Home intrusions are often pictured in the form of physical break-ins. The current reality of having many internet-connected devices in the home, however, has given rise to another type of intruder — one whose point of entry is the home network, where connected devices are potentially open to compromise. The sheer number of entry points can put the devices at the attackers’ mercy, either by locking them up with ransomware or even making them part of an army of botnets for distributed denial-of-service (DDoS) attacks. Mirai, Persirai, and Reaper botnet attacks have already driven the point home: unsecured connected devices can be highly disruptive. The botnets harnessed vulnerable devices such as IP cameras and routers to cripple several networks and wreak significant downtime. More reports have even surfaced over the years of how hackers could break into home devices like baby monitors and smart TVs to remotely snoop on personal data or seize control of the devices themselves.
Threats to Unsecured Home Routers
Beyond computers, smartphones, and tablets that an average user may possess, connected devices will continue to expand into homes, workplaces, and even factories at a rapid pace. This inevitable shift of having connected environments can easily be disrupted without proper security, which starts at the gateway: the router.
A vulnerable router makes a vulnerable smart home. Securing home routers will allow users to keep stock of all connected devices. The router acts as a hub for all of the devices, enabling users to keep tabs on network traffic in real-time and implement security across multiple devices. However, poor basic security such as an incorrectly configured home network, weak passwords, and lack of firmware updates are the factors that we saw in 2017 that opened doors to threats to the smart home.
Cyberattacks that involve home networks have two kinds: inbound and outbound. Attacks are classified as inbound if the home network is breached to target connected devices like desktop computers, tablets, smart TVs, and game consoles via the internet (from internet to home network). Outbound attacks, on the other hand, refer to instances when hackers access a home device through an inbound attack and then use the device to remotely execute malware, either to obtain sensitive information or intercept communications, or to launch attacks against other external targets (from home network to internet).
| Inbound Attacks | Number of Events |
| MS17-010 SMB-related | 2,441,996 |
| Brute Force Login via RDP | 1,464,012 |
| Suspicious HTML Iframe Tag | 926,065 |
| Microsoft SQL SA Password Brute Force | 431,630 |
| Brute Force Login via POP3 | 373,782 |
| Brute Force Login via SMTP | 289,746 |
| Remote Command Execution via Shell Script | 241,498 |
| CoinHive Mining Attempts | 194,665 |
| Apache Struts Dynamic Method Invocation Remote Code Execution | 175,019 |
| Netcore Router Backdoor Access Exploit | 142,902 |
Note: Our telemetry shows that desktop/laptop computers primarily make up the home devices detected triggering the events.
When considering all of the home networks we observed in 2017, there was a 3:1 ratio of outbound attacks to inbound attacks — meaning there were more instances of home devices being used to attack the internet. What’s interesting to note is that MS17-010 SMB-related was the most common attack, both inbound and outbound, with desktop and laptop computers targeted for their Windows Server Message Block (SMB) protocol. This can be traced back to the pervasive threat of the WannaCry ransomware in May, whose impact resonated across many industries throughout the year. With its worm-like behavior, WannaCry did not only encrypt data but also managed to affect connected devices and equipment in hospitals and factories.
| Outbound Attacks | Number of Events |
| MS17-010 SMB-related | 9,716,094 |
| ICMP BlackNurse | 1,786,694 |
| DNS Amplification | 1,615,122 |
| Brute Force Login via RDP | 1,067,895 |
| SYN Flooding via TCP | 777,218 |
| IIS HTTP.sys-related Denial of Service | 544,883 |
| IMAP SUBSCRIBE Command Buffer overflow | 457,158 |
| HTTP Negative Content-Length Buffer Overflow | 451,049 |
| NULL-Byte Injection | 356,359 |
| Apache Http2 Null Pointer Dereference | 303,442 |
Note: Our telemetry shows that desktop/laptop computers primarily make up the home devices detected triggering the events.
Table 3 lists the ranking of all the noteworthy events we detected in 2017, with the respective total event counts. Both inbound and outbound attacks are collated, together with the rules triggered by our intrusion prevention system (IPS). Note that the event counts do not necessarily indicate that they were malicious, as some may include potentially unwanted applications (PUAs) such as adware or grayware.
| Noteworthy Events | Number of Events |
| Cryptocurrency Mining | 45,630,097 |
| TELNET Default Password Login | 30,116,181 |
| MS17-010 SMB-related | 12,164,033 |
| Brute Force Login | 3,695,143 |
| ICMP BlackNurse | 1,792,854 |
| DNS Amplification | 1,602,448 |
| Android Stagefright-related | 1,170,348 |
| Suspicious HTML Iframe Tag | 946,832 |
| SYN Flooding via TCP | 855,185 |
| IIS HTTP.sys-related Denial of Service | 547,570 |
Note: Our telemetry shows that desktop/laptop computers primarily make up the home devices detected triggering the events.
As shown in Table 3, cryptocurrency mining was the most detected network event in 2017. A number of factors may have affected the spike. For one, the top cryptocurrency Bitcoin, no matter how much the price fluctuates, has risen to over US$100 billion in market capitalization — prompting investors to jump in on the seeming cryptocurrency craze.
Throughout 2017, we observed different home devices that were mining for cryptocurrency (notably Q3 having the most pronounced increase), although our telemetry cannot verify if these activities were authorized by the users.
Cryptocurrency mining is a computationally intensive task that requires a lot of processing power. So why is it that aside from PCs, IoT devices, which are relatively underpowered, are displaying mining activity?
One controversial reason is that some companies want to monetize their websites through their users’ CPU power by adding cryptocurrency mining scripts. Think of it as an alternative revenue stream to intrusive online advertising, without user consent. Many websites have been reported to be cryptojacking visitors, i.e., surreptitiously stealing resources from visitors’ computers to mine for cryptocurrencies. This has led to crackdowns on illicit crypto-mining through browser extension and built-in blockers.
Cryptojacking is not limited to browsers. Cryptocurrency-mining malware, for instance, are capable of infecting devices to illicitly mine for cryptocurrency. We already found a particular miner that first exploits a vulnerability then installs WMI (Windows Management Instrumentation) scripts in order to download its coin-mining payload. Such malware can spread the same way other malware types spread, e.g., through spam emails and malicious URLs, and take advantage of the computing power of multiple devices to increase yield from mining.
Unlike ransomware, which needs to actually engage the victim for the attack to pay off, unauthorized cryptocurrency mining is almost unnoticeable. Unsuspecting users will not detect any visible indicators of suspicious activity in their devices, especially those with low user interaction like IP cameras, unless users take time to inspect their systems in case of a hike in electricity usage or frequent system crashes. That shroud of muted activity is just what cybercriminals want — small money generated per device, but when accumulated, might just be lucrative down the road.
It is possible that we are seeing a lot of cryptocurrency mining events today because cybercriminals are exploring whether compromising home devices for financial gain is a plausible venture in the long run. After all, the anonymity afforded by cryptocurrencies already draws cybercriminals to use them to facilitate activities.
Aside from use by cybercriminals, the volatile nature of the cryptocurrency market and growing public interest in its trade have attracted further government scrutiny. Furthermore, the many cryptocurrency-related hacks in recent years are elevating the conversations on the likelihood of international cryptocurrency regulation, which could entail stricter rules on exchange platforms for virtual currencies.
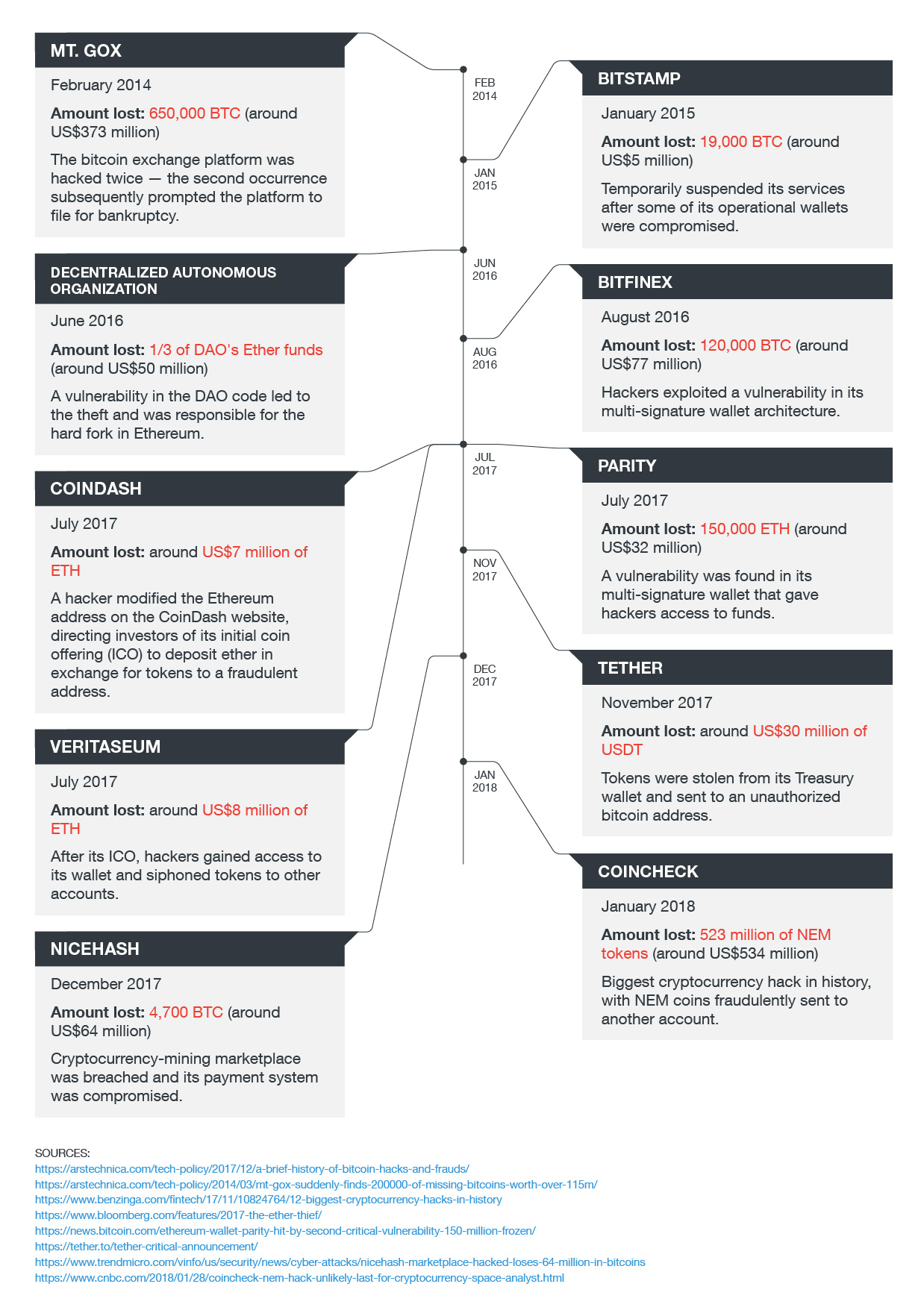
Note: The approximate U.S. dollar equivalents of the digital currencies were taken from the current value at the time the hack occurred.
Drawing from the WannaCry outbreak in May that affected many computer systems, what stood out was how connected systems can be locked up with ransomware. Ransomware in connected devices is not only about cybercriminals targeting valuable data; criminals can also lock the devices up so that their functionalities are rendered useless, or even controlled remotely by hackers, until users pay up.
A flaw in the SMB was exploited by the WannaCry ransomware. Using EternalBlue, the attackers were able to propagate the ransomware across networks, without requiring any direct interaction with the users of other connected machines. It can take only one affected user for the ransomware to infect more machines and systems as it moves through the network.
Shortly after, the same exploit was used in the Petya ransomware outbreak, crippling more computers and networks in its wake. Malware families like WannaCry and Petya are a cause for concern: Internet-connected devices and systems present potential entry points for any hacker that looks to infect networks, possibly even in home environments, with lax security protections in place.
And it’s not only ransomware that will present threats to home networks. As noted in our security predictions for 2018, we can see even more vulnerabilities being discovered due to many device manufacturers bringing functionality to the fore with security often as an afterthought. Mirai’s success, for instance, in targeting vulnerable devices has brought forth other IoT malware that bank on vulnerabilities, as in the case of Persirai, which targeted over a thousand IP cameras exposed on the internet.
An interesting finding from last year is the marked increase in Telnet Default Password Logins. While it is possible that some of the numbers were triggered by regular users’ login, it is not far-fetched that most of the numbers were prompted by malicious attempts. Telnet protocol is known to be used for remotely logging in to computers via the internet, while factory default passwords are notoriously taken advantage of to access vulnerable devices.
What comes to mind is Mirai: Once infected with it, computers continuously search the internet for vulnerable devices and then use default credentials to log in. Default credentials, which many users may ignore or forget to change, infamously powered the botnet that facilitated the largest DDoS attack on record. With its code since publicly released in 2016, Mirai has seemingly spawned a flurry of botnets — some even causing permanent damage — that also use default credentials in their attack. Armed with a list of default passwords used by potentially hundreds of thousands of connected devices, hackers can also consider creating botnets of their own.
Aside from default password logins, home users also need to be mindful of Brute Force Logins via RDP. RDP stands for Remote Desktop Protocol and is commonly used for remote administrator access. Through RDP, a remote user is allowed to log in as if a local user and use specific operating systems (OSs) or applications. This ease of use may pose a problem when users are willing to make security exceptions for it.
The risk lies in the network, when a hacker is able to gain access to the RDP without the user admin knowing. The home network is where all the connected devices and stored data lie. Information about users and control of the devices — these are just the things a brute force attacker might want.
In a brute force attack, an attacker repeatedly attempts within a short period to log in to the RDP servers by identifying the source and destination IP used. If the pair is tracked, an attacker will try to gain access to the machine by brute forcing into the system using countless username and password combinations. This method of attack can be easy to implement and difficult to detect. Once successful in matching a combination, an attacker can have full control of the routers or connected devices and use them for malicious activities. Brute force logins via RDP, additionally, have also been found to be related to ransomware infections.
Securing Home Routers With Trend Micro Smart Home Network
With over 1 million active routers and 6.7 million devices in over 200 countries, including United States, China, Sweden, Canada, and Japan, secured by Trend Micro Smart Home Network™ (SHN) solution, we constantly analyze feedback data and potential network threat activities from routers worldwide.
In 2017, through Trend Micro Smart Home Network’s expansive threat research intelligence, over 110 million of vulnerability connections were prevented by our industry-leading deep packet inspection (DPI) detection of network threat activities in smart homes across the world.
Total number of outbound attacks prevented in 2017
We protected home networks from over 8.5 million attacks that attempted to connect to home devices. Almost 75,000 hits of Mirai attacks and 50,000 of Persirai’s were also prevented from getting into homes.
We also blocked over 6.7 million hits of ransomware-related site connections. Over 460,000 hits of ransomware attacks were blocked through virtual patching, while 17 million hits of MS17-010 SMB-related attacks were prevented less than two months after the WannaCry and Petya outbreaks alone.
Best Practices for Home Users
Applying timely patches is one of the best forms of protection for home users, since the updates are usually related to security issues. Make sure to update the firmware of your device as soon as they are available; and if the device allows, enable the auto-update feature. Other measures you can take:
- Implement network segmentation for devices and isolate them from public networks.
- Monitor outbound and lateral network traffic. Identify the baseline of your devices’ normal traffic and monitor for aberrant behavior that may be caused by rogue devices in the network.
- Disable device functions that you don’t regularly use and set up a firewall to restrict traffic to specific ports only.
- Do not use default, easy-to-guess passwords, and avoid using personally identifiable information (PII) when setting up devices, starting with the router. Use unique and strong passwords for multiple accounts.
- Do not click on suspicious URLs or attachments from unknown sources. An infected connected device may corrupt other devices in the network.
Comprehensive Security Solutions for Home Networks
Home routers sit between connected devices and the internet. Home users should employ router security that will be able to identify potential attacks on all devices connected to the network. Trend Micro Smart Home Network can help secure potential network intrusions through virtual patching that blocks malicious traffic from the gateway. System configuration settings such as password strength assessment for all connected devices and parental controls for protecting kids online are also some of the factors that build a secure home network. SHN is also capable of the following features:
- Provide Device Identification (Device-ID) for different smart device types and Application Identification (Application-ID) for different application behaviors that allow visibility across the home network
- Improve internet traffic management through better bandwidth allocation and traffic prioritization techniques with Intelligent Quality of Service (iQoS)
- Identify and block both inbound and outbound attacks before they reach vulnerable connected devices, powered by built-in DPI for embedded network security
- Offer a mobile application that allows a user to control children’s network access to mobile devices even if the user is away from the home network
- Employ a global network of threat intelligence to update cloud data analysis continuously and block threats in real time
The continuing expansion of connecting everything will only further improve productivity and enhance convenience for home users. The same connectivity, however, will present a number of consequences if not implemented properly: The devices will be used to launch direct attacks against users, or to mount other types of threats.
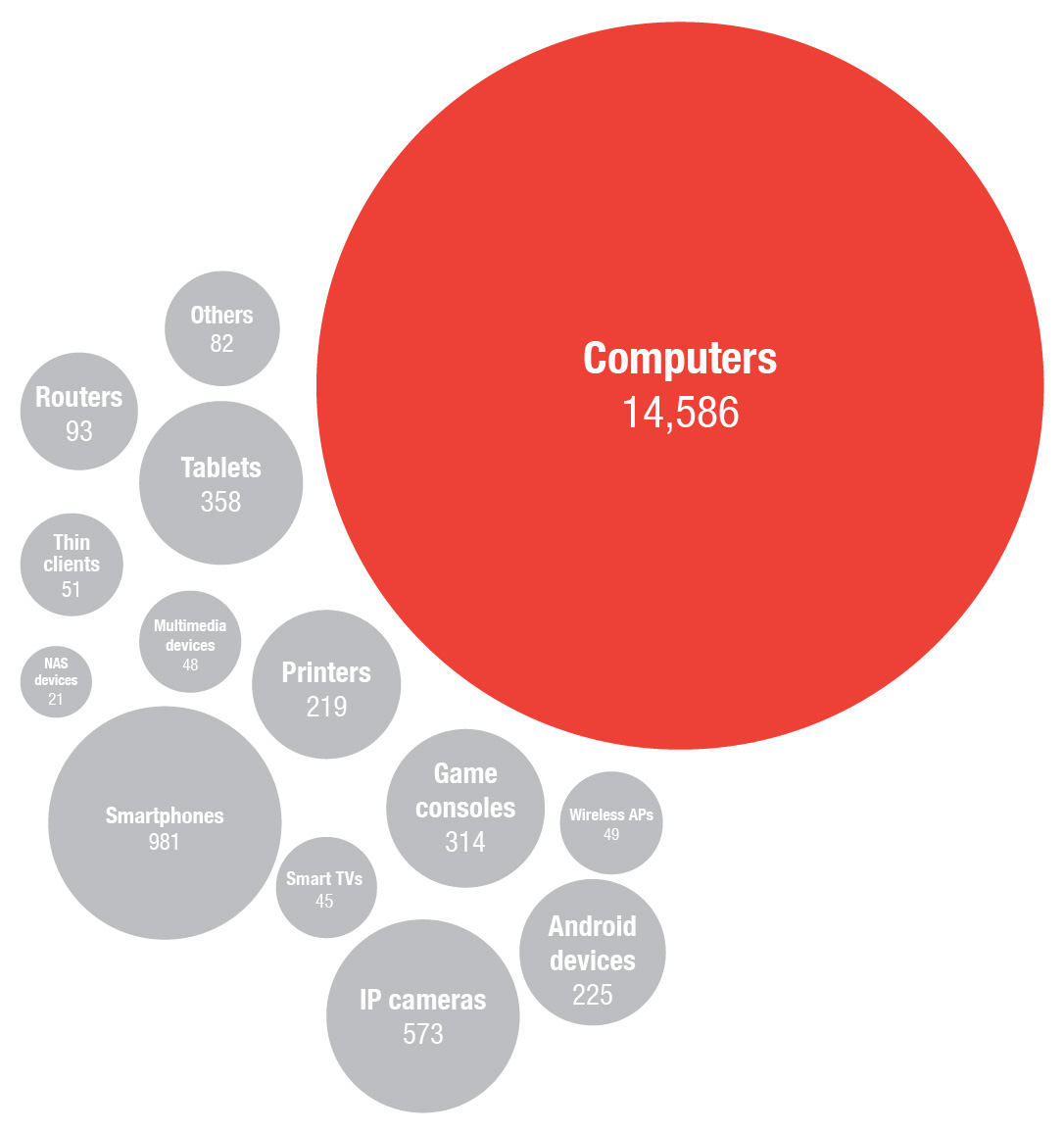
With an average of 11 connected devices per smart home, it’s not surprising that we found about 10 percent of homes with compromised devices. Around 36 percent of those connected homes visited at least one malicious site every week.
Home users, as always, should be careful with their online activities and be responsible for configuring their devices securely. As we see more smart, connected devices hitting the market, it can only be anticipated that the attack surface in homes will be broadened, giving cybercriminals more potential opportunities to abuse the home network. Users, however, can adopt the measures we shared to avoid risks and stay secure.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One