Security 101: Protecting Wi-Fi Networks Against Hacking and Eavesdropping
 by Jindrich Karasek (Cyber Threat Researcher)
by Jindrich Karasek (Cyber Threat Researcher)
Setting up home and small business networks
It has been known that there are existing vulnerabilities in Wi-Fi security protocols and hardware components that are introduced by manufacturers. These include poorly secured administrator access and vulnerable services like Telnet, Universal Plug and Play (UPnP), and Secure Shell, which are widely abused by botnets such as Mirai and its various iterations. For instance, the web administration interface is sometimes prone to authentication bypass so that every, or any for that matter,
The default configuration of connected devices, factory default passwords, and weak encryption are also among the most notorious factors that have contributed to attacks not only to the ecosystem of the internet of things (IoT) but also to networks in general. Every device exposed to the internet could be a possible entry point for attackers. For example, if a surveillance camera doesn’t have encrypted traffic while it’s connected to a Wi-Fi network, an attacker can snoop on the footage in a given environment.
Why is Wi-Fi hacking still a preferred cybercriminal method?
Wireless networks can be seen as inherently
On the other hand, there is Wi-Fi Protected Access 2 (WPA2), which has been known as a secure wireless protocol, using Advanced Encryption Standard (AES) for encryption. However, it has also been proved to not be bulletproof, when the Key Reinstallation AttaCK (KRACK) vulnerability was found; KRACK is said to most likely affect all Wi-Fi-enabled devices, even those with proper implementations of WPA2.
Attacks against wireless networks can be facilitated in multiple ways. They can be deployed with Raspberry Pi and installed tools as long as it’s attached to the proper wireless adapter. They can also be done with rooted smartphones and proper open-source tools.
A successful attack could require only the following components:
- An appropriate device with installed tools. The tools are usually open-source and thus publicly available. A requisite Wi-Fi adapter could cost as low as US$20.
- Traffic on the network. If traffic is too silent, it would be difficult to sniff enough packets to retrieve the password.
- A short password. The shorter the password, the faster the decryption process. For example, a short password like
hackm can take only four minutes to decode.
An attacker can just pretend to sit and wait in a lobby, enjoy his coffee, and while away his time, or just use his phone while standing nearby. Footage check of security feeds would not help as the activity would look like normal browsing or the device could be hidden in a bag or otherwise obscured during the whole attack.
What are the scenarios that enable attackers to attack Wi-Fi networks?
Wi-Fi is often used in spaces like coffee shops, public libraries, and homes, and in small businesses such as banks and insurance companies. The latter, in particular, are usually far from the reach of the main information technology (IT) department and may find it difficult to enforce compliance with company network policies. Moreover, monitoring these remote office locations can be tricky as they may be on network segments different from those of the rest of the company.
Another factor that could play a role in heightening the security challenges is how the policies of some internet service providers (ISPs) may provide their clients with obsolete routers, leaving users with devices that will no longer be updated. It’s not unreasonable to assume that these homes and offices are using years-old technologies or, at the very least, factory default settings, thereby posing low-hanging fruits for attackers.
Individuals who introduce their own poorly secured Wi-Fi routers enabled with WEP into the networks of their companies or institutions may also effectively introduce the risk of attacks into the networks. While it may look harmless from the point of view of the individuals who introduced the vulnerable devices to the networks, the companies or institutions could nevertheless be subjected to network compromise.
Consequences can escalate to a privacy breach, a situation which is more fraught now than ever with the enforcement of the General Data Protection Regulation (GDPR), a directive that affects all companies that engage with the data of European Union (EU) citizens, regardless of their location.
The motivations of attackers may vary. Either they may be interested in breaking into corporate networks to sniff data or they aim to hijack vulnerable routers and other networked devices to turn these into parts of botnets. From there, attackers can launch further attacks, perhaps the most notorious of which are distributed denial-of-service (DDOS) attacks. Cryptocurrency mining and malware infection for command and control are a couple of the other ways criminals can turn their attention to for malicious activity. All of these aforementioned attacks can be done without the knowledge, let alone the consent, of the owners of the devices and the networks. Some attackers even go as far as removing traces of their activity to make post-infection forensics even more difficult.
How can attackers locate unsecure wireless networks?
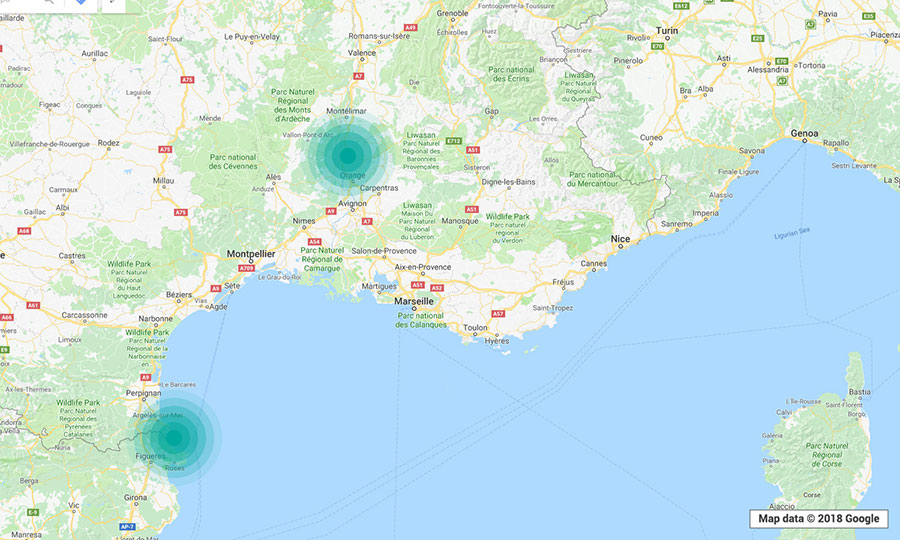
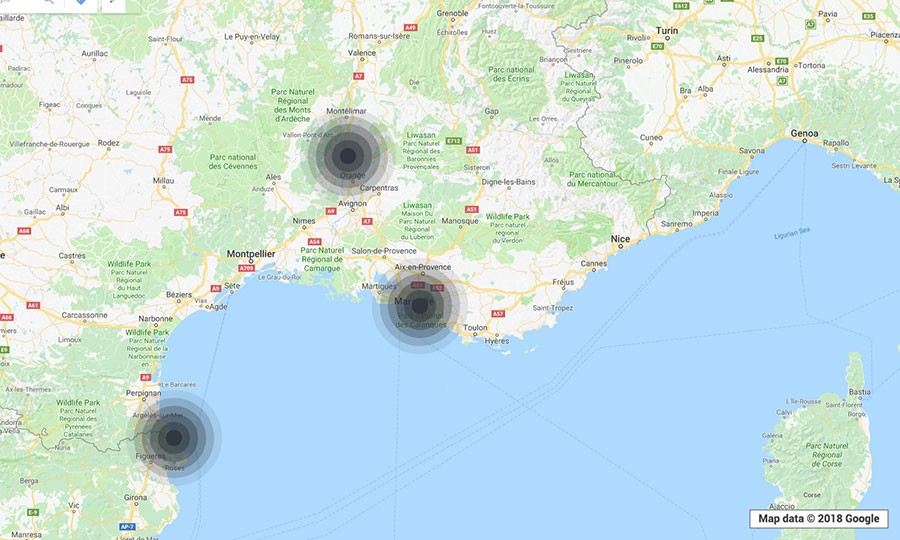
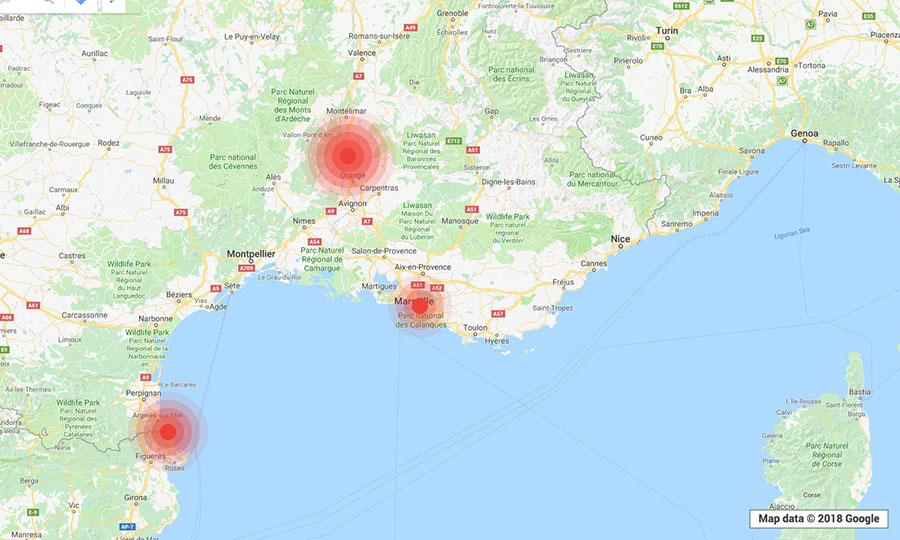
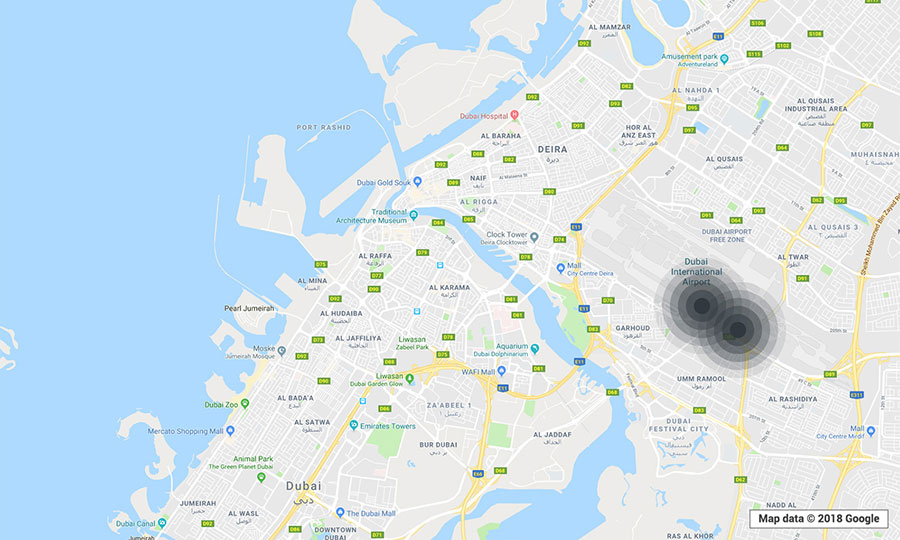
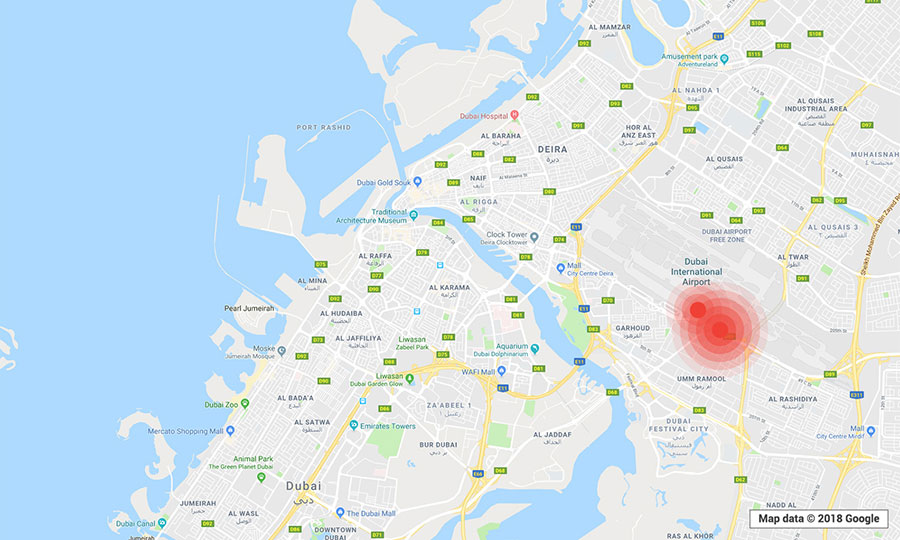
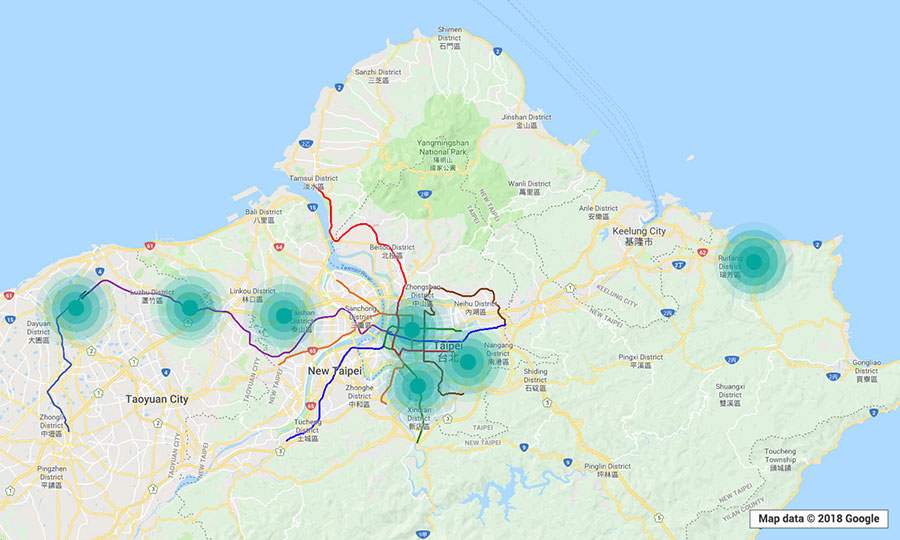
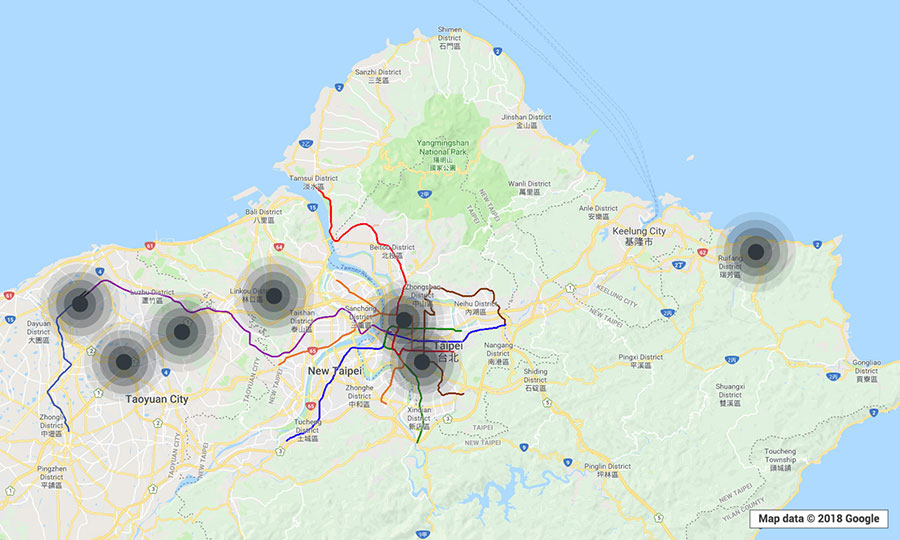
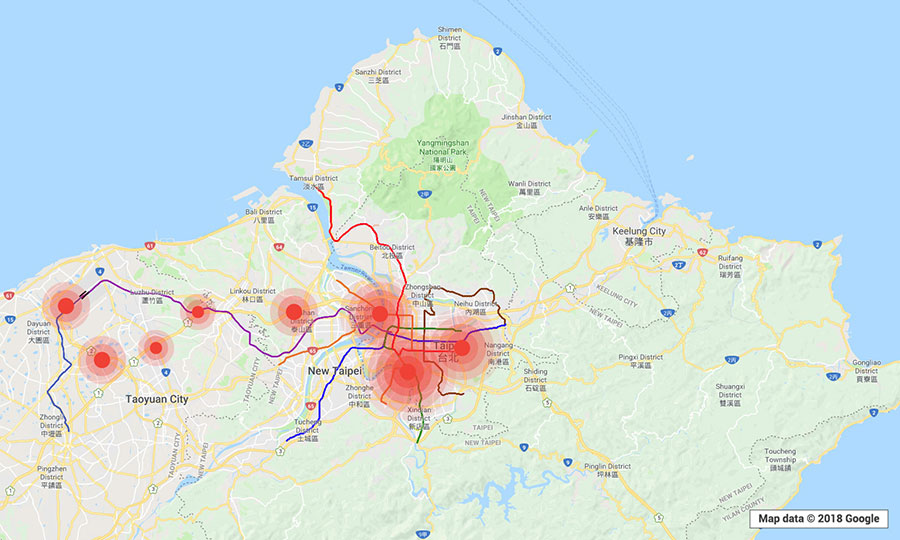
To get a real-world look at the prevalence of the
Just by using a smartphone installed with a legitimate Wi-Fi monitoring app and walking or driving through the locations, we were able to determine the exact GPS coordinates, network names or service set identifiers (SSIDs), encryptions, channels, and signal strengths of open local wireless networks. (The SSIDs came out empty if hidden.) Data from various “trips” were gathered into the clustered maps below. (“Clustered” means that every point indicates that there was at least one vulnerable WEP or WPA2 network in operation in the location.)
Note: The visualizations are meant only to provide a look at potentially
The kinds of establishments spotted to be using
- Gas stations and fast food chains abutting these stations.
- Motels along public roads and highways.
- Coffee shops, public libraries, and schools.
- Airbnb locations and Airbnb-like apartments.
- Museums, galleries, and research centers.
After compromising vulnerable networks, hackers can capture the traffic and sniff session IDs, information shared, websites visited, and even credentials used. This could enable them to perform
How can wireless networks be protected against compromise?
While it may be considered as a dated cybercriminal method, Wi-Fi network hacking remains a threat to users and businesses’ data and privacy as poor security practices are still employed. Users and businesses can prevent attackers from exploiting vulnerabilities in wireless connections by being aware of the aforementioned security considerations and adopting best practices.
Users can minimize the risk of attacks in their networks by:
- Changing default Wi-Fi network names (SSIDs) and passwords, especially for bundled routers provided by service providers, to complex credentials to deter unauthorized access.
- Updating the firmware of Wi-Fi-enabled devices, routers, and other hardware as soon as updates are available, and considering switching to Ethernet or wired connections until patches are rolled out.
- Enabling the firewall for added security in devices, or using a virtual private network (VPN) especially when remotely accessing assets.
For businesses, the crucial mitigation is for the IT department to have stringent policies in place, such as:
- Raising company awareness on the risks related to
unsecure connections and the use of wireless networks at work as well as at home. - Employing network monitoring to oversee connected devices and web traffic.
- Regularly reviewing device logs and monitoring results for any suspicious activity. This process can be automated.
- Using authentication tools, such as two-factor authentication, for all users connecting to the wireless networks other than inputting a password. An authentication method that will allow network administrators to immediately track and block entry points to the network in real time should help in case of a security incident.
Another good countermeasure is to limit the signal strengths of Wi-Fi routers. Mobile devices and laptops do not have high-gain antennas, so there is no need for long-range signals. In this case, if a user is outside the office, the Wi-Fi network is practically inaccessible. Attackers may still use high-gain antennas, however, to hit the network from a considerable distance; after all, successful infiltration of wireless networks happens only if the attackers are within range.
Trend Micro solutions
The Trend Micro Hybrid Cloud Security solution, powered by XGen™ security, delivers a blend of cross-generational threat defense techniques that have been optimized to protect physical, virtual, and cloud workloads. It features Trend Micro™ Deep Security™ protection for data centers, which provides network security capabilities such as deep packet inspection, intrusion prevention, and host firewall. Trend Micro™ OfficeScan™ endpoint protection, which is a critical component of Trend Micro Smart Protection Suites, and Trend Micro™ Worry-Free™ Business Security Services protect users and businesses with capabilities such as behavioral analysis, application control, web and file reputation, endpoint encryption, and data loss prevention.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One