Hacker Infrastructure and Underground Hosting 101:Where Are Cybercriminal Platforms Offered?
 Download The Hacker Infrastructure and Underground Hosting: An Overview of the Cybercriminal Market
Download The Hacker Infrastructure and Underground Hosting: An Overview of the Cybercriminal Market
Underground platforms are part of a mature ecosystem for trading cybercrime goods and services. How does a capable hosting infrastructure allow illicit activities to thrive?
In the cybercrime underground, a criminal’s hosting infrastructure serves as the foundation of their entire business model. It hosts anonymizing services for keeping their activities private, command-and-control (C&C) servers for taking advantage of victims’ machines, and discussion forums for communicating with other criminals. Criminal sellers provide services and infrastructures that other criminals need to execute their attacks. An underground hosting service or underground infrastructure enables threat actors to harbor cybercriminal components and carry out their malicious activities undisrupted by takedowns or arrests, which usually require intervention by service providers.
An underground hosting service can include the provision of hosting infrastructures, domain name provisions, fast-flux infrastructures, traffic accelerators, virtual and dedicated servers, and virtual private networks (VPNs). Hosted infrastructures are also used to send phishing emails, trade illegal goods on online shops, and host virtual private systems (VPS) that can be used to launch attacks from.
In the first part of our underground hosting research series, we’ll be looking into the underground marketplaces to see what goods and services they offer to hacker communities and how criminal sellers conduct their transactions with criminal infrastructure buyers.
Criminal Infrastructure: Services Offered in the Underground
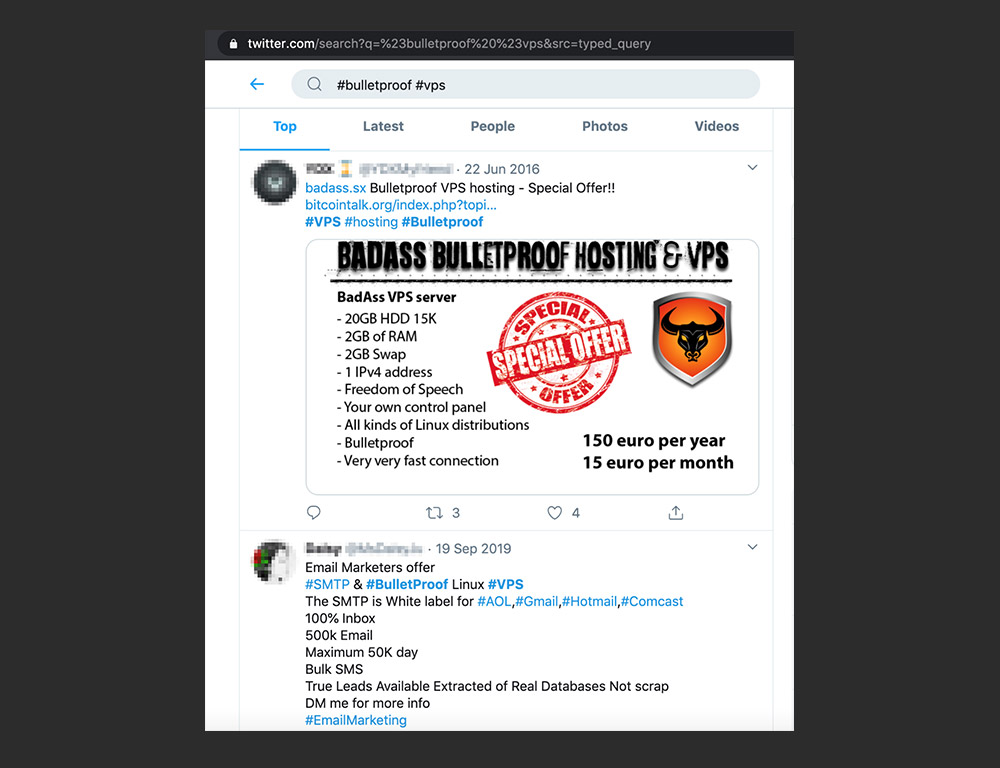
- Dedicated and virtual hosting providers, including bulletproof hosting, fast-flux networks, and other types of hosting provision.
- Service protection and anonymization providers, including anonymization services, traffic acceleration services, proxies, reverse proxy services, and VPNs.
- Additional infrastructure provision, including less used infrastructure provisions such as in-browser botnet services, IoT hosting services, and telecommunication-related services (e.g., calling, call landing, SMS spamming).
- Legitimate services/systems used and exploited for malicious purposes, including free services such as cloud services, dynamic DNS hosting, and SSL certificate provision.
Why is hosting crucial for threat actors and underground users?
Hosting services allow users to bypass internet restrictions, maintain anonymity, and make forensics tricky. Here are other reasons why they’re used often:
- Criminals use it to incorporate malicious components
- Criminal groups use it to facilitate their communication systems
- Botnets require it to deploy C&C infrastructures
- Spam operators need it to host and conduct spam distribution systems
- Underground forums need it to run communication platforms
Hosting Services in the Underground
Underground platforms offer a wide range of services that cater to criminal hackers, from bulletproof hosting and proxies to VPSs and VPNs. Interestingly, such services were also observed on forums related to online betting, online marketing, and search engine optimization (SEO) — the services can be used to produce clicks that can influence search engine behavior.
We also found chat groups in online messenger platforms like VK, Telegram, and WhatsApp that were used to advertise the abovementioned services. We could link the ads on underground forums and social networks through the same contact information provided by the sellers. This is contrary to an existing notion that criminals only sell illicit goods in the underground. They also mirror their marketplaces on the surface web.
This is the current state of the cybercrime underground market — well-established with forums packed with offerings and vibrant communities of actors of different maturity levels. Underground marketplaces have evolved and developed structures that mirror legitimate businesses. Sellers have developed detailed business models and monetization systems that accept common means of payment, such as PayPal, Mastercard, Visa, and cryptocurrencies.
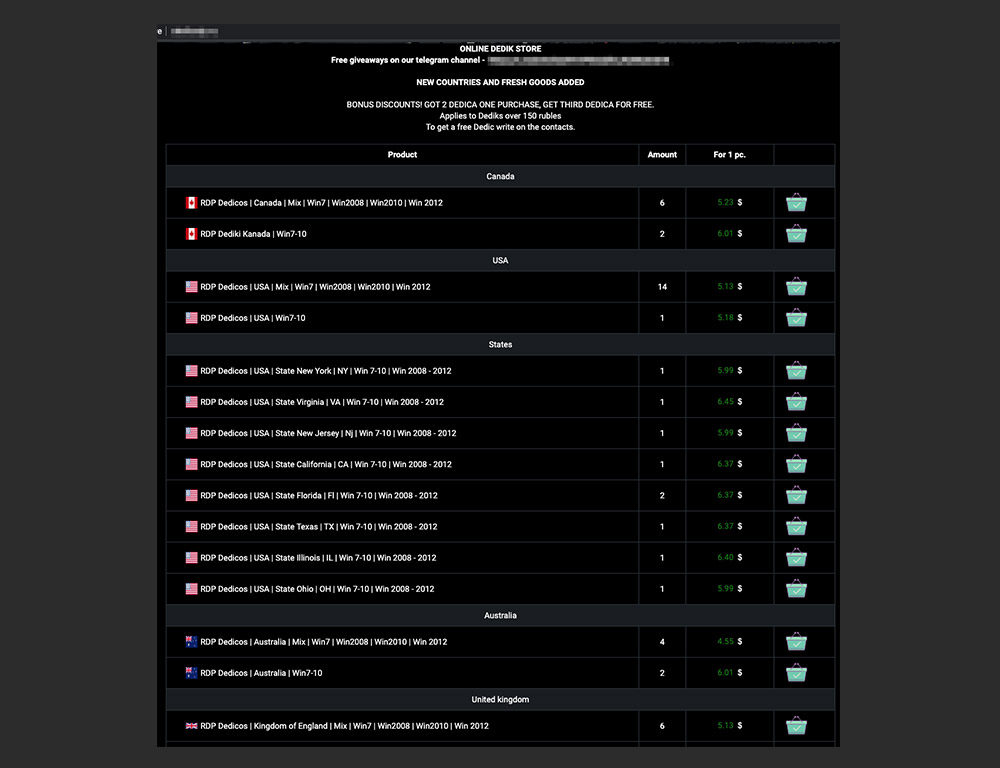
The product slate in the underground is diverse. Aside from the garden variety underground offerings of credit card dumps and skimmers, hacking services abound in dedicated shops, offering dedicated servers, SOCKS proxies, VPNs, and distributed denial-of-service (DDoS) protection.
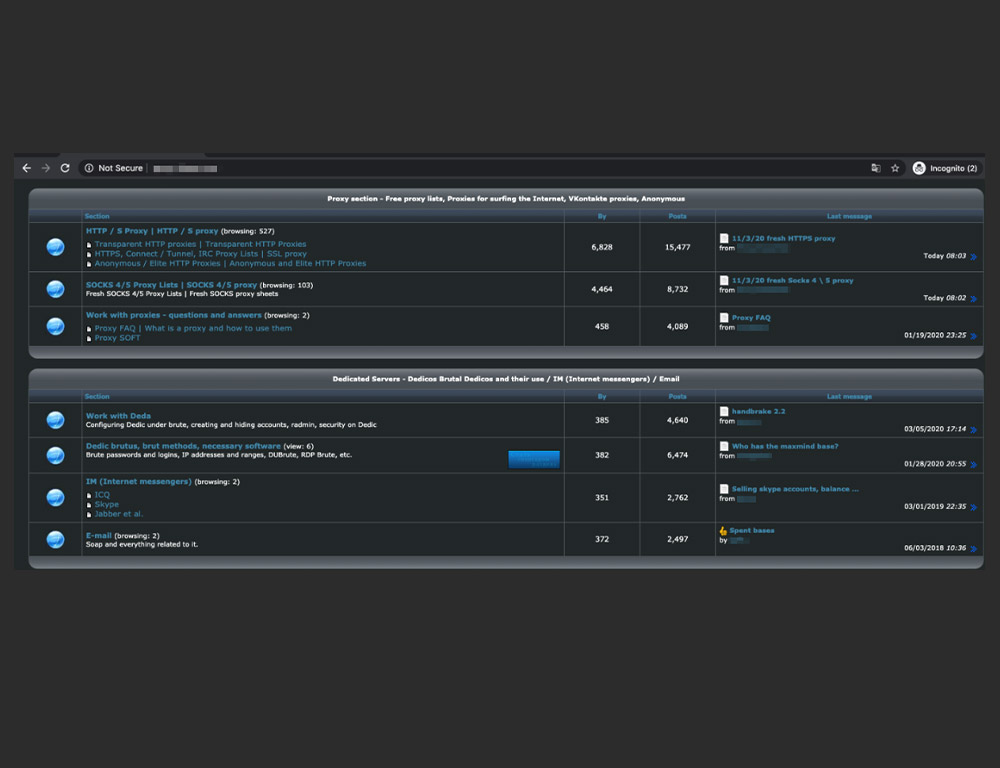
Underground forum sections related to hosting and VPNs
Underground forums could have tens and hundreds of posted topics. A certain forum, for instance, can have over 10,000 topics and 25,000 posts related to proxies and VPNs only. Law enforcement action against forum users is also widely discussed in underground threads.
Services Advertised to Criminal Infrastructure Buyers
We found official resellers of public hosting services to be advertising in underground forums. These hosting providers have legitimate clientele and advertise on the internet. However, several resellers cater to criminals in the underground, either with or without the company’s knowledge. This shouldn’t come as a surprise since criminals may also wish to avail and make use of such services that tout excellent features.
We spotted underground actors sharing reference links from hosting providers and even earning referral money from the community. Hosts are commonly discussed and advertised by criminal actors for their anonymity and abuse-handling (or no-handling for that matter).
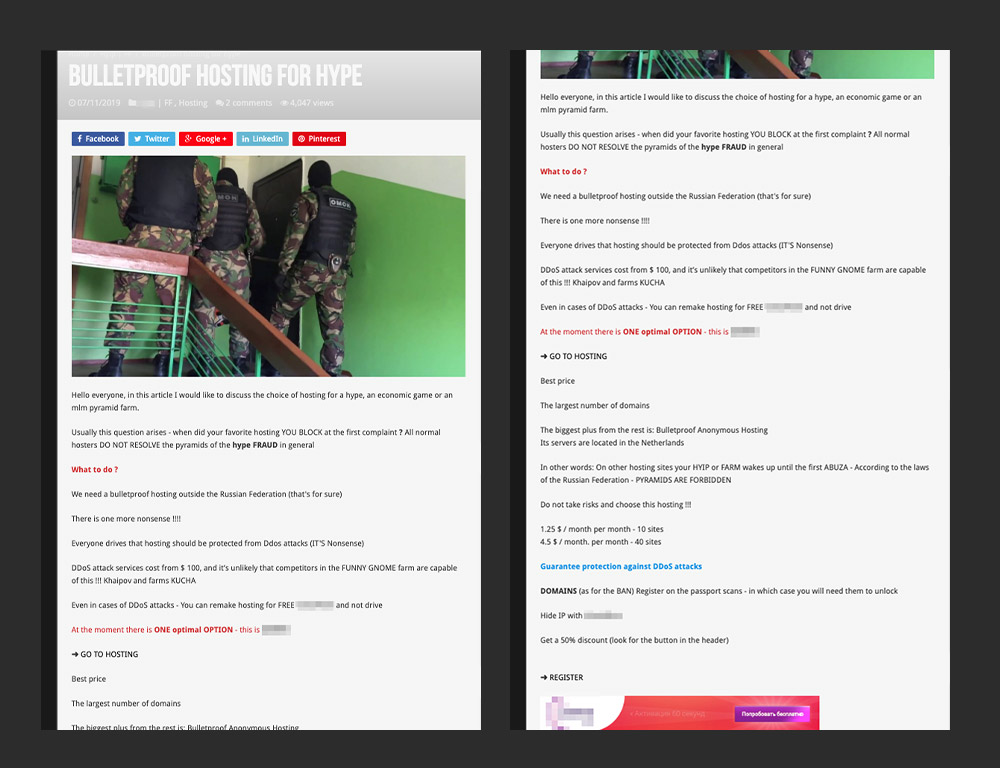
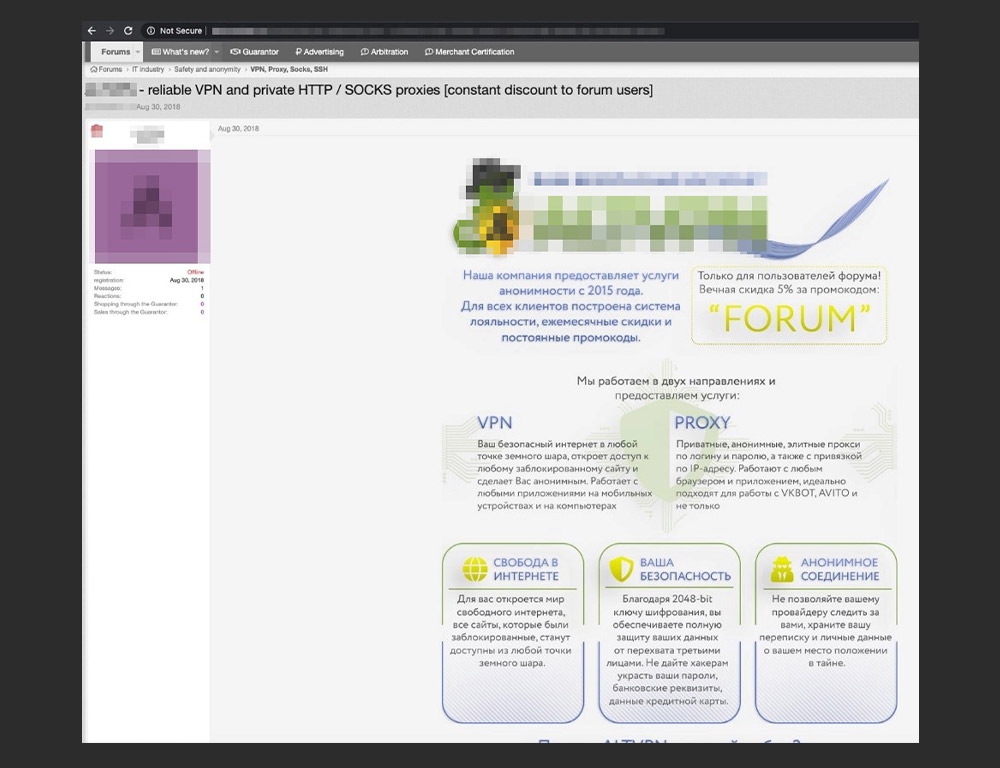
An advertisement for a bulletproof hosting service provider
Unlike regular hosts, providers that are advertised as bulletproof are typically used to host malicious content such as malware repositories, phishing sites, pornography, vulnerability scanners, and spammers. These providers ignore abuse reports and allow cybercrime operations to be orchestrated on their servers. This makes facilitating takedowns even more difficult in countries with lenient cybercrime laws, which may hinder law enforcement investigations.
Social Media Platforms Leveraged by Criminal Sellers and Buyers
Like any business that sells goods and services to potential buyers, criminal sellers also advertise. Sellers use different platforms to promote their products and services: chat channels, hacking forums, and social media posts.
For instance, we found a hosting service advertised on the social network VK. In the underground, it is positioned as suitable to carry out brute-force attacks and run mass internet scans via Masscan, Nmap, and ZMap.
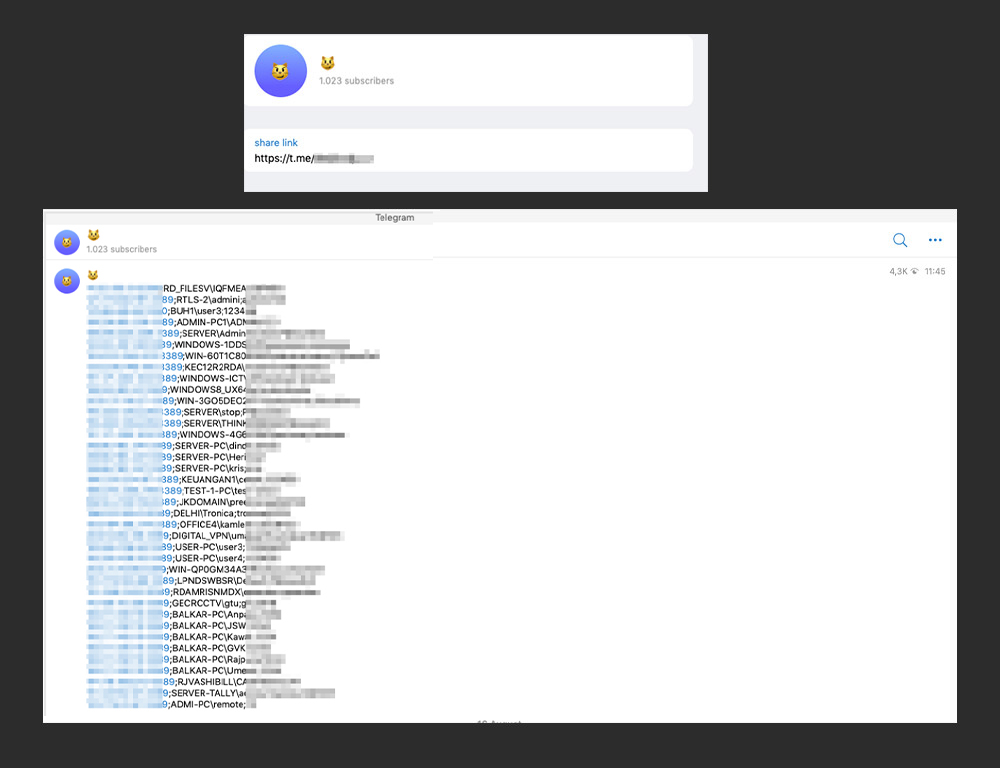
A Telegram channel that shows compromised assets to advertise their services
Telegram, for instance, has become a point of contact for services advertised in underground forums. In some cases, it is used as a platform for advertising services. Dedicated chats and bots are also used to sell servers and other compromised assets such as hosts with RDP access and VPNs.
Better awareness of the underground is crucial in helping organizations, the InfoSec community, and law enforcement to manage and reduce cybercrime. Detailed findings can be read in our full paper, “The Hacker Infrastructure and Underground Hosting: An Overview of the Cybercriminal Market,” which provides insights into the workings of an underground economy and the foundations of online criminal infrastructure.
More underground hosting research:
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One