Cryptojacking Gaining Traction as Starbucks and Streaming Users Targeted
International coffee chain Starbucks confirmed that customers at their Buenos Aires stores were unintentionally used for cryptocurrency-mining. Apparently, the WiFi network on the affected sites was modified to embed a CoinHive miner on pages loaded via the in-store WiFi. Thanks to this modification, the devices of users who connected to the network were used to mine the Monero cryptocurrency without their knowledge.
After being called out on Twitter by Noah Dinkin, an executive from a New York-based tech company, Starbucks responded that it swiftly handled the situation.
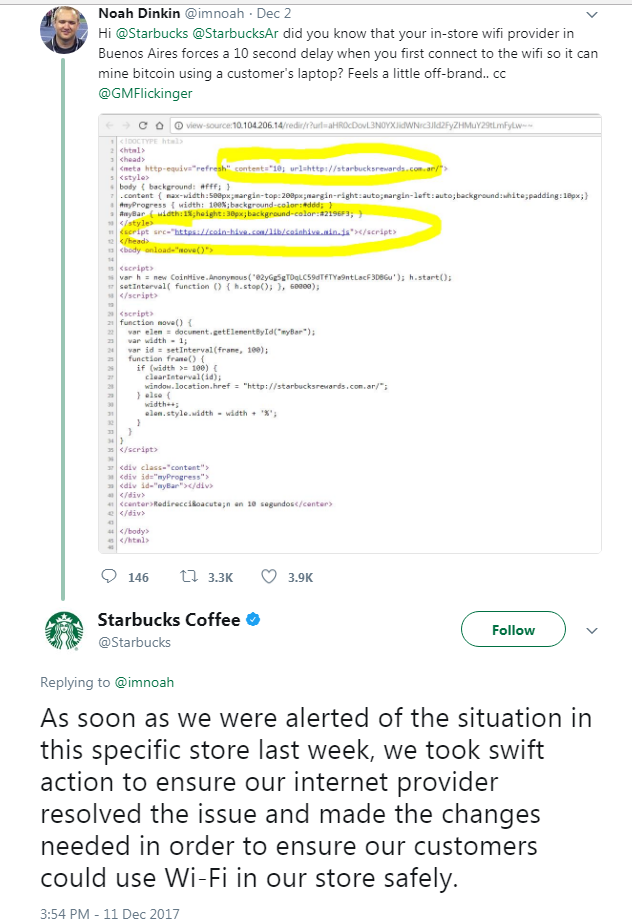
Figure 1. Dinkin highlighting the problem on Twitter
Because the value of cryptocurrency continues to rise, and the resources needed to mine are also skyrocketing, cybercriminals and even a few legitimate businesses are looking for different ways to profit from mining. Some popular sites are asking for a trade-off—instead of being bombarded with ads, a user can donate processing power to be used for mining.
Upstanding sites explicitly tell their users about their cryptocurrency mining intentions, but others do not. According to a report published by AdGuard researchers, nearly one billion visitors to streaming sites have been used for secret cryptocurrency mining activities, a practice they dubbed as “cryptojacking”. They also listed several popular streaming sites and online video-converter sites that mine through their users. The script for the miners is embedded where users might spend a lot of time, like lengthy videos. The researchers note that not all the owners might be aware of the mining script embedded in their sites.
There are specific antivirus or ad-blocking extensions capable of blocking these scripts, but unless a user has these enabled, then they might be unaware that their processing power is being used to mine cryptocurrency for whoever placed the scripts into sites they visit. The researchers note that there is already a project in the works called CoinHive Stratum Proxy, which shows how cryptojackers can circumvent ad blockers. Although the effects of cryptojacking may not be noticeable, users should be wary of this and other threats that use their resources.
Trend Micro Solutions
Comprehensive security solutions can block URLS and scripts that are known to be malicious or exhibit malicious behavior. Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security protect end users and businesses by detecting these threats and all related URLs. Trend Micro™ Smart Protection Suites deliver several capabilities like high fidelity machine learning, web reputation services, behavior monitoring and application control that minimize the impact of this threat.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One