Facebook Users Should Not Take Threats Lightly
 View infographic: Spring Forward with Social Media
View infographic: Spring Forward with Social Media
An average person manages at least three social media accounts, the most prominent one being Facebook. The social networking giant created by Mark Zuckerberg currently has around 829 million active users per day and 654 million daily users on mobile. That’s a lot of people viewing and exchanging messages, links, photos, and videos.
Just imagine how much content these users post within 24 hours. Imagine the wealth of personal information available on just one site. It’s no surprise that cybercriminals have taken a liking to Facebook. With the site’s ever-evolving interface and set of features, the bad guys have no problem finding more ways of tricking and attacking unwary Facebook users.
Over the years, we’ve seen several online threats and scams taking advantage of the site and its features.
Phishing
In January 2009, phishers were able to hack into accounts and use them to defraud the friends of each account owner. In August of the same year, the bad guys took advantage of wall posts and streams to launch phishing attacks. In 2010, two years after Facebook Chat was introduced, phishers utilized the site feature to fool other Facebook users and steal their credentials.
Spam with malware
In May 2011, the bad guys went beyond phishing and started spreading malicious links on wall posts, events, and Chats. Clicking on the links led to the download of malware.
Credit card fraud
In October 2013, threats went mobile. We spotted fake mobile Facebook pages that were designed to steal credit card credentials.
Regular Facebook users might be able to identify scams from legitimate posts, but this does not give them a free pass to be careless while using the site. We always recommend that Facebook users apply strict privacy settings to protect their accounts and data from prying eyes. They should also be more discriminative of the people they add on the site. They can also invest in security solutions that protect social media use on both PC and mobile devices.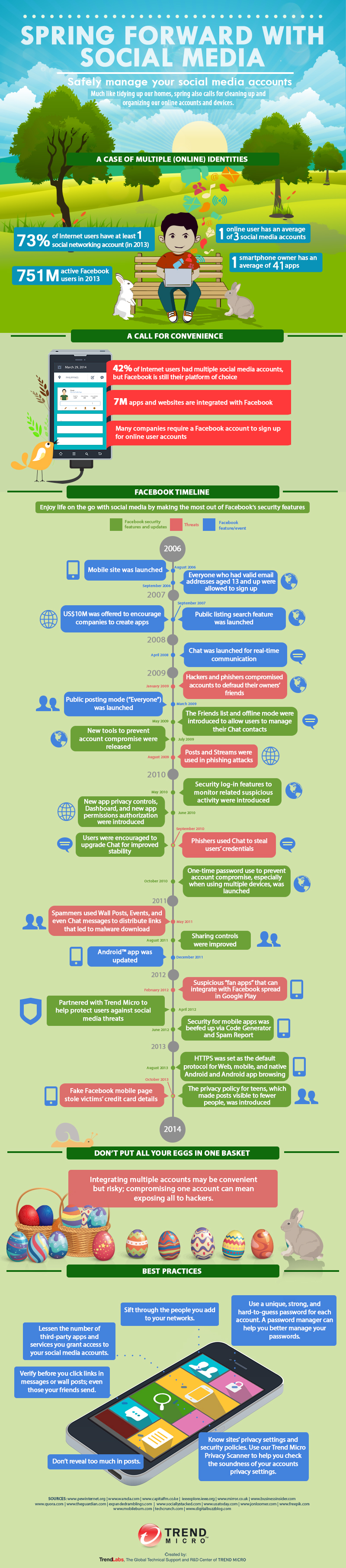
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One