ICEDID
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
ICEDID, also known as BokBot, is a modular banking malware designed to steal financial information. It was first discovered around 2017 and observed in the wild downloaded as a second stage payload from EMOTET campaigns.
It is capable of propagation over the network, monitor activities from the infected system and exfiltration of data. It conducts a man-in-the-browser attack such as web-injection, proxy setup and redirection. It continuously evolves to increase persistence and detection evasion.
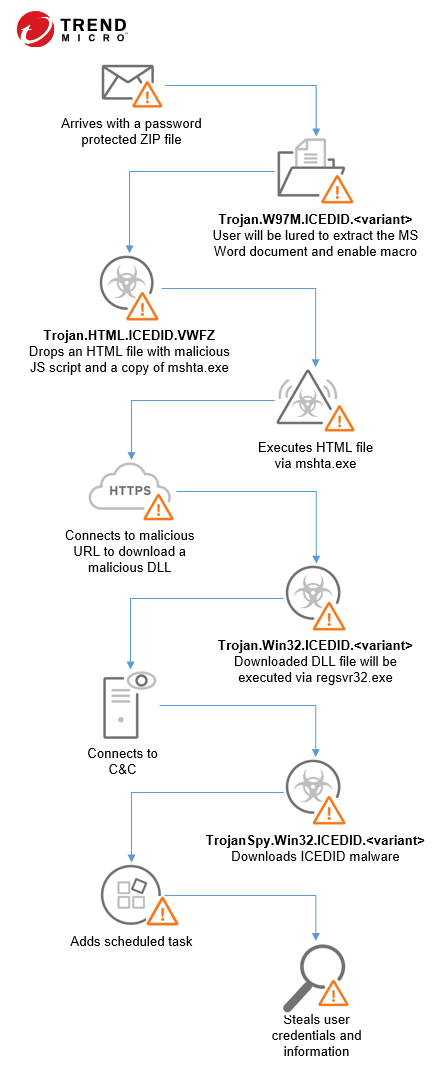
In recent spam campaigns, it uses a technique similar to the campaign used by a cybercriminal threat group called Shathak or TA551 to distribute the malware. The spam has a password protected ZIP attachment that appears to contain a request document. Extracted from the ZIP file is an MS Word document containing malicious macros. It uses social engineering attempt to trick the user to enable the macros. It then downloads the ICEDID loader as a DLL file with a different extension such as .tmp or .pdf. It connects to the C&C server to download a PNG file that contains encrypted data of the ICEDID malware. The loader decrypts the data and inject the malware in an instance of svchost.exe.
It is capable of the following:
- Has anti-debugging and anti-VM checks
- Hides encrypted payload in PNG files (steganography)
- Modification of code injection tactics
- Stealth and fileless operation
It typically follows the infection chain below: