New Pokemon Go Ransomware Creates Windows Backdoor Account
 With all the frenzy around the Pokemon GO mobile game, it was only just a matter of time before attackers leveraged its popularity to spread ransomware. A new ransomware was recently discovered impersonating a Pokemon GO application for Windows. Detected by Trend Micro as Ransom_POGOTEAR.A, it appears to be like any other ransomware. However, a closer look revealed that its creators based it on Hidden Tear, an open-sourced piece of ransomware released last August 2015, with the intention of educating people.
With all the frenzy around the Pokemon GO mobile game, it was only just a matter of time before attackers leveraged its popularity to spread ransomware. A new ransomware was recently discovered impersonating a Pokemon GO application for Windows. Detected by Trend Micro as Ransom_POGOTEAR.A, it appears to be like any other ransomware. However, a closer look revealed that its creators based it on Hidden Tear, an open-sourced piece of ransomware released last August 2015, with the intention of educating people.
The Pokemon GO ransomware developer designed it to create a “Hack3r” backdoor user account in Windows and is added to the Administrator group. The registry is tweaked to hide the Hack3r account from the Windows login screen. Another feature creates a network share on the victim’s computer, allowing the ransomware to spread by copying the executable to all drives. Once the executable is copied to removable drives, it creates an autorun file so the ransomware runs each time someone accesses the removable drive. The executable is also copied to the root of other fixed drives. This way, the Pokemon GO ransomware will run when the victim logs into Windows.
There are numerous indicators that the ransomware is still under development. One of them is that it has a static AES encryption key of “123vivalalgerie”. Additionally, the command & control server (C&C) uses a private IP address which means it cannot connect over the Internet.
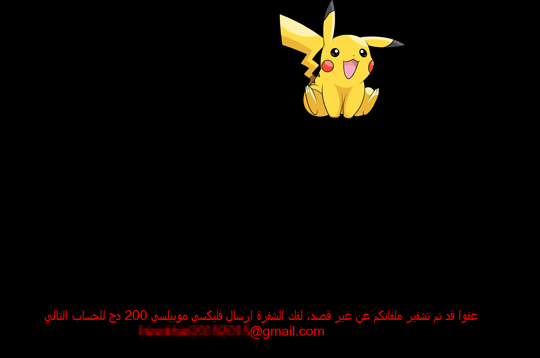
Based on the language used by the ransom note, the Pokemon GO ransomware appears to target Arabic-speaking users, with an accompanying ransom screen that features a Pikachu image. In addition, the screensaver executable is also embedded with an image of “Sans Titre”, which is French for “Untitled”, suggesting a clue to the developer's origin.
The Hidden Tear ransomware isn’t new. In January 2015, Trend Micro discovered a hacked website in Paraguay that distributed ransomware detected as RANSOM_CRYPTEAR.B. According to the analysis, the website was compromised by a Brazilian hacker, and that the ransomware was created using a modified Hidden Tear code. Prior to this discovery, when the source code of Hidden Tear was made public for educational purposes, the creator was very specific about not using Hidden Tear as ransomware. Unfortunately, as expected, the following discovery of Ransom_CRYPTEAR.B and this current Pokemon-themed ransomware has shown that even with the best intentions, improper disclosure of sensitive information can lead to troublesome scenarios such as the mentioned discoveries.
To avoid ransomware, users are encouraged to regularly back up files and to have an updated security solution. Trend Micro solutions can protect users from the recent Pokemon Go ransomware. As the game is introduced in new regions, the Pokemon GO craze is expected to continue to gain momentum and cybercriminals will find ways to capitalize on it. In fact, in the month of July alone, malicious Pokemon Go apps were found tricking users into downloading them. This should remind users to remain vigilant of threats that may ride along the popularity of such games.
Visit the Threat Encyclopedia for step-by-step instructions on how to remove Ransom_POGOTEAR.A.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One