Into the Battlefield: A Security Guide to IoT Botnets
 The internet of things (IoT) has revolutionized familiar spaces by making them smarter. Homes, offices, and cities, are just some of the places where IoT devices have given better visibility, security, and control. However, these conveniences have come at a cost: traditional cyberthreats also found a new arena for attacks and gave rise to realities like IoT botnets.
The internet of things (IoT) has revolutionized familiar spaces by making them smarter. Homes, offices, and cities, are just some of the places where IoT devices have given better visibility, security, and control. However, these conveniences have come at a cost: traditional cyberthreats also found a new arena for attacks and gave rise to realities like IoT botnets.
IoT botnets battle to cancel each other out, while IoT integrators fight to keep control over their devices. Users and integrators must know who they are up against to create stronger strategies to keep their IoT devices on their side.
What are IoT botnets?
Traditional botnets or bot networks, are networks of computers (called zombies) cybercriminals have taken control over using a malware. Cybercriminals remotely utilize the resources of compromised computers that make up a botnet to conduct attacks like distributed denials of service (DDoS) or activities like cryptocurrency mining. Much in the same way, IoT botnets are a collection of smart devices hijacked by cybercriminals largely with the same end goal as traditional botnets.
IoT devices also have processing capabilities and can act like simple versions of computers with more specialized functions. When these devices flooded the market, however, not all of them had adequate security to fend off cyberattacks that were possible on their specifications. IoT devices went online in homes and offices without the accompanying security awareness that have gradually been developed for computers. Making a perfect recipe for IoT botnets and a slew of other threats.
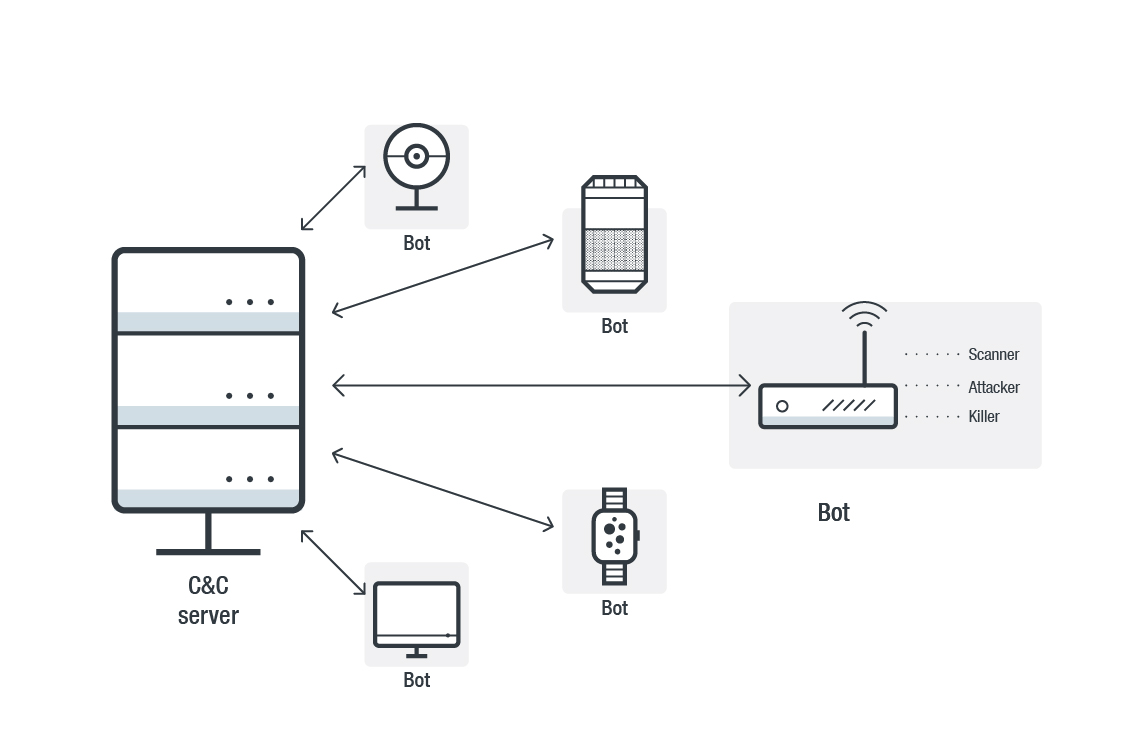
Figure 1. Components of an IoT botnet
In terms of composition, IoT botnets still closely resemble traditional botnets, in that it has two major components. One is the command and control (C&C) server where a threat actor sends commands from and control the botnet. And the second are the bots or zombies that are individually hijacked or infected devices that have become part of a larger network of similarly infected bots. These bots can consist of other common components, like a scanner for other vulnerable devices, killer of competing malware, attacker that performs DDoS, and for some, a cryptocurrency mining payload.
History of IoT botnet malware
The first recognized IoT botnet malware appeared more than a decade ago and illustrated the above mentioned components. Several others followed that became the building blocks of the campaigns seen today. Here are some of the notable IoT botnet malware discovered through the years.
Hydra
Hydra was released in 2008 as an open source botnet framework and infected routers. It also had DDoS and spreading capabilities, which are staples of future IoT botnet malware families.
Several other malware variants were linked to Hydra. In 2009, one of them was discovered in the wild and was called Psyb0t. It targeted routers and DSL modems, spreading to other IoT devices, primarily through Telnet and SSH access. Armed with thousands of common usernames (6,000) and passwords (13,000), it also used brute force to access devices. Other notable malware variants that closely resembled Hydra and Psyb0t were the Chuck Norris and Tsunami.
Aidra
Aidra was created in 2012 and is described by its own author as an “IRC-based mass router scanner exploit.” It spread by searching for open telnet ports that are accessible using default credentials. Like Hydra, it is also an open source project with a code accessible online. The researchers who discovered the malware variant found that in 2014, it was also used to make infected devices mine cryptocurrency.
BASHLITE
This malware is also named Lizkebab, Torlus, and gafgyt. BASHLITE (detected as ELF_BASHLITE.A) was first discovered in 2014 when it used ShellShock or the bash vulnerability to compromise Linux-based IoT devices and launch DDoS attacks. In 2016, it had made a resurgence by infecting 1 million devices likely because its source code had been leaked back in 2015, allowing more developers a chance to enhance it. Most of the affected devices were digital video recorders (DVRs) and cameras, routers, and Linux servers.
BASHLITE is still active up to the present. In 2019, Trend Micro discovered a variant that infected WeMo devices to mine cryptocurrency and another variant later in the year that called itself “Ayedz”, which targeted routers.
LuaBot
LuaBot is notable for being the first malware variant written in the LUA programming language that targeted Linux servers and IoT devices. Further investigation about LuaBot revealed that aside from adding devices to a botnet, it also conducted application level DDoS attacks. This malware was also capable of bypassing DDoS firewall protections of certain providers.
Remaiten
Remaiten was released in 2016 and was also known as KTM-RM. It combines the DDoS features of Tsunami (a mentioned Hydra variant) and an improved version of the scanning abilities of BASHLITE. Once Remaiten has acquired access to IoT devices, it downloads bot executable for many embedded architectures used in these devices, allowing it to launch attacks adapted for specific architectures. Although much less known than Mirai, which was released in the same year, Remaiten is notable for its sophistication and effectiveness on most embedded architectures of IoT devices.
Mirai
Since it exploded into notice in 2016, Mirai had become the most famous IoT malware in existence. Although less sophisticated than Remaiten, it garnered more attention for its massive DDoS campaigns on well-known websites. In a single year, it had taken down Krebs on Security and OVH using thousands of compromised IoT devices, which accounted for its initial notoriety.
Mirai’s attack on Dyn, a managed DNS service provider, had caused critical disruptions for Dyn’s customers—major websites like Amazon, Twitter, Spotify, Reddit, and AirBnB. This “achievement” cemented Mirai’s status as the most formidable botnet malware ever known and earning it the distinction as the malware that “brought down the internet”.
The DDoS attack on Dyn was recorded at an impressive 1.2 Tbps, due to the 100,000 IoT devices hijacked for the attack. What made the Mirai attack additionally memorable is the fact that most of its targets are innocuous household IoT devices like home routers, baby monitors, and security cameras. Because of the weak or inadequate security on these devices, Mirai was able to use an initial list of 64 common username and password to hijack devices. Despite its simplicity, its success had been due to how well the malware infected thousands of insecure IoT devices and coordinate them in a single DDoS attack.
Since Mirai’s source code had been leaked to the public, developers continue to use its code to spawn new variants that have plagued IoT devices over the years.
Linux/IRCTelnet
This malware is also known as NewAidra but its components are largely built from many IoT botnet predecessors also on this list. It takes parts from Aidra (root code), Tsunami (IRC protocol), BASHLITE (infection techniqies), and Mirai (credential list). It targets DVRs and IP cameras. At the time of its release in 2016, it had infected 3,500 in just five days. Linux/IRCTelnet demonstrated how developers build on other malware to create new and more powerful campaigns.
Persirai
Trend Micro discovered Persirai (detected as ELF_PERSIRAI.A) in 2017. It was among the botnet malware families vying for control over unsecure IP cameras and had been targeting over 1,000 models at the time of its discovery.
Like many IoT botnet variants, it uses the Universal Plug and Play (UPnP) protocol to spread to other IP cameras. Exploiting three vulnerabilities, the malware can acquire user passwords and conduct command injections regardless of password strength. It also has a “self-defense” component that fends off other malware that tries to infect a device it has already infected.
The present state of IoT botnets
Similar to Linux/IRCTelnet, many of the IoT botnet malware seen today are modeled, if not almost exactly copied, from the source code of decades of IoT botnet malware. Mirai, especially, has led to many new campaigns seen today and it would be safer to expect more moving forward. Trend MIcro's roundup of the first half of 2019 showed an increase in the number of routers involved in possible inbound attacks (from the internet and the devices connected to them) during the second half of 2018 that remained steady going into 2019.
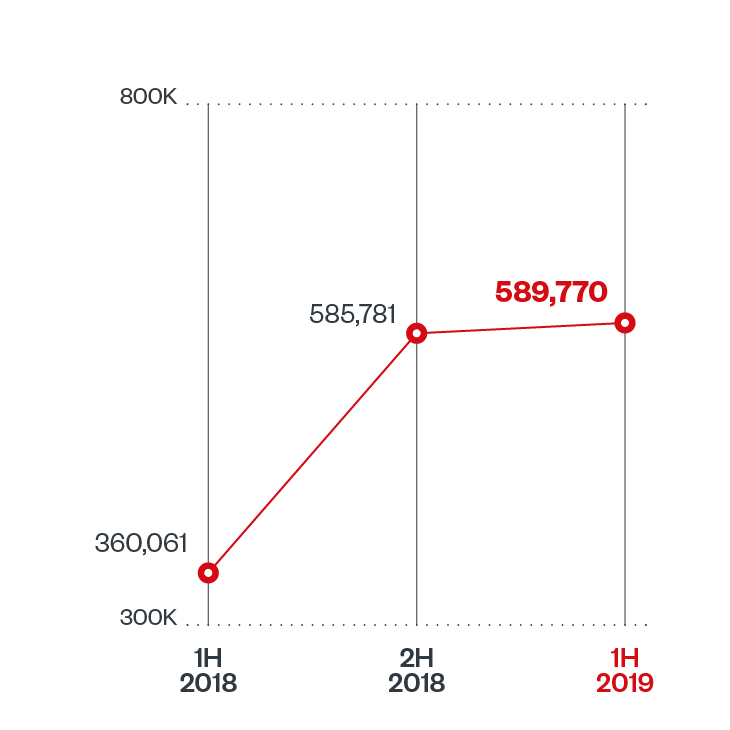
Figure 2. Half-year comparison of routers identified to have been involved in possible inbound attacks
Based on our Smart Home Network detections, going into the second half of 2019, this trend remained the same even spiking in the month of October, with a total count of 114,066,704 more than double of that of August and September’s detections.
Current characteristics and techniques employed by IoT botnets
The cyberattacks in 2019 reflect not only the continuing presence of IoT botnets in the threat landscape, but also reflect the trend among the cybercriminals behind them. In this section, we list down the techniques and characteristics of the IoT botnets we saw this year.
Using old and patched vulnerabilities
A large part of what makes IoT botnets spread successfully is because of unpatched vulnerabilities. Users do not apply the necessary patches as soon as they are made available, allowing malware to find an opening to hijack devices. This was evidenced in many of the attacks in 2019.
Early in the year, we had discovered the exploits of the ThinkPHP vulnerability patched in 2018 by Yowai and Hakai, which are new variants of Mirai and Gafgyt respectively.
In March, we also found another variant of Mirai using thirteen vulnerabilities to hijack routers. This is the first time all thirteen had been seen used in a single campaign, though all had been used in separate attacks by different malware variants, leading researchers to speculate that the author had simply copied the code from other variants.
Following our March discovery, we then saw several campaigns happening one after the other, all of which using various exploits to target routers. These included Ayedz a Bashlite variant, Asher a Mirai variant, and Neko.
Cryptocurrency mining
Malicious cryptocurrency mining still remained laced to IoT botnet attacks. As mentioned earlier, predecessors of IoT botnet malware use malicious cryptocurrency mining as a payload of their attacks. Traditional botnets also exhibited this capability, so it is of no surprise that threat developers of IoT botnet malware would also try this tactic to profit more from their attacks. This is reflected in a new variant of BASHLITE we saw targeting WeMo devices to mine cryptocurrency.
Hiding their C&C and unique evasion tactics
IoT botnet malware from 2019 showcased techniques to evade the notice and pose challenges for security researchers. One of the notable techniques we saw was employed by another Mirai variant. It kept its C&C hidden in the Tor network to avoid its IP address being tracked and consequently shut down when reported to domain hosts.
Another IoT botnet malware we saw from this year used a unique protocol to evade detection. The use of a new protocol also made it harder for security researchers to enter the C&C of the campaign. The case demonstrated how the developer behind it anticipated the typical actions of a security researcher trying to crack down their botnet campaign.
These trends reflect the current mindset of cybercriminals behind IoT botnet campaigns. The continued use of cryptocurrency mining payloads show how they would like to get the most value out of their attacks. The repetitive use of certain exploits reflects more on cybercriminal’s perception of users, believing that these vulnerabilities are left unpatched. Employing unique evasion tactics demonstrate how they continuously find ways to stay hidden from security experts trying to take them down.
The future of IoT botnets
Another way cybercriminals monetize IoT botnets is by simply selling them to interested buyers. A research we had done on the cybercriminal underground revealed a market for IoT botnets in several underground communities. The developer behind Satori is a well-known example of entities who both used and rented out created botnets. The presence of this market means that there are cybercriminals who continue to create IoT botnets because there are buyers interested in using them for whatever motivation. The bottom line being, IoT botnets would remain a part of the threat landscape in the coming year.
This outlook should be enough impetus for IoT stakeholders to strengthen their defenses against future botnet attacks. Botnets effects are always two-fold: not only do they render devices unavailable, they can also cause massive attacks to another target. Looking at how prolific IoT botnets are today could seem overwhelming. But they do highlight how the security of the internet is a shared responsibility. When users, manufacturers, and organizations share a united front in improving the security of the IoT, cybercriminals will find it harder to use the technology to wage their battles for them.
Here are some security best practices that can be applied for IoT devices:
- Start security from the design phase. Strong security should be present from the design phase when creating devices, to protect users and avoid issues once deployed.
- Apply patches as soon as they become available. Applying patches as soon as they become available is the best way of narrowing openings for potential attacks.
- Use secure configuration. Strong configuration settings for devices allows integrators to better understand their devices and prevent the success of unforeseen attacks.
- Use strong and hard to guess passwords. Brute force attacks have been a consistent part of IoT botnet malware routines. Strong passwords can prevent many of these attacks from accessing devices.
- Apply network segmentation. Using network segmentation isolates malware that have successfully penetrated defenses.
Users can also employ multilayer defenses that also provide better visibility as the Trend Micro™ Security and Trend Micro™ Internet Security solutions, which offer effective safeguards against threats to IoT devices through features that can detect malware at the endpoint level. Connected devices can also be protected by security software such as the Trend Micro™ Home Network Security and Trend Micro™ Home Network Security SDK solutions, which can check internet traffic between the router and all connected devices. The Trend Micro™ Deep Discovery™ Inspector network appliance can monitor all ports and network protocols for advanced threats and protect enterprises from targeted attacks.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One