-
Vulnerabilities1
-
Adware, fake apps and ad fraud2
-
Targeted Attack3
-
Malware4
-
2019 trends and beyond5
While the 2018 mobile landscape saw an increase in the number of campaigns and deployments, developments in 2019 resulted in cybersecurity successes and the decrease of some threat types. The number of simple and easily replicated Android malware samples dropped, and operating systems’ (OS) security improvements led to a significant reduction in mobile ransomware infections. Actors and routines that piggybacked on the popularity of cryptocurrency mining malware have almost disappeared, likely due to its exchange depreciation and distribution access restrictions on mobile platforms.
Despite these developments, the mobile landscape is far from becoming threat-free, as previously reported bugs and infections either resurfaced or were modified to adapt: the objectives, measures, and potential damage of these redeployed threats became more focused and latently impressionable. Targeted digital espionage continued to increase as they expanded their tools and methods. Mobile malware routines evolved to become long-term invasive residents in users’ devices to steal currency, information, and access. Fraudulent apps that were riddled with unrelated functions occupied marketplaces, official and otherwise. Ad fraud wreaked havoc on the mobile industry’s profits, reputations, data collection, and performance valuations. Banking trojans repeatedly impersonated or replaced legitimate services, explored more menacing routines, and included cross-platform capabilities.
The sophistication of techniques and new technologies employed in the routines and attacks we analyzed made the mobile threat landscape appear more difficult to tread. Even with cybercriminals using patched exploits and dated (but altered) malware families and campaigns, the obfuscation and evasion procedures have heightened the likelihood of infecting and spreading across devices. We reviewed the notable threats and events for mobile that took place in 2019 to see what users and organizations can do to defend their devices and systems.
OS, app vulnerabilities and root malware dug deep
A large number of mobile application vulnerabilities marked the year, especially for messaging and email platforms that allowed unauthorized access to users’ devices. A number of these security exploits enabled execution even without user interaction, allowing attackers to collect system or personal data, leak information, or conduct social engineering schemes such as phishing. A number of these security and functionality flaws can be abused on different platforms, often interchangeably on both Android and iOS. Cybercriminals also modified previously seen exploits to get through applied patches, and combined them with newly discovered mobile exploits to improve intrusion, obfuscation, and targeting.
Moreover, malware infection routines continue to use previously exploited vulnerabilities such as DirtyCOW (CVE-2016-5195) and IovyRoot (CVE-2015-1805) to infect users’ devices. We found new samples targeting ARM64 devices and Linux kernel using DirtyCOW and IovyRoot:
Detections for malware using DirtyCOW
Detections for malware using IovyRoot
We also added six detections for vulnerabilities in devices to detect and deter malicious apps from exploiting them. These include use-after-free (UAF), race condition, and type confusion flaws targeting various modules such as the kernel’s file system, notification system, transmission control/internet (TCP/IP) protocol stacks, Binder, and some third party libraries.
Notable iOS vulnerabilities and trends
We found authorization vulnerabilities (ZDI-19-583 and ZDI-19-232) in WeChat and Alipay that attackers can abuse through a technique we called URL hijacking. This method is enabled by improper validation of a URL scheme, allowing attackers to log into victims’ accounts to modify requests on the affected apps to leak information, steal tokens, or bill phish.
A stack overflow bug (CVE-2019-8648) in FaceTime was disclosed by Team Pangu Foundation. The flaw was found in the Apple Watch Series 1 and later, and is exploitable due to the false placement of stack canary in the LLVM plugin when handling the ARM compiler. Google Project Zero also disclosed six vulnerabilities within iMessage; the four flaws (CVE-2019-8641, CVE-2019-8647, CVE-2019-8660, and CVE-2019-8662) could be abused to execute malicious codes in the infected devices. No user interaction is needed for the said bugs; the attacker can simply send a specially crafted message and it will automatically execute once the user opens the app. The two other bugs (CVE-2019-8624 and CVE-2019-8646) also require no user interaction. Once abused, both vulnerabilities can allow an unauthorized actor to leak data from an infected device’s memory and read files from a remote device. Apple addressed all the issues in separate updates.
For iOS flaws, we have 128 detections for jailbreak tools, the majority of which had codes that were based on publicly posted exploits. Three local privilege escalation (LPE) vulnerabilities were used for jailbreaking, such as Voucher Swap (CVE-2019-6225), Sock Puppet (CVE-2019-8605) and Checkm8 (fixed, without an assigned CVE number).
Android apps’ and mechanisms’ vulnerabilities could lead to significant risks
We analyzed CVE-2019-3568 and CVE-2019-11932, which are high-risk vulnerabilities in WhatsApp. CVE-2019-3568 is a bug in the app’s voice over internet protocol (VoIP) stack that, when exploited, allows an attacker to send a specially crafted secure real-time transport protocol (SRTCP) packet to the target mobile phone number for remote code execution (RCE). By calling the user’s device via WhatsApp, the malicious actor can gain access to the device. This exploit affects Android and iOS, and works even if the user doesn’t take the call to initiate the attack. Further, the said calls will have no record in the call log of the device or app. Meanwhile, CVE-2019-11932 is a flaw in a GIF open-source parsing library used by WhatsApp. By using this double-free vulnerability in libpl_droidsonroids_gif.so, cybercriminals can generate malicious images, read arbitrary files in the device, or bounce a shell to execute a remote attack.
CVE-2019-1105 is a cross-site scripting (XSS) vulnerability found in a JavaScript file responsible for rendering the Outlook page. Exploiting this flaw could allow attackers to send emails embedded with malicious payloads to the users’ contacts and attack the device via emailRenderer-android.js. Google Project Zero discovered CVE-2019-11707, a type confusion vulnerability in Firefox when manipulating JavaScript elements in Array.pop. If abused, it can be used for RCE alongside another sandbox escape flaw to intrude into systems, as reportedly done in attacks on financial institutions and cryptocurrency exchanges between 2017 and 2019. Promon and Lookout also reported an Android exploit, called Strandhogg, that allows malware to hijack legitimate apps to leak or phish for information stored in devices by tricking users into granting permissions.
Binder, the inter-process communication (IPC) mechanism in Android devices, was also found to have a few vulnerabilities that can be used for intrusion. Water Drop (CVE-2019-2025) is a flaw that can root all pixel-series phones for sandbox and privilege escalation, and arbitrary reading and writing. CVE-2019-2215 is a use-after-free flaw in the kernel that allows privilege escalation from a malicious app to the Linux kernel.
Other hardware features were also vulnerable. We found CVE-2019-9353, a heap-base buffer overflow vulnerability within the parsing of Bluetooth packet lengths that can lead to RCE. It requires no user interaction, can allow an attacker to execute code unknown to the user in the guise of a system process, and may be used to leak or phish information from the device. Other discovered flaws are ZDI-19-780 (a double free vulnerability) in the Video4Linux (V4L2) driver Android kernel arising from the lack of validation in the existence of an object prior to performing operations on the object, and CVE-2019-14088 (a UAF vulnerability) from the lack of resource protection while the CRM is accessing the link pointer from a device’s private data. Once exploited, attackers can escalate their privileges in the context of the kernel. Android has yet to release an update regarding this vulnerability.
First active attack using CVE-2019-2215 exploit linked to the SideWinder APT group
We found a campaign abusing an Android Binder vulnerability soon after it was disclosed in November. The campaign was abusing CVE-2019-2215 as it was exploited in the routines we attributed to the SideWinder APT Group. The group is also known to target high-value military targets’ desktops, but this attack shows that it seems to have started exploring mobile devices. Malicious apps were disguised as photography and file manager tools available for download in the Play Store. Once installed, it uses the exploit to deploy a spyware and steal user and device information. This is the first active attack seen to exploit CVE-2019-2215 in the wild, as well as the first recorded SideWinder activity targeting Android users.
One-click mobile exploits abused to target specific groups
University of Toronto’s Citizen Lab reported that senior members of Tibetan communities and groups received specially crafted WhatsApp messages with malicious links, purportedly from NGO representatives, journalists, and other related individuals. Analysis revealed that the links led to codes that exploit browser vulnerabilities (eight for Android, one for iOS) and install spyware, all designed to conduct various attacks to steal information from the infected devices.
While none of the analyzed samples used 0-day exploits and some turned out to be modified versions of previously reported exploit codes, other researchers also reported on similar overlapping campaigns that formed part of a digital espionage siege. The campaigns also appear to target a specific indigenous community. This campaign presents the first documented case of attackers abusing this technique, and an example of the use of escalation of espionage routines to target a specific group. The exploits used for this campaign are CVE-2016-1646, CVE-2016-5198, CVE-2017-5030, CVE-2017-5070, CVE-2018-6065, CVE-2018-17463, CVE-2018-17480, CVE-2019-5825, and a JavaScriptCore (JSC) vulnerability yet to be assigned a CVE.
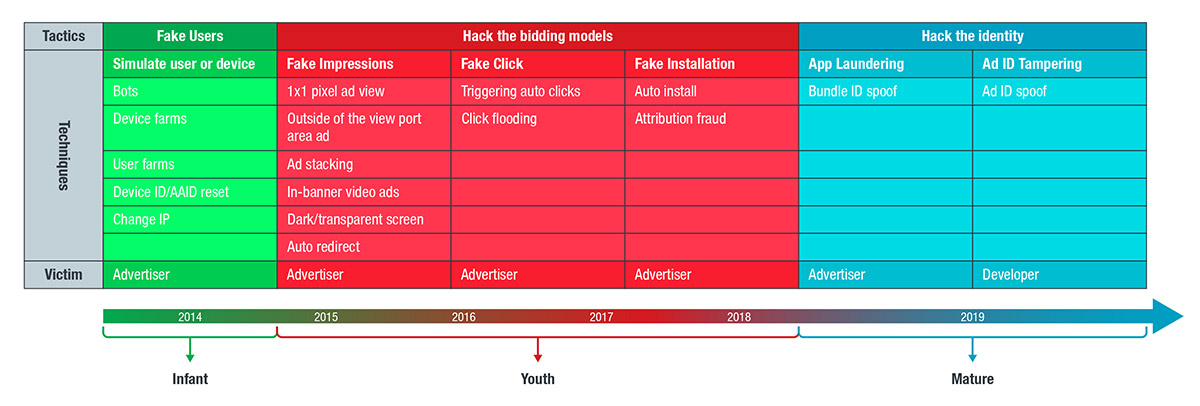
Malicious actors showed knowledge of the mobile app and advertising industry with refinement of techniques
Mobile advertising spending worldwide grew to $190 billion in the past year. As companies increased their mobile advertising budgets and spending, cybercriminals used a number of ways to piggyback on the growing ad revenue percentage. Reports showed that 23% of in-app programmatic ads were fake, causing advertisers to lose revenue, reputation, and campaign performance.
Industry players and technology developers have been trying to combat ad fraudsters, but malicious actors simply rode the wave of implemented countermeasures to evade security policies. They have been seen using more sophisticated ad fraud schemes that involve the use of bot farms, fake users, and distracting ad pop-ups to steal impressions and clicks.
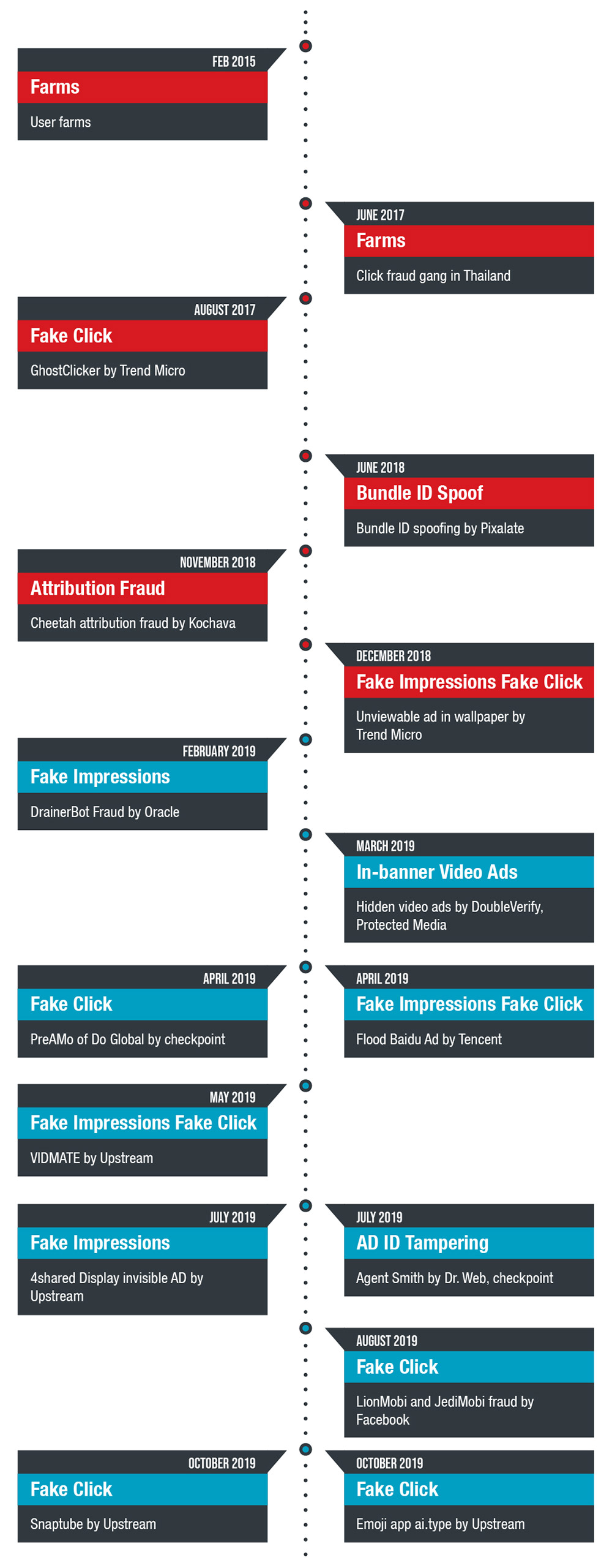
The timeline below shows how threat actors’ techniques evolved from simple methods to sophisticated routines.
Evolving ad fraud techniques
With sophisticated ad ID tampering, Agent Smith came to life
Our team has been monitoring routines utilizing ad ID tampering since January 2019 as part of several samples’ operations when we noticed a sudden uptick in the bundled malicious behavior. Specifically, the abuse of Janus (CVE-2017-13156) and hidden ads’ behavior, the use of the EvilParcel (CVE-2017-13315) exploit to replace the apps, and ad ID tampering to replace the apps’ unit IDs and profit diversion. By targeting the ad unit ID, attackers target the profits that go to the legitimate app developers, in contrast to common ad fraud tactics targeting advertisers such as fake ads or ad traffic redirection. The sporadic appearance of the routines initially appeared as unrelated until more sandboxes and reports of infection attempts increased, likely going unnoticed until the developers lost profits. Likewise, users and inexperienced system administrators missed the routine altogether without the security measures and updates in place. This technology maturity via ad ID tampering can serve as a precedent to more arbitrary intrusions.
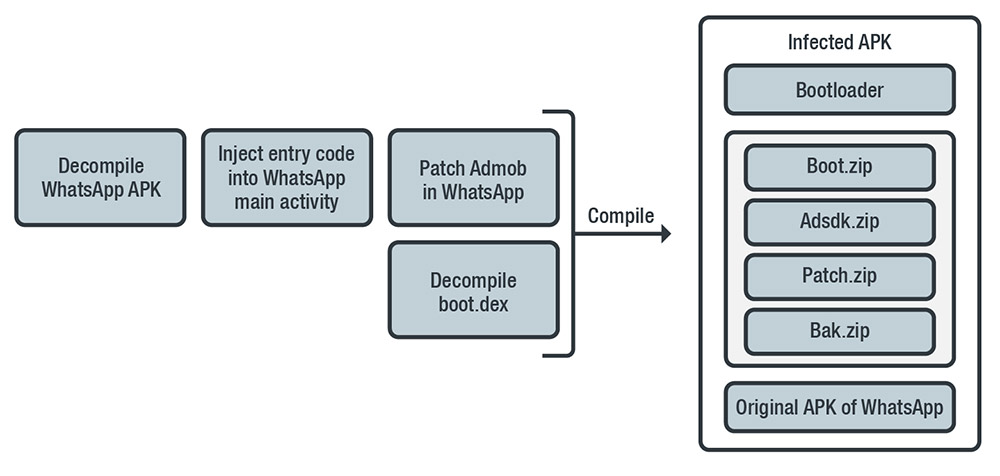
How Agent Smith infected popular apps such as WhatsApp
In July, researchers found new variants of Agent Smith as users downloaded infected Android apps from third-party marketplace 9Apps more than 25 million times, stealing ad revenue from more than 2.8 billion ad events from 2016 to 2018. Instead of creating new or fake apps, the fraudsters behind Agent Smith targeted popular apps installed on the infected devices, replacing them with malicious versions or abused ad ID tampering to force intrusive ads on users and redirect profits. It exploits Android vulnerabilities Janus, Bundle, and Man-in-the-Disk across three stages of an infection chain. Discovered and dubbed by Check Point as the first mobile malware to have weaponized all these flaws, the cybercriminals profited by taking the ad click profits from legitimate developers and advertisers.
Rogue apps and adware disrupted users’ app experience and evaded deletion
Rogue apps and adware plagued users with large, intrusive ads. These apps were disguised as games and stylized camera apps, and use hidden icons that make them difficult to remove. Evasion routines and anti-uninstall functions can go a step further by disguising the apps to appear as if they were part of the app settings page.
Adware apps will continue to become a nuisance to mobile companies as the number of adware continues to surge despite Google’s efforts to remove these malicious apps in waves. In January 2019, we found over nine million devices infected with adware, while more than 100 adware apps were deleted from the Play Store and other third-party app marketplaces in July. During the second half of the year 49 disguised adware apps were found with enhanced evasion features, and an additional 85 fake photography and game adware apps were discovered and removed. In total, Trend Micro’s MARS technology detected 219,780 hidden ad apps from all marketplaces. From the Play Store alone, 6,605 different versions of 536 different apps recorded 56,538,195 combined installs before they were removed.
App and ad fraud losses were cut short in Android
Trend Micro’s MARS technology detected 78,452 apps with fraudulent behaviors, 4,244 of which comprised of different versions of 699 unique applications in Google Play. Combined installs of these supposedly educational (e.g., books, news, weather forecast), optimization, entertainment and game apps reached 856,723,763, while other fraudulent ad apps were seen in third-party app marketplaces. We found that patterns of fraudulent techniques emerged from these apps:
- Low-value and fake apps were available on official platforms, alongside legitimate and high-value apps with real user traffic
- Ad fraudsters generate fake traffic for these fake apps, and combine them with existing user traffic and legitimate application information such as ad and bundle IDs to disguise the generated data
- Targeted advertisers can be duped into thinking the traffic came from mid- to high-value apps
Significant ad techniques and events
Most of the notable ad fraud events were tracked back to popular apps such as VIDMATE, 4shared, Snaptube, and ai.type. Other notable apps included were developed by CooTek, JediMobi, LionMobi, and DO Gobal. The delisted apps had notable features that should have raised red flags:
- The apps were acquired and subsequently transferred to shell companies
- Compared to other applications within the same category, these apps requested more permissions from the user
- A number of the requested permissions were “dangerous permissions,” or functions that were unrelated to their listed purposes
- The apps had concealed information
iOS App Store scrubbed malicious and fraudulent apps
Distribution of iOS malware that Trend Micro MARS detected in 2019
Fake applications were also found on the App Store, with descriptions that were inconsistent with the apps’ functions. These fake apps shared similar suspicious behaviors with some of the rogue apps in the Play Store — specifically, these applications could transform from benign apps into live gambling apps. This may be the developers’ workaround for Apple’s updated policy concerning real-money gambling apps. After the deadline and upon analysis, these gambling apps were found to be in violation of local government regulations as well as app store policies, and Apple subsequently removed them. Wandera also found 17 apps infected with clicker trojan malware in the App Store; these apps inflated website and app traffic, and collected fraudulent ad revenue.
Targeted attack campaigns and deployments on mobile devices increased
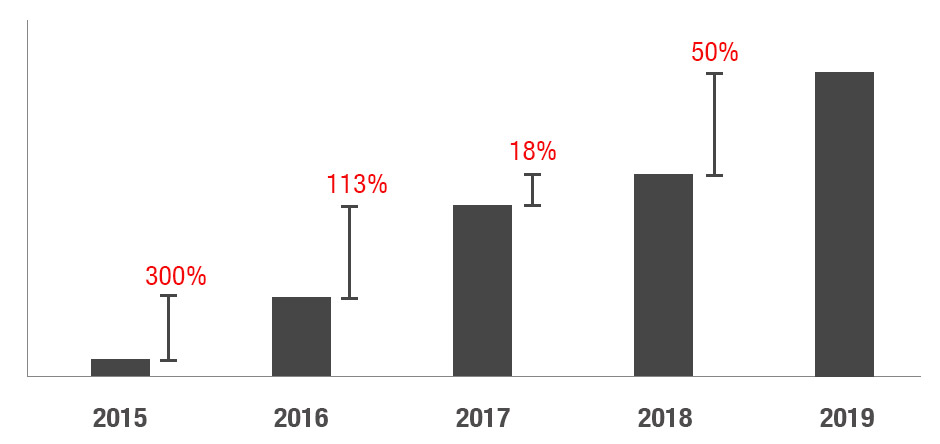
Total percentage comparison of targeted attacks on mobile
From 2015 to 2019, more cyberespionage actors were observed shifting to or adding mobile platforms to their operations. In four years, mobile cyberespionage campaigns have increased by 1400%, spread across multiple platforms, operating systems, and countries. These campaigns continue to evolve, with more organized groups traditionally associated with desktop attacks gradually shifting their attention and techniques to the mobile arena, such as the employment of social engineering, watering hole technique, and the use of social media as a threat vector.
Cybercriminals tried hiding malware in repackaged legitimate apps and sites for delivery
In 2019, we observed the cyberespionage campaign Bouncing Golf targeting the Middle Eastern region’s military sector. Our analysis found malicious codes embedded in seemingly legitimate applications that were hosted on websites instead of app stores and promoted extensively on social media. Apart from its ability to steal confidential data stored in infected devices, it is also capable of executing commands such as file exfiltration and downloads, taking screenshots, recording audio and video, installing other application packages (APK), and updating the malware version installed in the device.
CallerSpy was discovered by Trend Micro’s Mobile App Reputation Service (MARS), and we analyzed it in its early development phases. The campaign used a new spyware family disguised as chat apps that were hosted on a phishing website and masqueraded as a Google page to deceive users into downloading the app. The malware schedules data retrieval tasks to collect call logs, messages, contacts, and files from the infected device, and receives commands from the C&C to take screenshots.
MobSTSPY was a spyware disguised as several different applications in the Play Store, with some downloaded more than 100,000 times by users from 196 countries. It uses Firebase Cloud Messaging to send gathered information from users to its server, stealing data such as user location, SMS conversations, call logs, and clipboard items. It was also capable of gathering additional credentials through phishing by displaying bogus pop-up overlays that requested the user’s Facebook and Google account details.
MuddyWater is a threat actor group known to target organizations’ computers in the Middle East and Asia. Apart from the new tools and payloads that the group used during the first half of the year, we also found that it shared common characteristics, such as shared infrastructure, with four other Android malware variants posing as legitimate applications.
Security researchers in Korea have been observing cyberespionage group Konni since 2014. The group has been tracked to be working with other organized groups, and a series of campaigns have been attributed to it. Their criminal activities on Android users were published for the first time by EST Security in 2019. Researchers observed that its traditionally desktop-based attacks shifted to the mobile platform, impersonating popular apps in the region to take over users’ devices and steal information. According to the report, the group steals system information, accounts, list of installed apps, contacts, SMS, clipboard data and files stored in the SD card, SMS control for access to one-time passwords (OTP), contacts’ takeover, voice recording and keylogging, and C&C commands’ execution.
Combined with “old” techniques, mobile malware evolved to become more diverse, enterprising, and bold
Despite security policy changes implemented on official digital distribution services, malicious actors still found their way into official marketplace platforms and adjusted their techniques to make their fake apps inviting to users. Cybercriminals used a range of different techniques — such as overlay attacks, SMS controlling and spam, remote access tools (RATs), and impersonation of legitimate apps — to make banking malware more effective. MARS sourced more than 220,000 mobile banking malware samples in 2019 alone, with East Asia experiencing the most attack attempts as these were combined with social engineering techniques.
We also observed some banking trojans adopting techniques from other types of malware. The mobile banking trojan Riltok was found using a method that involved hiding malicious code in native code. It was also capable of hiding notifications from legitimate bank apps. Unofficial app stores also played a role in hosting more evasive and persistent trojans, allowing them to infect more devices.
Malicious apps infiltrated digital distribution services, and users who downloaded these apps unknowingly provided entry
Total number of malicious Android applications sourced and analyzed by Trend Micro MARS from 2016 to 2019
Monokle is a sophisticated set of custom Android surveillanceware tools that compromises a user’s privacy by collecting personal information, which it then exfiltrates to a C&C infrastructure. The malware is only embedded in a limited number of applications, and comes with legitimate functions to avoid suspicion. This implies that its targets are “attacker-specified” and of high value. Exodus is an Android spyware developed by a video surveillance company equipped with a repackaged version of the DirtyCOW exploit. The spyware is disguised as local telecommunications’ service applications, possibly to collect further information, perform subsequent intrusions and data tampering. Code modifications from 2016 to 2019 showed extensive data retrieval and diversion capabilities.
BRATA is an Android RAT malware family primarily hosted on the Play Store and targeting victims in Brazil. It propagates by pushing notifications on compromised websites, chat apps such as WhatsApp, malicious messages via SMS, and sponsored links in Google searches. The malware’s features include keylogging, real-time streaming, and the ability to use Android’s accessibility service feature to interact with other applications installed on the user’s infected device.
Banking malware families not only followed the money, but looked to exfiltrate data for more profit
Comparison of unique Android banking trojans Trend Micro sourced from 2016 to 2019
Almost a third of the total mobile malware detections were identified as FakeSpy and XLoader samples, and continue to be popular among cybercriminals in the East Asian underground. Our analysis found these malware variants disguised as logistics companies’ mobile services or web browser apps, and propagated across other Android and iOS devices through different methods such as SmiShing and DNS hijacking.
We observed Anubis banking malware targeting more than 300 financial institutions worldwide using motion-based evasion techniques as it made its way into the Google Play Store in early 2019. Analysis found that the malware family’s operators increased activities throughout the year as MARS discovered domains hosting more than 17,000 malware samples in July. The malware is disguised as a benign app that lures victims into sending their banking credentials, security codes, and credit card details through overlays in the guise of software updates, app markets, flash player apps, and utility tool apps. The combination of advanced features used in other Android app malware made it one of the most notorious Android banking trojans of 2019.
Among the new and notable banking malware families, Cerberus was notable as it was promoted and sold on Twitter. Analysis of the samples showed that its code showed no similarities with other previously deployed malware, indicating that it was created from scratch. It remains active, and is being sold in the wild as malware-as-a-service (MaaS), deployed using overlay attacks, intercepts and controls the device’s SMS traffic, and harvests contacts.
Gnip is another new banking malware family that uses some code snippets from Anubis. Samples showed its overlay attacks, abuse of the accessibility service feature, SMS intercept, and contact harvesting primarily focused on Spanish banks, as well as social and utility applications such as the Play Store, Facebook, WhatsApp, Chrome, Skype, Instagram, and Twitter. The banking malware has the ability to inject requests for the country code of a targeted organization, which indicates that the cybercriminals behind it might be planning to expand its targets to applications that are popular in other countries and regions.
Stalkerware subscriptions – and drawbacks – increased
Trend Micro’s MARS technology detected the increased deployment of stalkerware in the past year. While surveillance tools have been growing in number through the years and have become more refined, stalkerware infections peaked in March and declined in April 2019. These tools present cybersecurity concerns for its widespread use, the organizations and individuals it targets, how the data collected is being utilized and stored, and the possible repercussions if the developers are hacked or breached.
Stalkerware apps are not available on official marketplaces and can only be downloaded from dedicated websites, as discussed by Kaspersky; a number of their featured “services” go against Google’s and iOS’ security policies because these apps expose devices to aggressive behaviors and malware. It not only exposes the device of the person under surveillance to risks, but opens the stalkerware subscriber to breaches as well.
Trends and predictions on the mobile threat landscape
Total number of mobile threats blocked by Trend Micro from 2016 to 2019
Country distribution of mobile threats detected by Trend Micro MARS in 2019
We observed cybercriminals riding on “threat fads” to study their techniques’ effectivity, profitability, potential for subsequent use and profit, and impact on users. From this perspective and with the mobile platform’s ubiquity, these devices are fast becoming an effective propagation and entry point for threat actors. Possible human error and organizations’ seemingly steep learning curve on new technology implementations present attackers with opportunities to infiltrate and steal from enterprises with repeated attacks.
Further, the number of attacks enabled via remote and arbitrary executions increased in the past year, regardless of the attack or threat vector used. Malicious actors may be ramping up their techniques for mobile, as evidenced by the transitions done by groups that formerly targeted desktop platforms. We could expect more pronounced threats and effects — the commercial and industrial implementations of 5G may thin out security administrators’ and teams’ ability to monitor and analyze security incidents.
Our telemetry data indicate that mobile cyberespionage campaigns will likely keep increasing in the foreseeable future. They will also be further refined as far as techniques, deployment, targeting, reconnaissance, and information retrieval are concerned. Political and military conflicts between countries will likely compound these attacks; the more confidential and influential the source of the stolen data, the wider the impact to the user, the entities under scrutiny, and the people involved with the storage and security of the information. This will be appended by the multi- and/or cross-platform capabilities of the tools, expanding platforms, and actors finding that it’s possible to meet their sponsors’ objectives and make a profit with the proliferation of mobile devices vis-à-vis developments in the cloud.
And as more campaigns from known persistent threat groups surface, more and newer unknown mobile APT organizations will also be discovered and overlap with previously seen attacks. Security researchers will be busy disclosing these activities due to lower (and easier) barriers of entry: Open source tools are widely available with almost all the hard coding work done, published, or sold; commercial spyware is readily accessible, and; cross-platform capabilities of these routines have made learning-by-imitation within reach.
Meanwhile, as the mobile advertising industry increases its spending for clients and targeting for users, so will the mobile ad fraud market. Fraudulent actors will keep fine-tuning their techniques to either expand the scale of targeted devices for infection or to evade detection. On the other hand, new regulations may be created to protect the interests of the advertising industry. Existing silos have to be reevaluated as cooperation from differing roles in the advertising ecosystem and the cybersecurity industry may benefit all the parties involved with new technologies such as artificial intelligence (AI) and blockchain.
Users and companies directly involved in the mobile ad industry will experience surges in fraud and adware. While changes in the policies and procedures of tracking and app uploads have been updated in an effort to boost security on official app platforms, cybercriminals can be expected to find workarounds. Tracking their activities and techniques, a growing number of malicious actors expanding to mobile now have organized teams: clear role delineations in deploying schemes on users and devices according to their knowledge of the ecosystem, app development, and operating systems. They will continue to search for and target apps with large user bases and use sophisticated techniques to fake the identities of these apps, such as bundle IDs and app-specific ad IDs. Routines such as Agent Smith serve as a precursor to more intrusive behaviors, such as arbitrary app installation with malicious payloads. If the supply chain is mature enough, techniques such as ad ID tampering can act as an agent to help the underground players install spyware, or change the object of infection to financial apps.
Based on the new mobile malware families we observed, the mobile underground market according to the different infrastructures used. One side will be in favor of how mobile attacks used to be deployed, while the other will be for those in favor of automated package deployment technology. Techniques using automated package deployments generate a completely new sample whenever a victim accesses an attack vector, making it one of the reasons for the increase in the total number of samples in 2019. As the cybersecurity industry tries to use new technologies to defend against these entities, malicious groups and actors will simultaneously abuse these developments to use to their advantage.
While media server vulnerabilities still exist, they generally decreased in 2019. Cybersecurity companies and researchers focused on flaws in features and mechanisms of devices such as Bluetooth, v8, NFC, Binder, and Qualcomm drivers. Android users can expect more vulnerability disclosures and attacks for 2020: While attacks and intrusions hardly come in through exploits for all systems using just one chain due to fragmentation, the two vulnerabilities in Binder makes all Android devices prone to infection as all of them use it as part of the system. As more researchers look into these mechanisms, we expect more discoveries on its flaws. More attack campaigns can also be expected in the coming year using these posted exploit chains.
The App Store team might become inundated with uploaded apps that they have to check more closely in relation to the changes in the real-money gambling policies vis-à-vis upcoming events such as the Olympic Games. Malicious actors will likely find ways to circumvent these changes to profit from these events, including possible flaws in built-in apps such as FaceTime and iMessage. More exploits in device hardware, software, and firmware will be analyzed as the dates of the games approach, notably for RCE. Cybercriminals will likely continue to refine their evasion and intrusion techniques via exploits and combine them with old-school social engineering techniques such as smishing and phishing to target unwitting users.
In a proactive defense stance, developers and other parties in the mobile ecosystem have begun implementing enhancements and security measures to deter cybercriminals. Cybersecurity companies such as Trend Micro have begun using the MITRE ATT&CK Framework to accompany our analyses, making it easier for practitioners to identify and describe attacks and campaigns for attribution, publishing, and impact breakdown.
Android’s earlier improvements included features that limit the abuse of application programming interfaces (APIs) to hijack processes and activities. The platform also added required runtime permissions and enhanced PIN reset processes, among others. Newer versions of their OS and device hardware updates have also been introduced, and every device version replacement is accompanied with the latest updates to detect and protect it against known samples of previously seen malware. These security enhancements can make it more difficult to deliver malicious payloads, and conversely easier for security systems and analysts to identify and detect unusual behavior.
As more desktop features and services shift to mobile accessibility and the cloud, misconfigurations and leaks may become the supplementary treasure trove of stolen data and information with mobile devices as side entrances. Platform and app developers, as well as product designers and manufacturers, should intentionally include security by design from the onset. Executing and marketing beyond functionality, data privacy, and security should be embraced as a compendium in device and app development, operations, maintenance, and life cycle.
Users can go back to the basic telltale signs of cybercriminals’ old techniques to defend against threats, and practice security hygiene. Organizations should review their mobile use procedures and become more flexible in adapting and balancing security policies for their Bring-Your-Own-Device (BYOD) enactments.
End users and enterprises can also benefit from multilayered mobile security solutions such as Trend Micro Mobile Security for Android (available on Google Play), and Trend Micro Mobile Security for Apple devices. Trend Micro Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning. It also protects devices from attacks that exploit vulnerabilities, prevents unauthorized access to apps, and detects and blocks malware and fraudulent websites.
Trend Micro’s Mobile App Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies. It can protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerabilities.
Data on the mobile threats detected and blocked by Trend Micro in 2019 is in this appendix.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One