Crypto-Ransomware Spreads into New Territories

Though crypto-ransomware detections are prevalent in regions like North America and Europe, we have noted a spike in incidences outside of these territories. Much interest in the Critroni or Curve-Tor-Bitcoin (CTB) Locker—an old crypto-locker variant—is already being noticed in Asia. Though the number of detections in these new territories is not as large, it can still be a precursor for more widespread crypto-ransomware incidents in the near future.
What is crypto-ransomware?
It is a type of ransomware that encrypts a user’s system or files in exchange for money. This prevents a user from accessing his files or computer.
[More: Ransomware 101: What It Is and How It Works]
How is CTB Locker different from other crypto-ransomware variants?
- The common CTB Locker asks the user to pay 3 Bitcoins (USD 732.95)
- It does not require the Internet to encrypt files; it can function even without a connection.
- It supposedly offers free decryption for five files.
- It extends the ransom deadline for encrypted files.
- It gives its victims language options for the ransom message.
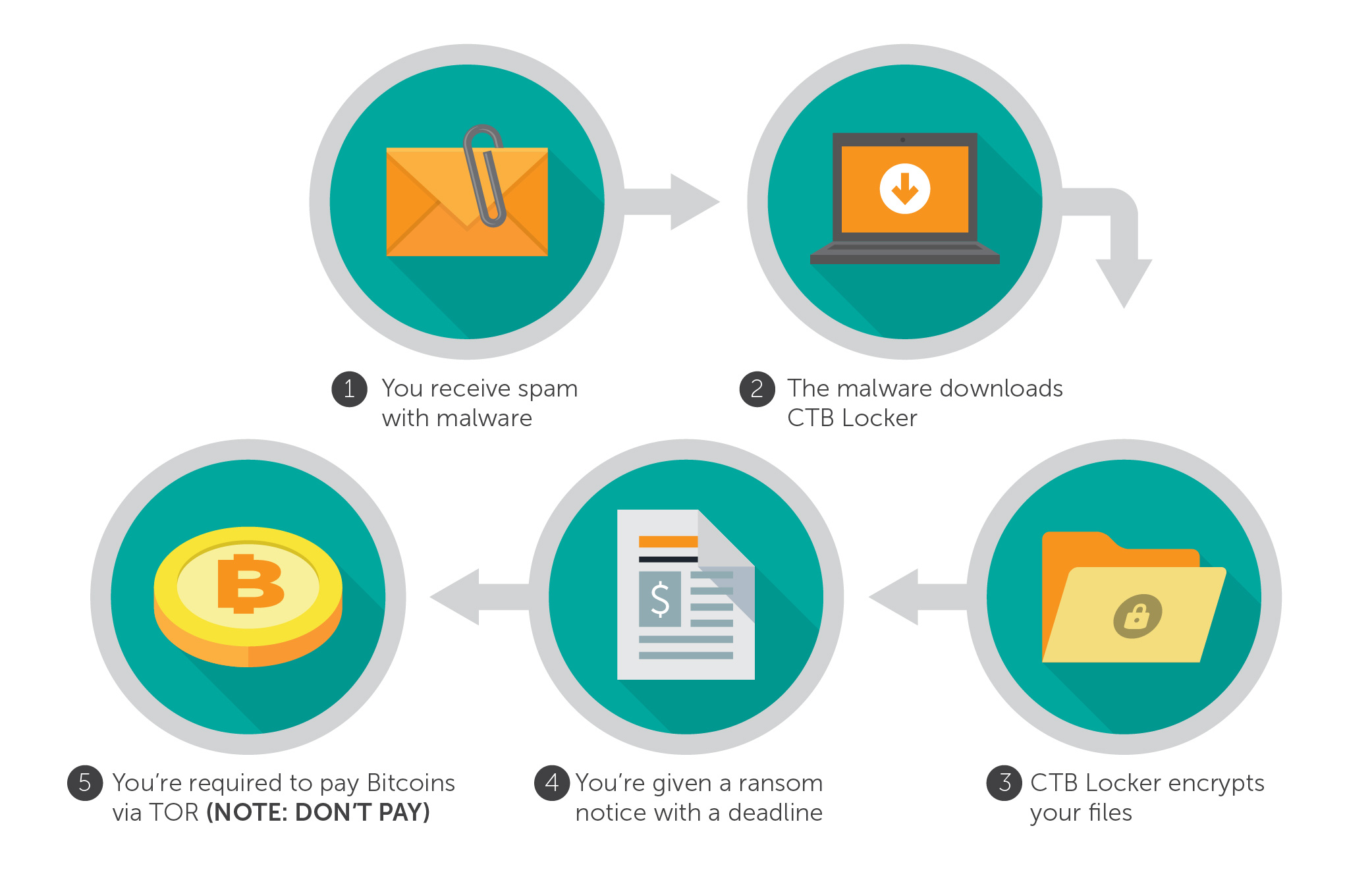
How does a user get infected by CTB Locker?
- The victim receives spam with malware.
- The malware downloads CTB Locker.
- CTB Locker encrypts the victim’s files.
- The victim is given a ransom and a deadline to pay.
- The victim is then required to pay Bitcoins via TOR.
What is CTB Locker’s impact in new territories?
Below are the top affected countries outside of the US and EMEA. The reasons behind the incidences vary, but the most probable causes are poor browsing habits and the lack of proper and updated security solutions installed.
- India
- Thailand
- Indonesia
- Taiwan
- Vietnam
- Malaysia
- Philippines
- Australia
- Hong Kong
- South Korea
- Singapore
- New Zealand
In case users are already infected, can they still retrieve their data?
Though the promise of getting their data back by paying ransom are tempting, they should not. More often than not, chances of retrieving the encrypted data are slim even if they pay. The best way to protect against this type of ransomware is through prevention.
How can users avoid getting infected by CTB Lockers?
They can do the following:
- Avoid clicking suspicious links.
- Backup important data.
- Check the email sender.
- Double-check the message content.
- Ensure their software is updated.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One