Surging Tech Support Scams and How to Avoid Them
 Cyber scammers are learning that you can trap more flies with honey than with vinegar. In a widely spreading tech support scam, the scammers shift from the usual scare tactics and instead graciously offer to “help” potential victims. This scam involves convincing victims that their computer has been compromised, before conveniently offering their services to deal with the issue.
Cyber scammers are learning that you can trap more flies with honey than with vinegar. In a widely spreading tech support scam, the scammers shift from the usual scare tactics and instead graciously offer to “help” potential victims. This scam involves convincing victims that their computer has been compromised, before conveniently offering their services to deal with the issue.
Victims of this recent scam find their screens locked, with an ad for a company called “SupportBuddy” on the monitor. The browser is frozen, the keypad is locked, and the victims are pressured into calling the number on the screen. When the victim places a call, SupportBuddy kindly offers to fix the problem for a specific sum. The hackers pose as legitimate tech support from major companies and attempt to get credit card and personal information from the victims.
This form of social engineering is relatively new. The more traditional tech support scams typically use intimidating alerts, with alarming language and an urgent call-to-action. An example would be: “Windows health is critical. Do not restart. Contact us immediately!” This usually goes along with threats of data loss and malware infection, to scare the victim into using their service.
Trend Micro has been monitoring tech support scams since June due to a sudden increase in cases. Most of the URLs encountered display similar blue screen system error alerts, which can only be terminated via task manager. They also provide a hotline number that puts victims in contact with the scammers. These malicious sites have common URL keyword patterns, and some of the infected domains are hosted on IP addresses which are already being monitored.
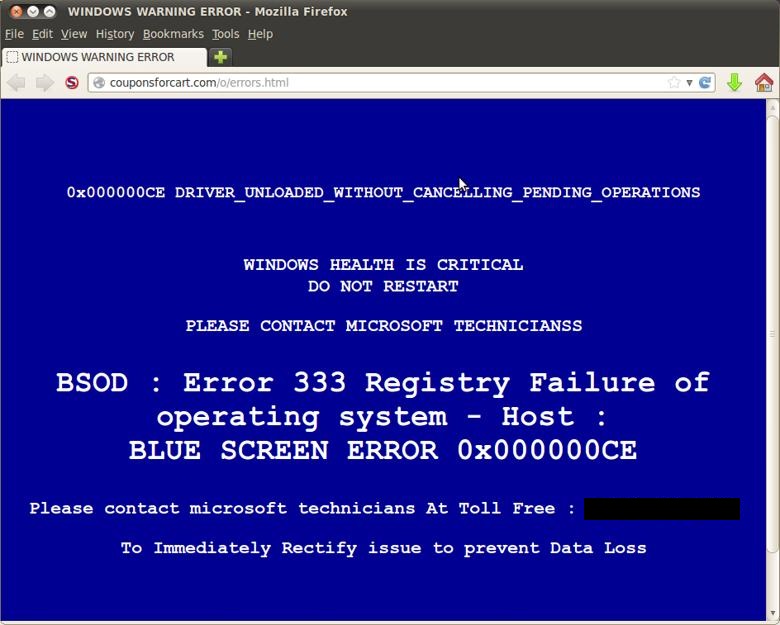 A sample of a fake alert message from an infected site
A sample of a fake alert message from an infected site
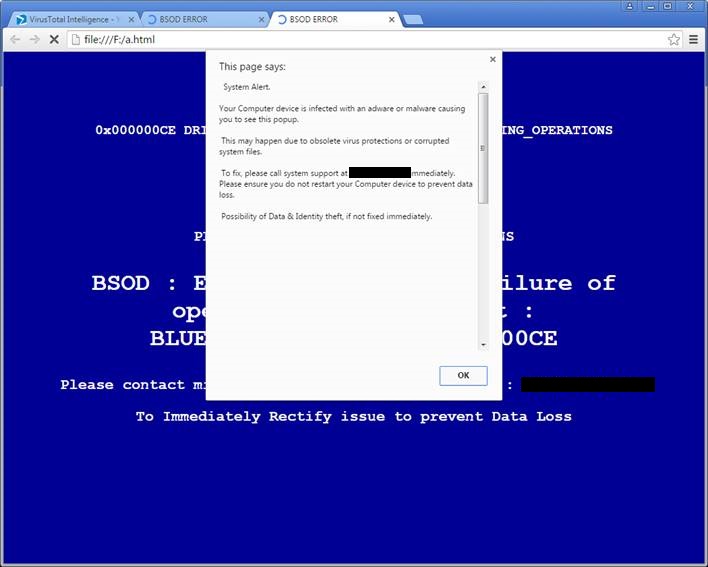
The same site blocked by web protection software
What avenues are used to attack victims?
Despite increasing awareness about internet scams, people still click on unfamiliar sites or ads that expose them to risks. Links lead to malicious sites which employ malware to control a user’s computer. Once they gain control, they freeze the screen to display their message and hotline number. For these most recent tech support scams we detect the pages with fake alerts containing HTML_FAKEALRT.NM.
Scammers also trick users into downloading the malware directly, often naming files after something popular so they have a broader target base. A recent scam uses Hallmark e-cards as bait. Greeting card brand's icon gives a look of legitimacy to the file, but once users download it, their computers are disabled as a window pops up warning users of a “critical failure”. A support number is also provided, which users are urged to call to get a “response code” to unlock their computer. This particular Trojan is detected as TROJ_TECSAM.A. Its only purpose is to trick the user into calling the number for technical support, where they can be manipulated into giving personal information or extorted for money.
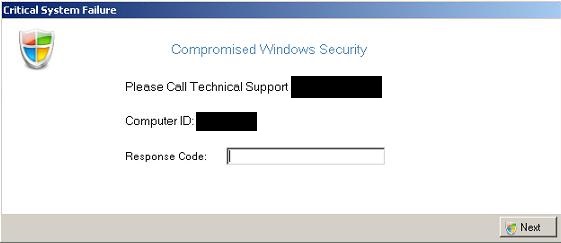 The simple pop-up window from the Trojan TESCAM
The simple pop-up window from the Trojan TESCAM
Another way tech support scams reach users is via Internet Service Providers (ISP). Hackers can employ malicious advertisements to discover a user’s IP addresses, and from there they can find out their ISP. They pose as the victim’s specific ISP tech support and try to get financial information out of them.
Tech support scammers are known to use a variety of tactics to manipulate would-be victims. Here are tips for avoiding them
- The best way to avoid tech scams is to be aware of common attack methods.
- Remember that legitimate tech support won't call you. You have to request help from them. Be suspicious of unsolicited calls. If you need to reach out to tech support, make sure you have the correct number. Go straight to the official website of your provider to get the contact details for their support line.
- If your screen freezes with a malicious ad, don’t panic. You can easily terminate the URL by ending the browser process from your Task Manager. Definitely do not call the hotline that you see on ads or alerts. Contact your IT department if you are in the office.
- If the support agent you’re talking to asks for remote access right away, be cautious. Remote access is usually done by a higher level of the support team, and not the call technician.
- Act fast if you’ve encountered this scam. If you gave away credit card information, contact your bank immediately. Change the passwords on your computer, especially if you gave them remote access.
- Get effective and legitimate anti-virus software to prevent your system from accessing malicious sites. If you already have one, make sure you have the latest version installed. The latest updates of the software will include the most comprehensive protection against recent malicious URLs.
Trend Micro already provides solutions for this problem. Endpoint products such as Trend Micro™ Security, Smart Protection Suites, and Worry-Free Business Security have features that proactively prevents you from clicking on malicious URLs.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One