US$100 – 300 billion: That's the estimated losses that financial institutions can potentially incur annually from cyberattacks. Despite the staggering amount, it’s unsurprising — over the past three years, several banks suffered $87 million in combined losses from attacks that compromised their SWIFT (Society for Worldwide Interbank Financial Telecommunication) infrastructures. That’s just the tip of the iceberg: A single cybercriminal group siphoned $1.2 billion from over 100 financial institutions in 40 countries before its leader was arrested in 2018.
Cyberattacks can undermine the integrity of a financial organization’s underlying infrastructures as well as the systems that drive its operations. The past two years showed this, with attacks that were more persistent, elaborate, and far-reaching. Attackers are seeking low-hanging fruits, fueled by previous high-profile attacks, heightened consumer awareness on breaches, and constantly improving security mechanisms protecting sensitive credentials.
Our continued forays into the cybercriminal underground allowed us to see how these tactics and techniques changed over the years. What cybersecurity blind spots are they capitalizing on? What are their real-world implications? What can users and organizations to do defend against them?
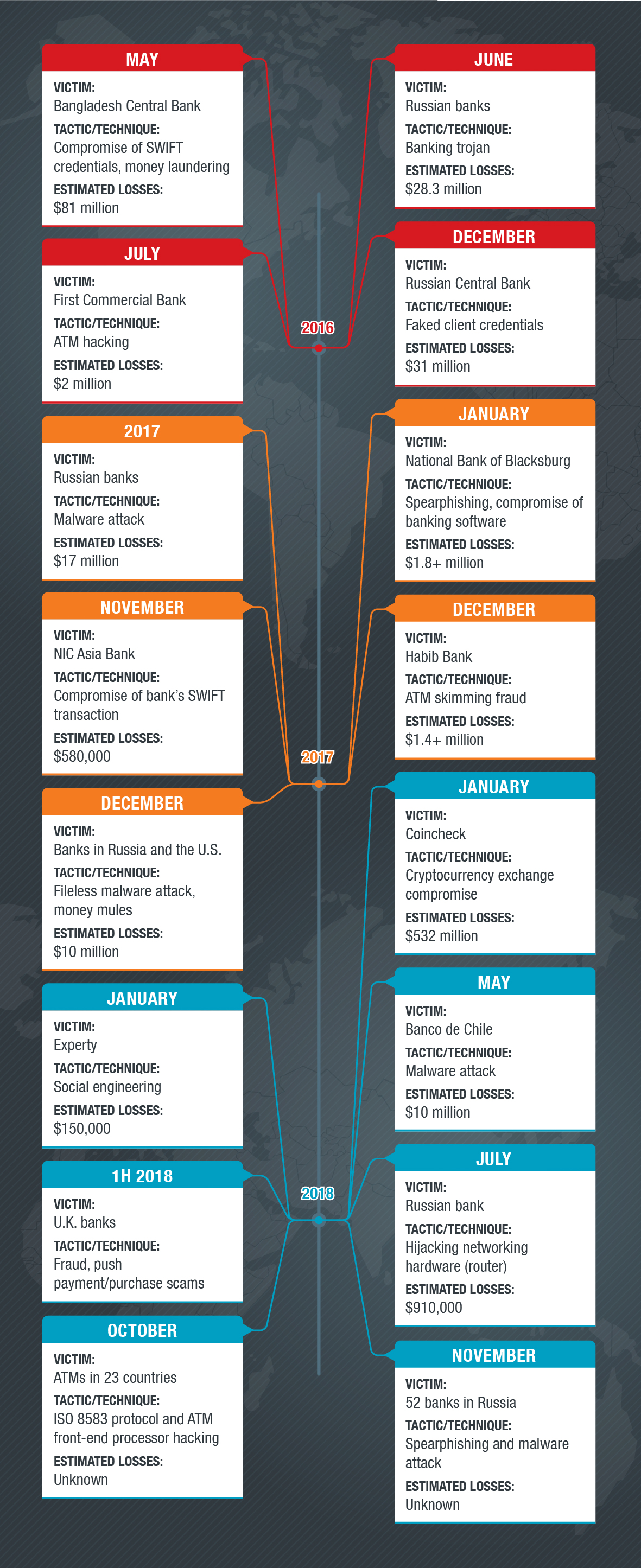
A timeline of most notable cyberattacks on financial institutions
Shifting Tactics and Techniques
Financially motivated attackers traditionally targeted bank customers, but some, like the Lurk cybercriminal group, shifted their attention to large business organizations’ employees. These attacks commonly went after workers within financial departments, targeting accountants and bank employees. Cybercriminals realized that they can steal money not only by compromising banking accounts, but by also targeting the bank’s infrastructure itself or tampering with payment documents and systems. Telecommunication networks and banking infrastructures are seen as lucrative targets because it's essentially where the money is. Attacking them can entail targeting ATMs, SWIFT networks and payment gateways, card processing systems, and similar facilities. For instance, attackers could have the capability to manipulate a bank customer’s digital information, but simply lack the ability to forge a legitimate paper trail, which could be fabricated, for example, by a cooperating insider.
Our research also saw instances of criminal groups attempting to bribe individual banking employees into creating money exfiltration and money laundering schemes. In one concrete instance, we saw an attempt to create a seemingly legitimate charity organization, with bank accounts and a legitimate-looking website. The attackers used this organization's bank accounts to siphon money from compromised bank accounts; the charity cover story gave them sufficient time to wire and cash out the stolen funds.
Telecommunication companies play an important role in the finance industry, which also makes them ideal targets. Compromising telecommunication network infrastructures presents another moneymaking opportunity — from money laundering and premium SMS number subscriptions to SMS rerouting and hijacking. Banks often use mobile devices as a second-factor authentication mechanism or a means to deliver a one-time password (OTP) to their customers. It’s no surprise that we’ve also observed increased interest in telecommunication networks in the cybercriminal underground.
An ad in the underground peddling access to a telecommunication network’s signaling system
Social engineering attacks, also known as “SIM Jacking” has become very widespread. In these attacks, the attackers identify the phone numbers of bank customers whose accounts they have compromised. They then pretend to be the telecommunication company's subscriber, report that they lost their SIM card, and trick the telecom provider into reissuing the SIM card for the reported number. The attackers then use the reissued SIM card to authorize the monetary transaction and steal the customer’s money. A variation of this attack involving temporal rerouting of the phone number also has also been observed. These attacks have been on the rise in recent years, with a massive number of incidents being reported in Russia, Eastern Europe, and North America.
Attacks on bank customers
Targeting users/customers can involve the use of different techniques. The attackers combine and take cues from old (but effective) phishing techniques such as the FakeSpy Android banking trojan. Some are constantly honed, adding features that can automate the exfiltration of stolen data and funds. A banking malware can do this by using an automatic transfer system (ATS) engine, which allows the use of a web injection script, also known as an inject, to automatically initiate fund transfers and bypass authentication mechanisms.
These browser injects are versatile. Attackers can use them to bypass a bank’s security controls, force users into installing malicious components on their mobile devices, circumvent authentication mechanisms, or exfiltrate payment data such as credit card information. They can also be used for social engineering attacks to steal personally identifiable information (PII) — date of birth, mother’s maiden name, and first pet’s name, among others — or auto-transfer funds to attacker-controlled banking accounts (also known as money mule accounts).
Code injections are inserted into a banking website or its components (like JavaScript libraries or hidden iframes). Unfortunately, an everyday user could unwittingly trust what a compromised website displays without realizing that the actual web page has been tampered with.
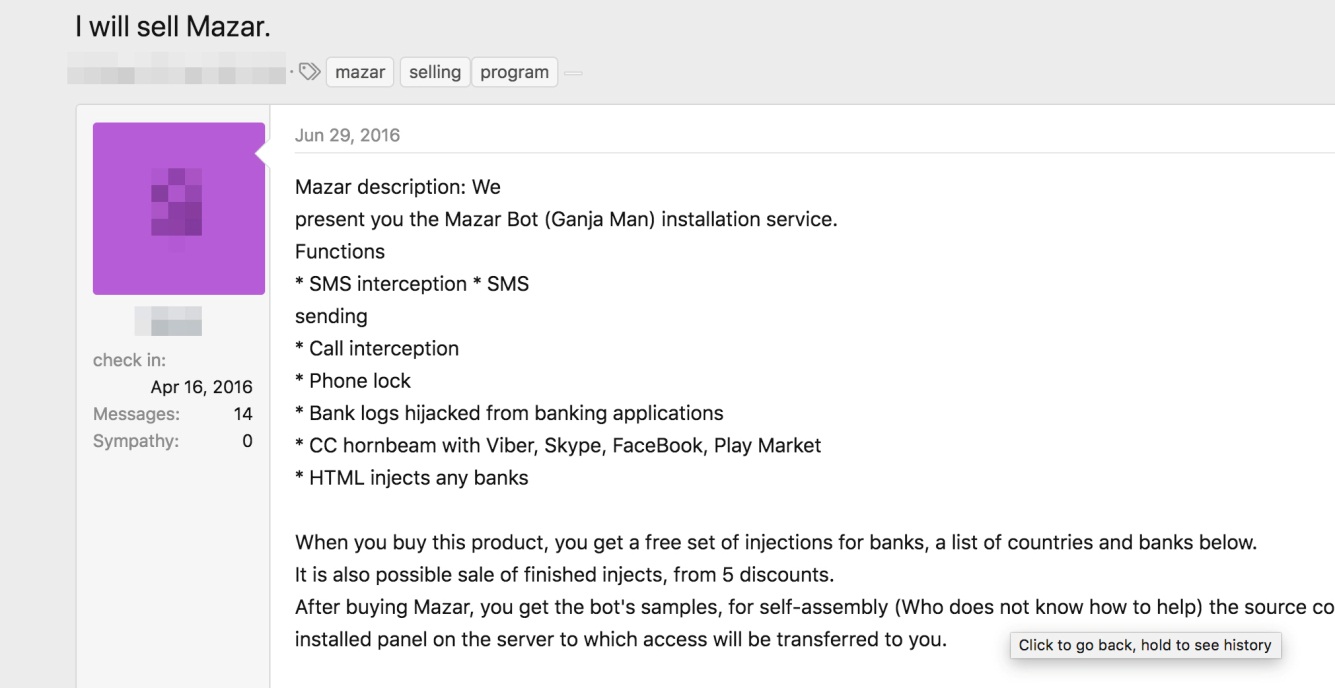
An advertisement in the underground selling the Mazar Bot, which is supposedly capable of HTML injections tailored to applications and websites of banks in Canada, France, Austria, Poland, Germany, Australia, New Zealand, Spain, Netherlands, Singapore, Turkey, and the U.S.
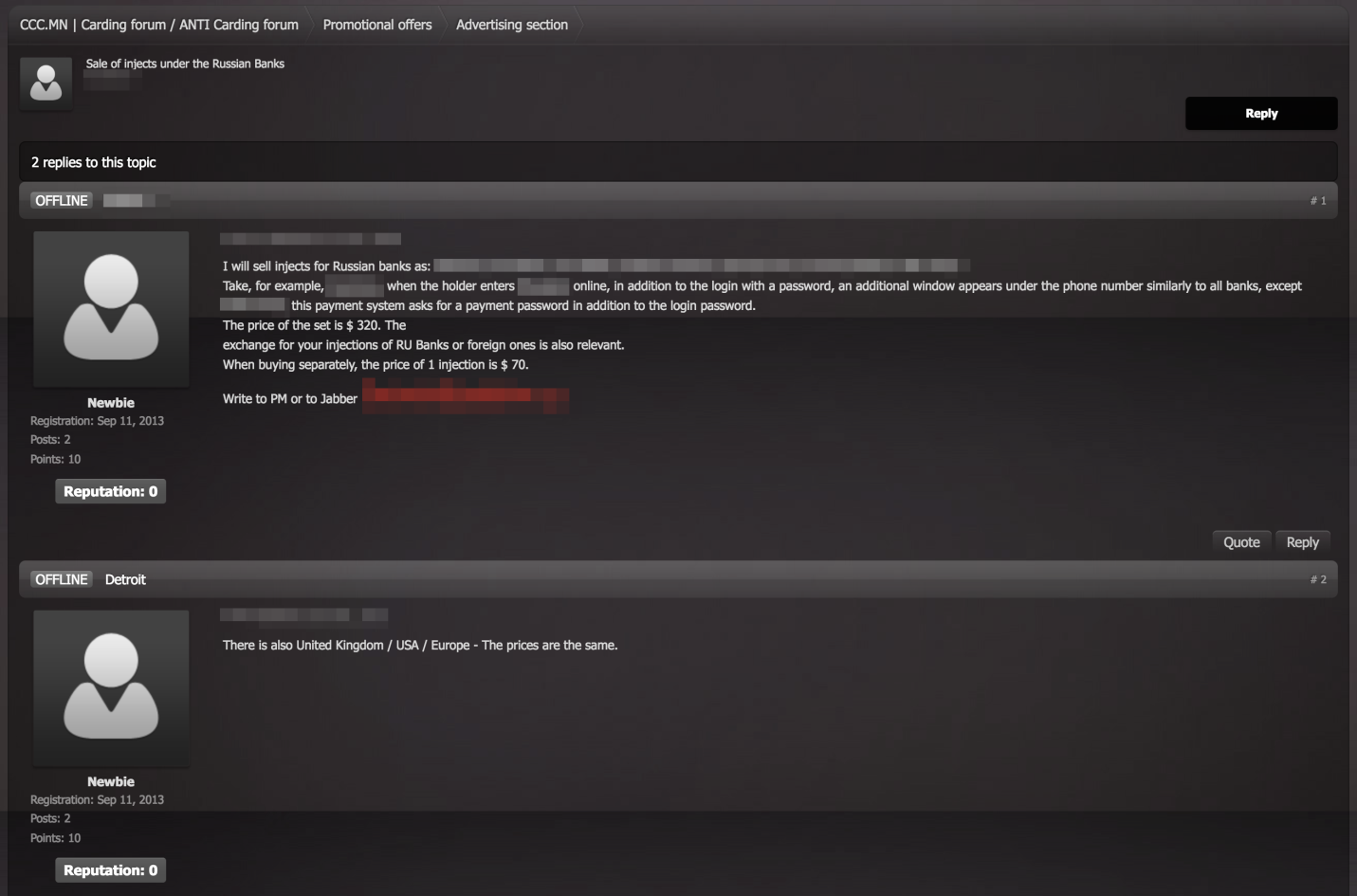
An advertisement in the underground peddling banking malware bundled with a code injection kit, targeting mainly Russian banks. Banking malware sold in underground forums now often have ATS and code injection features, which are further packaged with customized injects for different/regional banks.
Attacks on infrastructures
Attackers also target network infrastructures. Unfortunately, many banking system components, such as internal banking systems or point-of-sale (PoS) interfaces, are often left exposed on the internet, making them more likely to be targeted by opportunistic attackers.
While they are not key targets, we’ve seen multiple malware campaigns with domain name system-changing (DNS) capabilities using them as springboards to get to their actual targets. User network equipment is tampered at scale, which, in turn, would redirect users to a hacker-controlled DNS server. It works as a typical resolver so users would not notice the compromise. When users try to access a targeted banking website, the attacker-controlled DNS server would redirect them to a system they control. This exposes users to phishing and man-in-the-middle attacks.
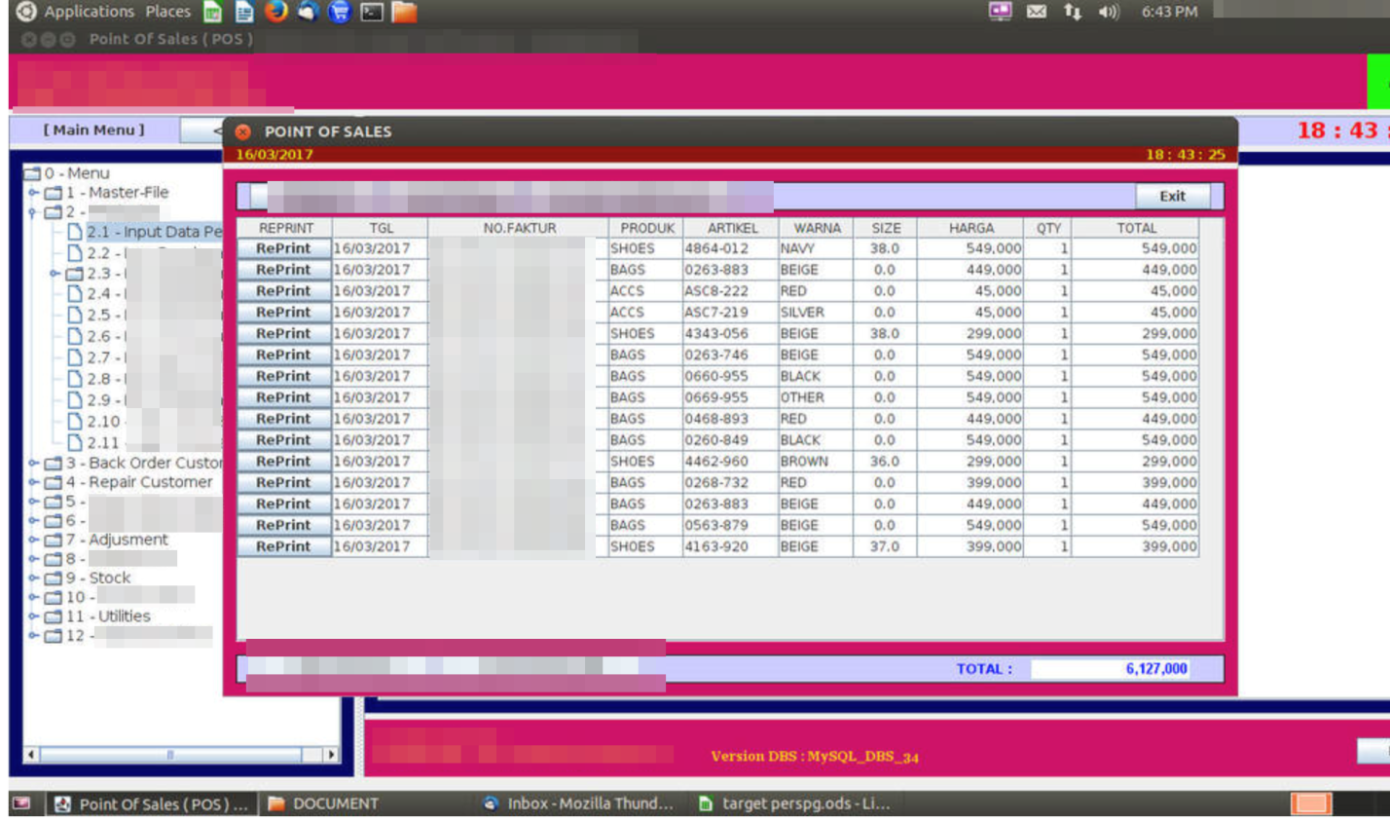
Examples of a PoS system (top) and banking system (bottom) exposed to the internet
Attacks on third-party companies servicing banks
To access a targeted banking organization, attackers need to get down to its proverbial brass tacks. They often do so by attacking their target’s weaker links. Social engineering attacks are their bread and butter: Hackers, for instance, need to learn about the organization’s actual employees, possibly including their positions and topics of interest. Appearing to be legitimate helps the weaponized documents they send to these employees slip past suspicion.
A way to gather employee information is to compromise companies servicing these organizations, such as third-party vendors servicing ATM equipment, or hacking into topical forums or distribution mailing lists. The Lurk group, for instance, compromised an online forum for accountants to get to their actual targets. Attackers could also obtain information on potential targets by analyzing data on already compromised machines. Groups such as Cobalt and Silence are also known to employ this technique.
In fact, data from our Smart Protection Network™ (SPN) reveals that Silence targeted financial organizations in Russia, Belarus, and even Vietnam. Cobalt, on the other hand, is still active, especially within the Commonwealth of Independent States (former USSR countries) and Eastern European countries such as Bulgaria.
Cobalt is also known to compromise a bank or financial organization’s supply chain to ultimately access its target’s IT/online perimeter. Using SPN telemetry, we’ve identified Cobalt attacking companies like software integrators, financial services firms, and other banks to get to their bank of interest. In 2018, for instance, we observed a spearphishing campaign against a high-profile system/software integrator in Russia that was used as jumping-off point to target domestic financial organizations.
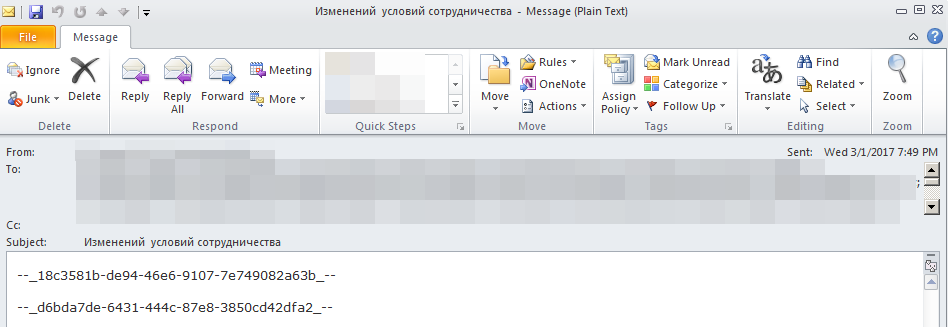
A phishing email sent by the Cobalt group using a servicing company's email address
>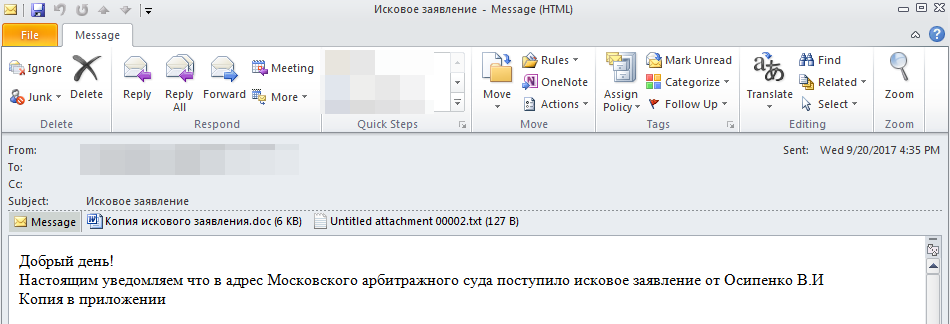
Example of a spearphishing email sent to a company servicing ATMs
Attacks on banking infrastructures
Directly attacking the bank’s IT perimeter is uncommon as attackers usually use phishing to first gain a foothold into their target. Attackers go to great lengths when preparing phishing campaigns. For example, in each campaign, they would register a domain name resembling a company that their targeted organization has a relationship with or expects to receive emails from. The subject and content of the phishing email would also be related. One of the techniques that helps us proactively detect these campaigns is to analyze newly registered domains for keywords of interest and then monitor the domains’ appearance in the email traffic.
Watering hole techniques are also commonly used. Exploit code is planted into compromised websites that the targeted organization's employees frequently visit. Interestingly, we’ve observed timing dependencies used in this technique. For example, activities increase at a certain time of the day, like lunchtime, when users would likely have the time to browse the internet, or in late afternoon, when users tend to be less attentive to suspicious emails.
Timeline of watering hole attacks we observed from Cobalt (top) and Silence (bottom) groups showing activity spikes during certain times of the day. We observed Silence’s campaign on December 27, 2018, and Cobalt’s on January 23 and 24, 2019. Note: Data from Trend Micro™ Smart Protection Network™
While the ultimate goal is to steal money (either in electronic or paper form), we’ve also seen attacks motivated by theft of sensitive or confidential data, blackmail, and stock or online currency trading manipulation, among others. Attackers also exploit vulnerabilities in ATM and PoS infrastructures to pilfer or launder money, such as illegally collecting payments from stolen credit cards by running charges through PoS terminals.
Different groups use different techniques. The Lazarus group, for instance, is notorious for tampering with ATM switches to steal funds from banks, while others prefer more traditional methods. More recently, Lazarus reportedly stole US$13.5 million by hacking into a bank’s ATM and SWIFT infrastructures.
The attack demonstrated a good understanding of SWIFT’s platform by attempting a fraudulent transfer. It also showed the attackers’ knowledge of banking systems by tampering with the ISO 8583 protocol communication, which is an international standard used for defining financial transactions. Attackers hacked into the ATM’s front-end processor, which handles initial processing and communications between input devices and the host computer, and tampered with ISO 8583 software by injecting code that produced fraudulent responses to requests from ATM machines. The United States Computer Emergency Readiness Team (US-CERT) accordingly issued an advisory following this attack, which was nicknamed FASTCash.
Lateral Movement and Monetization
Once attackers establish a foothold, they often attempt to harvest credentials from compromised machines (usually via ready-made tools) and spread laterally, such as accessing domain controllers and card processing segments.
How they monetize the attack influences how much they would have to compromise their target’s resources. An example is manipulating account balances and ATM withdrawal limits then dispatching money mules to take out stolen cash. This tactic is so common that threat actors actually seek accomplices on cybercriminal forums.
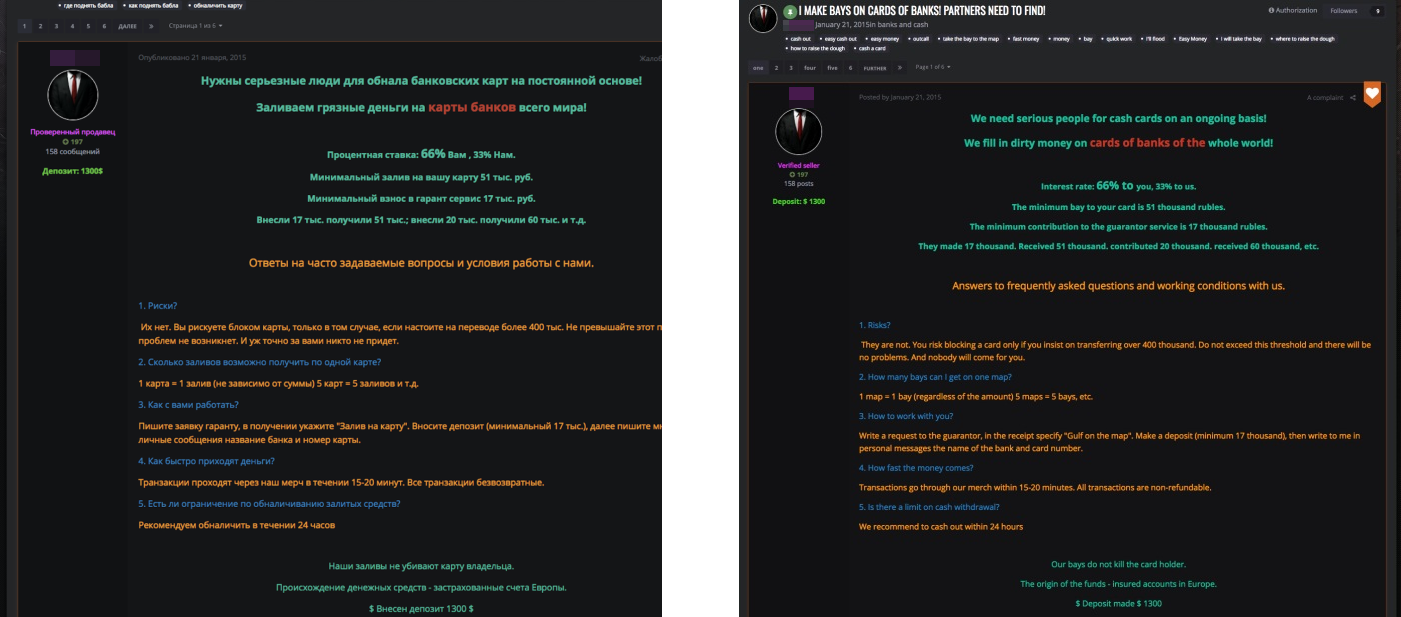
An advertisement (original post, left) in hxxp://vor[.]nz for money mules (Google-translated, right)
Monetization via ATM withdrawals is also common. Once a target bank is compromised, for instance, the hardware they used is identified and manipulated. In fact, there are also cybercriminal forum posts and advertisements seeking “operators” of NCR 6625 (a specific ATM model). We also saw an instance where an account of a fake charity organization is set up at the bank. Unauthorized transactions were then made from banking accounts with balances exceeding the cap — with attackers ultimately making off with US$50,000.
These attacks aren’t limited to Russia or Russian-speaking countries. For instance, there are also underground forum posts looking for money mules who could be commissioned to cash out money from SWIFT transactions in China.
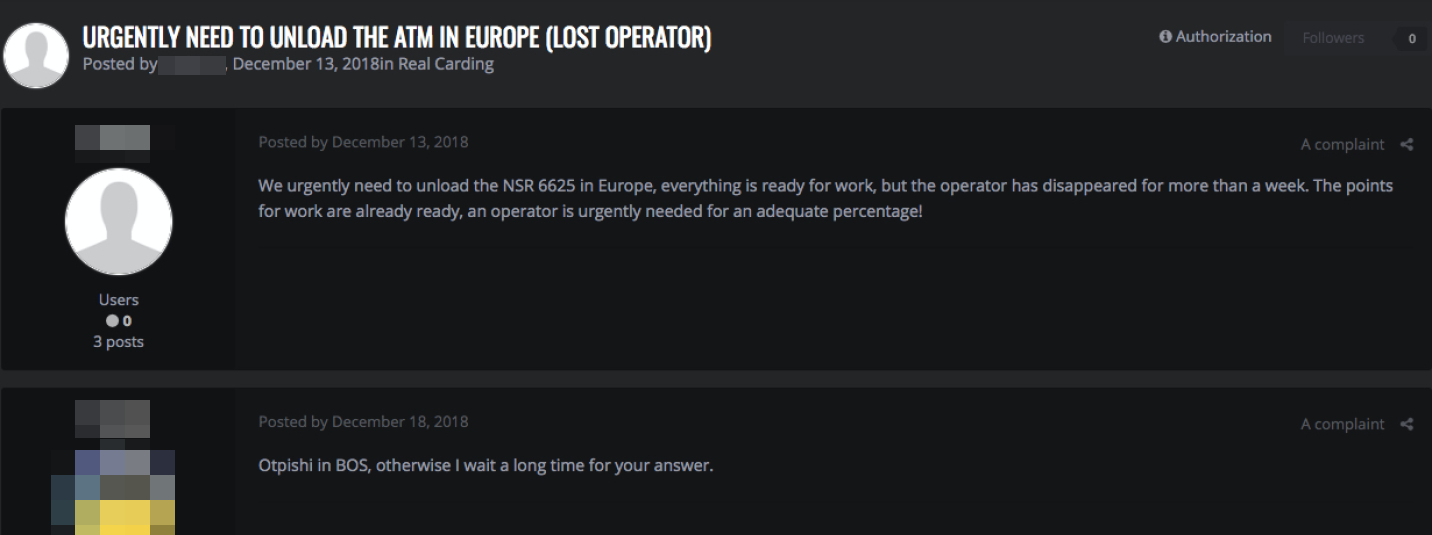
A cybercriminal forum post seeking an operator of a cash dispenser
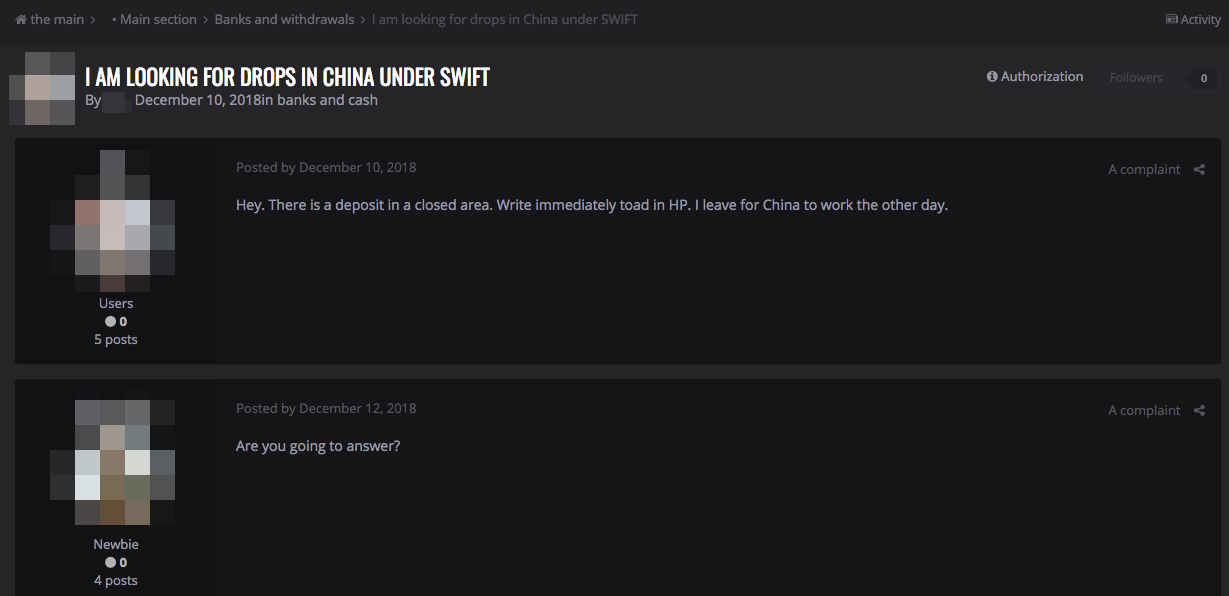
A cybercriminal forum post seeking a money mule in China
Staying Ahead of Threats
Financial organizations don’t just contend with an attack's adverse impact to their bottom line. They also have to deal with the marred reputation, reduced customer trust, and indemnities that follow. And with the plethora of techniques we’ve seen leveled against financial organizations, they are no longer just targets of threat actors using complex attack chains. With a modus as straightforward as sending a phishing email, they’ve also become targets of opportunistic cybercriminals.
The diversity of their attacks means organizations need to be multifaceted, too — being able to see, monitor, and filter what’s happening in — and going through — the network and the systems connected to it. This is particularly true for the financial industry that has stringent data protection (i.e., compliance with EU General Data Protection and Regulation) and patching requirements, and the hefty fines that can be incurred from infringing them.
Security controls at each layer of the organization’s online perimeters mitigate risks to a bank’s physical and virtual servers and network segments, ports, and protocols to the endpoints that process transactions. Defense in depth also provides visibility on the infrastructures needed to respond proactively to attacks. An environment where threats are isolated — particularly from email gateways where many of these kinds of attacks start — helps monitor and filter email traffic and weed out anomalous emails. Network segmentation and data classification mitigates risks of lateral movement and further breach. Security mechanisms like virtual patching and intrusion prevention systems proactively bridge security gaps without causing disruptions and additional overhead to operations and business processes. End users, particularly customers and employees, also need to be equally proactive.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 MQTT and M2M: Do You Know Who Owns Your Machine’s Data?
MQTT and M2M: Do You Know Who Owns Your Machine’s Data? Building Resilience: 2024 Security Predictions for the Cloud
Building Resilience: 2024 Security Predictions for the Cloud Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023 Mitigating the Threat of Sidecar Container Injection
Mitigating the Threat of Sidecar Container Injection