Security Architecture for Smart Factories
 Building smart factories is a substantial endeavor for organizations. The initial steps involve understanding what makes them unique and what new advantages they offer. However, a realistic view of smart factories also involves acknowledging the risks and threats that may arise in its converged virtual and physical environment.
Building smart factories is a substantial endeavor for organizations. The initial steps involve understanding what makes them unique and what new advantages they offer. However, a realistic view of smart factories also involves acknowledging the risks and threats that may arise in its converged virtual and physical environment.
As with many systems that integrate with the industrial internet of things (IIoT), the convergence of information technology (IT) and operational technology (OT) in smart factories allows for capabilities such as real-time monitoring, interoperability, and virtualization. But this also means an expanded attack surface. What’s more, cyberthreats in converged environments can directly translate to physical scenarios.
IIoT security, therefore, plays a crucial role in creating and operating smart factories. But how should it be implemented? Identifying the building blocks of IIoT security is key to answering this question.
The architecture
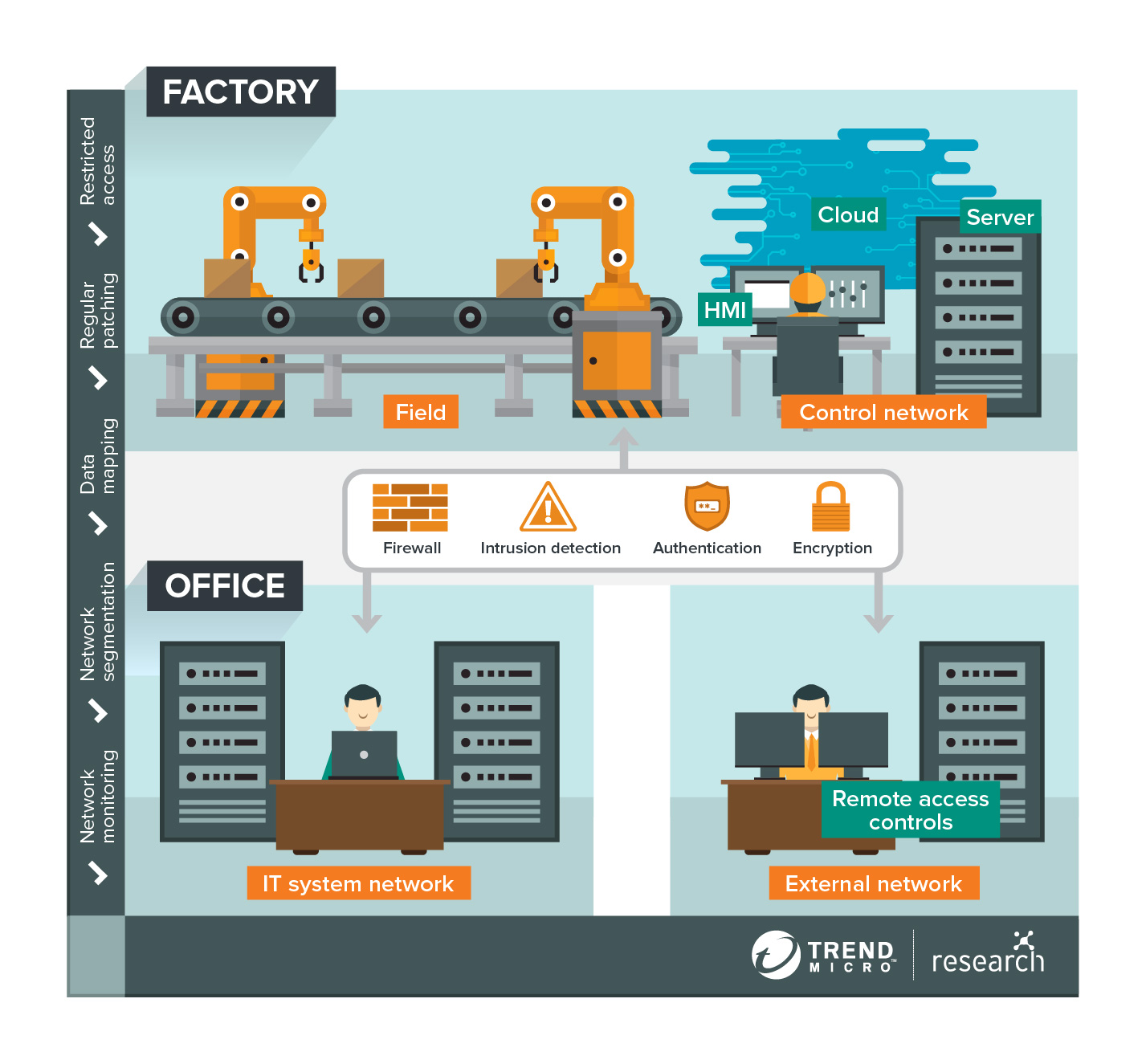 Recommended security architecture for smart factories
Recommended security architecture for smart factories
Mapping the data
Smart factory operations are data-driven. The abundance of data a smart factory harnesses can include the amount of raw materials it has in storage, the production speeds of its machines, the location of ongoing deliveries, and a great deal more, depending on its industry. Big data allows the smart factory to paint a virtual copy of physical operations that is used to carry out functions such as predicting outcomes and making autonomous decisions.
Organizations should be prepared for the vast amount of data this entails. They should be able to identify the types of data to be used and map out its course from collection and transfer to processing and storage. Mapping also means noting all possible exit and entry points. Personnel, for example, can move information from the office to the factory using external storage devices like USB flash drives. Terminals can also be taken in and out of factories for servicing. Aside from setting security protocols for personnel in handling such scenarios, tools should also be used to make sure that these portable devices are clean and virus-free before being connected or reconnected to the factory’s systems.
Securing the network and various communication channels
Data is also communicated over the network that connects the smart factory. Using the right cybersecurity measures on the network and the cloud can help prevent exploitation of device vulnerabilities, denial-of-service (DoS) attacks, and malware infection, among other security incidents. In-house IT systems not directly connected to the factory should be updated if necessary as doing so will reduce the possible entry points of attacks. Monitoring the network will also allow the early detection of suspicious behavior.
Noting the individual communication channels used within the factory, including those involving industrial control systems (ICSs) as well as other devices, can help in pinpointing possible areas of exposure. Also, knowing what kind of information is being transferred through the various channels can show which channels need stricter security. Organizations can also keep their remote access controls or any other external communications secure by using strong firewalls, encryption, authentication, and intrusion detection. These steps can help in preventing man-in-the-middle (MITM) attacks and information theft by threat actors.
Protecting equipment
Just as every device and piece of equipment on the factory floor is important to overall production, so is each important to the security of the smart factory. Setting up devices on the factory floor should be meticulously done with the goal of trimming away unnecessary functions, connections, and instances of data collection. This should allow devices to operate with improved precision and reduce areas of compromise and data theft.
It is also important to remember that vulnerabilities will always be a concern with regard to connected devices. Looking into possible vulnerabilities should be one of the preliminary steps in choosing equipment. In addition, once the factory is operational, regular patching should be part of its maintenance procedures.
Throughout all this, physical security of each device should not be neglected. Unauthorized access to a device can lead to a compromised network, just as a compromised network can lead to device malfunctions.
Assuming compromise and minimizing damage
In a smart factory environment, assuming compromise and planning countermeasures can minimize damage from a successful intrusion. Organizations should set protocols to alert of, contain, and mitigate attacks that could penetrate initial defenses. One containment technique for ICSs, for example, could be the use of network segmentation, where equipment and devices are grouped into hierarchies based on the sensitivity and criticality of their functions; this could prevent malware from spreading immediately to more sensitive and critical devices.
Maintaining security
Security should be part of the periodical maintenance of a smart factory. Regular maintenance should also be done to ensure that each component of the factory is updated with its most recent patches or firmware. Considering the convergence of IT and OT systems in smart factories, using a layered security approach like Connected Threat Defense will enable security solutions across networks, endpoints, and cloud environments to share information and defend each component of these converged systems.
Company personnel play an important role in this regard as well. Given that personnel directly access data and machinery, standard operating procedures (SOPs) and policies concerning the right handling of equipment and systems should be created carefully with input from both IT and OT departments. Involving personnel in the security of the environment in which they work can help establish and maintain a consistent level of security not only on the factory floor but across the organization as well.
From the design phase
These security recommendations are meant to be embedded deep within the smart factory’s architecture. This is because, especially in the case of smart factories, security should be considered as early as possible — from the design phase.
After all, weak defenses can allow threat actors to negate the very advantages organizations sought in building smart factories in the first place. Rather than quicker production of quality goods, enterprises with inadequately secured smart factories may have to deal with threats and risks that can cause undetected defects, which, in turn, may necessitate costly product recalls. Or instead of predicting and preventing accidents on the factory floor, organizations may be subjected to undetected attacks that can actually cause the incidents.
Implementing security measures late into the process or even once a smart factory is already operational can mean overhauling work procedures or replacing expensive equipment, among other undesirable consequences. Security, therefore, should be treated as a necessary component, not a mere accessory.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One