UK MPs Criticized for Password Policies
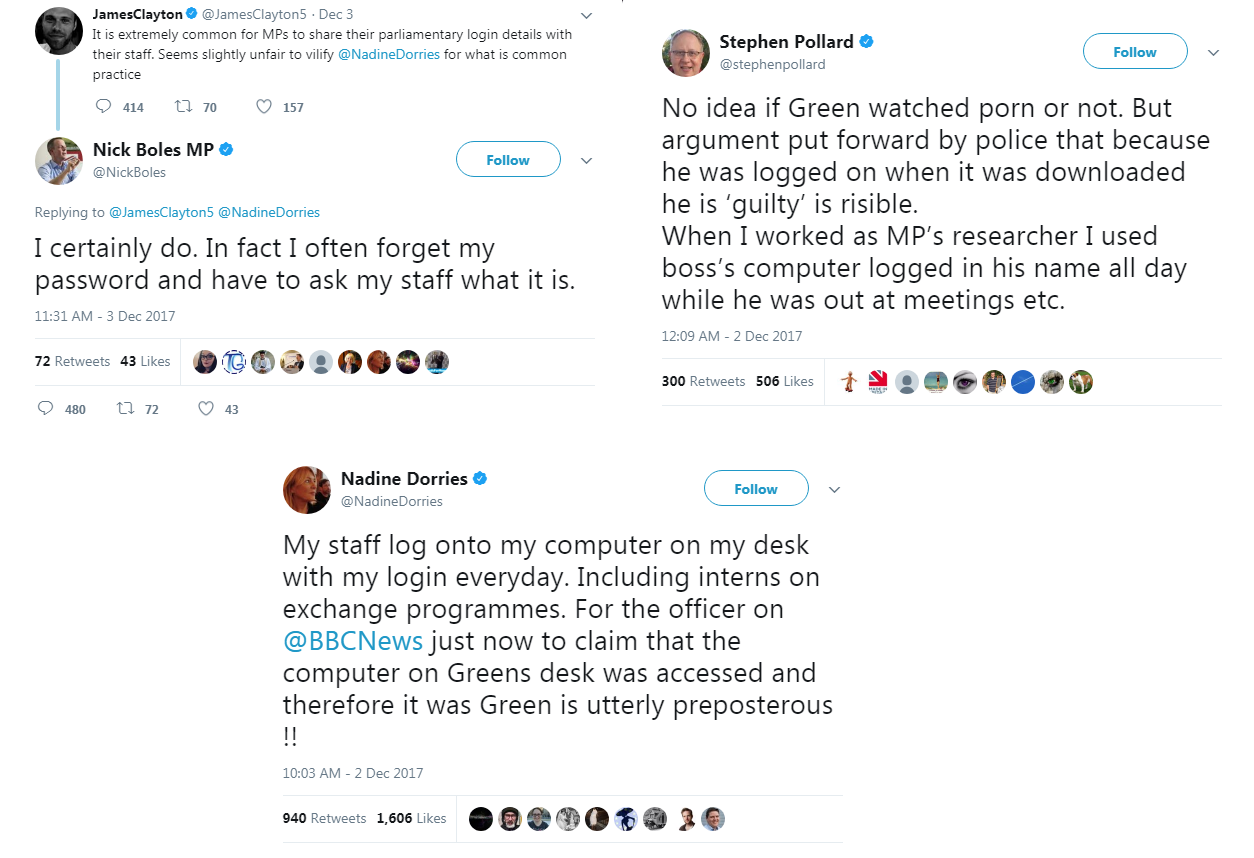
 Security measures employed by Members of Parliament (MPs) from the United Kingdom have come under scrutiny after a series of tweets from a few MPs. The issue started after Nadine Dorries, an MP for Mid Bedfordshire, posted a comment regarding an unrelated issue involving First Secretary of State Damien Green.
Security measures employed by Members of Parliament (MPs) from the United Kingdom have come under scrutiny after a series of tweets from a few MPs. The issue started after Nadine Dorries, an MP for Mid Bedfordshire, posted a comment regarding an unrelated issue involving First Secretary of State Damien Green.In her initial tweet, Dorries claimed her staff had access to her computer, including interns on exchange programmes, to help her manage emails. After an initial reaction from Twitter users and news commenters, other MPs replied to her statement with their own security habits. One MP claims he regularly forgets his password and has to ask his staff for it, while another said he leaves his machine unlocked and shares his password with his office manager.
Aside from MPs, former employees also joined the discussion. A past researcher claims that when he worked for an MP, he would log on and use his boss’ computer regularly. A producer for BBC’s NewsNight added that MPs sharing login details with staff is common practice.
Security experts have already criticized the MPs, while the Information Commissioner's Office reminded them that they are obligated to secure their data. Sharing passwords is understood to be unsafe; the more people that are allowed access to a device, the more chances that the access will be abused either on purpose or accidentally. And enabling two-factor authentication—already widely available to even casual email users thanks to mega-breaches in 2016—should be in practice by any individual handling any kind of sensitive data.
Ultimately, the MPs seem to have a laid-back attitude regarding password security. This comes at a time when cybersecurity is a matter of concern across the globe. The UK Parliament recently suffered a cyberattack in June, with some emails compromised because of weak passwords. And the General Data Protection Regulation (GDPR), which gives organizations strict guidelines for cybersecurity, is set to take effect in May 2018. Data protection, which starts with a secure and private password, should be top-of-mind for all organizations.
Password security
Securing passwords is one of the most basic steps when protecting a system. Shared passwords are a weak point in an organizations cybersecurity—it allows attackers an easy entry point into the system. From then, a compromised email can lead to a number of different attacks, or these credentials can even be used to gain deeper access into the network.
As cybersecurity incidents like data breaches become more commonplace, strengthening security practices for email and online accounts should be a priority for all users. Here are some basic tips on how to secure email accounts, and also allow others to access to your email securely:
- Email providers actually have features that allow users to delegate access without compromising security. For example, on Microsoft Outlook, a person can allow another person to access folders, calendars and even answer emails on his behalf.
- To secure any online account, the most basic step is to choose complex passwords with a mix of uppercase and lowercase letters, and numbers.
- Users should also enable two-factor authentication, a feature offered by many sites for an extra level of security. With this enabled, a user needs two types of verification to access an account, making it more difficult for unauthorized parties to log in.
- Make full use of the security options offered. Sometimes email providers or websites will update with new and more effective security measures. Stay updated and take advantage of the latest features.
- Use unique passwords for different accounts. Many people use the same password across multiple sites, and cybercriminals can leverage these re-used passwords to access a user’s account on other sites.
- Use multi-layered security solutions to help you lead a safe and private digital life. Trend Micro™ Maximum Security secures multiple devices, helps manage passwords, and guards against the most prevalent online threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One