
The term ‘incident response’ refers to the strategic, standardized set of policies, procedures, and tools an enterprise uses to detect and resolve security events.
Table of Contents
Incident response (IR), sometimes referred to as cybersecurity incident response, is about preparing for, identifying, containing, and resolving any security incidents such as a cyberattack or a data breach. IR policies, plans, and technologies are designed to quickly detect threats and attacks, prevent or limit damage, provide effective and timely remediation, minimize downtime and costs, and reduce the risk of future events.

An important element of proactive security, the aim of IR is to maintain business continuity—both in terms of short-term operations and long-term goals. The idea is to identify incidents and limit the damage they cause by restoring business operations quickly—minimizing revenue losses as well as the costs of downtime and remediation efforts.
IR also helps organizations comply with regulatory or legal requirements for their industry, such as Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), or the EU’s General Data Protection Regulation (GDPR). This prevents the organization being subject to fines or other legal liabilities.
Overview of incident response
To understand incident response, it’s important to clearly define what’s meant by “incident.” An incident is any physical or digital event that endangers an organization’s security or compromises the integrity or confidentiality of the data or systems.
Incidents may be caused by accidental or unforeseen situations such as operational outages or natural disasters, or by deliberate cyberattacks such as phishing schemes, malware, denial-of-service (DoS) attacks, man-in-the-middle (MitM) attacks, ransomware, supply chain attacks, insider threats, privilege escalation attacks, password attacks, and web application attacks.
Incident response versus incident management
IR is part of the larger function of incident management. Incident management refers to an organization’s overall approach to dealing with a serious security event, and involves internal and external stakeholders from the executive team, HR, legal, communications and PR, and IT. Incident response is more focused, referring to the organization’s technical handling of a cybersecurity event.
Importance of incident response planning
With the rise in criminal resourcefulness on one side and the potential for human error on the other, cyberattacks have become unavoidable. The potential negative fallouts from security events are far reaching, making incident response a crucial part of an organization’s cybersecurity platform. Cyber events cannot be viewed as just technical problems—they impact the whole organization, from internal operations to business-critical computing systems, to confidential customer or public information.
Benefits of effective incident response
Being able to respond effectively to cyber incidents allows an organization to:
- Limit the disruptiveness of a cyber incident to enterprise operations and productivity while minimizing the cost of containment and remediation
- Limit data losses or the length of time data is exposed, and better protect sensitive data
- Restore operations more quickly
- Meet regulatory demands by showing vigorous processes, accountability, and due diligence
- Increase security resilience and their ability to respond to future events
- Preserve the organization’s reputation and relationship with customers, partners, and other stakeholders
Common challenges without an IR plan
The lack of a predefined, detailed IR approach affects almost every aspect of the business. Security and IT teams are forced to scramble in the midst of a crisis, possibly without the necessary technology or executive support to deal effectively with a cyberattack. A disorganized, uncoordinated response also gives cyber criminals further opportunities to exploit the organization, widening the negative impacts of the attack.
The business suffers internally due to downtime and service disruption and externally with damage to its brand and external stakeholder relations. These disruptions translate into higher costs to the business, not to mention legal or regulatory fines that might be levied.
What is an incident response plan?
One of the key components of IR is an incident response plan (IRP), which specifies the procedures, technologies, roles and responsibilities for detecting, containing, and resolving a cybersecurity incident.
An IR plan needs to support an organization’s priorities, operational needs, and constraints, and be tailored to an acceptable level of risk. It’s essential to see IR policies as evergreen. Just as cybersecurity is constantly evolving, so are organizational needs and operations, so the IR plan can’t be a “set it and forget it” document. It must be regularly reviewed, vetted, and tested.
A complete IR plan will include:
- Procedures for incident identification and classification
- Specified security solutions: software, hardware and other technologies
- A business continuity plan: how the organization will reestablish critical systems in the wake of an incident
- Detailed steps for each phase of the incident response lifecycle (see below)
- Strategies for containment, eradication, and restoration
- Roles and responsibilities for each phase of the process, including workflows
- A communications plan for informing internal and external stakeholders about an incident, breach, or data loss, including law enforcement
- Directions on collection and documentation of relevant metrics for post-incident reporting

Many organizations find it helpful to create an incident response playbook. Whereas an IR plan is the overarching policy, a playbook details the standardized steps and procedures, roles and responsibilities for each phase of the incident response lifecycle. It ensures that incident response is effective, efficient, and consistent because everyone is following the same workflow.
An IR playbook can also be used in simulations and training to prepare the team for a hypothetical event, and may include:
- Runbooks
- Checklists
- Templates
- Training exercises
- Security attack scenarios
- Simulation drills
The incident response lifecycle
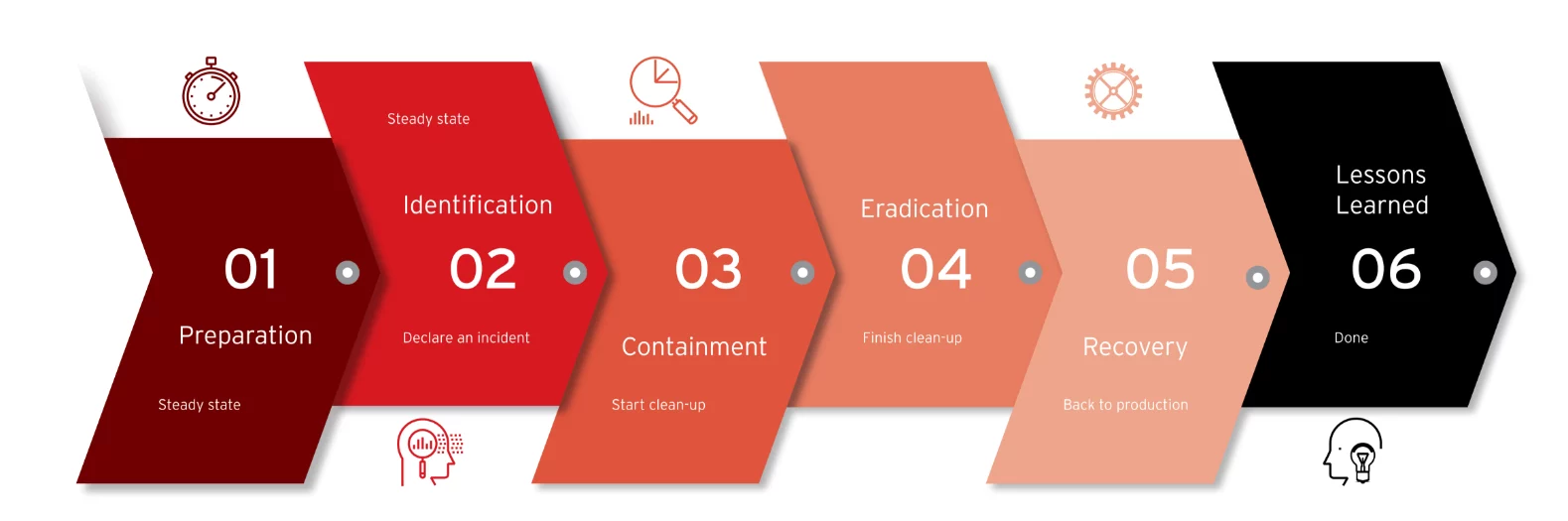
The National Institute of Standards and Technology (NIST) and the SANS Institute have created widely accepted models defining the various phases of IR. The six phases proposed by the SANS Institute are detailed below.
1. Preparation
This is the process of creating, reviewing, or refining IR policies and procedures, and should be seen as a continuous effort. Regular risk assessment should be undertaken so the organization can prioritize incident responses by system, data, and type of incident severity. The goal is to decide on the most effective procedures, technology and methodologies to detect, minimize, and recover from an incident. This should include a reliable process for regularly creating backups which will be needed when it comes to recovery. This is also the phase in which to run simulations and scenarios. Tools like playbooks and templates can then be created for the most effective response protocols when it comes to a real attack.
2. Identification
Also known as detection, this stage involves the use of technologies and methodologies to pick up on the fact that a security event such as a cyberattack has occurred. There are many security solutions available to monitor systems and data in real time, automate alerts, and automate responses. Often organizations use a security information and event management (SIEM) platform. Data from tools like device logs, intrusion detection systems, or firewalls is used to find suspicious activity. Alerts are then sent to the incident response team who analyse and triage them, identifying indicators of compromise (IoC) and eliminating false positives. In the presence of a security incident, the IR plan comes into play with the appropriate personnel being notified and the communications plan followed.
3. Containment
Containment is about stopping an identified incident or attack from continuing to damage systems, data, or the business. Most immediately, this involves isolating affected systems so the attack can’t spread. Long-term containment measures also need to be put into place by setting up stronger security controls over unaffected systems, such as enacting security patches or updates. It’s also important to collect and retain forensic evidence of the attack for the post-incident analysis phase.
4. Eradication
In this phase, the threat is completely removed. This might mean ejecting an attacker or removing malware. It’s important to make sure there are no traces of the attack or breach so that data and/or systems can be fully restored.
5. Recovery
This is about reinstating systems, data, and operations so the business can function smoothly again. The team will restore from the last clean copy of data and bring updated replacement systems online. Once restored, the systems must be tested, monitored, and validated.
6. Lessons learned
Post-incident review is the final phase: the team examines the evidence gathered during the incident and the way the event was managed. The organization may need to involve law enforcement during the investigation. Overall, the review phase is about recognizing the strengths and weaknesses of the organization’s incident response, and determining opportunities for improvement. In the case of an attack, it’s important to understand the root cause and how the attacker was able to breach the network. As part of this analysis, the team might consider data such as mean time to detect, mean time to identify, mean time to respond, mean time to contain, and total cost.
Post-incident analysis is a crucial part of IR because it enables an organization to strengthen their security strategy in order to reduce the likelihood of a similar event reoccurring. It also gives the team the data they need to update their incident response plan, and to make any upgrades or modifications to their tools, systems, or processes.
Incident response roles and responsibilities
Organizations need more than just incident response plans: they also need dedicated teams to implement them. This team is often referred to as the computer security incident response team (CSIRT), cyber incident response team (CIRT), or computer emergency response team (CERT). The members and size may differ depending on the organization, but it is usually a cross-functional team with a range of backgrounds and skills.
Most IR teams include an executive member (CSO or CISO), security and IT staff and analysts, leaders from human resources, legal, communications or public relations, and external stakeholders such as consultants, MSPs, vendors, or partners.
The role of the team is to provide leadership, investigation, communications, documentation, and legal representation. It establishes policies and procedures, creates the IR plan, enacts security best practices, provides support for all incident response actions, and trains end users in cybersecurity best practices.
Key players on an incident response team include:
- A response manager or incident commander who supervises the whole IR process, manages the team, and makes sure procedures are followed.
- An executive to lead critical decision-making.
- A well-rounded technical team potentially including an incident response coordinator, security analysts, incident responders, threat researchers and forensic analysts. These roles and responsibilities will be detailed in the IRP and correspond with the six phases of incident response.
- DevOps specialists to review and analyze events, identify root causes, and suggest remediation actions.
- Operations or IT staff with expertise in network infrastructure, systems administration, and application development to suggest technology solutions and ensure operations run smoothly.
- Legal advisors to be aware of and comment on legal implications, ensuring the IR plan complies with regulatory or legal obligations.

Training and skill development for incident response professionals
Given the strategic importance of IR, the frequency of cyberattacks, and the ever-changing nature of cybersecurity, it’s crucial to provide regular training to the members of the incident response team. This might include drills based on previous events or simulated scenarios. It’s important that these scenarios cover a wide range of attack vectors, such as ransomware, malicious insiders, and brute-force attacks. Many organizations run tabletop exercise which include hands-on tasks and enactment of the phases of the IR plan to pinpoint any weaknesses or opportunities for improvement.
Technologies supporting incident response
Several technologies help to identify threats, streamline data, and automate responses.
Some of the most common include:
- ASM (attack surface management): automates continual detection, monitoring, assessment, and remediation of vulnerabilities across the assets in an organization’s attack surface.
- EDR (endpoint detection and response): automatically defends users, endpoint devices and IT assets against cyberthreats that breach antivirus software and other endpoint security tools.
- SIEM (security information and event management): pulls together and correlates security event data from internal security tools and devices on the network.
- SOAR (security orchestration, automation and response): allows teams to determine playbooks and workflows to coordinate security operations and tools in response to security incidents.
- UEBA (user and entity behavior analytics): detects abnormal or suspicious user and device behavior.
- XDR (extended detection and response): consolidates security tools, control points, data and telemetry sources and analytics across a hybrid environment.
Role of automation in incident response
Given the number of alerts created by these monitoring technologies, most teams—however expert—don’t have the time to analyze and deal with them all. This could result in serious incidents being missed or noticed too late. This is where automation comes in.
Automation can:
- Detect incidents and perform threat hunting
- Create tickets and alerts
- Analyze and prioritize alerts
- Streamline data
- Execute incident response tasks and processes
- Undertake case management
- Create reports
These capabilities reduce alert fatigue and enable team members to direct their efforts to the most strategic endeavours. Automation also enables teams to respond to and resolve incidents faster, putting the organization in a stronger position, minimizing damage and downtime, and saving money.
Future trends in incident response technologies
The proliferation of cloud technology has introduced new challenges to the incident response process. With more and more of an organization’s data and applications stored on the cloud, it can be difficult to accurately and quickly detect a security incident and investigate it fully. This means organizations need to include cloud in their IR plan, potentially adopting new technologies like a cloud-native application protection platform (CNAPP), learning new skills, or collaborating with a cloud service provider (CSP).
AI, with its ability to process vast amounts of data quickly, is making it possible to more speedily and accurately identify suspicious behaviors or patterns. Generative AI can even inspect data in real time, interrogate the context of an incident, and create responses based on its analysis. These insights reduce human labor time and help to develop more proactive responses. The data produced by AI can also help determine the root cause of incidents, predict future threats, and develop training scenarios.
What Legal and Regulatory Factors Should You Consider?
Incident response must align with key industry regulations, including:
GDPR (General Data Protection Regulation): Requires breach reporting within 72 hours.
NIST Cybersecurity Framework: Provides best practices for cybersecurity risk management.
- HIPAA (Health Insurance Portability and Accountability Act): Mandates the protection of healthcare data.
Real-World Incident Response Scenarios
Ransomware Attack Disrupts City Services
A city in California was hit by a ransomware attack that took down phone lines and financial data systems, forcing them offline. This disruption affected essential services, leaving the city scrambling to restore operations.
You can read more about it here.
What can we learn from this?
Public sector organisations are prime ransomware targets.
A solid incident response plan can mean the difference between quick recovery and prolonged downtime and investing in proactive cybersecurity measures is crucial to preventing similar incidents.
How Can You Stay Ahead?
Cyber threats aren’t going away, but a well-structured incident response plan ensures resilience and quick recovery. You must continuously refine your strategy, invest in advanced security tools, and train your teams to stay ahead of evolving threats.
We structure our Incident Response engagements along the SANS incident response model, an industry standard proven to be fast and decisive. Our team will assist you throughout the process to:
STOP the ongoing attack in its tracks
START rebuilding your production environment by localizing unaffected assets and backups
HARDEN your network, servers, and endpoint defenses to protect against future attacks
Incident Response with Trend Vision One
Security is our mission. We’re laser-focused on protecting your clients before, during, and after breaches, harnessing our cybersecurity platform, Trend Vision One™, as well as our threat experts and Breach and Assessment Services. Breaches are costly and time-consuming, but our competitive rate structure is intended to reduce claims and keep your customers happy.
Armed with leading breach response and detection technology and bolstered by our incident response experts, Trend’s Incident Response (IR) team:
- Contains, eradicates, and neutralizes the threat with minimal downtime and provides recommendations to improve future resiliency
- Gains access to telemetry 92% faster than other companies to reduce claims
- Discovers “patient zero” 90% quicker than other solutions with our patented technology to minimize downtime
FAQs
What is Incident Response in Cyber Security?
- Incident response is a structured approach to detect, contain, and recover from cyberattacks, minimizing damage and ensuring business continuity.
Why does Incident Response matter?
- It helps organizations reduce downtime, protect sensitive data, comply with regulations, and respond effectively to increasingly sophisticated cyber threats.
Why do you need an Incident Response Plan (IRP)?
- An IRP provides clear roles, processes, and guidelines to quickly identify, contain, and resolve incidents before they escalate into critical breaches.
What are the 5 Incident Response steps?
- The five key steps are: preparation, identification, containment, eradication, and recovery, followed by continuous learning and improvement.
What is an Incident Response unit?
- An incident response unit is a dedicated team of security professionals that manages, investigates, and mitigates cyber incidents within an organization.
Related Articles
Trend 2025 Cyber Risk Report
From Event to Insight: Unpacking a B2B Business Email Compromise (BEC) Scenario
Understanding the Initial Stages of Web Shell and VPN Threats: An MXDR Analysis
The Forrester Wave™: Enterprise Detection and Response Platforms, Q2 2024
It’s Time to Up-Level Your EDR Solution
Silent Threat: Red Team Tool EDRSilencer Disrupting Endpoint Security Solutions
Modernize Federal Cybersecurity Strategy with FedRAMP
2024 Gartner® Magic Quadrant™ for Endpoint Protection Platforms (EPP)
The Forrester Wave™: Endpoint Security, Q4, 2023