 View Demonstrating Industrial Robot Attacks in Today’s Smart Factories
View Demonstrating Industrial Robot Attacks in Today’s Smart Factories
The modern world relies heavily on industrial robots. But is the current robotics ecosystem secure enough to withstand a cyber attack?
Can Robots Be Compromised?
Industrial robots have replaced humans in a lot of large-scale production and manufacturing activities because of their efficiency, accuracy, and safety. These mechanical, programmable devices can now be seen in practically all industrial sectors―making cars, fabricating airplane parts, assembling food products, and even providing critical public services.
Soon enough, robots will become a ubiquitous feature of modern factories that we must ask now whether the current ecosystem of industrial robots is secure enough to withstand a cyber attack. This is the question we—the Forward-looking Threat Research (FTR) team and our collaborators from the Politecnico di Milano (POLIMI)—had in mind when we started examining the attack surface of today’s industrial robots. More importantly, we wanted to demonstrate whether it is actually possible to compromise them.
This attack demonstration, which we documented in the following video, was done in a laboratory setting on an actual working industrial robot. Due to the architectural commonalities of most modern industrial robots and the existence of strict standards, the robot chosen for our case study is representative of a large class of industrial robots.
An industrial robot is an “automatically controlled, reprogrammable, multipurpose manipulator programmable in three or more axes, which can be either fixed in place or mobile for use in industrial automation applications.
What Robot-Specific Attacks Are Possible?
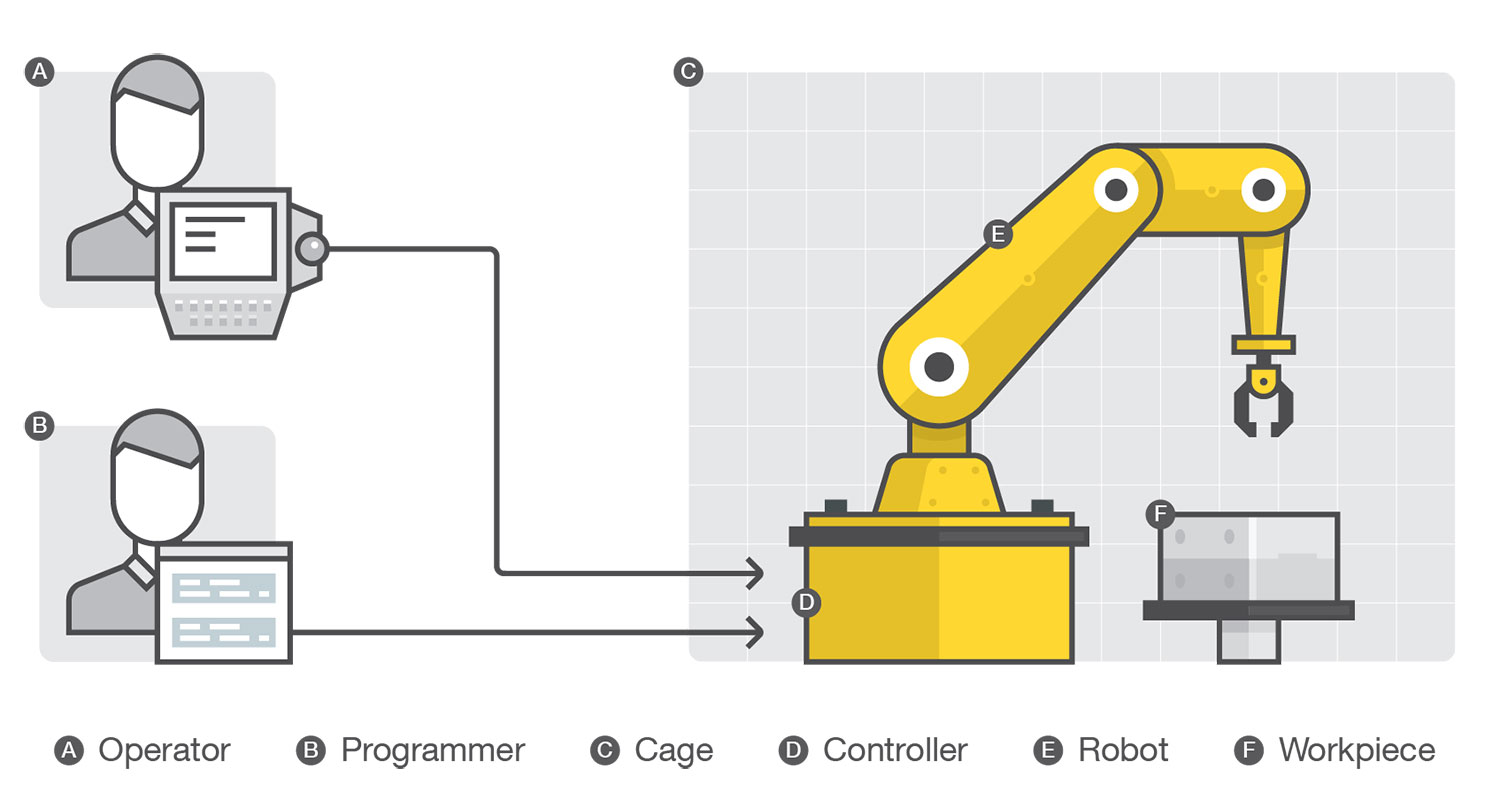
Operating an industrial robot requires several parts working together properly. A programmer or operator typically controls it by issuing high-level commands through the network (via a remote access interface like a teach pendant) to a controller. The controller, which is nothing but a computer, then translates the commands into low-level inputs for the different components of the robotic arm to interpret and execute.
Industrial robots are expected to perform with a high degree of safety, accuracy, and integrity. Any violation of these operational requirements, if initiated through a digital attack, can allow a cyber attacker to take control of a robot. We were able to determine five classes of attacks that are possible once an attacker is able to exploit any of the several weaknesses that we found in industrial robot architectures and implementations.
In our comprehensive security analysis, we found that the software running on industrial robots is outdated; based on vulnerable OSs and libraries, sometimes relying on obsolete or cryptographic libraries; and have weak authentication systems with default, unchangeable credentials. Additionally, the Trend Micro FTR Team found tens of thousands industrial devices residing on public IP addresses, which could include exposed industrial robots, further increasing risks that an attacker can access and compromise them. The vendors, with whom we are working closely, have taken our results very responsibly, showing a positive attitude toward securing the current and future generation of industrial robots.
Attack Class and Description
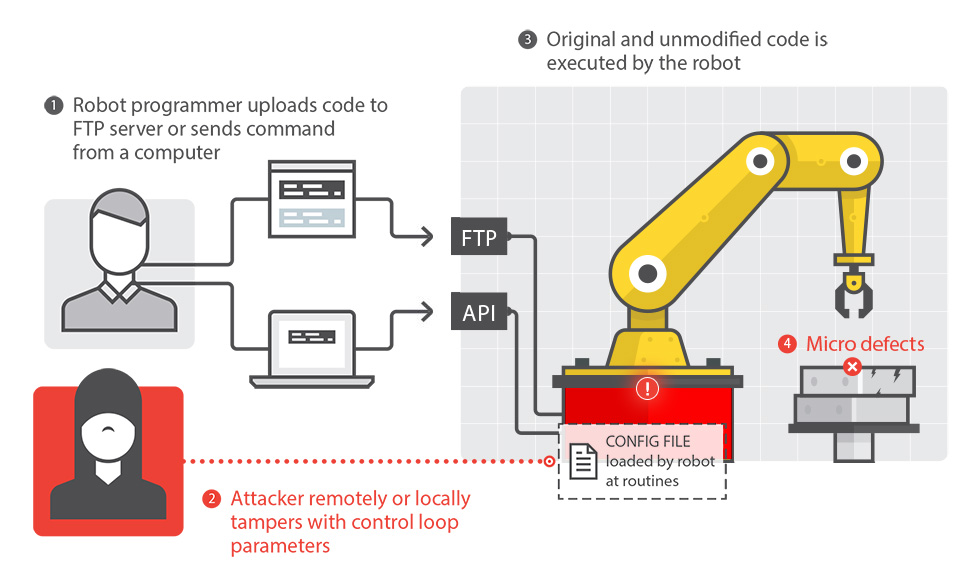
Attack 1: Altering the Controller’s Parameters
The attacker alters the control system so the robot moves unexpectedly or inaccurately, at the attacker’s will.Concrete Effects: Defective or modified products
Requirements Violated: Safety, Integrity, Accuracy

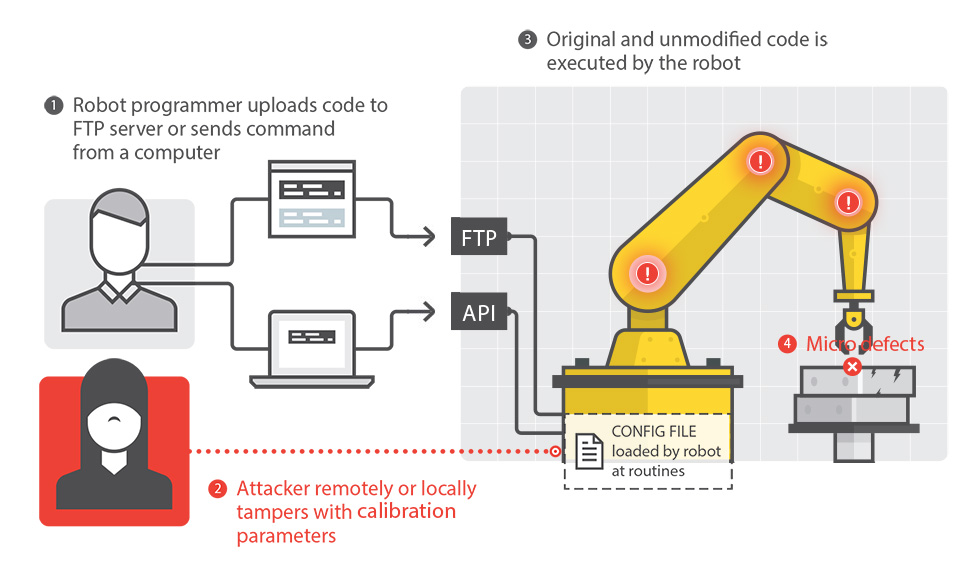
Attack 2: Tampering with Calibration Parameters
The attacker changes the calibration to make the robot move unexpectedly or inaccurately, at the attacker’s will.Concrete Effects: Robot damages
Requirements Violated: Safety, Integrity, Accuracy

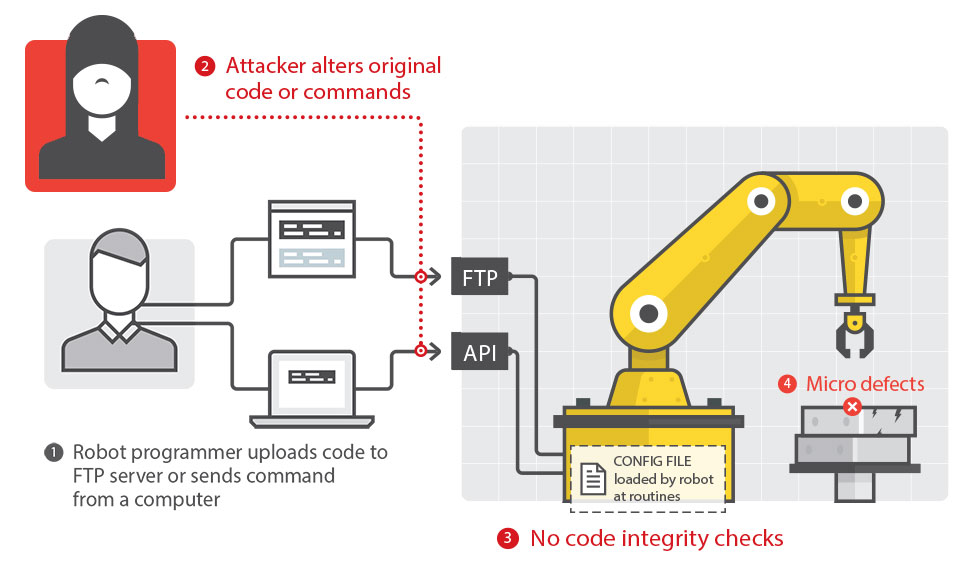
Attack 3: Tampering with the Production Logic
The attacker manipulates the program executed by the robot to introduce defects in the workpiece.Concrete Effects: Defective or modified products
Requirements Violated: Safety, Integrity, Accuracy

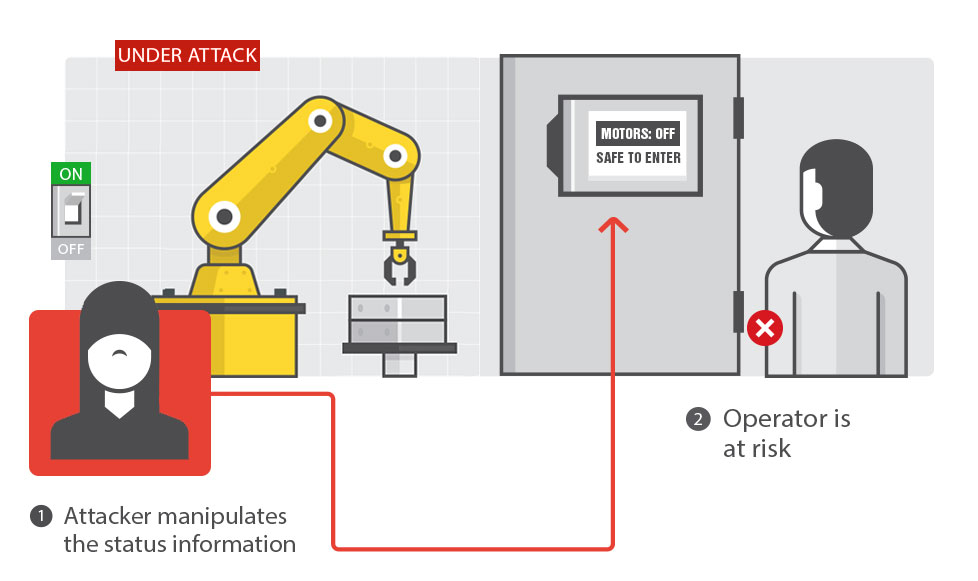
Attack 4: Altering the User-Perceived Robot State
The attacker manipulates the status information so the operator is not aware of the true status of the robot.Concrete Effects: Operator injuries
Requirements Violated: Safety

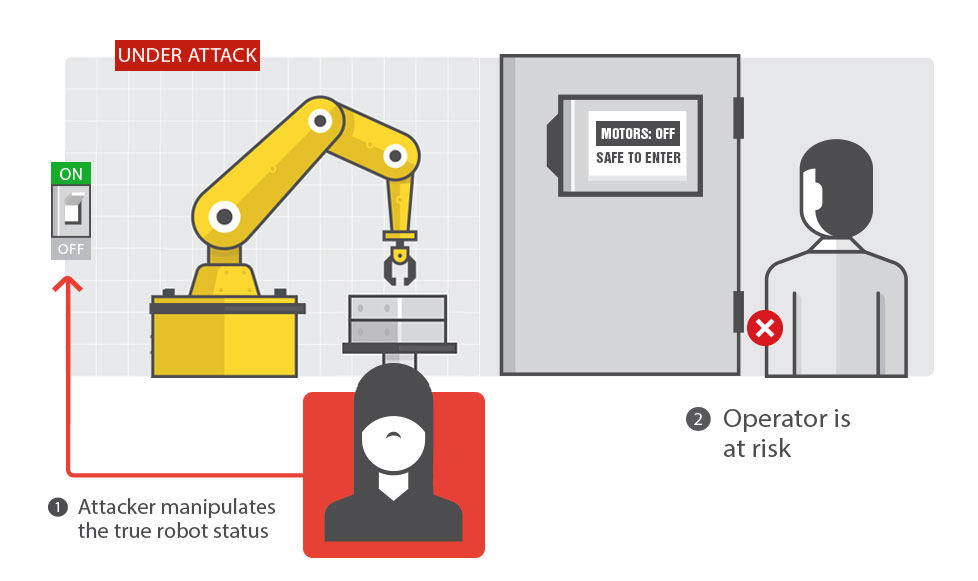
Attack 5: Altering the Robot State
The attacker manipulates the true robot status so the operator loses control or can get injured.Concrete Effects: Operator injuries
Requirements Violated: Safety

How Can These Attacks Be Used?
Using any of the attacks above, the following threat scenarios are possible.
What Should Be Done Now?
Industrial robot standards must consider cybersecurity threats the same way ICS and automotive sector standards have evolved to mitigate them. Network defenders must fully understand the unique position that industrial robots have in terms of securing them. Robots have a very long lifetime, which means vendors must be able to provide security updates to all currently deployed versions, which they may not always be able to do. Furthermore, customers may be worried by downtimes or potential regressions carried by software updates and thus refrain from timely patching their systems.
We treat several other challenges in more detail in our technical paper, including clear and actionable recommendations for improved security strategies for the industrial robot ecosystem. On this journey toward improving the security posture of robots in the Industry 4.0 setting, we also began reaching out to vendors, among whom ABB Robotics stood out in that it readily welcomed suggestions we had to offer and even started working on a response plan that will affect its current product line without losing time.
More exhaustive technical details of our research, including the vulnerabilities we discovered and subsequently reported to vendors, will be published in the upcoming Institute of Electrical and Electronics Engineers (IEEE) Symposium on Security and Privacy in San Jose this coming May.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One