Out on a Highway Run: Threats and Risks to ITSs and Smart Vehicles
 Today’s transportation systems not only get us from one point to another, but also work to answer issues in traffic management, insufficient resources, and the environmental impact of growing cities. Not anymore seen as only a tool for mobility, transportation systems are now viewed holistically as mobile computers to accompany, guide, and customize our trips wherever we go. The application of network technology in transportation led to Intelligent Transportation Systems (ITS), which also use data analytics that provide comprehensive insights relevant in resolving congested city concerns.
Today’s transportation systems not only get us from one point to another, but also work to answer issues in traffic management, insufficient resources, and the environmental impact of growing cities. Not anymore seen as only a tool for mobility, transportation systems are now viewed holistically as mobile computers to accompany, guide, and customize our trips wherever we go. The application of network technology in transportation led to Intelligent Transportation Systems (ITS), which also use data analytics that provide comprehensive insights relevant in resolving congested city concerns.
The research firm Counterpoint predicted that by 2022, the number of vehicles with embedded connectivity will grow by 270% — excluding those with already active connections and features for connecting users’ internet of things (IoT) — thanks in part to the European Union’s (EU) eCall initiative. Continued user interest in ITS, opportunities offered by 5G, and growing business opportunities from automotive-related enterprises such as insurance companies and original equipment manufacturers (OEMs) are also seen as growth factors in ITS adoption.
Moreover, ITS’ efficiency in infrastructure management and analytics research, as well as loss pre-emption -- life, maintenance, time, funds, and data -- has driven other countries to adopt ITS to automate and manage public infrastructure.
The expected increase in technology adoption, however, does not come without risks — from petty showcases of hacks to possibly bigger threats to safety and financial losses. In a 2018 study by the Ponemon Institute on the automotive industry’s procedures, the cybersecurity programs and practices set in automotive companies have yet to catch up to the technologies of these connected vehicles released in the market. In relation, Consumer Watchdog published a report concluding that a hack of connected vehicles during the rush hour can result to accidents equivalent to the scale of 9/11, definitively resulting in financial losses, damages to infrastructure, and loss of life. What can urban and government planners and developers do in order to secure their growing cities’ and smart transportation’s needs?
[Read: Securing the industrial internet of things: Protecting energy, water and oil infrastructures]
The ITS Framework
As discussed in Trend Micro’s paper, the ITS ecosystem integrates a number of sectors, components and operational systems to work, and a threat or an attack in one may cause other complications in its related industries – unauthorized intrusions via physical, network and wireless attack surfaces. The strategic framework applied on the ITS architecture enables designers and engineers to visualize and implement the technical details necessary, and there are six main categories by which the subsets can be grouped to represent specific functions in the architecture:
- Vehicles: Connected or autonomous units of transportation, usually embedded with wireless Local Area Network (wLAN) to access other internal or external IoT devices, or automated to navigate and sense its environment even without human input or intervention via advanced technologies such as cameras, light detection and ranging (LIDAR), sensors and tracking systems such as GPS.
- Roadway reporting: For real-time traffic and roadway conditions’ monitoring and efficient movement, commonly achieved with the use of systems such as cameras, detection systems, roadside weather stations, and sensors to send data back to a centralized control center.
- Traffic flow controls: Also for real-time traffic data collection and roadway flow conditions’ monitoring, this is achieved using traffic signal control systems, railway crossing barriers, dynamic message signs, and automated toll systems.
- Payment applications and systems: Automatically collect, manage and increase revenue streams while reducing other costs, such as radio frequency identification (RFID) payments or tags, kiosk payment machines, or e-ticket applications.
- Management applications and systems: A centralized system handling different functions working simultaneously to monitor the flow of traffic and to define the limits of the complex integration. At its minimum, it has the controls for the likes of the traffic management center; parking systems; air, railway and ferry transport providers; construction and maintenance center; emergency services center; tourism information, and; public transportation systems, among others.
- Communications applications and systems: Information exchange is at the center of the ITS ecosystem, with all the centers and devices facilitating data in coordinated protocols to ensure efficient traffic flows and safety, increase revenue, and reduce environmental impact. This can be vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I), and infrastructure-to-infrastructure (I2I), and the tools, media and systems may include apps, social media, websites, alerts and announcements.
Here are some of ITS threats and risks based on three broad classifications covering the applications and systems (A&S) subsets. This also includes some best practices that enterprises and consumers can follow to protect ITS security.
[Read: The IoT attack surface: Threats and security solutions]
Physical attacks and risks
While physical attacks fall at the lowest ranks in Trend Micro’s threat assessments, physical damages to facilities entail heavy losses in finances and recovery. ITS facilities are exposed on roadsides and highways, making them physically accessible to anyone. Malicious actors can tamper with the physical components such as the exposed ports, gauges, and network antennas, causing failures in data upload and reporting.
Another plausible manner that all kinds of vehicles can be physically attacked is through the Controller Area Network (CAN bus), a standard that most vehicles have in order to control and communicate the applications between the devices even without a central computer. The CAN bus’ security gaps have been explored since 2016, but is still further studied to find other devices, components, and techniques by which it can be used to enter other systems such as smart homes and public networks to infiltrate enterprises.
In the trend of ride sharing services, there are also the physical components of other public vehicles such as e-bikes that may experience problems, such as users themselves unable to return them to proper dock stations, technical and environmental challenges, and battery and other vandalism-related issues. Moreover, other means to physically tamper with interconnected vehicles have also been considered, a theoretical scenario of an unknown or even a trusted individual installing additional components to compromise vehicles or to increase sales.
[Read: From homes to the office: Revisiting network security in the age of IoT]
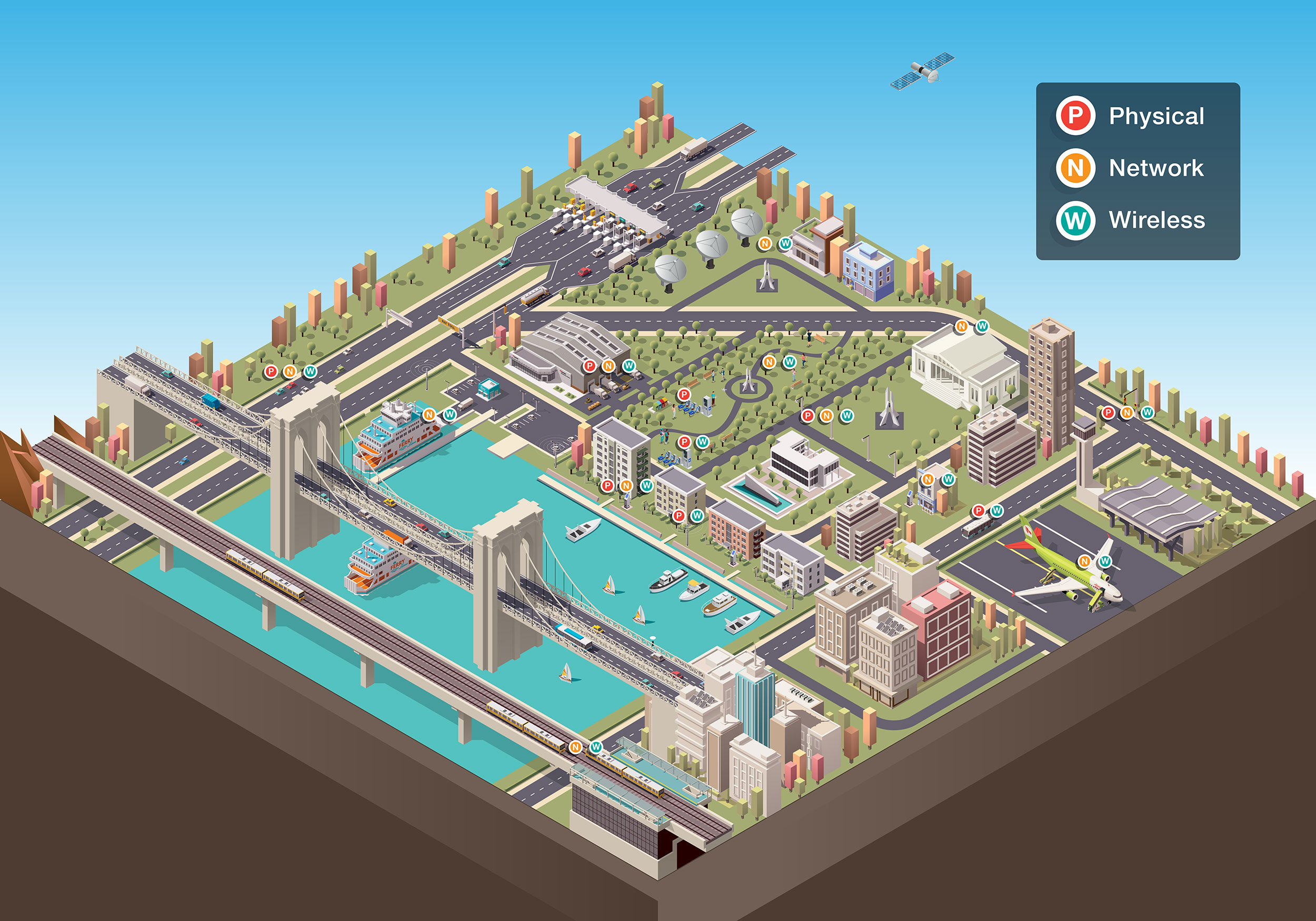
Figure 1. The ITS and its threats
Network attacks and risks
According to Trend Micro’s research, network attacks on ITS pose the highest threat to growing smart cities and transportation systems. Network attacks and threats target the regular operational functions of devices and equipment, disrupting services and possibly leading to data breaches and information theft. Malware is commonly used by cybercriminals to deliver other malicious payloads to paralyze public and private service industries such as government offices, logistics sectors, and other related infrastructures dependent on connectivity and communication, and can further enable cybercriminals connections to other unsecured facilities such as commercial buildings and residential areas to more sinister attacks: distributed denial of service (DDoS), man in the middle attacks (MiTM), or privilege escalation, among others.
Intrusions in the systems controlling and managing these transportation systems can also cause unnecessary and unauthorized use of valuable resources, become sources of sensitive information for high value targets, lost revenue, and stolen property. In instances of shared or rented vehicle services, there have also been cases wherein the devices can be used to track down previous clients’ data – a concern whether the privacy of information may be in violation of data privacy laws.
[Read: US cities exposed in Shodan]
Wireless attacks and risks
Wireless communications for V2V, V2I, and I2I will be the backbone of smart transportation and cities’ operations, especially in the exchange of real-time data and response deployment. But as the well-known jeep hack in 2015 showed, remotely compromising vehicles via embedded components or connected devices are not unknown and impossible. Vulnerabilities in the vehicles or peripherals, as well as unencrypted public wifi connections can be used to hijack vehicles running on the road. In a Georgia Tech research, it showed that only 20% of the interconnected cars stuck in traffic in the middle of Manhattan would be enough to paralyze the city – including emergency responders’ deployment and communications – or even less if the hack were applied to other cities. Further, server-side security would need to improve from the design phase to distribution; as vulnerable websites, weak passwords and app data searchability can quickly expose manufacturers’ customers’ data, control traffic, or software flaws used to unlock and start automated cars.
Considering the devices that manufacturers are integrating such as voice-enabled assistants, known vulnerabilities and techniques of these smart and connected gadgets can also be used to compromise these vehicles. Weaknesses and openings in apps can be used to infiltrate, scan and take over connected transport and vehicles, or used to get into critical infrastructures and industries.
[Read: EU report highlights cybersecurity risks in 5G networks]
Best practices
Cyberattack and intrusion prevention strategies with actionable measures should be included as an integral aspect of implementing ITS in every country, contributed to by everyone: policymakers, manufacturers, citizens and/or residents, designers, planners, and operators. Increasingly, breaches on public infrastructures and enterprises have been becoming commonplace, and mitigation measures are paramount as an overall proactive defense and protection for the entire system. While no defense stands invincible against determined attacks, here are some best practices to mitigate against physical, network, and wireless cyberattacks:
- Implement and strengthen physical security measures around ITS devices’ and/or facilities. Ensure that no unauthorized personnel are around the area to tamper with or vandalize specific components of the facilities. Consider limiting the number of authorized staff who can have physical access to the equipment or facility, and at internally known and sanctioned intervals or periods. Restrict the connected digital equipment brought within range of these equipment to devices only necessary to conduct security audits and maintenance checks.
- Apply network segmentation, monitoring, detection, and blocking systems. Before attacks can reach or execute their malicious actions, security systems such as firewalls and threat management gateways can quickly analyze and block attempts for malicious URLs, commands, emails and scripts. In the instance of an attack, security and IT teams can quickly identify, isolate, and contain breaches at a faster pace to stop intruders from going further into the network and endpoints, therefore preventing possible losses of data or infections. Monitoring also helps a multilayered protection system detect anomalies and unusual data exchange faster, especially in the inclusion of analytic technologies such as machine learning and artificial intelligence – from the equipment to the mobile devices connected to the network.
- Conduct regular security audits to make sure there are no gaps in the network, hardware, software and firmware. Map all the connected devices connected to the network at home or in the enterprise, and ensure manufacturers’ default credentials for all smart devices have been changed. Conduct vulnerability scans to find gaps in the system to immediately apply the appropriate solutions. Implement a patch management procedure that ensures downloads for all the systems connected without interrupting services and operations. Use available tools such as Shodan to scan for exposed devices, and for proper mechanisms to be installed such as multi-factor authentication (MFA) on all applicable platforms, or closing all ports to prevent unauthorized incoming or outgoing traffic.
[Read: Securing smart cities]
Conclusion
While ITS’ connectivity and automation offer new opportunities for innovation and convenience, it can also widen the attack surface and provide new opportunities for malicious actors to take advantage of, often at the users’, companies’, and the public’s expense. These emerging changes are putting a new dynamic to traditional vehicle manufacturers and transportation industries: vehicle and transport companies are no longer just producers of machines and equipment but are also entering the innovations, software, and user experience design businesses. Products sold from the showroom no longer mean users have complete ownership as software updates are deployed by companies and their third party contractors, and maintenance of these related products can only be acquired from the companies themselves.
But at its worst, the lack of cybersecurity testing and integration on the onset, innovation outpacing security measures, and the influx of cyber threats can reduce the peoples’ confidence in emerging technologies and dampen innovation, put down enterprises’ reputations, and endanger lives. Implementing vigilant security standards and measures for physical facilities and all its networked connections serves as an initial defense to deter malicious intents. Separating the network into sections and constantly monitoring the flow of data traffic enables containment in the shortest time possible, it also allows for earlier detections of unusual activities, whether it be outgoing or incoming. And security audits and awareness among relevant personnel and employees not only keep all parties updated on the latest security measures that can be implemented, everyone becomes familiar with the responsibilities of keeping the whole system and city safe and working efficiently.
[Read: The first steps in effective IoT device security]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One