A Constant State of Flux: Trend Micro 2020 Annual Cybersecurity Report
2020 was the year that stymied organizations and tested their limits on many fronts. Incidents of great consequence, shifts to remote-work arrangements, and other significant changes from the familiar prompted a renewed awareness and reassessment in organizations. The challenges they encountered paved the way for adaptive and alternative solutions that took into account human as well as technological perspectives.
For cybercriminals, however, the year afforded a mother lode of opportunities for malicious activities. They took advantage of major events in their schemes to turn in illicit profit. Using techniques old and new, they exploited vulnerabilities, misconfigurations, and other security gaps as individuals and enterprises rushed to adopt technologies so as to adapt to the attendant challenges.
Looking back at a most unprecedented year, our annual cybersecurity report surveys the most notable and crucial security concerns that emerged and persisted in 2020, and provides users and organizations with insights into how they can navigate a drastically changing threat landscape.
Targeted attacks
Ransomware
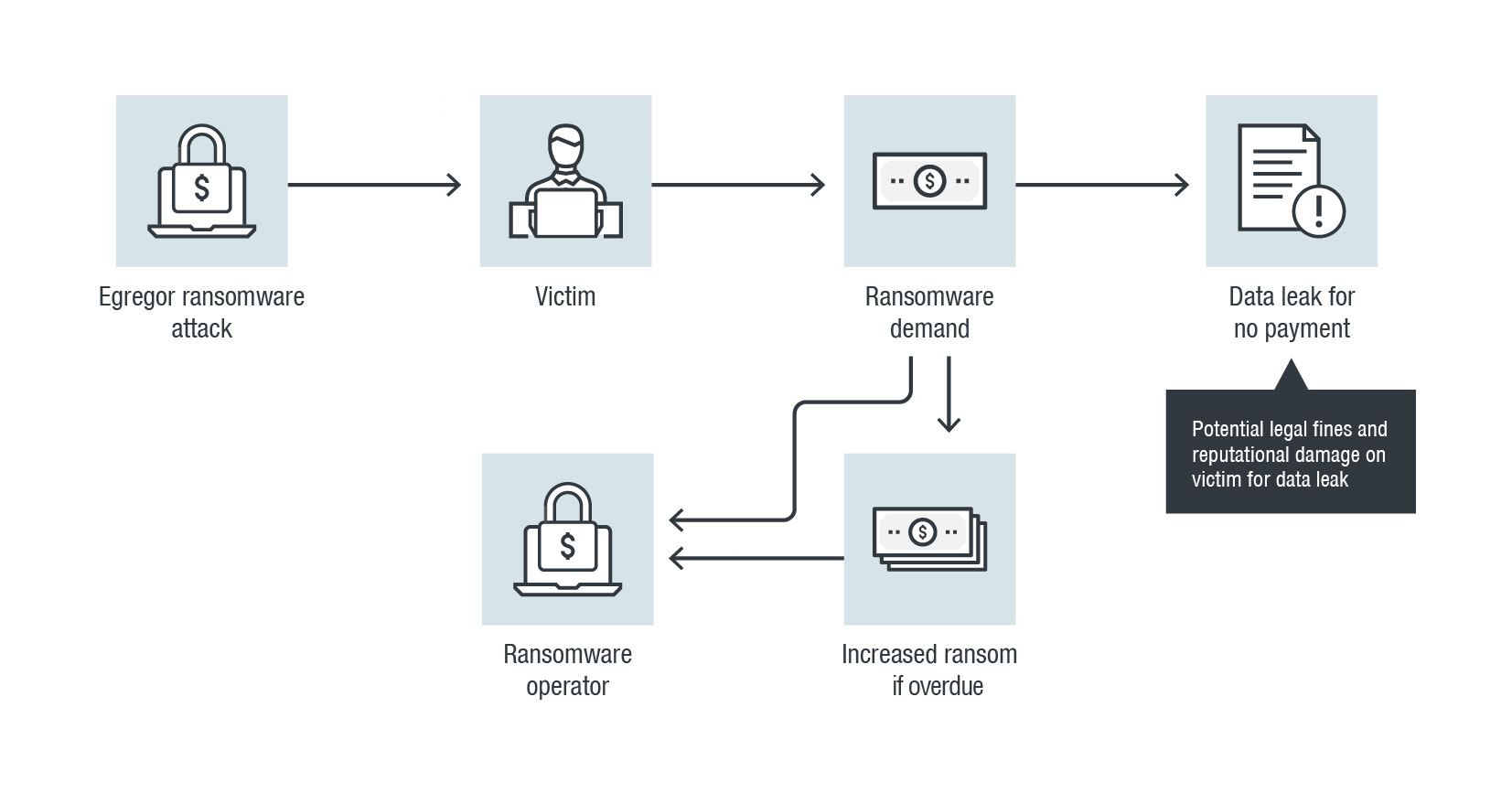
Ransomware operators maximized their profit streams with a double whammy. In addition to demanding money for the restoration of their victims’ access to encrypted data (and even increasing the ransom when payment was overdue), they threatened to leak sensitive information if the victims didn’t pay up. Given the risk of public exposure, victim organizations confronted the possibility of reputational damage as well as data loss. The essentiality of the functions of the frequent targets of ransomware attacks — including agencies and companies in the government, banking, manufacturing, and healthcare industries — only heightened the urgency of giving in to the demands of ransomware operators.
A comparison of the numbers of new ransomware families in 2019 and 2020
The 10 industries most targeted by ransomware attacks in 2020
The newcomer Egregor, which made its mark in the latter months of the year, notably employed the double extortion technique as it went after high-profile targets, including major organizations in retail, gaming, and human resources.
Supply-chain attacks
While organizations might have enhanced their security, malicious actors could still find ways to their systems by compromising their partners within their supply chains instead. By taking advantage of the established relationship and trust between a target organization and its partners, supply-chain attackers could gain a foothold in the organization’s systems.
One of the most highly publicized supply-chain attacks in recent memory came to light in December in the form of the attack involving Orion, a widely used network management system software developed by SolarWinds. The malicious actors behind the attack inserted a vulnerability into certain builds of Orion that could allow attackers to compromise servers running the software. Once the relevant update was pushed to customers, the attackers were able to deploy backdoors that gave them complete access to the affected networks and allowed them to perform various malicious activities. Given the nature of some of the targets, including top US government agencies, the attack could have far-reaching consequences.
Pandemic-prompted threats
Covid-19 scams
While Covid-19 continued to take its toll on the lives of people around the world, malicious actors took advantage of the unease and uncertainty brought about by the pandemic to further their illicit schemes. The vast majority of our detections of Covid-19-themed threats came in the form of malicious spam emails, including those that phished for personal and financial information, and most of them came from the US, Germany, and France, which were also among the countries that had been hit hardest by the pandemic. The scammers behind these threats gave them a sense of currency and urgency by customizing them with references to relevant concerns such as Covid-19 stimulus packages and vaccine rollouts. Business email compromise (BEC) scammers also banked on the pandemic: The subject lines of the bulk of the BEC samples we detected mentioned Covid-19.
TOTAL: 16,393,564
The distribution of detections of Covid-19-related threats in 2020 by type
TOTAL: 16,393,564
The distribution of detections of Covid-19-related threats in 2020 by country
Remote-work challenges
As organizations implemented remote-work arrangements in response to the pandemic, virtual private networks (VPNs) became valuable tools in protecting network connections from external threats. But like any software, VPN solutions could also be host to vulnerabilities, which, if exploited, could enable attackers to steal proprietary information from and conduct surveillance on their targets’ systems. One VPN vulnerability, CVE-2019-11510, accounted for nearly 800,000 detections in 2020 alone and was involved in attacks in 2020 where it was exploited to deliver ransomware. Malicious actors also found other ways to incorporate VPNs in their attacks: In September, we discovered an instance where an attacker bundled a VPN installer with the Bladabindi backdoor, which could be used to gather information from infected machines.
The rise in remote work also meant an increase in the use of communication tools such as Zoom, Slack, and Discord. This, in turn, led to an increase in attacks that abused these applications: from “Zoombombing” pranks and malicious Zoom installers to a ransomware variant that used Slack webhooks and a spam email campaign that used Discord to deliver malware.
The detection counts of notable VPN vulnerabilities in 2020
Cloud and IoT risks
Cloud threats
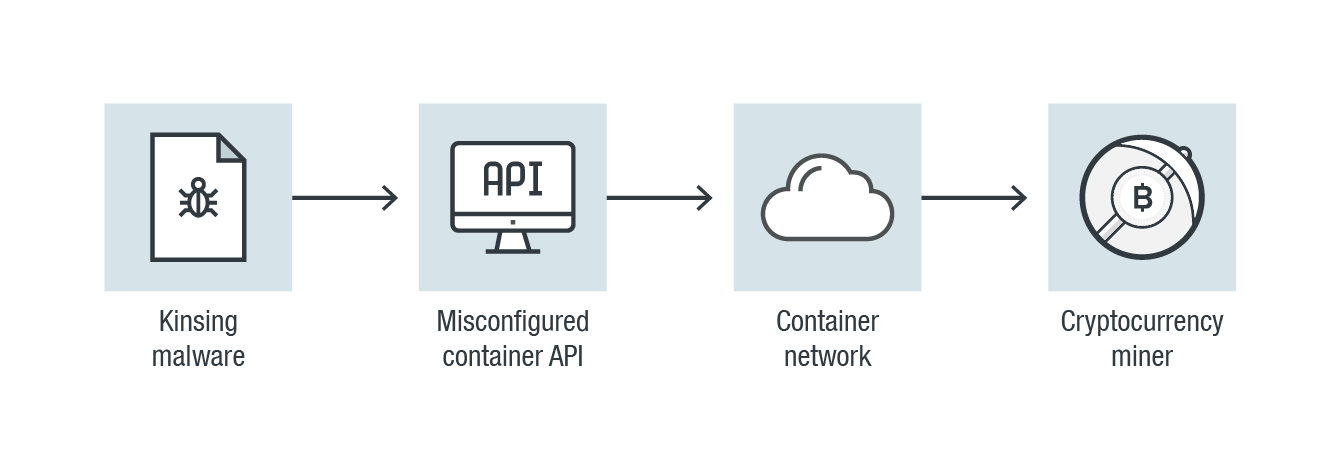
In 2020, the cloud became an even more integral component of the operations of many organizations. But the proper configuration of cloud assets and services continued to be a challenge. In April, for example, it was reported that attackers had dropped cryptocurrency miners on misconfigured Docker daemon API ports via the Kinsing malware. And in October, we reported on an attack on exposed Docker APIs that involved the use of the Metasploit Framework (MSF) shellcode as a payload — the first time we observed the use of such a technique.
In 2020, we also published our findings on how malicious actors take advantage of the underground cloud infrastructure. In the underground, cybercriminals regularly interact and transact with one another. On occasion, they delegate tasks for common jobs, thereby commodifying underground services. Some underground participants also sell access to troves of stolen data advertised as “clouds of logs.”
IoT attacks
Cybercriminals also took notice of the increased reliance of organizations and employees on the internet of things (IoT). This should be a major concern since home networks and devices could be abused by attackers to gain access to the corporate networks they’re connected to. Routers are particularly vulnerable, especially since security at an employee’s home is not as tight as at an enterprise workplace.
In 2020, we saw an uptick in the total number of inbound attack events, which was more than triple the 2019 tally, and in the total number of outbound attack events, which nearly doubled from 2019.
A comparison of the detection counts of possible inbound attacks in 2019 and 2020
A comparison of the detection counts of possible outbound attacks in 2019 and 2020
The threat landscape
57,262,610,930
25,825,951,753
31,436,659,177
Blocked email threats
3,698,445,871
1,028,006,974
2,670,438,897
Blocked malicious files
1,676,675,194
969,254,232
707,420,962
Blocked malicious URLs
79,743,156,637
36,271,603,944
43,471,552,693
Email reputation queries
1,523,957,334,514
708,757,638,233
815,199,696,281
File reputation queries
2,338,754,688,044
1,006,547,423,405
1,332,207,264,639
URL reputation queries
A comparison of the numbers of blocked email, file, and URL threats, and of email, file, and URL reputation queries in the first and second halves of 2020
A comparison of the numbers of blocked malicious Android apps in 2019 and 2020
A comparison of the numbers of detected BEC attempts in 2019 and 2020
Download our full report to learn more about the most significant cybersecurity issues of 2020 and the most effective strategies against current and emerging threats.
 Download A Constant State of Flux: Trend Micro 2020 Annual Cybersecurity Report
Download A Constant State of Flux: Trend Micro 2020 Annual Cybersecurity Report
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One