Nemty Ransomware Spreads via Love Letter Emails
 Additional Insights by Joel Arvin Merete
Additional Insights by Joel Arvin Merete
Threat actors are distributing Nemty ransomware through a spam campaign using emails that pose as messages from lovers, according to a report by Malwarebytes and X-Force Iris researchers. Trend Micro researchers also encountered the emails. The malicious JavaScript file contained in the attachments is detected by Trend Micro as Trojan.JS.NEMTY.THBBHBO.
The email commonly had subjects that included “My love,” “Don’t tell anyone,” “You should read this,” “Will be our secret,” “Can’t forget you,” “Letter for you,” “Just for you,” and “My loveletter.” The emails contain only a wink emoticon in its email body. They include ZIP file attachments with the file name formatted as LOVE_YOU_
Nemty ransomware was first discovered in August 2019. It resurfaced on November 2019 and was distributed using the Phorpiex botnet. The new samples likewise use the Phorpiex botnet to send spam emails. Cybercriminals behind the ransomware threaten to leak stolen data if the ransom is not paid, an extortion threat similar to other ransomware variants like Maze that go beyond encrypting files on the device.
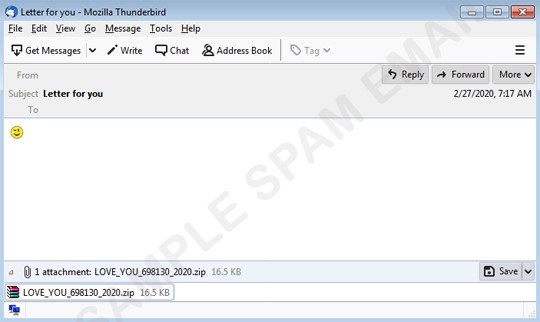
Figure 1. Nemty love letter email sample
Defending against ransomware
Ransomware can cause hundred thousands of dollars’ worth of losses, either through the value of lost files or through paying the ransom to avoid the downtime and data loss caused by the infection. According to the Trend Micro Annual Security Roundup, the detection of ransomware-related threats surged from over 55 million in 2018 to over 61 million in 2019, showing the threat’s continued proliferation. Besides the increase in number, ransomware variants are also continually evolving with increased complexity.
Like Nemty, other recently discovered ransomware families don’t just stop with file encryption. They also include abilities that steal files (Maze), force Windows machines to reboot into safe mode to bypass security software (Snatch), and end various processes (Zeppelin).
Enterprises and individual users can follow a few best practices to prevent a ransomware infection or mitigate the effects of an attack:
- Don’t download attachments or click URL Links in emails from unknown senders
- Back up important files
- Install the latest updates and patches to address software vulnerabilities
A multilayered security strategy can be used to thwart ransomware across the network. Add more layers of protection through solutions such as XGen™ Security: Trend Micro Email Security for email and web protection, Trend Micro Apex One™ for endpoints, Trend Micro™ Deep Discovery™ for network protection, and Trend Micro™ Deep Security™ for server protection.
Indicator of compromise
| SHA 256 | Trend Micro Pattern Detection |
| f3e743c919c1deaf5108d361c4ff610187606f450fabda0bea3786d4063511b1 | Trojan.JS.NEMTY.THBBHBO |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One