Inside the Bulletproof Hosting Business: Cybercriminal Methods and OpSec
 Download The Hacker Infrastructure and Underground Hosting: Cybercrime Modi Operandi and OpSec
Download The Hacker Infrastructure and Underground Hosting: Cybercrime Modi Operandi and OpSec
Bulletproof hosting (BPH) services have long been crucial parts of the cybercriminal infrastructure. How do they protect malicious activities, and how do cybercriminals use them to stay in business?
Many cybercriminal operations have some level of organization, planning, and some form of foundation that reflects the technical acumen of the individual or group behind them. The use of underground infrastructure is inherent to the modus operandi of a cybercriminal. In our Underground Hosting series, we have differentiated how cybercrime goods are sold in marketplaces and what kinds of services are offered. In this final part of the series, we will explore the methods criminals employ to secure their assets and survive in the business.
Criminal sellers use different mechanisms to protect their businesses. The offerings of these "businesses" are often suited to the respective requests and demands of the criminals. Bulletproof hosting (BPH) services, also known as abuse-resistant services, and in some cases, offshore hosting, usually comprises compromised assets and infrastructures with a high level of resistance to abuse. Providers often offer customer support by sharing early notifications of abuse requests and even automatically moving servers to another IP space.
A bulletproof host employs various ways to sustain crimes operating under its wing and offer protection from law enforcement agencies. BPH services tend to strategically allocate resources globally, keeping in mind local regulations and geographical characteristics.
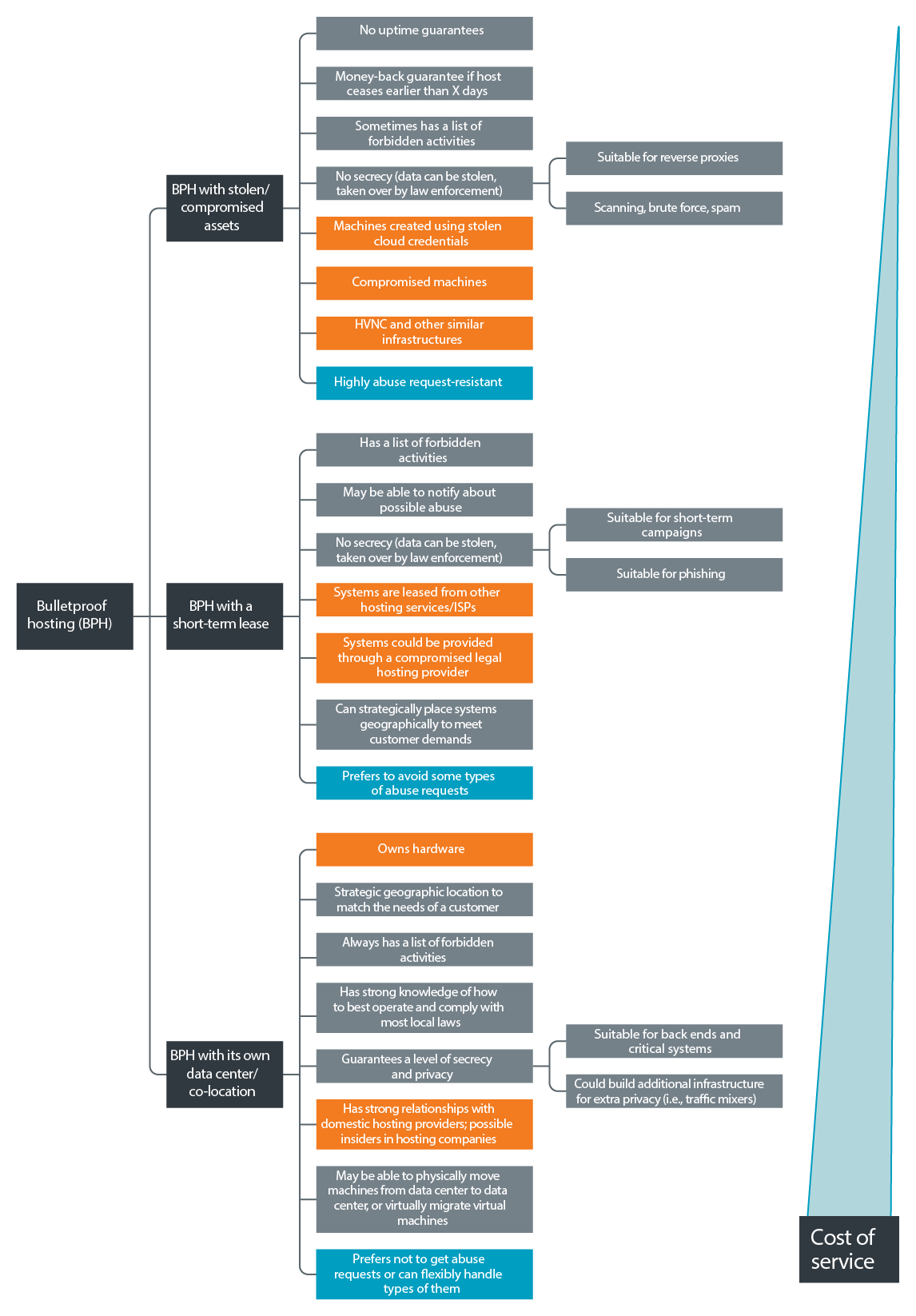
Breakdown of BPH hosting providers
Hosting on compromised assets is the cheapest option, with the caveat that the hosts do not survive for long. Hosting providers that have their data centers and infrastructure are more viable for systems that require long-term availability.
Geolocation of IP addresses used by an underground forum between January and April 2020
Note: Pins on this map point to a particular IP address of an underground site. Circles are clusters of IP addresses located in a particular country. The color of each circle varies depending on the density of IP addresses located in a particular country.
The hosts' survivability relies on the operators' adaptability. If the business is shut down, new shell companies can be created in response to abuse requests. An upstream provider could simply move IP ranges to new companies. Some providers even relocate their virtual private server (VPS) to make it more difficult for law enforcement to seize systems. When bundled with front-end reverse proxies, hosts also ensure high availability of services. For instance, a host may operate continually from a location for a certain period before actively jumping across different countries.
Bulletproof Hosting: A Customer Perspective
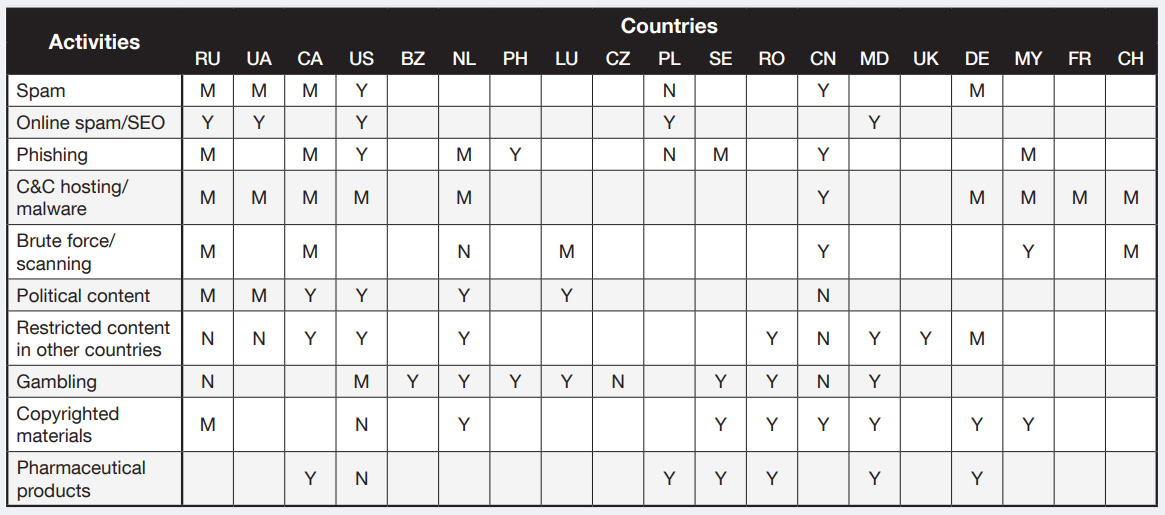
Preferred criminal hosting locations by country and activity, based on underground actors' hosting feedback
Note: [Y]es: Underground actors mention this location; [N]o: Underground actors actively suggest not using this location; [M]aybe: Underground actors sometimes mention this location along with restricted factors, like the targeted region
The many differences in restrictions and services based on location have led criminal sellers to combine benefits to maximize their business model. Many of the BPH advertisements we encountered not only describe the type of hosting, but the country where the equipment is physically located.
BPH providers also appear to be well-informed of the regional legalities and how law enforcement agencies respond and cooperate internationally. It is common for operators to minimize the number of useful log files and to access the system from anonymous sources like Tor networks.
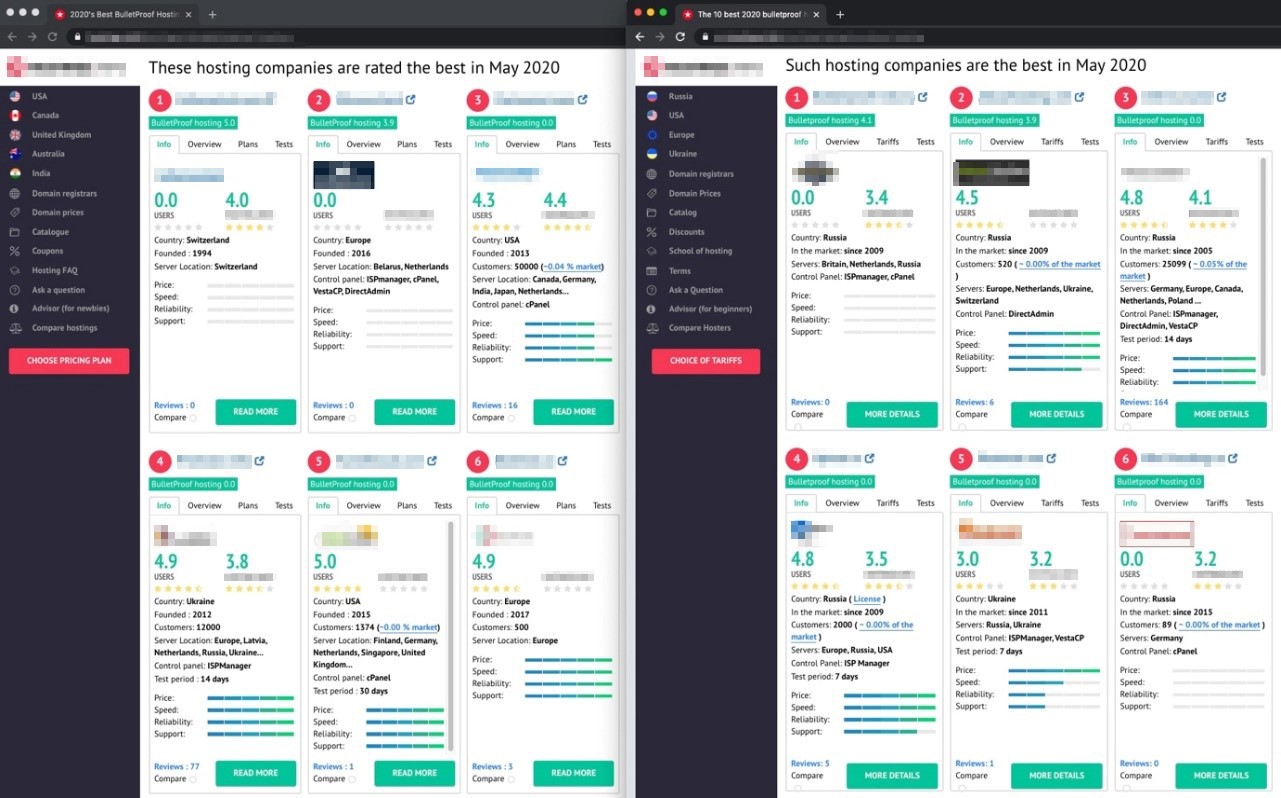
An example of a ranking page for bulletproof hosting services (list of service offerings for English language speakers [left], list for Russian language speakers [right])
Customers, like any other buyer, could compare hosting providers available in the market. A site we came across integrates information from over 1,000 hostings (both legitimate and questionable) and breaks them down into categories and features, along with detailed customer reviews. As indicated in the breakdowns in the preceding images, a host's geographical location is a significant factor that can influence buyer preferences.
Criminal Approaches to Avoid DDoS Attacks and Forum Scraping
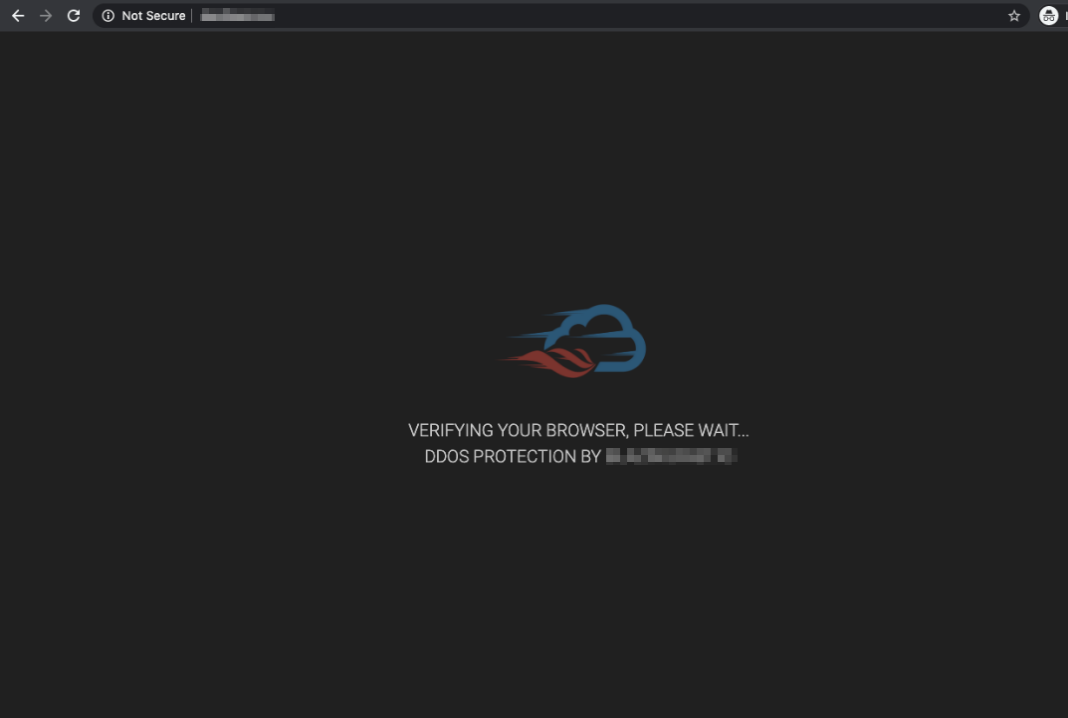
Underground forums are common targets of distributed denial of service (DDoS) attacks by disgruntled forum members and competitors. A downtime could significantly impact a forum's reputation, consequently leading to members moving to competitor forums. As members leave, operators' revenue gets affected. Having protection against DDoS attacks, on the other hand, elevates a forum's reputation as a stable platform.
An underground forum protected by a DDoS protection service
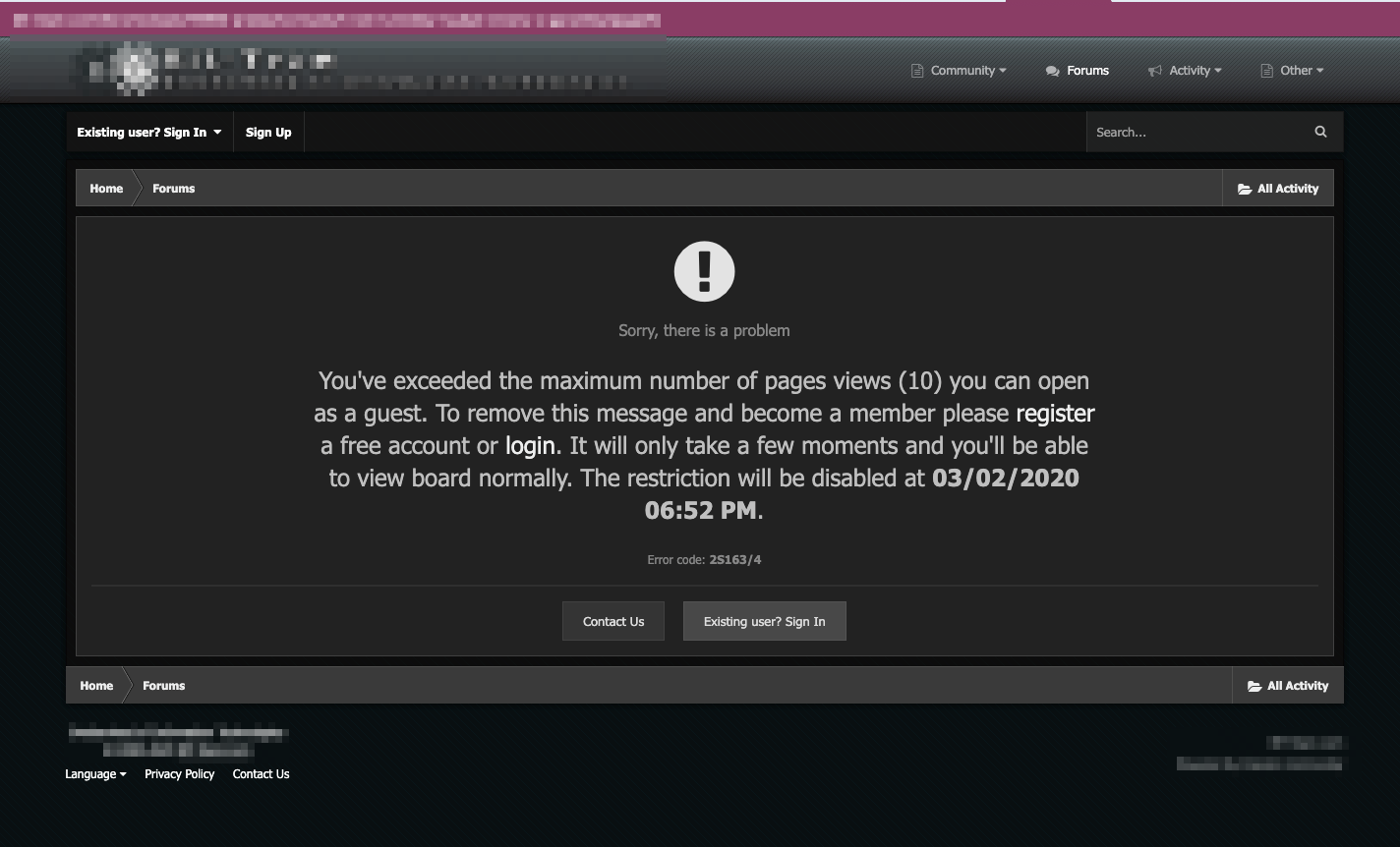
Forum operators also employ various mechanisms to avoid automated scraping of their content. Forum scraping is often done by threat researchers and law enforcement investigators to analyze the activities of underground actors. Some forums would then allow temporary or unauthorized users to see only 10 pages within a 24-hour timeframe.
Forum scraping protection in an underground forum
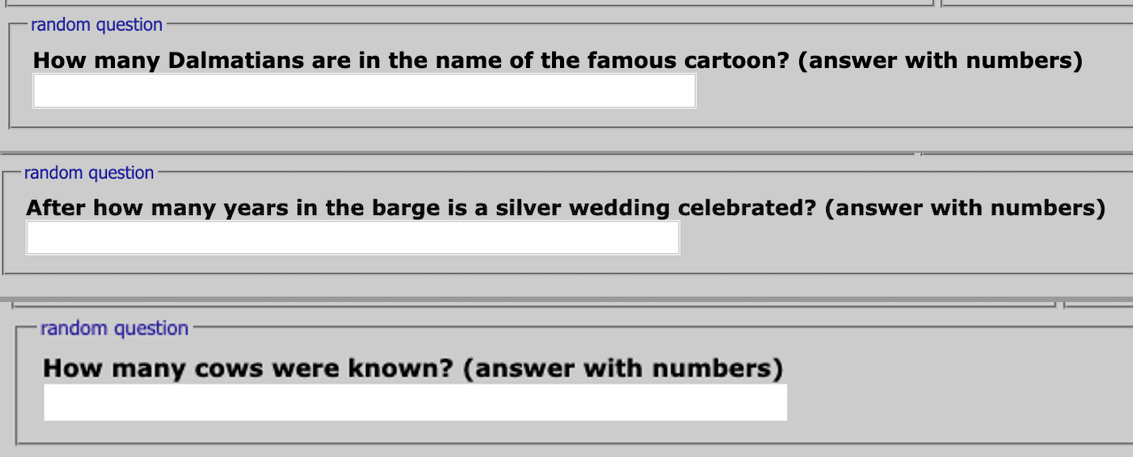
Examples of questions used instead of a captcha
Like legitimate sites, criminal forums also use Captcha systems to protect its pages from automatic scraping and visits by search engines and bots. For some underground actors, however, they have come up with creative replacements for Captcha. Sites usually ask random questions on different application fields — some of which require knowledge of the cultural background of the forum's intended audience. (For instance, the last question could be tricky in the English translation, while the Russian wording hints at the "33 Cows" song from the 1983 "Mary Poppins, Goodbye" USSR movie.) The preceding screenshot shows an example of such a system, which starts with a category of general knowledge questions before going into a niched query that could stump non-native speakers relying on machine translation.
As infrastructure-providing platforms diversify, malicious sources have proved to be tricky to uncover. Our research paper, "The Hacker Infrastructure and Underground Hosting: Cybercrime Modi Operandi and OpSec," aims to shed light on the ecosystem of bulletproof hosting from a criminal perspective. In particular, we outline major survival principles and key weaknesses that can help researchers and law enforcement undermine BPH providers. This way, readers will be able to understand the cybercriminal mindset and frame an appropriate response.
More underground hosting research:
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One