A Roadmap to Secure Connected Cars: Charting the WP.29's UN Regulation No. 155
 Download Identifying Cybersecurity Focus Areas in Connected Cars Based on WP.29 UNR155 Attack Vectors and Beyond
Download Identifying Cybersecurity Focus Areas in Connected Cars Based on WP.29 UNR155 Attack Vectors and Beyond
Connected cars are now on the way to becoming a regular part of everyday traffic all over the world. How should stakeholders make these vehicles more secure? The regulatory framework created by WP.29, UN Regulation No. 155 (UN R155), provides a guide, giving directions towards a safer path for connected cars moving forward.
Our research paper, “Identifying Cybersecurity Focus Areas in Connected Cars Based on WP.29 UN R155 Attack Vectors and Beyond,” focuses on the attack vectors defined in UN R155. We do so by putting each vector through the process of threat modeling. The result should help stakeholders identify which threats to prioritize. We also take a broader look at the landscape by predicting the evolution of these attack vectors and discussing other focus areas outside the scope of the proposal.
What is the WP.29 and UN Regulation No. 155?
WP.29 is short for the United Nations Economic Commission for Europe (UNECE) World Forum for Harmonization of Vehicle Regulations, which is a worldwide regulatory forum within the UNECE Inland Transportation Committee. WP.29 came up with a regulation that dealt with cybersecurity and cybersecurity management systems (CSMS) in vehicles. It requires manufacturers to adequately consider cybersecurity and demonstrate security best practices. The proposal was officially published and entered into force as UN Regulation No. 155 in January 2021. While the regulation is aimed at manufacturers, it has implications for the entire supply chain and is relevant to all connected car stakeholders.
A notable part of this document is Annex 5, which contains seven high-level and 30 sub-level descriptions of vulnerabilities and threats that include 69 attack vectors that directly affect vehicle cybersecurity, serving as a guide for stakeholders to better understand and mitigate these attack vectors. The attack vectors involve different factors that affect the connected car ecosystem as defined by the proposal, which are:
- Back-end servers
- Communication channels
- Update procedures
- Human error
- External connectivity
- Data/code
- Vulnerability hardening sufficiency
Annex 5 should not serve as a definitive checklist. It is meant as a guide for manufacturers. The next challenge posed by the regulation is for manufacturers to perform their own exhaustive risk assessments, which our paper aims to help with, beginning with the attack vectors in Annex 5.
Threat modeling
For this research, we used the DREAD threat model, which is one type of qualitative risk analysis. We did the exercise by applying current technologies, hacker tools, techniques, and procedures (TTPs), and learnings from published research in this domain to determine risk levels and answers to the DREAD questions. The compounded rating determined each threat’s risk level — low, medium, or high.
Low-risk threats
Low-risk attack vectors would have little impact if successfully conducted. Threats are also rated as low-risk if they are difficult to execute and demands advanced skills and in-depth knowledge from its threat operator as they will be difficult to execute, and hence have a lower likelihood of impacting daily drivers. Here are some examples of low-level risk threats:
- Spoofing of messages by impersonation. This attack will need to be highly targeted to succeed.
- Communications channels permitting the manipulation of vehicle-held data/code. Car communication attacks that involve intercepting information, monitoring communications, and gaining unauthorized access to files or data are all typically passive attacks that will likely have no effect on road safety.
- Innocent victims being tricked into taking an action to unintentionally load malware or enable an attack. This is a classic phishing scheme rated as low, since compromising the head unit would be an easier option than installing malware.
Medium-risk threats
Medium-risk attack vectors can have a moderate impact if successfully executed. Compared to low-risk threats, they are also more likely to be executed by threat operators, but with some limitations. Here are some examples of medium-risk threats:
- Loss of information in the cloud. Even if there is data loss in the cloud, exploiting the data supply can be difficult; therefore, damage potential would depend on the data stolen and its likelihood of misuse.
- Unauthorized internet access to the server. It is rare, but not improbable, for sensitive back-end servers to be exposed and discoverable online.
- Sybil attack (vehicle pretending to have more than one identity). This attack has a limited threat radius.
High-risk threats
High-risk attack vectors would significantly affect its target if successfully executed. Such attacks are also easily reproduced and requires little knowledge in order to conduct. Here are examples of high-risk threats:
- Sending a large number of garbage data to the vehicle information system, so that it is unable to provide services in the normal manner. Denial-of-service (DoS) attacks can cause widespread damage in a connected car’s ecosystem.
- Introducing malicious software or malicious software activity. Though difficult to execute as it requires middleware to work, attacks using malicious apps can potentially send dangerous inputs to the electronic control unit (ECU) while the car is on the road, jeopardizing road safety.
- Using remainders from development. Development remainders such as microprocessors, developer passwords, and debug ports can give attackers ECU access or gain higher privileges.
Future risk ratings
Our ratings for each of these attack vectors were based on current observations and recent research on connected car hacking. At present, we recommend stakeholders to focus on back-end security and data security. In the future, the focus must then shift to the communication channel as risks will dramatically increase in this aspect of connected cars. Most attack vectors related to the communication channel are considered low-risk threats, but we predict this will change as vehicles become more connected.
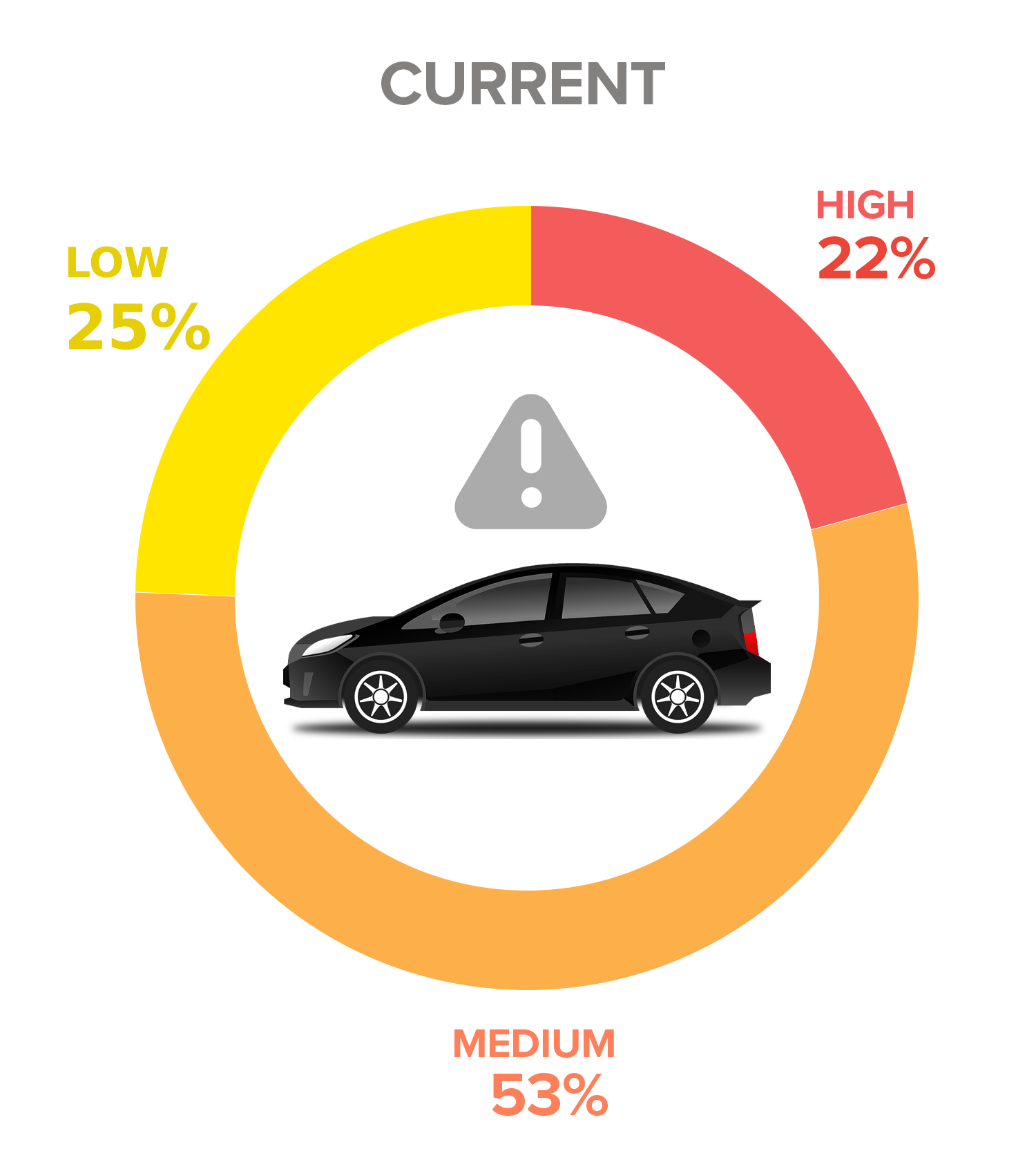
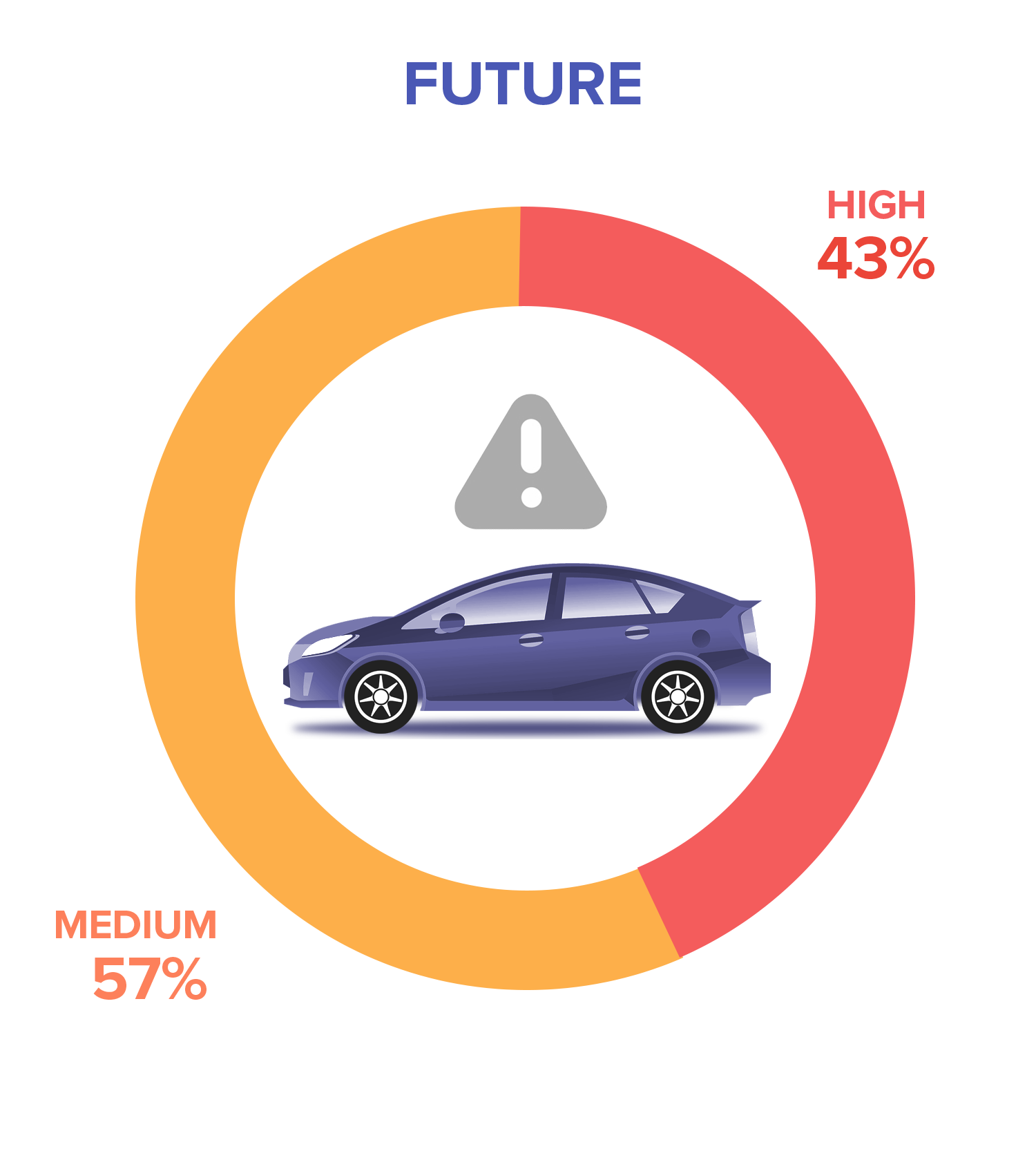
Figure 1. In the future, most of the attack vectors would transform into either medium-risk or high-risk threats.
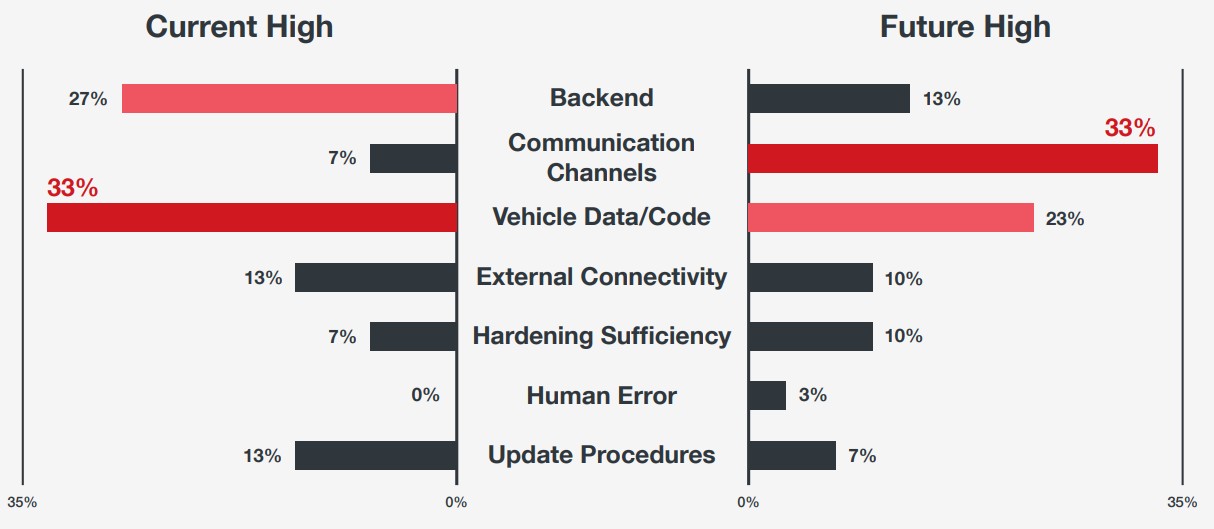
Figure 2. The type of attack vectors with high-risk ratings will change in the future, and therefore, so should the focus of security.
Additional focus areas
Aside from these attack vectors, stakeholders must remain vigilant against other potential threats that might arise. Based on our past research, we conducted cyberattack assessments on topics outside the scope of the WP.29 proposal. Other publications also brought forward notable security concerns in this field.
- Image processing attacks. Researchers have demonstrated that it is possible to fool vehicle cameras into misinterpreting roadway signs by adding small anomalies or stickers to road signs.
- Compromised roadway infrastructure. Most roadway infrastructures today are network- connected. Operators sometimes mistakenly leave these devices exposed online and these are discoverable by scanning services like Shodan.
- Compromised app-API supply chain. With car head units supporting app ecosystems, as well as being able to load authorized and unauthorized apps (in jailbroken phones), the app-API ecosystem will become a serious security problem in the near future.
- Social engineering attacks. It is possible to find more cybercriminals using known social engineering tactics on connected car users. Since modern cars are capable of interacting with mobile devices and head units being digital, this type of attack could prove effective.
We went beyond the proposal and introduced focus areas that stakeholders should be equally aware of.
Solutions for WP.29 defined threats
In line with our goal for this research, it is necessary for stakeholders to determine where they should place their focus. After all, security is a balance between benefit and cost. Having a clear hierarchy of priorities allows organizations to allocate their security resources more effectively and implement measures in phases.
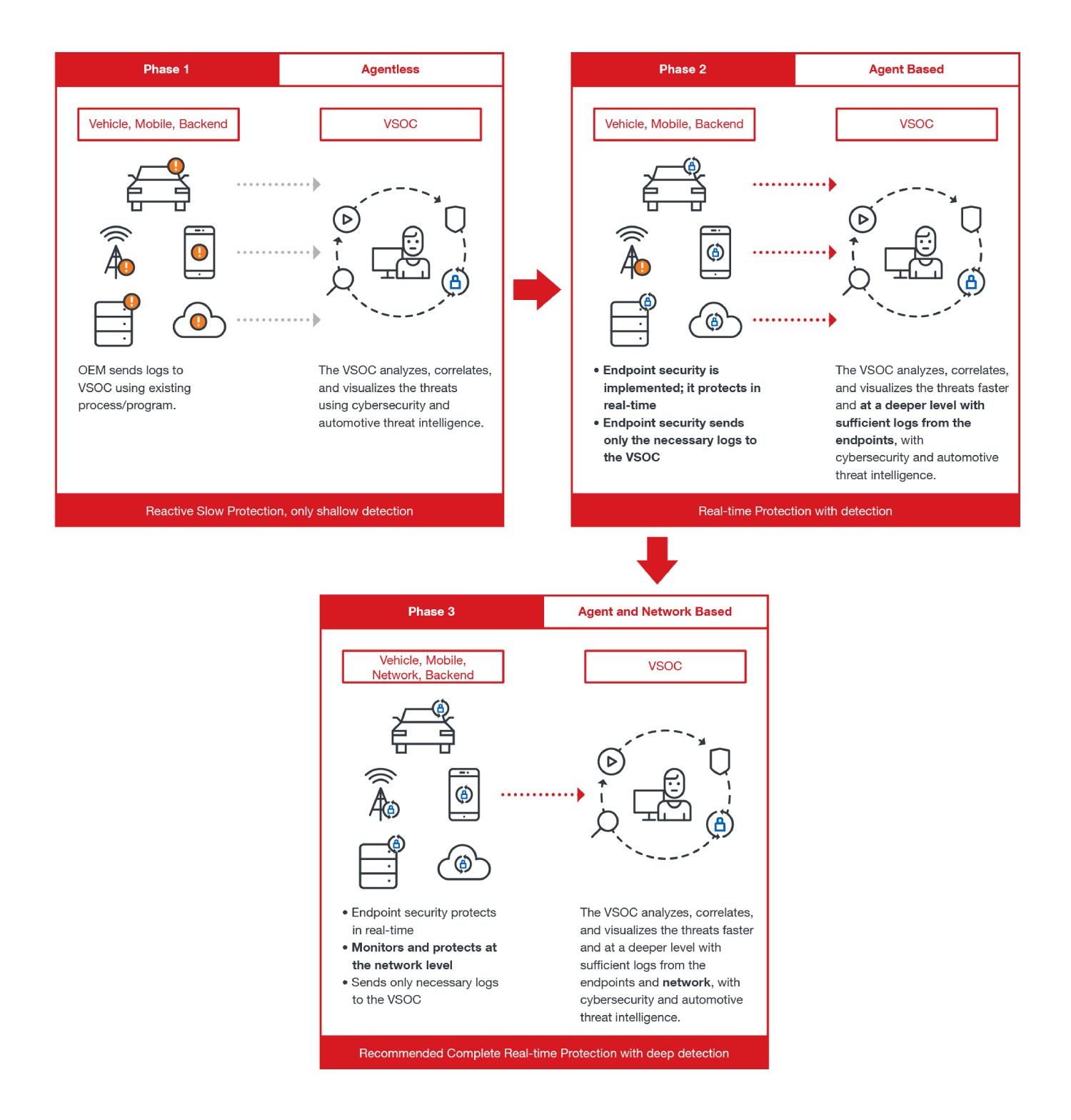
The WP.29 regulation is a correct regulatory step forward. It helps manufacturers and other stakeholders chart a course toward a safer connected car ecosystem while also leaving room for detours and reroutes, allowing them to remain adaptive to fast-paced technological advancements and for security to stay ahead of cybercriminals in a never-ending arms race.
To read the full research, please download “Identifying Cybersecurity Focus Areas in Connected Cars Based on WP.29 UN R155 Attack Vectors and Beyond.” The document contains the complete list of threat ratings we gave the WP.29’s defined attack vectors, with added observations and insights. A section is dedicated to our predictions on how these attack vectors will evolve in the next five to 10 years; it includes a list of the top present concerns and how these will shift given the direction of developing technologies. The research paper also contains a more detailed description of the other focus areas we have listed down here. It ends with a comprehensive solutions guide for addressing the WP.29-defined attack vectors and threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One