FBI: BEC Losses in 2017 Shot Up to Over US$675 Million
The Internet Crime Complaint Center (IC3), the Federal Bureau of Investigation’s (FBI) virtual complaint desk for various forms of online fraud and cybercrime, recorded 15,690 business email compromise (BEC)/email account compromise (EAC) reports in 2017. The incidents led to adjusted losses of over US$675 million — a staggering 87 percent increase from 2016’s US$360 million.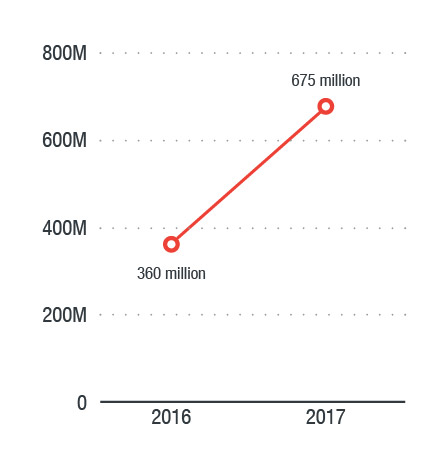
Figure 1. BEC losses grew 87 percent from 2016 to 2017
Having been reported in over one hundred countries now, BEC scams are predicted by Trend Micro to lead to total global losses of over $9 billion this year.1
Scamming tactics
Cybercriminals behind BEC/EAC scams utilize techniques that are associated with their targets’ regular business practices — the most common of which is wire transfer payments. Usually, one or more fraudsters are behind the scams, and legitimate business email accounts are compromised via social engineering or computer intrusion tactics.
Social engineering involves underhanded tactics that are especially deceptive: When a compromised email comes from a legitimate user’s mailbox, there won’t be anything suspicious in the mail header or sender address.
In addition to social engineering, fraudsters also utilize computer intrusion techniques to execute unauthorized fund transfers. These may involve keyloggers and phishing kits, which facilitate credential grabbing to gain access to enterprise webmails. This, however, is more costly for cybercriminals because they need to pay for builders and
Targets in 2017
The IC3 report noted that in 2017, the real estate sector had been highly targeted by BEC/EAC scammers, with many victims reporting losses during real estate transactions. BEC/EAC scams may also be connected to schemes that revolve around lottery winnings, romantic relations, employment opportunities, and rentals or properties. The scams target U.S.-based victims, who are manipulated to illegally transfer money
Cutting-edge technology to combat BEC/EAC schemes
As cybercriminals continue to sharpen their tools to produce lucrative payouts, traditional solutions could find it a challenge to keep up with BEC and EAC scams. More advanced security solutions are necessary to stop BEC and EAC scammers on their tracks.
The use of artificial intelligence (AI) and machine learning in Trend Micro™ email security products enhances overall cyberdefense against BEC, EAC, phishing, and other advanced threats. Trend Micro’s anti-BEC technology combines the knowledge of a security expert with a self-learning mathematical model to identify fake emails by looking at both behavioral factors and the intention of an email.
The new Writing Style DNA can detect email impersonation by using AI to recognize the DNA of a user’s writing style based on past written emails and compares it to suspected forgeries. This feature works best against BEC/EAC schemes that involve compromised legitimate email accounts. When an email is suspected of spoofing a user, the writing style is compared to this trained AI model and a warning is sent to the implied sender, the recipient, and the IT department. The new technology will be used by Trend Micro™ Cloud App Security™ for Microsoft® Office 365™and ScanMail™ Suite for Microsoft® Exchange™ products starting June 2018.
In addition to smart security solutions, workforce cybersecurity awareness can help effectively fill security gaps to prevent BEC/EAC scams from succeeding. Along with advanced security solutions, employee education on how BEC/EAC scams work should also be a top priority for businesses. Help employees become vigilant by sharing best practices against email fraudsters.
For a suspected BEC/EAC incident, report immediately to law enforcement or to the IC3 website.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One