Exploits as a Service: How the Exploit Kit + Ransomware Tandem Affects a Company’s Bottom Line
 View guide: Exploits as a Service
View guide: Exploits as a Service
Blackhole Exploit Kit introduced the lucrative but hazardous exploit-kit-ransomware combo with CryptoLocker back in 2013. Soon after, other exploit kits like Angler, Neutrino, Magnitude, and Rig followed suit. At least 18 percent of known ransomware families now arrive via exploit kits.
It should be noted that exploit kits have been distributing a plethora of threats as early as 2006. Since 2010, we’ve seen at least 100 exploits incorporated in more than ten kits. Ransomware comprise just one of the many possible threat types that exploit kits can deliver to vulnerable systems.
[READ: More on exploit kits]
Ransomware has already raked in around US$209 million from enterprises alone in the first quarter of 2016. While data loss is an immediate ransomware risk, other ill effects include damage to brand and reputation and legal fines to additional costs to recover critical data do surface.
[READ: The Reign of Ransomware]
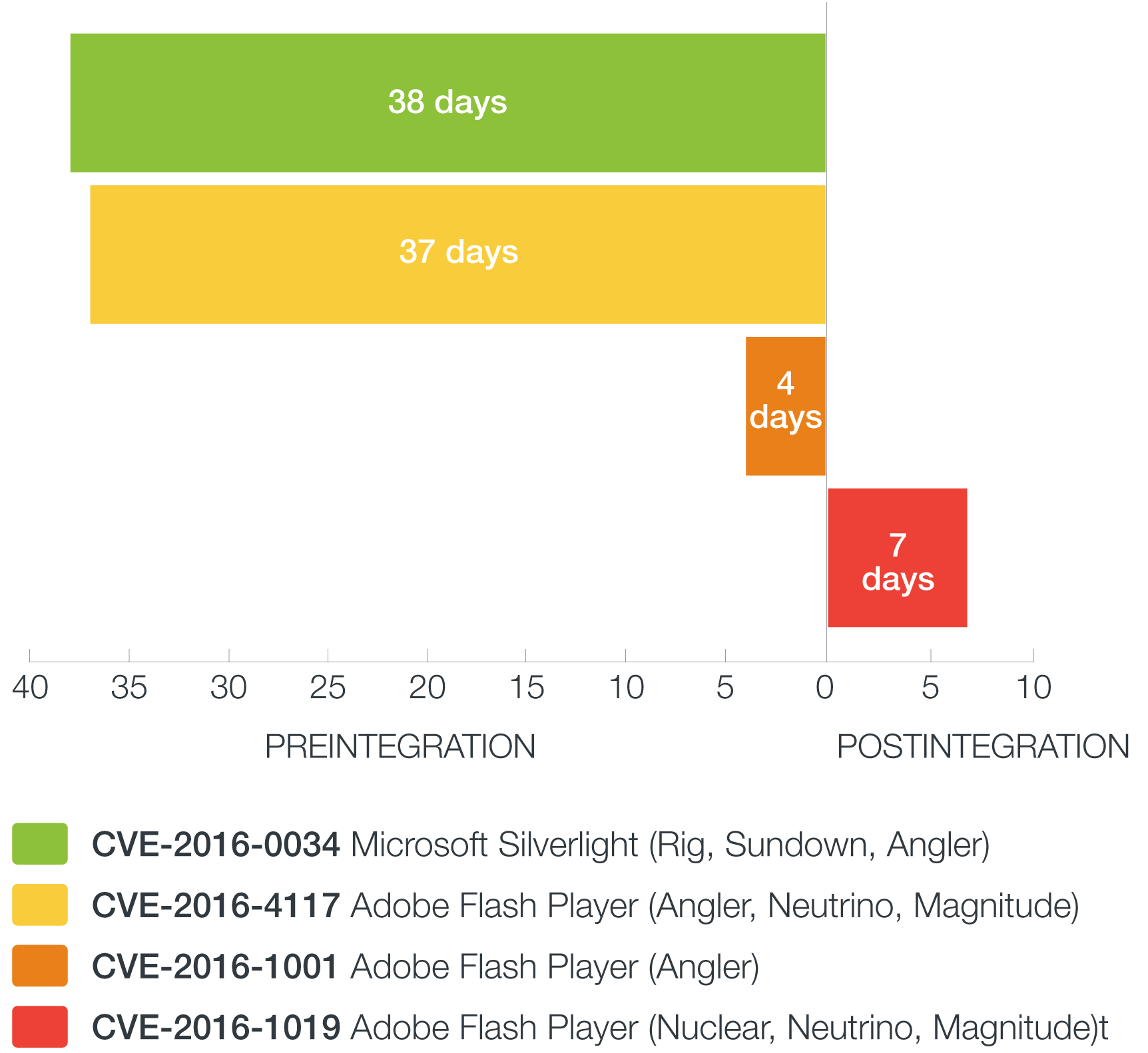
What makes exploit kits an effective means of delivering a myriad of threats? They require less user action, for one, as they take advantage of unpatched vulnerabilities in the most popular software. In the first half of the year alone, Trend Micro (with TippingPoint) and the Zero Day Initiative (ZDI) has already detected 473 vulnerabilities.
At any given time, networks will always have vulnerabilities, especially if they use legacy systems or software. Adding zero-day vulnerabilities to the mix turns system management into a constant race against time. IT administrators need to protect their networks even if security patches for zero-day exploits that are integrated into kits have yet to be released. They need to face various challenges like keeping mission-critical systems online while securing their network perimeters. It doesn’t help that they have to test patches prior to deployment. On average, enterprises need around 30 days for patch testing. These and other factors can introduce windows of exposure to threats brought on by exploit kits.
Read the attached guideon Exploits as a Service (EaaS) to learn how a company’s bottom line can suffer from related attacks and what it can do to secure its perimeter and data.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One