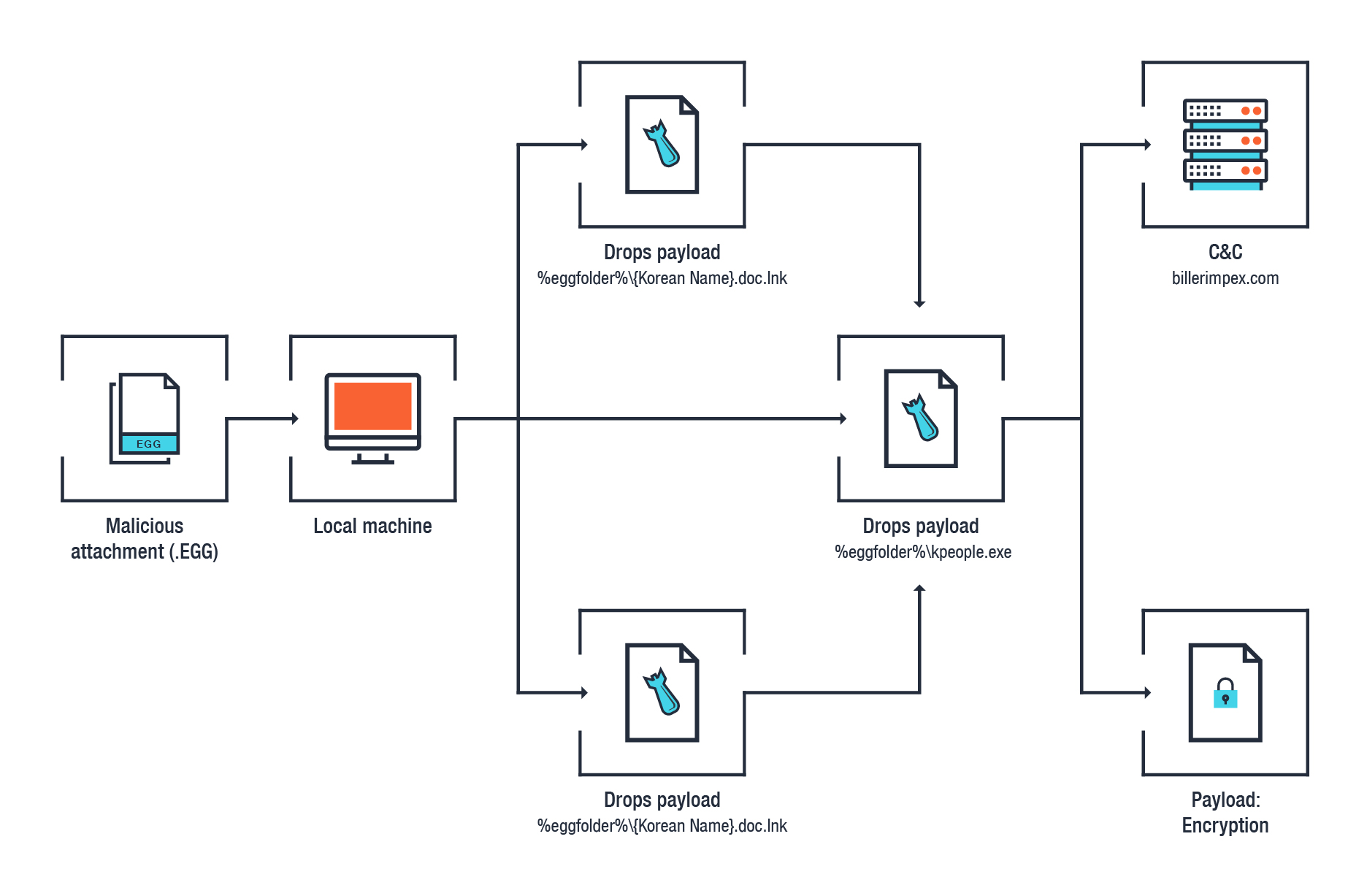
Figure 3. Infection chain
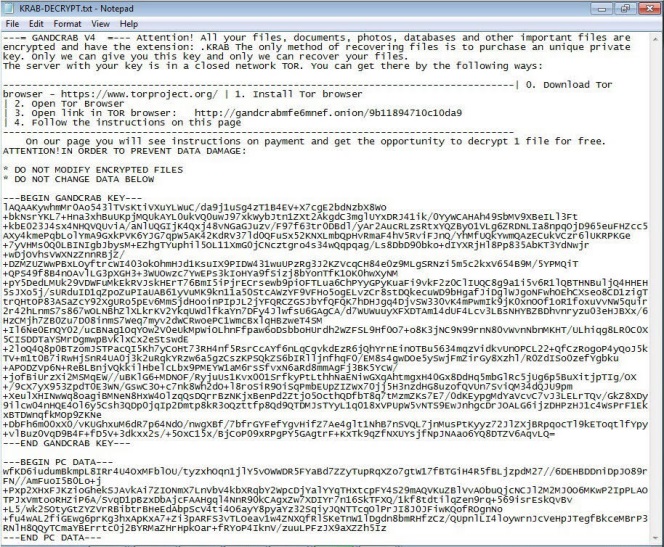
Figure 4. GandCrab v4.3 ransom note
Defending against GandCrab ransomware
Data from Trend Micro shows that GandCrab was the second-highest detected ransomware family globally from March to July 2018. Users and enterprises can adopt these best practices to eliminate the risk of infection by this increasingly pervasive ransomware.
In addition, Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. It features high-fidelity machine learning to secure the gateway and endpoint data and applications, and protects physical, virtual, and cloud workloads. With capabilities like web/URL filtering, behavioral analysis, and custom sandboxing, XGen™ protects against today’s purpose-built threats that bypass traditional controls, exploit known, unknown, or undisclosed vulnerabilities, and steal or encrypt personally-identifiable data. Smart, optimized, and connected, XGen™ powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise (IoCs)
- LNK_GANDCRAB.E (SHA256: 9d932a98c37b9a5454d3ba32596ef0292f55d3f7b3f9831a39df526ad1e686aa)
- Ransom_GANDCRAB.TIAOBHO (SHA256: 8163602357b51402b8e34b385b0228ac4a603e19c6c8006e1c7a7a8099450742)
- TROJ_GANDCRAB.TICABAK (SHA256: f6013b930287d6fdb7d1d403396e4362e34a8d70192ba97b1f35ad97f99552c0)
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One