A Practical Guide to Mobile Safety
 When was the last time you left your house without a mobile device?
When was the last time you left your house without a mobile device?
Throughout the day we use these devices to communicate with friends and family, browse favored websites, pay the bills, make purchases, and even work. Our mobile devices have become an essential part of our lives—not just because of the services and tasks they allow us to perform, but also to store data. Valuable contact information, personal photos, emails and files, even our entertainment are all saved on mobile devices. Unfortunately, there are threats that can put all that personal information and valuable data (as well as the information of the people closest to us) at risk.
A closer look at mobile threats
Cybercriminals are continuously looking for ways to exploit vulnerabilities in apps, operating systems, and software, trying to capitalize on security flaws before manufacturers find and patch them. They primarily target user data—from credit card credentials to email passwords and contact lists. Malicious actors also try to trick users into downloading adware or subscribing to paid services.
Cybercriminals use different techniques to mine information. The Marcher Android malware (detected by Trend Micro as ANDROIDOS_FOBUS.AXM) was first discovered in 2013, and has continued to evolve. Initially, this particular malware collected credit card credentials from users of the Google Play Store by overlaying a fake screen on top of the app store’s payment page. An updated version of Marcher improved its theft and fraud capabilities while targeting patrons of nine big UK banks. It intercepts communication between users and the banks’ two-factor authentication system and sends the user’s credentials to its command and control server.
In May, an Android info-miner was reportedly spotted masquerading as a Google Chrome update. The malware was squatting on URLs that mimic legitimate Google update addresses, and when users visited the URLs, they were prompted to install a compromised “update”. Researchers say the malware is capable of collecting stored data, snooping on calls and text messages, and even stealing banking credentials.
Cybercriminals also capitalize on current popular trends. Just last July, many malicious actors used the fervor over Pokémon Go to lure users into downloading repackaged apps, which are apps embedded with unwanted content that masquerade as legitimate. Fans eager to play the game couldn’t wait for it to be available in their regions, so they turned to third-party app stores and unwittingly downloaded compromised versions. Trend Micro researchers observed repackaged Pokémon Go apps for both Android and Apple users on third-party app stores. Some malicious apps were even camouflaged as “Pokémon Go Guides”, which appealed to enthusiasts who wanted gaming tips.
One unsettling development in the mobile threat landscape is the increase in mobile ransomware. Trend Micro researchers noted a staggering 1100% increase in unique samples of detected ransomware, based on data collected from April 2015 until August 2016. The top mobile ransomware family dubbed SLocker (detected by Trend Micro as ANDROIDOS_SLOCKER.AXBP) accounts for 77.92% of detections. It locks the screen of mobile ransomware victims, pretending to be a law enforcement agency (FBI or another agency) and demands a ransom through an online payment service.
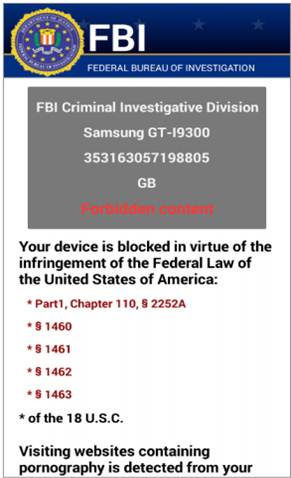
Figure 1. SLocker mobile ransom note
Different malware and ransomware can be distributed using a variety of ways—through third-party app stores, mobile ads, links on social media, spam on email, masquerading as updates, and sometimes even though SMS. Malicious actors cast a wide net, and mobile users should be wary of getting caught in it.
Mobile device safety tips:
- Regularly update the operating system and apps. New vulnerabilities are always discovered, and vendors work to quickly patch their applications and software. For the users, updating is essential for keeping mobile devices as secure as possible.
- Download apps from trusted sources. According to a 2016 Android Security Review by Google, Potentially Harmful Apps (PHA)are still the biggest threat to Android users. Certain third-party app stores have proven to be more likely carriers of malicious apps, so always download from trusted sources. Users should also do their due diligence and check reviews or comments on the app page to make sure it is legitimate.
- Know the risks of rooting. Manufacturers place security restrictions and safeguards on their devices to safeguard users. Rooting removes these limitations, leaving the system more vulnerable to malware and other threats.
- Avoid connecting to unsecured Wi-Fi. Turn off the automatic Wi-Fi connection feature on mobile devices. Public hotspots are not secure, and connecting to them can expose the device to a multitude of risks. If connecting is necessary, avoid logging into key accounts or financial services. Setting up a VPN is also a good way to secure data sent and received online.
- Be wary of unsolicited calls or messages. Attackers use a variety of methods to get users to download malware or reveal personal information. Any messages, calls, or emails from unknown senders should be scanned or well-vetted.
- Back up your files. Protect important data from ransomware threats by regularly backing up files. There are many different ways to store mobile device data—from synching with paired PCs to cloud services or even apps. Efficient programs can automatically back up mobile device data on a set timeline, which is convenient for the user.
And here are good privacy tips that can help protect personal information on mobile devices:
- Set automatic locks on mobile devices. Ensure that the mobile device locks automatically, and has a strong passcode—a simple pattern or swipe password isn’t much of a deterrent. If a device is lost or stolen, a strong password prevents anyone from quickly peeking at personal information.
- Limit the personal information given to apps and websites. When signing up for a new service or downloading a new app, registration often requires personal information. Be wary of revealing too much, and research on how secure the application or site is before logging on.
- Manage what is shared online. Make sure to use privacy settings on social media apps and sites. Some sites can broadcast location, email, phone numbers, or more to the public by default.
- Be aware of the scope of app permissions. Apps sometimes require more than the basic default permissions. Make sure the installed apps only have access to features they need.
Users should also invest in multilayered mobile security solutions that can protect devices against online threats, malicious applications, and even data loss. Trend Micro™ Mobile Security has advanced protection capabilities that can identify known threats and prevent them from damaging mobile devices or compromising data.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One