Commodified Cybercrime Infrastructure: Exploring the Underground Services Market for Cybercriminals
 Download The Hacker Infrastructure and Underground Hosting: Services Used by Criminals
Download The Hacker Infrastructure and Underground Hosting: Services Used by Criminals
Beyond standard underground offerings such as malware and exploit kits, cybercriminals also value having a stable hosting infrastructure that underpins all their activities. Such an infrastructure could host malicious content and the necessary components for controlling their operations (e.g., bulletproof hosting that run backend hacker infrastructure or a rented botnet of compromised machines).
In many respects, transactions among cybercriminals occur in ways similar to those in legitimate businesses. Amateurs and professionals alike rely on marketing their products across various platforms — some use social media, while some only do so in controlled, vetted underground forums.
Our first article in this research series provided an overview of the underground market, where services, infrastructures, and tools used to conduct illegal activities are bought and sold. Offerings are diverse and cater to every need. This part of the research series provides a look into the dynamics of the cybercrime ecosystem: the services offered in the underground and how infrastructures are set up for certain criminal applications.
Cybercrime Infrastructure Staples
Cybercriminal business models vary; they usually include a mix of dedicated and compromised assets along with resilient domain provisioning and anonymization services. Our research detailed some of the major service categories and new ways cybercriminals use different infrastructure services to defend against other criminals and law enforcement probes. What are the common service offerings?
Dedicated Hosting Services
We covered dedicated bulletproof hosting services in part one of our research series. Web hosting services offer access to different malicious and criminal activities. Dedicated servers are ideal for cybercrime setups that need to be highly resistant to disruption and takedown.
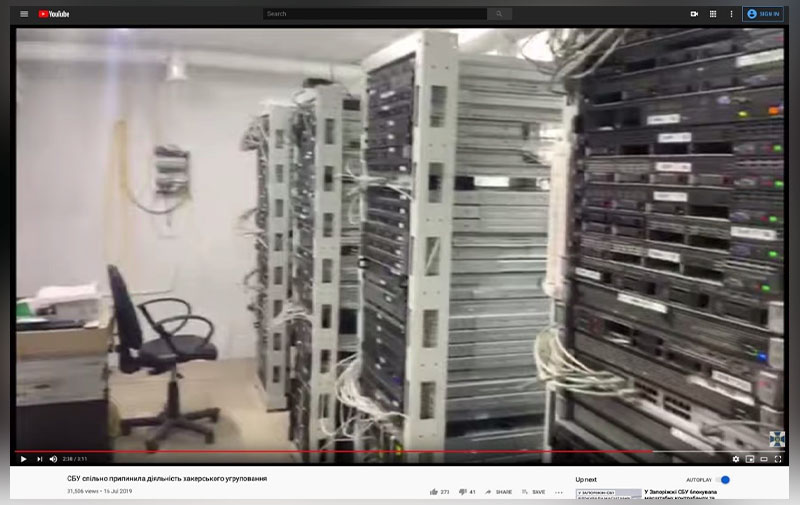
Dedicated and virtual private servers: An in-house data center in Ukraine
Source: Security Service of Ukraine’s official YouTube channel
Dedicated and virtual private servers (VPS) are used to host criminal infrastructure components such as botnet control panels and phishing pages or used as “jump servers” for securely accessing other infrastructures. Sometimes, criminals use “in-house” infrastructures in countries with relatively lenient legal frameworks. Racks of servers, located in side rooms of private properties, are offered to threat actors, as opposed to hosting them in larger commercial entities.
Modern fast-flux: Cost comparisons in hosting services
Fast-flux infrastructures allow criminals to constantly change their server location, consequently increasing their resistance to operation disruptions. Since fast-flux-backed services require maintenance of a pool of IP addresses with high availability, they are more expensive to operate than the usual bulletproof hosting services.
Compromised Hosting Services
The use and abuse of legitimate assets are common in the underground. Cybercriminals have increasingly depended on compromising machines to support their services. Some services resell compromised sites for further use as landing phishing pages, exploit kit hosting pages, or SEO doorways.
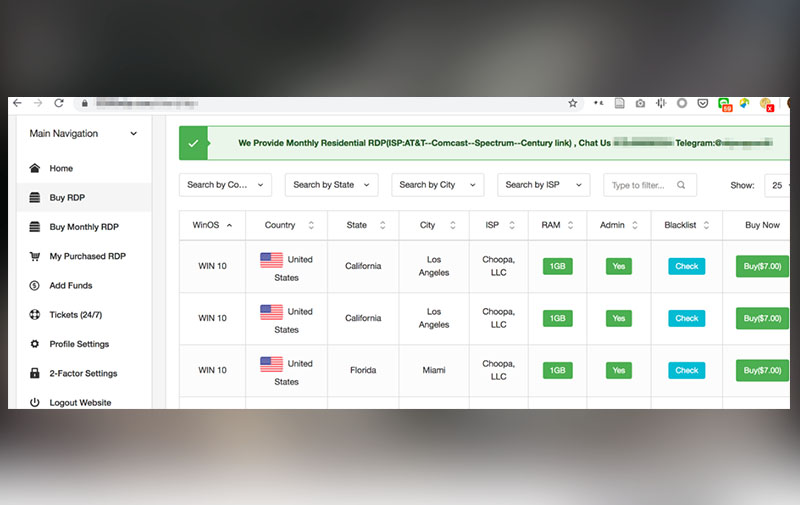
Compromised machines used as dedicated servers: A site selling access to compromised RDPs
Legitimate assets are compromised and used for hosting in at least one of the steps in a criminal’s monetization lifecycle. Exposed servers are exploited through vulnerabilities in server software, brute-force credential attacks, or phishing campaigns. Compromised assets are sold on online portals, underground forums, and dedicated marketplaces in social networks.
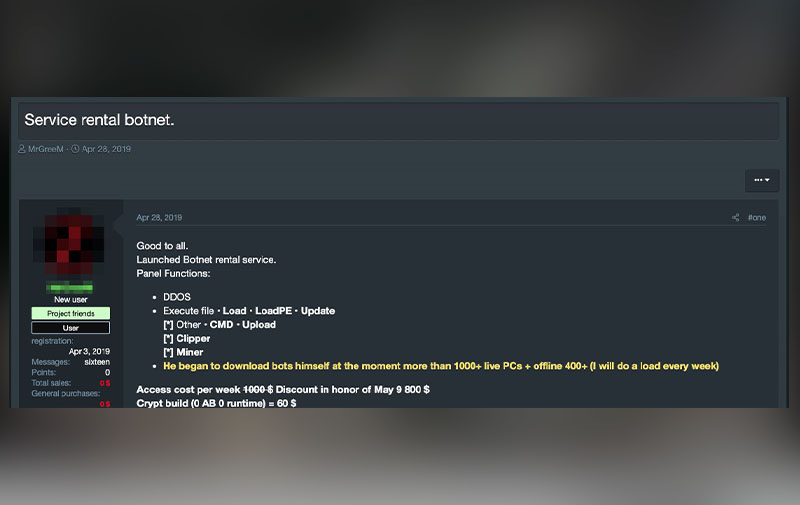
Botnets for rent (regular PCs): Botnet rental service offering with access to C&C panel
A PC-based botnet with over 1,000 connected PCs could cost US$800 and include functions for cryptocurrency mining, distributed denial-of-service (DDoS), and arbitrary file execution. Botnet owners commonly prohibit ransomware, cryptolockers, and files that have detections on VirusTotal since such compromise could be immediately exposed to the PC owner.
Below is a case study examining the overall lifecycle of a compromised asset and how they are typically used for malicious purposes. The figure indicates the various spin-offs a server goes through once it’s compromised, how it can be monetized and resold, and when security teams eventually deal with it.
The monetization lifecycle of a compromised server
Click around the graphic to see more information on specific components
major flow from takeover to future monetization stages
potential spin-offs and returns to previous monetization paths
IR team dealing with the threat
Cybercriminal takeover The server takeover is the earliest stage, where exposed assets are enumerated (i.e., via network scanners), accessed, and categorized by features (e.g., availability, bandwidth, and type of GPU) for further malicious purposes.
Categorization and estimation of monetization paths Compromised servers are categorized based on simple criteria that can be automatically collected by software tools used by underground actors (e.g., computing power, bandwidth, location, victim). A compromised asset can be taken over, monetized, and resold several times.
Sensitive data exfiltration This category includes theft from the compromised server of credentials, PII, financial information, and scanned or sensitive documents using a variety of automated keyword search tools.
Resale for targeted attacks Advanced categorization may find servers that are of interest to industrial espionage actors looking to dissociate themselves from the initial compromise. Particularly sensitive assets can be sold in underground auctions for hundreds of thousands of USD.
Resale for criminal monetization Some platforms offered in the underground automate the processing and monetizing of compromised servers, whereby sellers can collaborate to deliver more than a hundred compromised servers per day in some scenarios, sometimes called the “access as a service” model.
Criminal monetization A compromised server commonly gets monetized through cryptocurrency mining and malicious hosting. Ransomware attacks, especially targeted ones, may also be employed by actors who have in-depth knowledge about the infrastructure. Cryptocurrency mining should be of particular interest to defenders, as it often indicates a compromised asset that is in an idle state prior to being resold or having ransomware deployed.
Incident response The typical instances wherein a compromise or malicious activity is detected, and an incident response (IR) team deals with the threat.
Privacy and Anonymization Services
Anonymization services allow cybercrooks to move toward illicit activities with greater security and obfuscation. Without (a reliable) one, investigators can often determine a criminal’s true identity. Such services are in high demand to threat actors, and many developers dedicate considerable time to ensure the robustness of this side of the infrastructure.
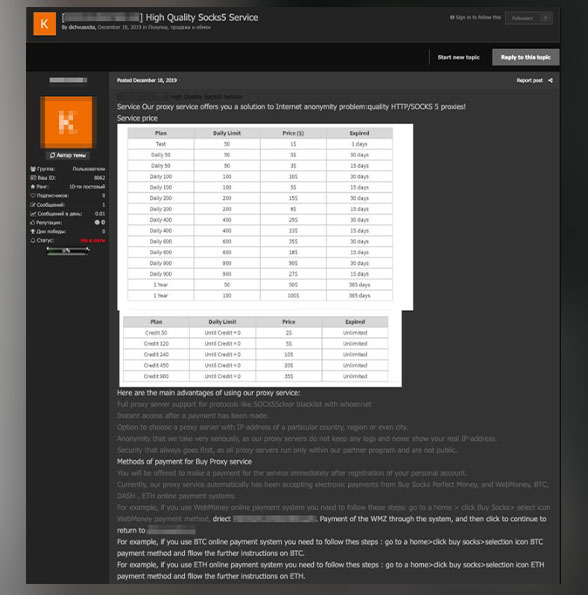
Proxies: Sample price list
Proxy services are common in criminal forums; there are even SOCKS unlimited plans that can sell for as low as US$2. These allow threat actors to hide activities without triggering detection by network security monitoring tools. Others trade legitimate communication protocols like Secure Shell (SSH) tools that, unlike RDP, are more versatile and less likely to go offline.
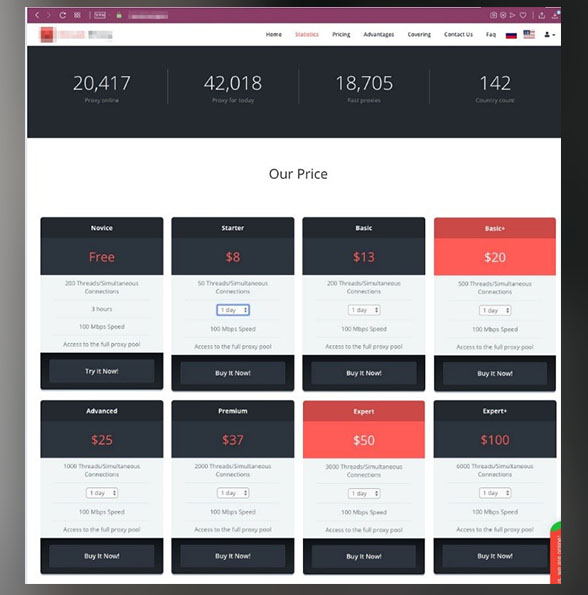
Anonymization VPN services: Selling short-term VPN contracts in the underground
Many sellers have anonymization services offered for rent as their primary business model. While legitimate VPN providers have monthly subscriptions, suspicious VPN offerings are often offered through a “period of contract,” sometimes as little as a single day. Services, like in the example above, provide a simple way of describing features, functionality, efficacy, and cost, in addition to upgrade attributes.
Domain Provisioning Services
Bulletproof domains have been part of hosting operations for a while now. Service providers offer abuse-resistant hosting for both IP addresses and domain names; some even notify users when they receive abuse complaints. Some sellers also offer recently freed and reputable domains, which are useful for bypassing reputation-based filters of security software.
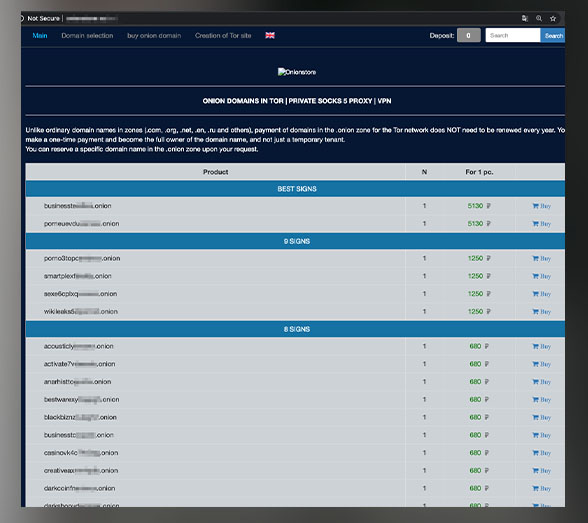
Domains in Tor: Price list for domains in the .onion zone
Cybercriminals often conceal the location of parts of their infrastructure by hosting platforms on darknet (.onion) sites. Market offerings for such domains often include bulletproof hosts and provision of illegal components. Popular domains retail for about US$10 to US$80.
Decentralized DNS: Sites that register Namecoin and Emercoin domains
We have written about the potential misuse of blockchain and decentralized domain name system (DNS) top-level domains (TLDs) back in 2013, and it appears that it has become more commonplace for threat actors. The distributed architecture of TLD, full anonymity, resistance to takedown, and capacity of domain name operations to be fully automated make the service appealing to hackers. GandCrab ransomware and associated strains, for instance, were prominently hosted within this space.
Cybercrime Infrastructure Niches
The underground offers a wide range of services. We found offerings that are not yet as widely distributed in the underground compared to those mentioned above, but we believe their popularity will grow in forums over time. These developments in the cybercrime underground will allow defenders to gain a better awareness of market niches and help them prepare for what’s more to come.
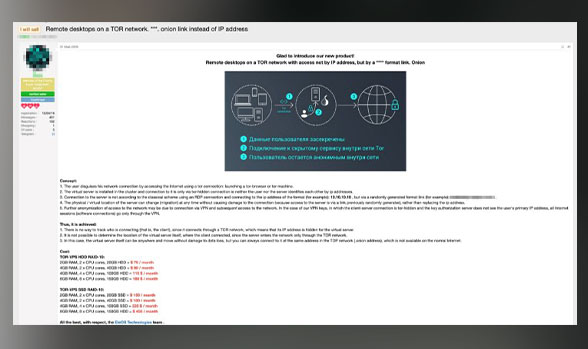
Mobile workspace: A bulletproof preconfigured workspace offering on Tor
We have encountered offerings for mobile working environments, which appear to be a bulletproof variant of a work environment. Aside from offering complete anonymity, the services also provide DDoS protection, outgoing traffic mixers, and VPNs. Some sellers even provide fast-flux services, customized routers, and their own “secure” Android variants.

Telephony-related services: An offering for subscriber details on mobile phone numbers
Some underground sellers have exhibited familiarity with telecom networks and infrastructures through services such as phone landing, disposable phone numbers, and caller detail checks. The services include various personally identifiable information on the subscriber. Interestingly, we also encountered a service for phone and corporate email confirmation, which allows attackers to create fraudulent accounts by bypassing common verification approaches.
Other emerging trends in underground cybercrime infrastructures:
- Abuse of satellite infrastructure
- Internet of things (IoT) hosting infrastructure
- Mobile infrastructure
- Parasitic computing for rent
- Route hijacking, BGP, and unused IP space
- Traffic mixing anonymizing networks
If there’s anything to be learned from observing the underground economy’s evolution, it’s that any offering imaginable has a good chance that it’s available, if not already thriving in a competitive market. Read our paper, “The Hacker Infrastructure and Underground Hosting: Services Used by Criminals,” where we discuss our findings in the context of major service categories.
More underground hosting research:
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines




 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One