With contributions from Shingo Matsugaya
In this report, we discuss in depth our monitoring of the ransomware landscape during the second half of 2023, with a focus on the families responsible for pulling in the highest number of attacks: LockBit, BlackCat, and Clop. Since 2022, LockBit and BlackCat consistently ranked among the ransomware-as-a-software (RaaS) providers with the most detections.
LockBit, which was behind 25% of all ransomware leaks in 2023, has undergone multiple iterations in an effort to remain a prominent RaaS provider; its most recent "Green" version was released in January of the same year. However, Trend Micro worked closely with the UK's National Crime Agency (NCA) in 2024 and provided threat intelligence for the NCA’s detailed analysis of LockBit-NG-Dev, an in-development version of LockBit. The analysis disrupted LockBit's operations by effectively making its entire product line unsuitable for criminal purposes.
BlackCat had made a hefty windfall prior to its shutdown at the hands of law enforcement toward the end of 2023: The Federal Bureau of Investigation (FBI) claims that, as of September 2023, the ransomware gang had raked in more than US$300 million worth of ransom payments from over 1,000 victims around the world, most of whom were located in the US.
Clop (sometimes stylized as “Cl0p”) also made headlines throughout 2023 owing to its abuse of CVE-2023-34362, a vulnerability in Progress Software’s MOVEit Transfer tool, that enabled Clop’s onslaught of data thefts affecting organizations worldwide. Progress has since released a security advisory regarding the vulnerability, as well as a service pack in July addressing three additional vulnerabilities — CVE-2023-36934, CVE-2023-36932, and CVE-2023-36933 — found in MOVEit Transfer.
This report is based on data from the leak sites of RaaS and extortion groups, Trend’s open-source intelligence (OSINT) research, and Trend Research telemetry data collected from July 1 to Dec. 31, 2023.
Active RaaS and RaaS-related groups grow more crowded as their victim counts soar
Our telemetry showed that over the third and fourth quarters of 2023, we detected and blocked a total of 7,472,013 ransomware threats across email, URL, and file layers — a 11.6% rise in overall ransomware threat detections compared to that in the first six months of the year, which had 6,697,853 total detections.
Data from leak sites, on which ransomware operators publish their successful attacks on organizations that refused to pay the ransom amount, shows that the number of ransomware victims totaled 2,524, representing a 26.3% increase from that of the first half of 2023. Notably, the number of active RaaS and RaaS-related groups had also risen to 52 over the second half of the year, representing a 15.6% growth.
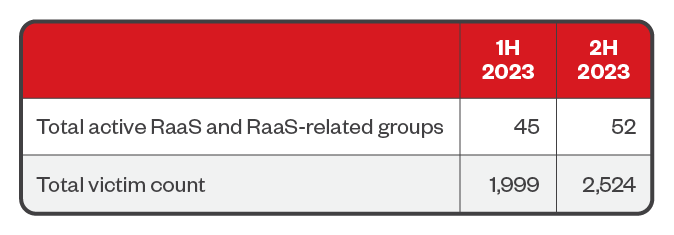
Table 1. The numbers of active RaaS and extortion groups and victim organizations of successful ransomware attacks in 2023
Sources: RaaS and extortion group leak sites
Prominent ransomware actors continue to head the most active RaaS groups in the second half of 2023
In a repeat of the first half of the year, data collected from leak sites revealed that the notorious RaaS operators LockBit, BlackCat, and Clop are still behind some of the highest numbers of successful ransomware attacks. LockBit retained its long-held spot as the top ransomware family, with 18.6% of the total number of victim organizations during the third quarter and 22.8% of the fourth quarter. Meanwhile, 12.9% and 0.7% of the total victim counts were attributed to Clop over the same periods. BlackCat was responsible for 8.1% of victimized organizations in each of the two quarters.
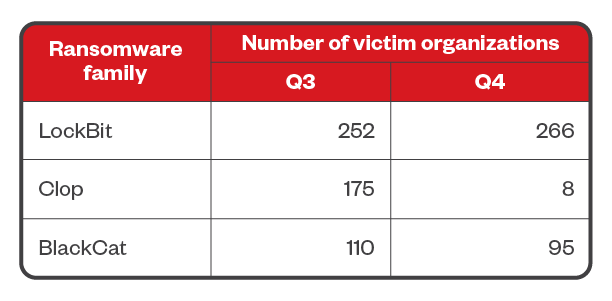
Table 2. The most active ransomware families used in successful RaaS and extortion attacks in terms of victim organizations from July 1 to Dec. 31, 2023
Sources: RaaS and extortion group leak sites
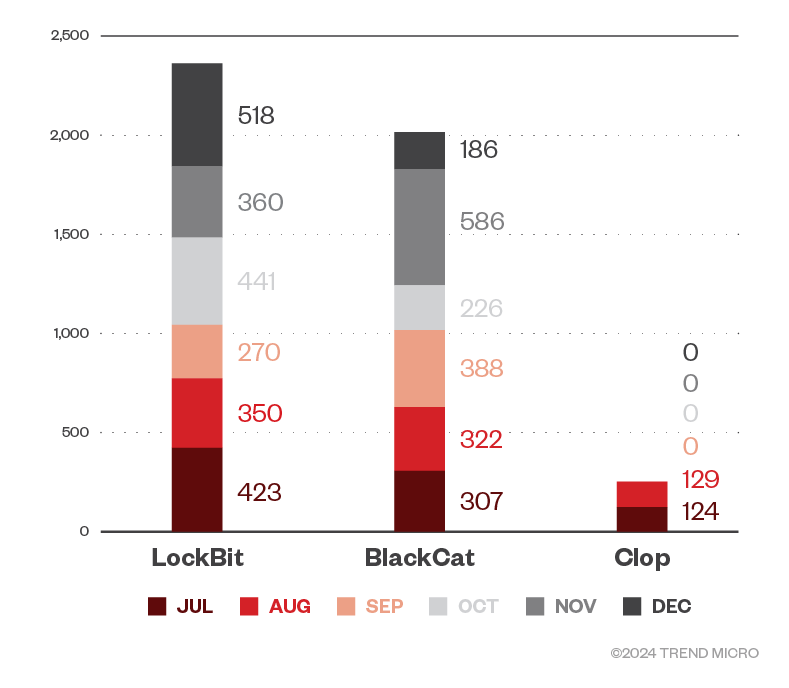
Figure 1. The numbers of ransomware file detections of LockBit, BlackCat, and Clop ransomware in machines per month during the second half of 2023
Source: Trend Research telemetry
LockBit struggles to maintain its dominance among RaaS operators
In November 2023, LockBit 3.0 attacks were found exploiting CVE-2023-4966. Dubbed “Citrix Bleed,” this vulnerability affected Citrix NetScaler ADC and Gateway products to pilfer data, encrypt files, and disrupt operations of companies around the world. Big-game victims include Boeing, the Industrial and Commercial Bank of China (ICBC), and the Australian arm of DP World, a logistics company based in the United Arab Emirates (UAE). Although a patch was made available in October, over 10,000 Citrix servers (most of which were located in the US) were still vulnerable to this flaw when the attacks took place.
LockBit-NG-Dev might have been designed as an upcoming version 4.0 of the LockBit ransomware, which has been subjected to many copycat groups like Spacecolon and Flamingo ever since LockBit’s ransomware builder was leaked in 2022. The rise of LockBit clones vying for RaaS market share, on top of internal strife within LockBit’s ranks, have been contributing factors to the group’s continued decline: Its number of successful attacks steadily dropped in late 2022 and throughout the greater part of 2023 despite the transition from LockBit 2.0 to LockBit 3.0. This downward spiral culminated in a decisive blow on Feb. 20, 2023, when the NCA-led Operation Cronos — an international task force that involved the cooperation of the FBI and nine participating countries — announced that it had successfully seized control of LockBit's source code, the technical infrastructure through which affiliates carried out attacks, as well as its leak site. The NCA then used this site to expose information about LockBit's inner workings.
BlackCat refines its extortion playbook prior to shutdown
BlackCat, also known as ALPHV, claimed responsibility for a July 2023 ransomware attack on Seiko Group Corporation (SGC), which the company confirmed later in August. About 60,000 items of data, including customer data and personnel details, from SGC, Seiko Watch Corporation (SWC), and Seiko Instruments Inc. (SII) were compromised as a result of the attack.
Following the gang's breach of Estée Lauder and the cosmetics company's subsequent refusal to engage in ransom negotiations, BlackCat also augmented its extortion strategy by offering an API for its leak site in July 2023 that heightened the visibility of its ransomware attacks. Additionally, the ransomware group appeared to divert from the conventional multi-extortion model in November 2023, when it lodged a complaint with the Security and Exchange Commission (SEC), claiming that one of its ransomware victims, MeridianLink, failed to disclose a breach within the SEC’s four-day requirement in what appeared to be a new tactic to strong-arm the victim organization into paying the ransom.
However, as with LockBit, an international law enforcement operation headed by the FBI was able to infiltrate and disrupt BlackCat's infrastructure. In December, the operation breached BlackCat's servers and took down its leak site after successfully seizing hundreds of public/private key pairs for BlackCat’s Tor sites. The FBI also offered a decryption tool that more than 500 BlackCat’s victims worldwide could use to restore their systems and avoid around US$68 million in ransom payouts.
Clop continues its wave of high-profile data theft attacks
Clop's mass exploit of the MOVEit Transfer zero-day vulnerability in May 2023 continued well into the latter half of the year. Clop initially used Tor sites, then sites on the clear web, to distribute the data stolen from its MOVEit attacks. But in August, the ransomware group shifted again to using torrents and set up an accompanying Tor site containing instructions on how to use torrent clients. This was done as a faster and decentralized means of releasing the data, making it more difficult for law enforcement to shut down the leaks.
More than 2,000 organizations and 94 million individuals have since been affected by Clop's attack spree. Counted among the victims was Flagstar Bank, which disclosed in October that the data of over 800,000 US customers had been leaked. In the same month, the data of more than 6,000 Sony employees had also been compromised in a MOVEit-related attack.
Small businesses were the target of choice among ransomware operators
Smaller organizations (which, compared to larger companies, typically have less resources to respond to and recover from cyberattacks) were the hardest-hit by the biggest ransomware families during the second half of 2023. Of LockBit’s 518 total victims, 61.8% were small businesses, while medium-sized businesses and large enterprises made up 19.9% and 6.2%, respectively. Likewise, the majority of BlackCat victims were small businesses at 50.7%, followed by midsize and large ones that accounted for 27.3% and 15.6%, respectively. Small organizations made up 62.3% of Clop’s 183 victims, midsize businesses composed 19.7%, and large businesses constituted 16.9%.
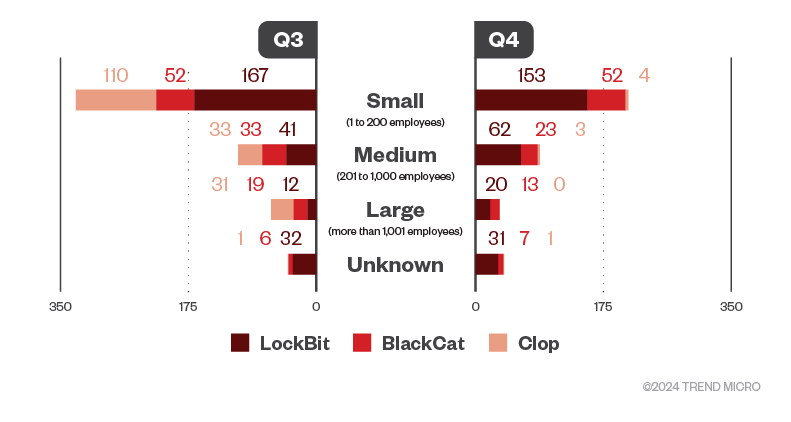
Figure 2. The distribution by organization size of LockBit, BlackCat, and Clop ransomware’s successful attacks in terms of victim organizations in the third and fourth quarters of 2023
Sources: LockBit, BlackCat, and Clop’s leak sites and Trend's OSINT research
Banking was consistently under attack throughout the second half of the year
Our telemetry showed that banking steadily topped the list of the most targeted industries based on the number of ransomware file detections, although a surge in detections was observed in the technology industry during the last quarter of 2023. Fast-moving consumer goods (FMCG), which came in third, had substantial ransomware detections from August to November.
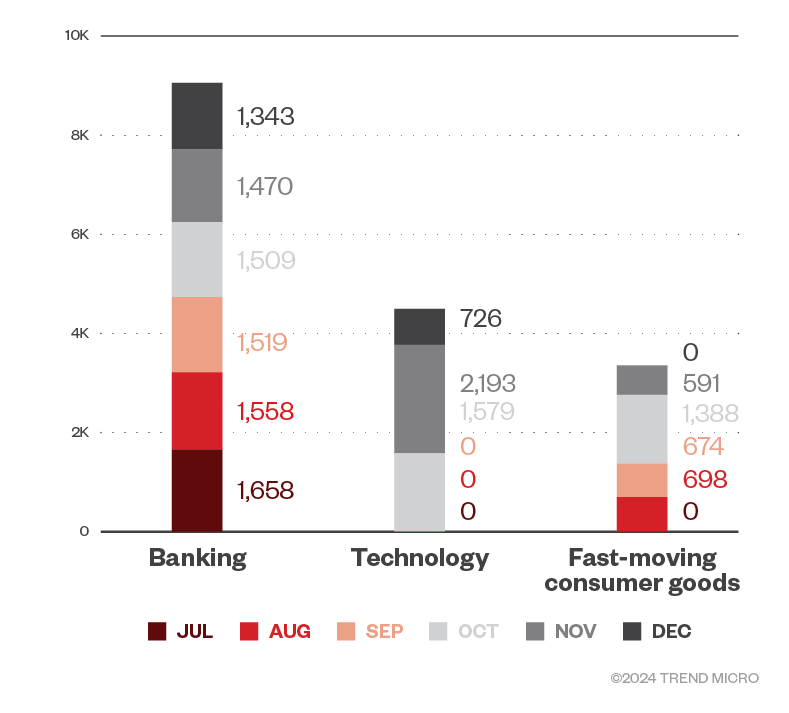
Figure 3. The top three industries in terms of ransomware file detections in machines per month in the second half of 2023
Source: Trend Research telemetry
According to ransomware groups’ leak sites, the manufacturing industry sustained the highest number of ransomware attacks, supplanting finance as the attackers’ primary focus during the first half of the year. However, organizations in finance were still commonly targeted over the third and fourth quarters of 2023, along with those in healthcare and IT.
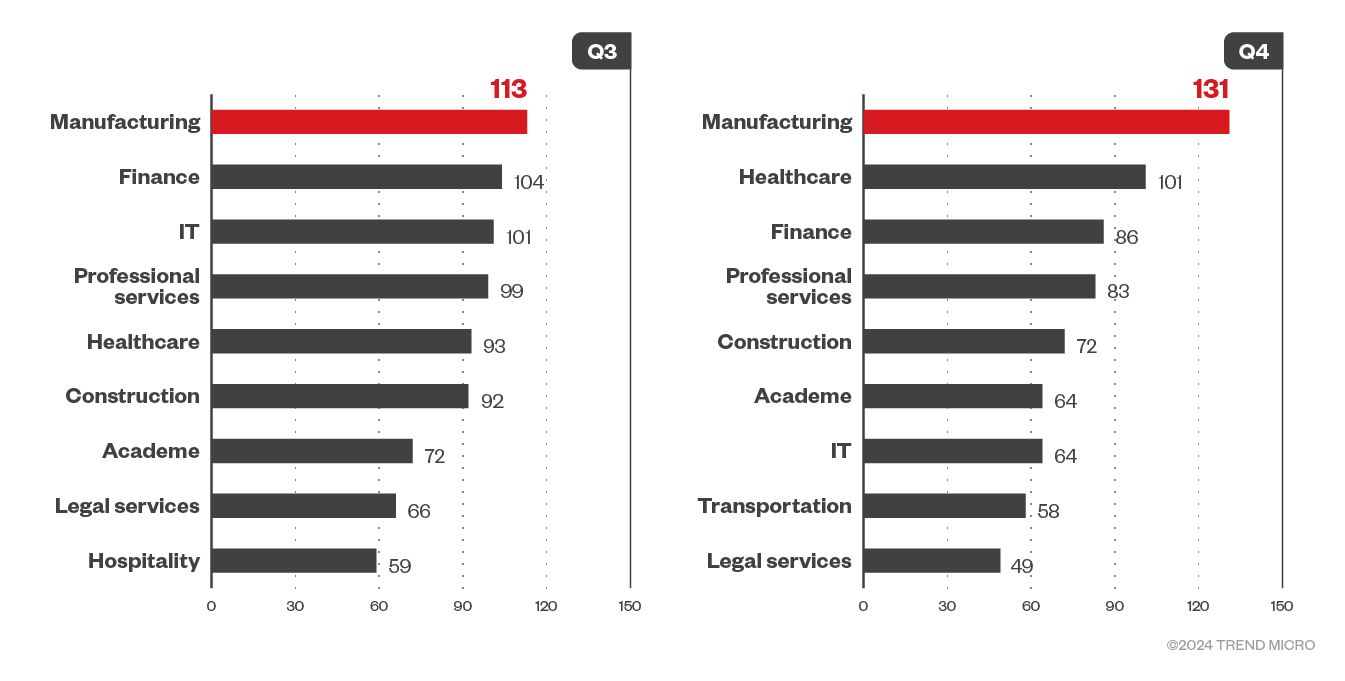
Figure 4. The top 10 industries affected by successful RaaS and extortion attacks in the third and fourth quarters of 2023
Sources: RaaS and extortion group leak sites and Trend’s OSINT research
LockBit ransomware operators targeted a variety of organizations, primarily preying on construction, professional services, and academic institutions in the third quarter, before switching their attention to organizations in manufacturing, finance, and healthcare. This is reflected in LockBit’s big-name victims in the second half of 2023, which included aerospace manufacturer Boeing and the biggest lender in China, the ICBC.
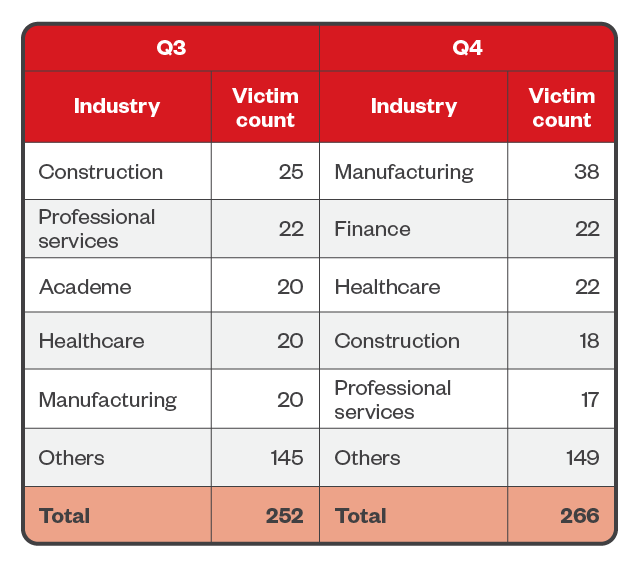
Table 3. The top five industries affected by LockBit’s successful attacks in terms of victim organizations in the third and fourth quarters of 2023
Sources: LockBit’s leak site and Trend’s OSINT research
Although legal services suffered the most BlackCat ransomware attacks in the third quarter, healthcare and finance also consistently placed among the group’s most targeted sectors. These made up 10.7% and 11.2%, respectively, of BlackCat’s 205 total victims over the last six months of the year.
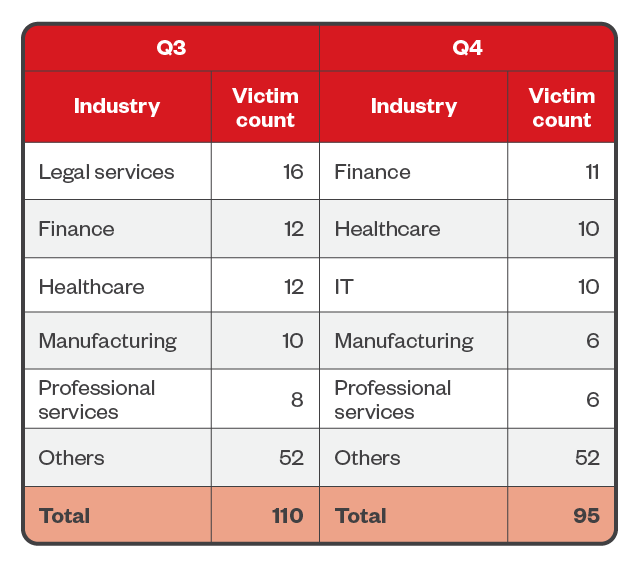
Table 4. The top five industries affected by BlackCat’s successful attacks in terms of victim organizations in the third and fourth quarters of 2023
Sources: BlackCat’s leak site and Trend's OSINT research
Most of Clop’s attacks in the second half of the year took place during the third quarter, with the ransomware group appearing to have lost its momentum heading into the tail end of 2023. Nearly a fifth of Clop’s 183 victims belonged to the IT industry, while 15.8% were composed of finance organizations.
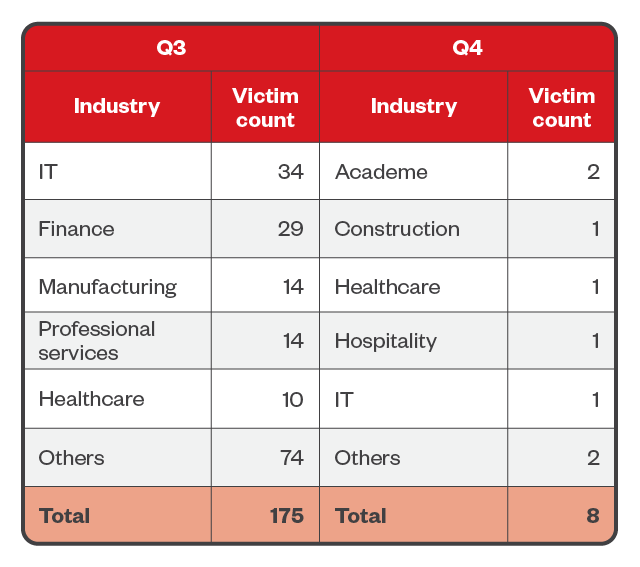
Table 5. The top five industries affected by Clop’s successful attacks in terms of victim organizations in the third and fourth quarters of 2023
Sources: Clop’s leak site and Trend’s OSINT research
The UK and North American countries bear the brunt of ransomware attacks
Like in the first half of the year, organizations in the US, UK, and Canada still ranked as the countries with the highest numbers of ransomware attacks throughout the third and fourth quarters of 2023. Victim counts rose across these three countries, with US-based victims tallying at 1,188, a 20% rise from the first two quarters. Similarly, the number of UK-based victims also increased by 23.5%, while Canada-based victims increased by 27.3%.
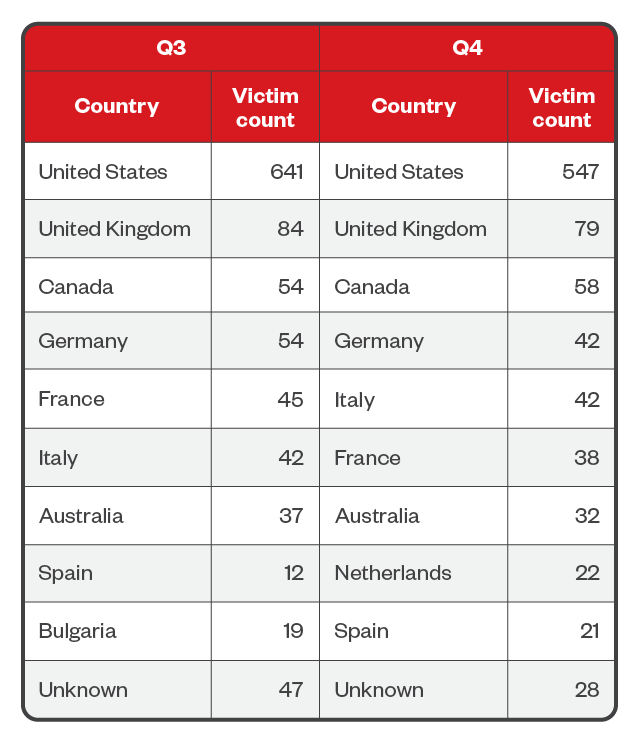
Table 6. The top 10 countries affected by successful RaaS and extortion attacks in the third and fourth quarters of 2023
Sources: RaaS and extortion group leak sites and Trend's OSINT research
LockBit actors focused most heavily on North America, with 45% of their attacks targeting the region. Europe and Asia-Pacific came in at second and third place, with 26.8% and 12.4% of LockBit attacks, respectively.
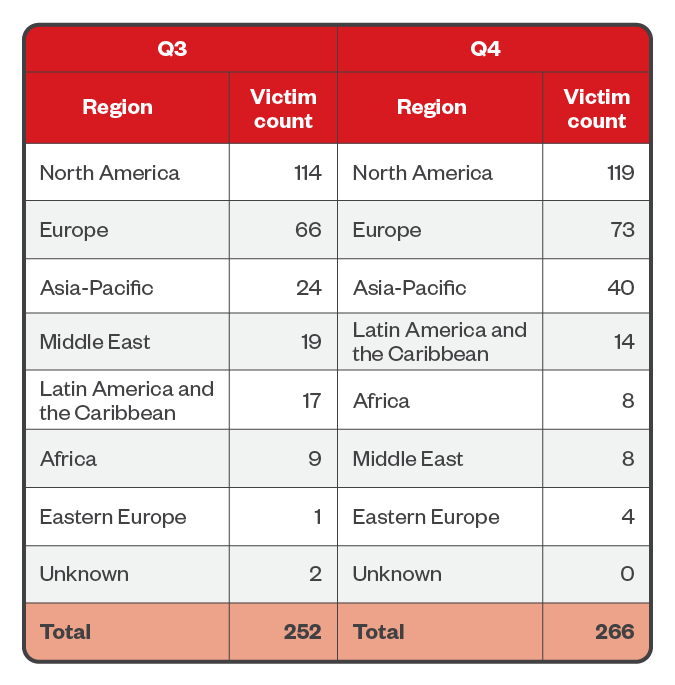
Table 7. The top regions affected by LockBit’s successful attacks in terms of victim organizations in the third and fourth quarters of 2023
Sources: LockBit’s leak site and Trend’s OSINT research
North America also accounted for 58% of BlackCat ransomware attacks during the second half of the year. This is followed by Europe and Asia-Pacific at 17.1% and 14.1%, respectively, though these two regions tied for second most-targeted sector in the fourth quarter.
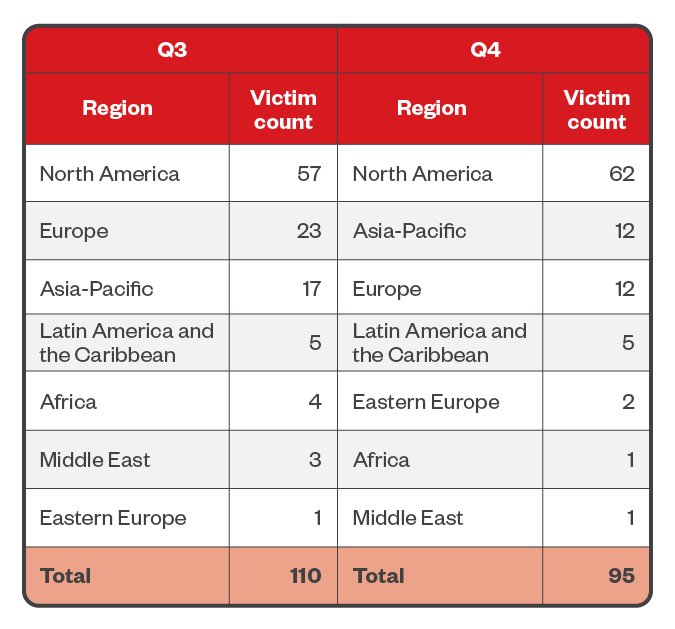
Table 8. The top regions affected by BlackCat’s successful attacks in terms of victim organizations in the third and fourth quarters of 2023
Sources: BlackCat’s leak site and Trend’s OSINT research
At 69.4%, the lion’s share of Clop attacks was likewise concentrated in North America; in fact, all of Clop’s ransomware attacks during the entirety of the fourth quarter were in this region. Europe placed at a distant second at 23%, while attacks in Asia-Pacific placed at 4.9%.
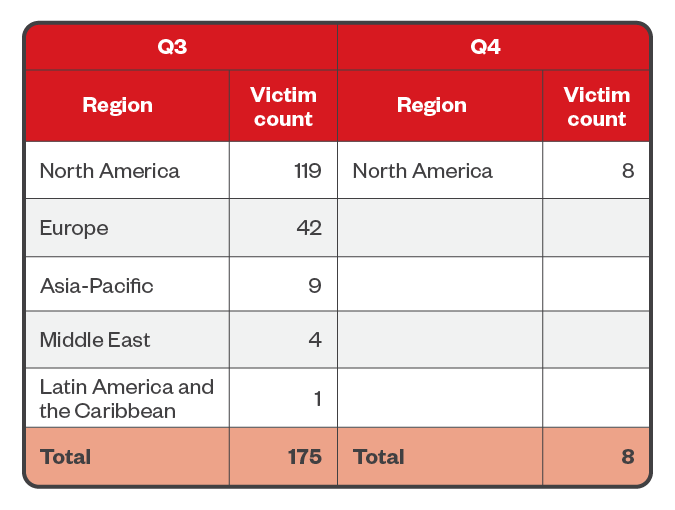
Table 9. The top regions affected by Clop’s successful attacks in terms of victim organizations in the third and fourth quarters of 2023
Sources: Clop’s leak site and Trend’s OSINT research
Mitigate the risk of ransomware attacks with cybersecurity best practices
Organizations around the world will continue to grapple with the dangers posed by ransomware attacks, which have evolved into an increasingly sophisticated and persistent threat. The call to effectively counter ransomware infections urges business leaders to remain vigilant and implement the following recommended cybersecurity practices:
- Enable multifactor authentication (MFA). Organizations should implement policies that require employees who access or store company data on their devices to enable MFA as an added layer of protection to prevent unauthorized access to sensitive information.
- Back up your data. Organizations should follow the “3-2-1 rule” to safeguard their important files: Create at least three backup copies in two different file formats, with one copy stored off-site.
- Keep systems up to date. Organizations should update all their applications, operating systems, and other software types as soon as vendors and developers release patches. Doing so minimizes the opportunities for ransomware actors to exploit vulnerabilities that enable system breaches.
- Verify emails before opening them. Malicious actors rely on tried-and-tested ways to compromise systems, such as using embedded links or executable downloads attached in emails sent to employees to install malware. Organizations should therefore train their employees to be aware of such methods to avoid them.
- Follow established security frameworks. There’s no need to reinvent the proverbial wheel. Organizations can craft cybersecurity strategies based on the security frameworks created by the Center of Internet Security (CIS) and the National Institute of Standards and Technology (NIST). The security measures and best practices outlined in these frameworks can guide members of an organization’s security team in developing their own threat mitigation plans.
Organizations can strengthen their cybersecurity infrastructure through multilayered detection and response solutions that can anticipate and respond to ransomware movements before operators can launch an attack. Trend Vision One™ is equipped with extended detection and response (XDR) capabilities that gather and automatically correlate data across multiple security layers — including email, endpoints, servers, cloud workloads, and networks — to prevent ransomware attack attempts.
Organizations can also benefit from solutions with network detection and response (NDR) capabilities, which can give them broader visibility over their network traffic. Trend Network One™ provides security teams with the critical network telemetry they need to form a more definitive picture of their environment, accelerate their response, and avert future attacks.
The supplementary data sheet for this report, including data from the leak sites of RaaS and extortion groups, Trend's OSINT research, and Trend threat intelligence, can be downloaded here.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Archive
- Phobos Emerges as a Formidable Threat in Q1 2024, LockBit Stays in the Top Spot: Ransomware in Q1 2024
- Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
- LockBit, BlackCat, and Clop Prevail as Top RAAS Groups: Ransomware in 1H 2023
- LockBit, BlackCat, and Royal Dominate the Ransomware Scene: Ransomware in Q4 2022
- LockBit and Black Basta Are the Most Active RaaS Groups as Victim Count Rises: Ransomware in Q2 and Q3 2022


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One