Spam Tricks Users Into Downloading Fake Facebook Messenger
Publish date: 17 de abril de 2011
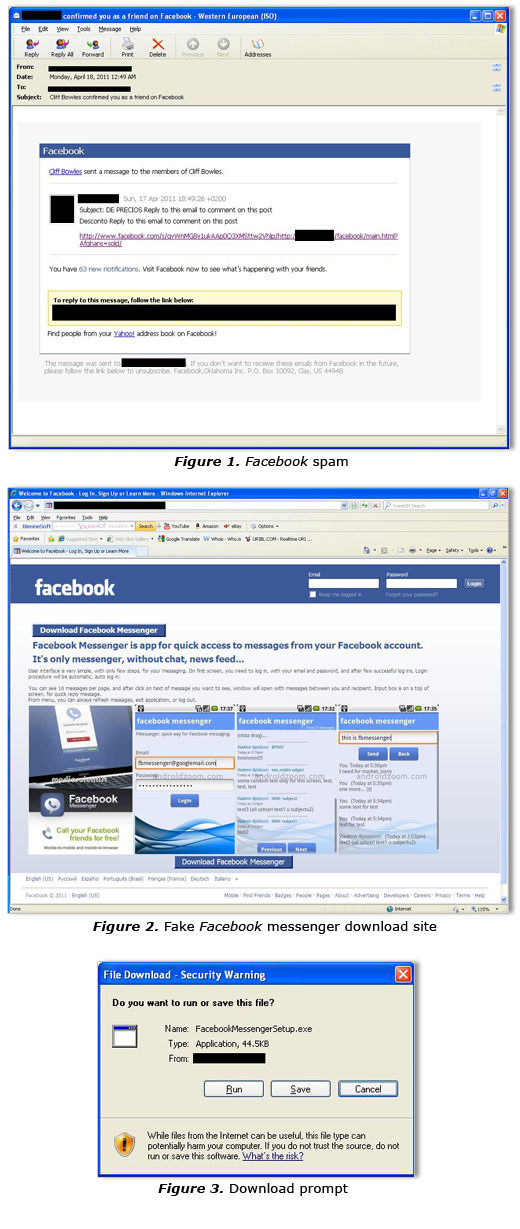
TrendLabs engineers have intercepted new spam samples that use social engineering tactics to trick users into download a backdoor onto their systems. This attack starts once users receive an email notification (Figure 1) purporting to originate from Facebook. When users click any of the links in the email body, they are directed to a website (Figure 2) that appears to be affiliated with the said social networking site. The site, a supposed download page for the nonexistent 'Facebook Messenger', also contains links that point to the same location where FacebookMessengerSetup.exe-1 can be downloaded. Trend Micro detects this malicious executable file as BKDR_QUEJOB.EVL.
Fecha/hora de bloqueo del spam: 17 de abril de 2011 GMT-8
TMASE
- Motor TMASE: 6.5
- Patrón TMASE: 8080