
Data security is the set of policies, technologies, and controls that protect sensitive data from unauthorised access, alteration, loss, or theft, wherever that data lives or moves.
Table of Contents
What Is Data Security?
At its simplest, data security means keeping business and personal information confidential, accurate, and available only to authorised users.
However, modern data security goes beyond locking down one system or channel. It is about understanding what data you have, where it is, who is using it, and how it could be exposed across environments.
A complete data security strategy typically aims to:
Prevent unauthorised access and exfiltration
Detect misuse or anomalous activity quickly
Limit the impact of incidents such as data breaches or data leaks
Support compliance with regulations and contractual obligations
Traditional data loss prevention (DLP) tools focused mainly on blocking obvious outbound transfers. Today, modern data security systems need to keep pace with cloud, remote work, and AI adoption, where data flows across many applications and identities.
Why Data Security Matters Today
If you zoom out across all the telemetry in Trend Micro’s 2025 Cyber Risk Report, one theme stands out: attackers go where the data is.

This research also shows that, even after a year of steady improvement, the average cyber risk index (CRI) across enterprises still sits firmly in “medium risk”, meaning most organisations retain enough unaddressed weaknesses to be attractive targets. While Europe saw the biggest drop in risk (helped by regulations like DORA and the Cyber Resilience Act), the regional CRI remains at a level where data-compromising attacks are likely if exposures are not actively managed.
Overall Top 10 Risky Events
1.
Risky Cloud App Access
2.
Stale Microsoft Entra ID Account
3.
Sandbox Detected Email Threat
4.
On-Premises AD Account with Weak Sign-In Security Policy - Password Expiration Disabled
5.
Advanced Spam Protection - Policy Violation
6.
Data Loss Prevention - Email Violation
7.
Microsoft Entra ID Account with Weak Sign-In Security Policy - MFA Disabled
8.
Microsoft Entra ID Account with Weak Sign-In Security Policy - Password Expiration Disabled
9.
Stale On-Premises AD Account
10.
On-Premises AD Account with Weak Sign-In Security Policy - Password Not Required
(Sorted by most detections, February 2024 - December 2024)
When you break down the top risky events, they are all about where business data now lives and moves:
Risky cloud app access is the single most detected risky event in enterprise environments, driven by rapid SaaS adoption and inconsistent user education. That means sensitive data is routinely moving through apps and services that security teams do not fully control.
Email risk is rising, not falling. Trend Vision One™ Email and Collaboration Protection blocked 57 million high-risk email threats in 2024, up 27% from 45 million in 2023, underlining how phishing, BEC, and malicious attachments continue to be a primary route into data-rich systems.
Cloud misconfigurations are a persistent exposure, with non-compliant access controls and weak security settings in services like Amazon S3 and GCP leaving data stores far more open than intended.
Home and remote networks are also vulnerable. Trend’s home network telemetry still sees brute-force logins and long-patched IoT vulnerabilities being exploited on devices used for remote work, creating new paths to corporate data from outside the traditional perimeter.
At the same time, Trend Micro’s research analysis on data security capabilities reveals that traditional, channel-centric DLP simply can’t keep up. It struggles to see insider movement between sanctioned and unsanctioned tools, sensitive data parked in SaaS or AI/ML datasets, and multi-channel exfiltration campaigns that blend email, cloud, and endpoint activity.
Essentially, most organisations now operate in state where attackers have multiple, well-proven paths to sensitive data across a widening attack surface. Therefore, modern data security is especially crucial to businesses now, because without it, those everyday exposures will continue to translate into real data breaches, regulatory pressure, and direct business impact.
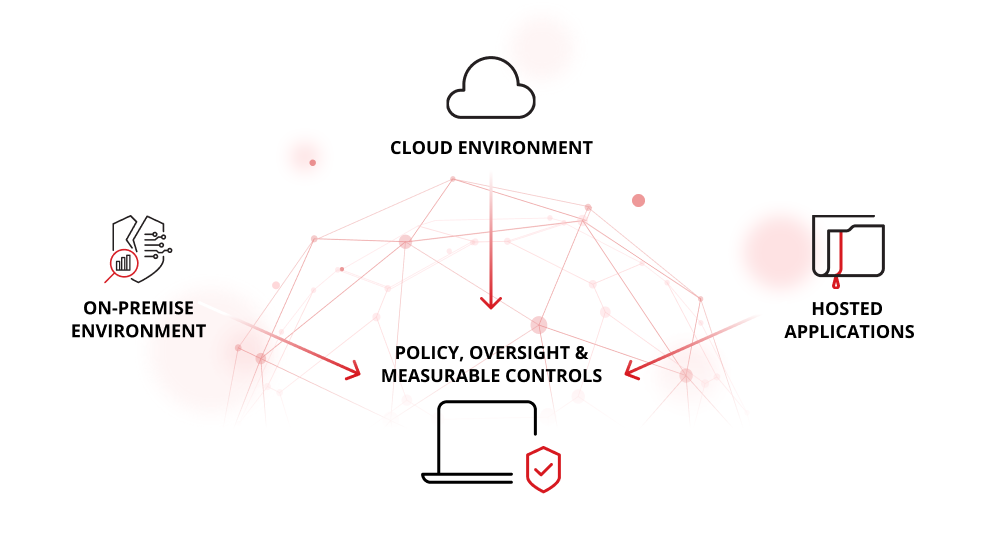
Data security in modern computing
In a world of distributed computing, enterprise operations span on-premises systems, multiple cloud environments, and services delivered “as a service.” Data security must therefore address protecting sensitive data across the full spectrum of environments. Risk-informed organisations recognise that protecting data is not simply a matter of firewalls, but of unified policy, oversight, and measurable controls.
The National Institute of Standards and Technology (NIST) defines the information life cycle as stages including creation, processing, use, storage and disposition, a model that underpins modern data-security strategies (NIST, 2016). The same research shows that knowing how data flows and where controls apply is foundational to effective protection.
Governments estimate the economic impact of malicious cyber activity at between US $57 billion and US $109 billion in a single year, underscoring how critical it is for business leaders to view data-security as an enterprise risk, not just an IT issue (White House, 2018).
8 Key Components Of Data Security

Data security is best viewed as a set of interconnected components, each answering part of the question: What data do we have, where is it, who is using it, and how do we reduce the risk?
1. Data discovery and classification
Data discovery and classification remove guesswork from data protection. Automated discovery identifies sensitive data — such as personal information, payment data, health records, and confidential IP — across endpoints, servers, databases, SaaS, and cloud storage.
Classification then applies consistent labels (for example, public, internal, confidential, highly confidential), so access controls and policies can be applied based on business criticality and regulatory obligations.
Without reliable discovery and classification, most other data security investments are operating blind.
2. Data inventory and lineage
A data inventory is the structured record of key datasets, including where they reside, who owns them, and which systems and services use them. Data lineage tracks how those datasets flow, transform, and are accessed over time.
Both inventory and lineage are critical to reconstructing incidents and proving that appropriate controls were in place. This combination enables teams to answer questions such as:
Which applications and services process customer data?
Which systems and users were involved in a given incident?
What is the downstream impact if one SaaS tool or AI service is compromised?
3. Access control and identity security
For most attacks, compromising an identity is the quickest route to data. Therefore, access control and identity security sit at the core of data protection.
Effective practices include:
Enforcing least-privilege access to sensitive datasets
Applying multi-factor authentication and conditional access for high-risk actions
Monitoring for unusual access patterns, especially for privileged and service accounts
Weak identity controls effectively bypass many other defences. By contrast, robust identity security prevents a significant proportion of potential data incidents before they start.
4. Data loss prevention and content inspection
Data loss prevention (DLP) and content inspection tools examine the content and context of data movements — for example, emails, file uploads, and endpoint transfers — and apply rules such as:
Blocking outbound emails carrying unencrypted financial or health data
Encrypting messages that contain specific identifiers or classification labels
Warning users when they attempt to send large data sets to personal accounts or unsanctioned tools
Since traditional, siloed DLP can be blind to modern, multi-channel exfiltration paths, it’s now essential for DLP must now be integrated into a wider data security architecture.
5. Data security posture management (DSPM)
Data security posture management (DSPM) brings a continuous-assessment mindset to data in cloud and hybrid environments. DSPM tools:
Discover and classify sensitive data across cloud services
Identify misconfigurations, over-permissive access, and risky sharing
Map likely attack paths from internet-exposed assets to high-value data stores
DSPM is essential for understanding which cloud data exposures represent material business risk, rather than treating all configuration findings as equal.
6. Encryption and tokenisation
Encryption and tokenisation are key safeguards when preventative controls fail:
Encryption at rest and in transit protects data if servers, backups, or devices are compromised.
Tokenisation and anonymisation reduce the use of real identifiers in environments such as testing, analytics, and AI training.
These controls significantly influence how regulators and courts view incidents. For example, a breach involving properly encrypted or pseudonymised data is often treated differently from one exposing raw records.
7. Monitoring, detection, and response
Modern data security requires the ability to detect and respond to suspicious data activity, including:
Unusual download volumes or exports from systems of record
Access from unexpected locations or devices
Privileged accounts or service identities behaving anomalously
For example, Trend Vision One™ integrates data security telemetry with extended detection and response (XDR), enabling analysts to correlate data movement with endpoint, network, email, and cloud events and respond from a single platform.
8. Governance, data security policies, and compliance
Governance and compliance ensures that data security is aligned with business objectives and regulatory requirements. It encompasses:
Data ownership and accountability
Policy frameworks and standards
Risk assessments, audits, and reporting
This is where security, privacy, legal, and business stakeholders align on what “acceptable data risk” looks like and how it will be maintained.
Data Security Threats And Attacks
While not every cyber threat directly targets data, the attacks that cause the most lasting damage almost always involve compromise, theft, or misuse of information.
Data breaches and unauthorised data access
A data breach occurs when data is accessed, stolen, or disclosed without authorisation. This often occurs by exploiting vulnerabilities, weak credentials, or misconfigurations.
Business impact depends heavily on the type of data involved: exposure of customer records, health data, or trade secrets carries different risk profiles from anonymised operational logs.
Ransomware and double extortion
Ransomware groups increasingly use double extortion tactics, exfiltrating sensitive data before encrypting systems and then threatening to publish or sell the data if the organisation does not pay.
This means:
Robust backups alone are insufficient; data theft is central to the extortion model.
Many ransomware incidents are also reportable data breaches, with associated legal and regulatory obligations.
The ability to limit what data can be exfiltrated — through segmentation, least privilege, and monitoring — is critical.
Data leaks and accidental insider threats
A data leak typically refers to unintentional exposure or disclosure of data, such as:
Sending a sensitive spreadsheet to the wrong recipient
Sharing cloud documents with overly broad access (for example, “anyone with the link”)
Uploading internal documents to public AI tools for assistance
ICO data underline that accidental disclosures are among the most frequent causes of reported incidents, even if they receive less media attention than large breaches.
Insider data theft and shadow IT
Malicious insider threats — or individuals under external pressure — may deliberately exfiltrate data using:
Unapproved cloud storage or file-sharing tools
Personal email accounts
Screenshots or external devices
Shadow IT, where teams adopt unsanctioned applications, amplifies this risk. Monitoring data movement, restricting high-risk channels, and enforcing clear internal consequences for misuse are key mitigations.
Cloud misconfigurations and exposed storage
Cloud misconfigurations are a major driver of unintended data exposure. Common scenarios include:
Cloud storage buckets left publicly accessible
Overly broad IAM roles allowing extensive read access
Test or development environments seeded with live production data
DSPM, combined with strong cloud security practices, helps identify and prioritise these exposures, focusing remediation on misconfigurations that expose sensitive information rather than treating all deviations as equal.
AI-enabled data exfiltration and model abuse
As organisations adopt AI assistants and agentic AI, sensitive data increasingly flows into prompts, conversation histories, and training datasets. From there, adversaries can:
Embed hidden instructions in documents or web pages to manipulate agents
Trigger agents to retrieve and transmit internal documents or records
Exploit weak agent-level safeguards to bypass existing access controls
This creates new exfiltration channels that traditional monitoring may not yet cover, making it critical for businesses to evolve their cybcersecurity systems to include AI risk management.
Supply chain and third-party data exposure
Partners, suppliers, and service providers often hold or process copies of your data. Compromise of these third parties — including AI, SaaS, or managed service providers — can result in secondary breaches that still affect your customers and regulators’ perceptions of your organisation’s security posture.
Third-party risk assessments, contractual security requirements, and ongoing monitoring are therefore central to data security.
Data Security Across Environments

Data moves across many different environments, each with its own risk profile. A modern approach applies consistent principles while adjusting controls to the context.
Data security in the cloud
Cloud platforms and SaaS services now store large volumes of business-critical and personal data. Effective cloud data security requires:
Comprehensive discovery and DSPM to understand where sensitive data is and how it is exposed
Strong identity controls and conditional access for cloud services
Integration with broader cloud security controls, including configuration management and workload protection
Data security for email and collaboration
Email and collaboration tools are central to business communication, and therefore to data risk.
When an email account is compromised, attackers can:
Intercept or manipulate financial communications and payment details
Harvest identity documents and personal information for fraud
Send convincing phishing messages to customers and partners to extend the compromise
Many reportable incidents also stem from simple mistakes: mis-addressed emails, misconfigured mailing lists, or over-shared meeting recordings.
Effective email data security combines:
User-centric controls – awareness training, protective prompts (for example, external recipient warnings), and clear handling guidelines for sensitive attachments
Technical protections – advanced email and collaboration security to stop phishing, BEC, and malware, as well as outbound DLP and encryption to control data leaving via email and file-sharing
Search and remediation capabilities – the ability to quickly locate, retract, or quarantine mis-sent or malicious messages
The same principles apply to collaboration platforms, which increasingly store chat logs, documents, and recordings containing sensitive information.
Data security on endpoints and devices
Endpoints — laptops, desktops, mobile devices, and servers — are where data is created, edited, and frequently cached. Even when the source system is in the cloud, users often:
Sync local copies of files
Store credentials and tokens in browsers and applications
Work offline with sensitive documents
This makes endpoints attractive targets for malware and targeted attackers.
Key endpoint security controls include:
Endpoint security software, hardening, and full-disk encryption
Endpoint DLP to manage transfers to removable media, personal cloud apps, and printers
Endpoint detection and response (EDR) to rapidly identify threats and automate responses
Remote wipe, isolation, and response capabilities for compromised or lost devices
Data security for applications, databases, and AI workloads
Applications and databases already hold some of the organisation’s most valuable structured and unstructured data. Now with AI added to the picture, cybersecurity risk has evolved and become even more data-centric.
AI-agent research demonstrates how indirect prompt injection hidden in web pages, Office files, or images can silently force multi-modal agents to exfiltrate documents, secrets, or conversation history they can access – without any explicit instruction from the user.
With data security, AI also brings both powerful defence capabilities along with new data risks:
AI Security Defence: AI can analyse huge volumes of telemetry, detect anomalous data access, and help predict which assets are most exposed.
AI Security Risk: AI agents and large language models can be manipulated to leak sensitive data they can see.
For applications and AI platforms, relevant data security measures include:
Secure application and API design – to prevent injection, logic flaws, and data exfiltration via vulnerable services
Database and data lake controls – including hardening, encryption, fine-grained access, and activity monitoring
AI company policies and analytics governance – regulating how training data, prompts, and outputs are handled, and ensuring AI agents adhere to data access and retention policies
Data security vs. traditional perimeter protection
Traditional perimeter security focuses on network boundaries, keeping threats out of the “castle.” In contrast, modern data security assumes threats can originate anywhere: endpoint, cloud service, supply chain. It protects the data itself regardless of location.
This shift aligns with zero-trust architecture: trust nothing by default, verify every connection, and protect every object. Data-centric security means focusing on how data is accessed, used, moved, and disposed of across the IT infrastrcture, not just within network boundaries.
Organisations must move from asking “Where is our boundary?” to “How is our data managed, accessed, and protected across the entire environment and services?” The critical question becomes not location, but control, visibility and accountability.
Aspect
Data Security
Traditional Perimeter Protection
Security Scope
Applies to data at rest, in transit, and in use across systems and platforms.
Focuses on securing the perimeter of a network (e.g., firewalls, routers).
Approach
Applies to data at rest, in transit, and in use across systems and platforms.
Broad, location-based, and relies on blocking unauthorised access.
Threat Detection
Uses data-centric monitoring, anomaly detection, and Data Loss Prevention (DLP).
Uses intrusion detection/prevention systems (IDS/IPS) at network edges.
Compliance & Governance
Aligns with data protection regulations (e.g., GDPR, HIPAA).
May not fully address data-specific compliance requirements.
Technology Examples
Encryption, tokenisation, DLP, Zero Trust, IAM (Identity & Access Management).
Firewalls, VPNs, IDS/IPS, DMZs (Demilitarised Zones).
Data security vs. compliance-only approaches
Compliance frameworks are valuable. They set minimum thresholds for protection, drive audit evidence, and support regulatory alignment. But compliance alone is not sufficient. A compliance-only mindset can leave operational gaps, technological blind spots and resilience shortfalls.
Data security must be embedded in strategy, not just a certification checkbox. When organisations align data-security controls with business risk, measure outcomes, and update policy/process/technology dynamically, they achieve performance and protection. Over time, policies evolve into best practices, and systems become measurable and accountable.
Aspect
Data Security
Compliance-Only Approach
Primary Goal
Protect data from breaches and unauthorised access
Meet regulatory requirements and avoid penalties
Focus
Risk reduction and proactive defence
Documentation and audit readiness
Key Activities
Encryption, access control, threat monitoring, patching
Policies, procedures, reporting, certifications
Outcome
Strong resilience against cyberattacks
Legal compliance but potential security gaps
Risk
Lower risk of breaches
Higher risk if compliance is treated as the end goal
Data Security Management: How Protection is Governed
Data security management refers to the operational and governance layer that keeps data protection functioning over time.
Effective cyber risk management typically includes:
Defined roles and responsibilities – clear ownership of key datasets, security controls, and regulatory interpretation (including the role of the data protection officer, where required).
Embedded risk processes – data protection impact assessments (DPIAs) and risk reviews for new systems, SaaS tools, and AI initiatives.
Standardised operational procedures – consistent approaches to access requests, permission reviews, onboarding/offboarding, and third-party data processing.
Meaningful metrics – visibility of discovery and classification coverage, data exposure levels (especially in cloud), incident rates, and time to detect and contain data-centric events.
Without a structured management approach, organisations may own strong tools but still be unable to answer basic questions such as, “Where is our most sensitive data currently exposed?” or “Did we fully contain the last incident?”.
Data Security Standards And Regulations
Organisations are subject to a range of data security standards and regulations, including:
UK GDPR and the Data Protection Act 2018
Sector-specific regulations in financial services, healthcare, and critical infrastructure
International information security standards such as ISO/IEC 42001
EU instruments such as NIS2 and DORA for many UK-linked organisations operating in Europe
These frameworks shape requirements for risk assessment, controls, breach notification, and evidence of due diligence.
Role of data protection officer in data security
Under UK GDPR, certain organisations are required to appoint a data protection officer (DPO), particularly when engaging in large-scale processing of special category data.
The DPO (or equivalent role):
Advises on data protection obligations and data privacy best practices
Monitors compliance and staff awareness
Oversees data protection impact assessments for high-risk processing
Acts as a point of contact with the ICO
Even when not mandated, a DPO function can help bridge legal, privacy, and security perspectives in the organisation’s data security management.
Business Data Security Best Practices Across The Data Lifecycle

Viewing business data security through the data lifecycle helps organisations understand where controls are most critical.
Create and collect
Limit collection to what is required for defined purposes.
Protect data capture points and APIs from injection and abuse.
Store
Ensure storage systems — on-premises or cloud — are hardened, encrypted, segmented, and monitored.
Avoid unmanaged copies and shadow repositories of sensitive datasets.
Use and share
Govern how data is accessed and shared via email, collaboration tools, and AI services.
Apply least-privilege access and data-aware controls to reduce inappropriate sharing.
Archive
Retain data only as long as necessary, in line with legal and business requirements.
Maintain equivalent security controls for archived data and maintain the ability to fulfil subject rights requests.
Dispose
Implement secure deletion and destruction processes for data and media.
Verify and document deletion where regulatory or contractual frameworks require it.
Data Security Tools And Data Security Software
From a business perspective, data security tools and data security software should be evaluated based on how effectively they reduce data risk and support governance.
Key categories include:
Discovery and classification – to build and maintain a reliable map of sensitive data across on-premises, cloud, and SaaS environments.
DLP and content inspection – to enforce data-aware policies across email, web, endpoints, and collaboration tools. Solutions such as Trend Micro’s integrated DLP capabilities help identify and control sensitive data in motion and at rest.
Data security posture management (DSPM) – to analyse cloud data stores for misconfigurations, risky access, and likely attack paths to critical datasets.
Identity and access security – to protect credentials and manage privileges, especially for high-value systems and data.
Endpoint and server protection – to block data-stealing malware, prevent unauthorised tools, and support endpoint-level DLP.
XDR and analytics – to correlate anomalies in data movement with broader threat activity and enable faster investigations
Encryption and key management – to protect data at rest and in transit, and support compliance and data sovereignty requirements.
Trend Vision One™ Data Security unifies many of these capabilities, providing centralised visibility, intelligent risk prioritisation, and rapid response to prevent accidental leaks, insider threats, and data-centric attacks across cloud and on-premises environments.
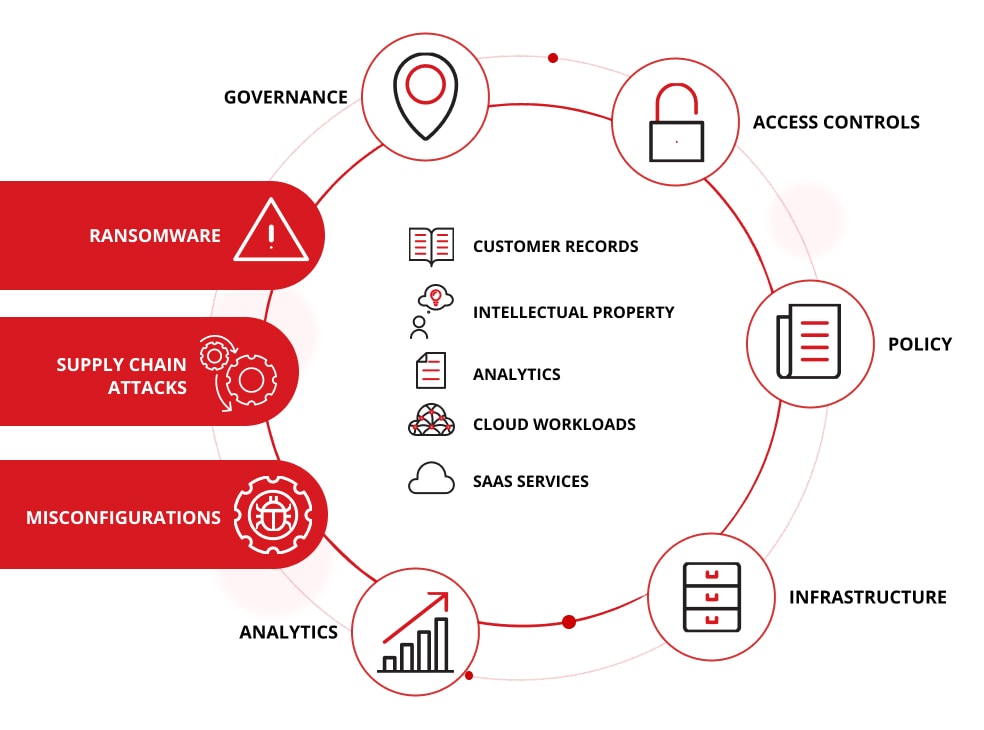
Why data security matters for today’s enterprises
Data is the lifeblood of modern business: customer records, intellectual property, analytics, cloud workloads and SaaS services drive value. Yet data is also the target of modern adversaries like ransomware, supply-chain attacks, and exploitation of cloud misconfigurations. Organisations with fragmented data oversight, unsupported infrastructure, or legacy controls are exposed.
By taking a holistic approach to data security that connects policy, infrastructure, access, controls, analytics, and governance, enterprises reduce risk, enable innovation, and build resilience. They meet regulatory obligations and build stakeholder trust. They also turn data into a strategic asset rather than a liability.
Modern Data Security With Trend Micro
Trend Micro’s approach to modern data security centres on treating data protection as a proactive, risk-based discipline rather than a collection of disconnected controls.
Trend Vision One™ Data Security is designed to:
Provide centralised visibility
Assess data security posture
Enforce intelligent policies and detect anomalies
Accelerate investigation and response
For organisations looking to move beyond traditional DLP and point solutions, Trend Vision One Data Security provides a path towards comprehensive, data-centric protection that supports AI innovation and more, all while keeping risk within acceptable bounds.
Scott Sargeant, Vice President of Product Management, is a seasoned technology leader with over 25 years of experience in delivering enterprise-class solutions across the cybersecurity and IT landscape.
Frequently Asked Questions (FAQs)
What is data security?
Data security is the practice of safeguarding sensitive information from unauthorised access, modification, loss, or theft through a combination of policies, processes, and security technologies applied consistently across all systems and environments.
Why is data protection important?
Data protection is important because data-centric incidents drive the most significant financial, legal, and reputational damage, and organisations are accountable to customers, regulators, and partners for how personal and business information is handled.
How can you keep data secure?
You can keep data secure by knowing where your sensitive data resides, limiting and monitoring who can access it, encrypting it at rest and in transit, enforcing data-aware policies for how it is shared, and ensuring you can detect and respond quickly to suspicious activity.
What are the main components of data security?
Core components include discovery and classification, data inventory and lineage, access control and identity security, DLP and content inspection, DSPM, encryption and tokenisation, monitoring and response, and governance through policies and compliance.
What is data security posture management (DSPM)?
DSPM is an approach and toolset that continuously analyses where data is stored across cloud and hybrid environments, how it is configured, who can access it, and how attackers might reach it, so that the most important data security risks can be prioritised and addressed.
Is data security the same as data privacy?
No. Data security focuses on how data is protected, while data privacy focuses on why and under what rules data is collected and processed, but both must work together to meet legal requirements and maintain trust.
Does every organisation need a data protection officer?
Not every organisation is legally required to appoint a data protection officer, but those engaged in large-scale processing of personal or special category data often are; many others still choose to create an equivalent role to coordinate privacy and data security activities.

