 Download A Current View of Gaps in Operational Technology Cybersecurity
Download A Current View of Gaps in Operational Technology Cybersecurity
Enterprises and industrial facilities rely on control systems to manage, command, or regulate the devices and the systems that make up their operations. The processes run by industrial control systems (ICSs) not only “keep the lights on” but also facilitate productivity and safety. Everything from temperature and sensory equipment to manufacturing lines and security devices are managed by ICSs.
In the past, these systems were under the purview of engineering departments, so their design and configuration were focused on functionality and process. But after 9/11, governments and enterprises became more concerned about cybersecurity. The management of ICSs moved to IT teams and, consequently, all cybersecurity monitoring and mitigation centered on the IP (Internet Protocol) network layer. ICS security went from being mission assurance to information assurance.
Systems under the engineering department are neither managed nor secured by IT teams. This means that control system devices — such as process sensors, actuators, and drives — that were managed by engineering teams years ago, but are still in use today, do not have capabilities for cybersecurity. They have no means for authentication or cyberlogging, and most cannot be upgraded. This presents a serious problem because the old cliché is true: Security is only as strong as the weakest link. Attackers will try to enter enterprise networks through all possible weak points in security.
Any comprehensive security plan for enterprises and large organizations should include cybersecurity policies for weak links in ICSs. Since they manage many vital aspects of enterprise operations, protecting these control systems will also protect workers, valuable digital assets, and physical property.
The scope and the history of ICS attacks
Trend Micro has been tracking threats to ICS environments since the early 1990s. The following timeline shows some of the most notable attacks from the past decade.


Havex supply-chain malware hits dozens of ICS targets across EU and US

Trisis infects Saudi Arabian petrochemical plant, marking the first known malware to target individual safety instrumented systems (SISs)

Berserk Bear claims to be targeting power and gas providers across Germany

North Korean Lazarus group suspected of malware attack against Indian nuclear power plant

DoppelPaymer launches targeted attacks on organizations in critical industries
Stuxnet worm infects Iranian nuclear plant, damaging 20% of centrifuges

Industries and BlackEnergy infect Ukranian power grid, hundreds of thousands of civilians lose electricity

WannaCry shuts down production in Honda plant, causing delay in output of more than 1,000 vehicles

LockerGaga infects Norsk Hydro network, shutting down production and costing the company over US$75M

Rheinmetall’s automotive division infected with malware, affecting manufacturing; losses estimated at US$4.5M per week


Four zero-day vulnerabilities on USB devices spread through the organization’s network and infected Siemens equipment.

The centrifuges were out of control during operations, causing physical damage.

Malicious actors accessed the office network through an APT attack, and then obtained privilege of control over the production system.

The steel mill shut down unusually, causing massive physical damage.
Japan's Monju Nuclear Power Plant attack

Malware was loaded onto vulnerable patch software.

More than 42,000 emails and personal training reports were leaked.

Malicious actors used spear-phishing emails with BlackEnergy 3 malware and gained employee login access.

They modified the system password and used a denial-of-service (DoS) attack on telephone lines, which meant systems could not be operated by employees. Around 220,000 people experienced blackouts.

Trisis malware attacked factory safety instrumented systems (SISs).

Plant operations were tripped up.

Ransomware attacked Taiwan Semiconductor Manufacturing Company (TSMC).

The company lost US$255M in downtime and 10,000 machines were affected.

Ransomware targeted the manufacturing company Visser Precision.

Files were encrypted and data exfiltrated.
A timeline of industrial cyberattacks and their impact
Trend Micro researchers also put a smart manufacturing honeypot, designed as a small business, online in May 2019 and left it operating for 7 months. The first attack came just a month after the honeypot went live. The longer the honeypot was exposed, the greater and more sophisticated the malicious activity that the researchers observed. This showed that a business with critical clients and inadequate security was a ripe target for attackers.
A map of ICS attack vectors
To fully understand the threats that target ICS environments, it is important to determine the possible attack vectors.
First, there are the devices that do not have any cybersecurity elements. Modern technologies improve productivity through these reliable, accurate, and secure sensors, controls, and actuators. But as mentioned, they are missing a key factor: cybersecurity. As a result, attackers could use these small and unsecured devices as entry points into an enterprise network.
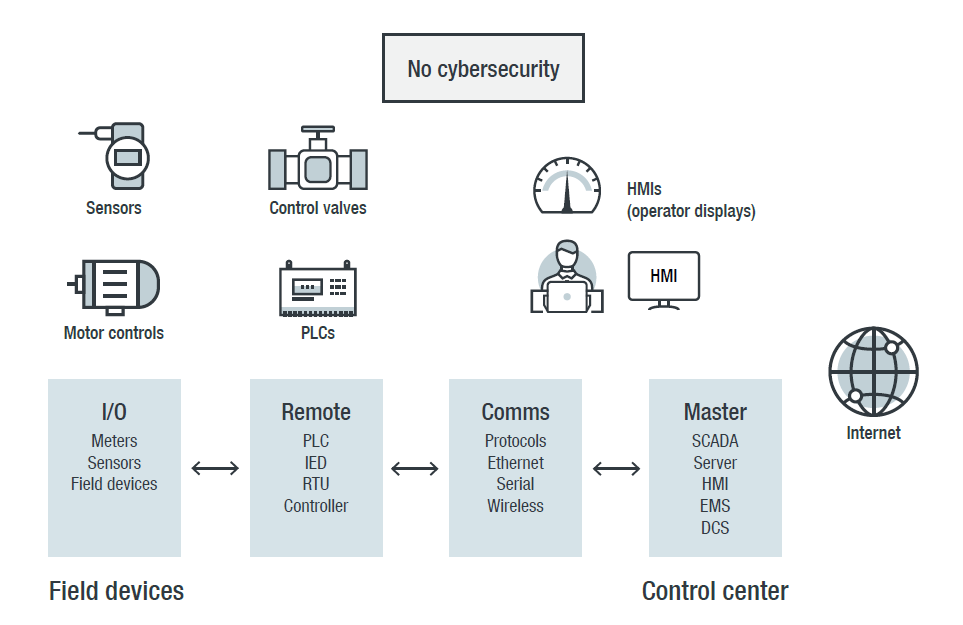
In some cases, attackers could compromise the operational technology (OT) network from the IT environment. (OT directly monitors or controls industrial equipment or processes, and ICSs are a subset of this group.) Examples include attacks on servers using malicious software, web application attacks on human-machine interfaces (HMIs), and communication protocol attacks that compromise traffic from the network router.
A typical organization’s OT and control system environment
In other cases, the attacks could come from physical attacks on the field network devices or software attacks injecting malware into the system during patches or firmware or software updates.
These cases emphasize the need for enterprises to have a thorough understanding of the threats they could face — or are already facing. There are any number of potential attackers who target ICS environments, and there are also relatively easy attacks that could be launched on OT networks.

ICS attack vectors
A security strategy for ICS environments
Addressing weak points in ICS security is not an easy task. Enterprises need to contend with outdated design aspects, security concerns in third-party applications, and many other issues. These are but a few of the challenges they need to overcome:
- Unknown devices and connections to the OT network
- Lack of security in the original design
- Vulnerable and unsecure third-party applications and operating systems
- Legacy systems and environments that may be hard to secure
Reducing cyber risk in an ICS environment also requires a significant understanding of the network environment, including the sensors, the process controls, the protocols, and the communication. Security planners should also have a clear view of cyberthreats and attack vectors in the environment.
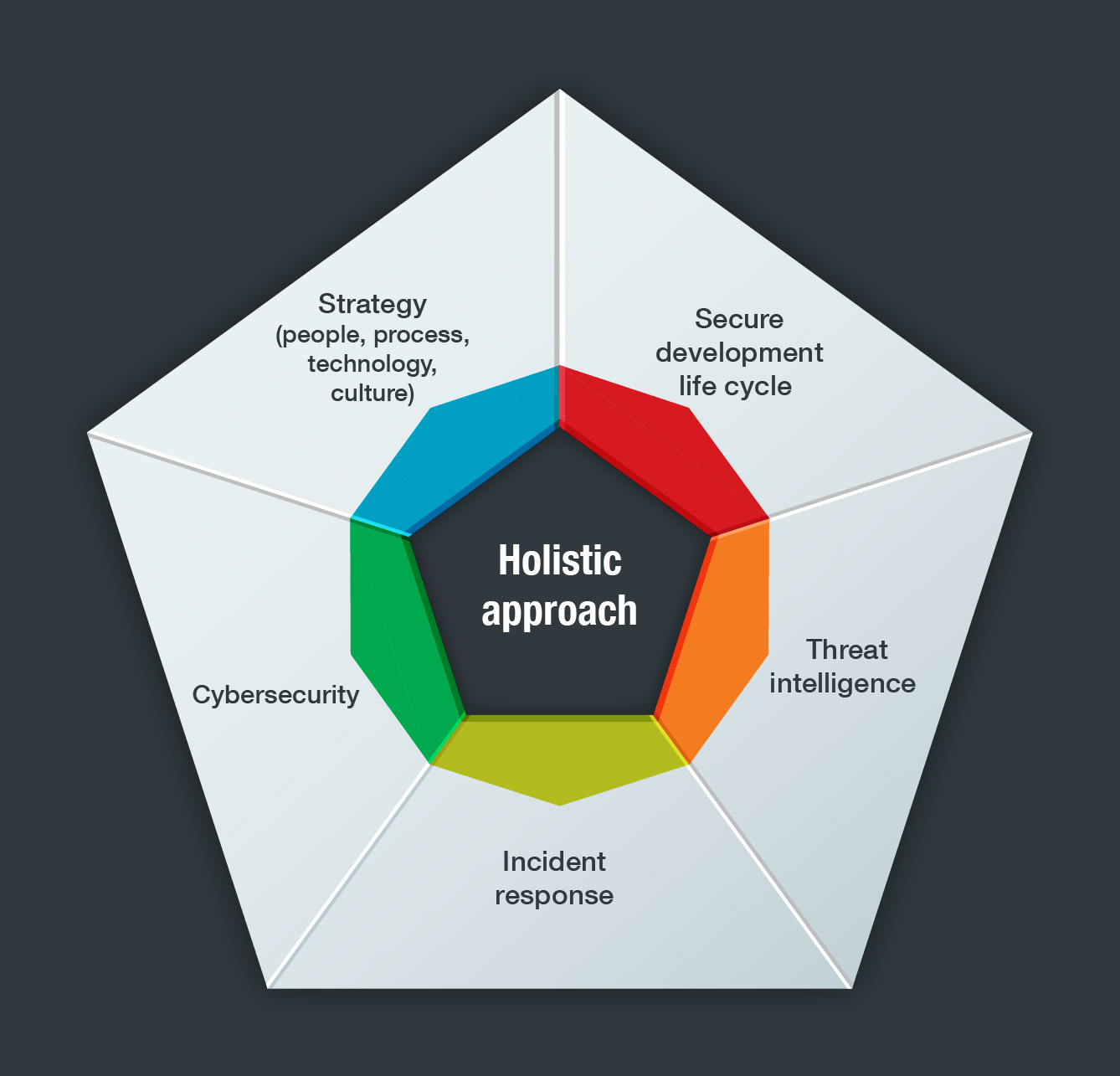
Cyber risk in ICS environments affects a great many industries, including power, oil and gas, manufacturing, pharmaceuticals, healthcare, and transportation. Because of the potential impact a cyberattack might have on critical industries and business in general, it is recommended that every organization implement a comprehensive cybersecurity strategy. A good place to start is with industry standards. Depending on what type of business is operating, there are different standards that can be enforced by governing bodies. Next, enterprises should implement a cybersecurity framework in line with the goals and the objectives of the organization. This can be done by creating a cohesive plan that works across four pillars: people, process, technology, and culture.
PEOPLE
PEOPLE
- Staff training and awareness on security
- Professional skills and qualifications
- Competent resources
PROCESS
PROCESS
- Governance, policy, and framework
- Management system
- Best practices
- IT/OT audit

TECHNOLOGY
TECHNOLOGY
- Testing, verification, and validation of technologies
- Competent people, support processes, and an overall plan for technology deployment
CULTURE
CULTURE
- Creation of a cyber culture within the organization for reduction of cyber risk
- Fostering of the cyber culture starting at the top and down to all levels of the organization
The four pillars of an effective ICS cybersecurity strategy
There are also basic activities that an organization can carry out to reduce cyber risk. These include strengthening account credentials, disabling unused physical and network service ports, encrypting system configuration files, and limiting the IP and media access control (MAC) addresses that can access the network.
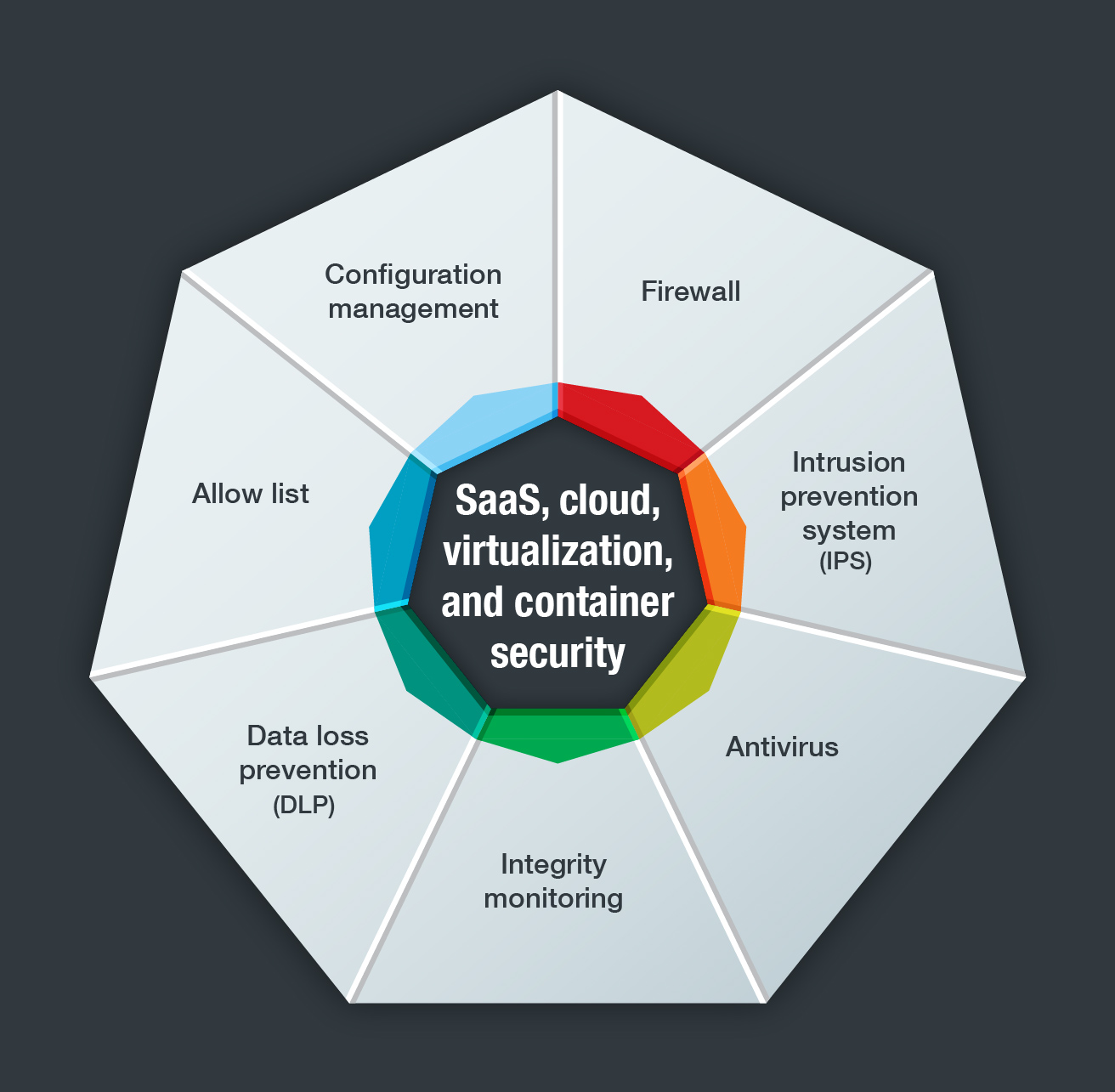
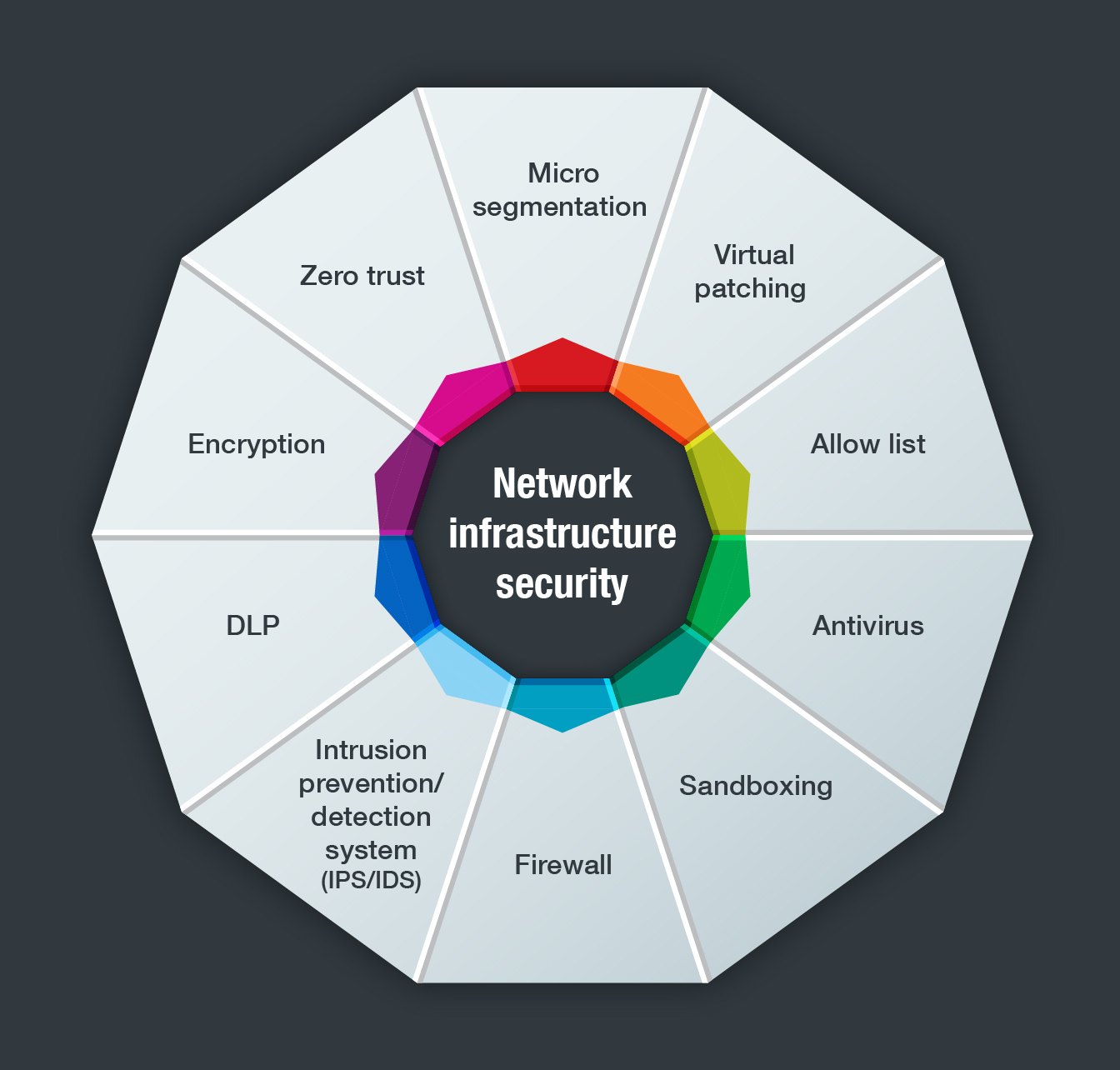
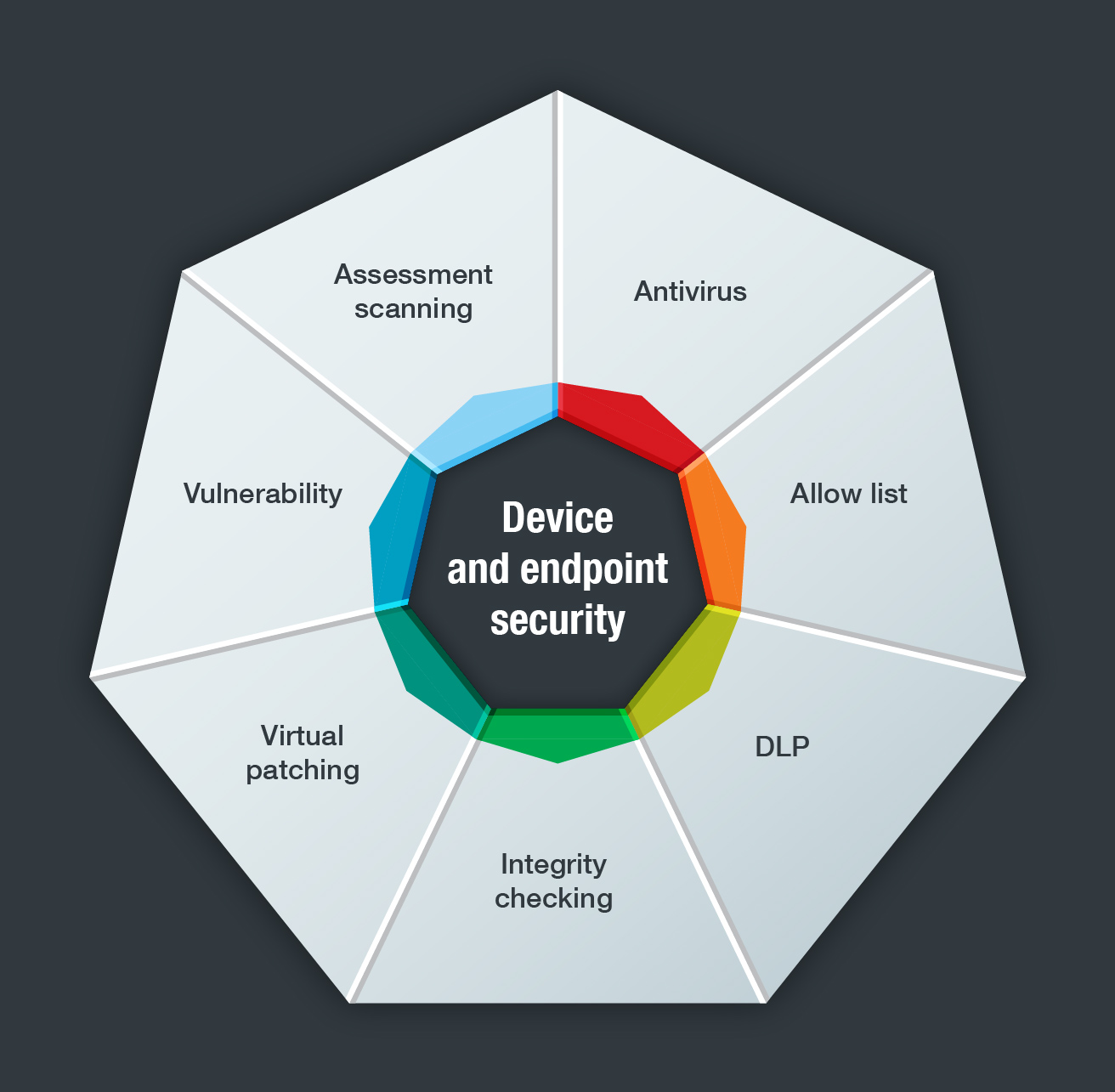
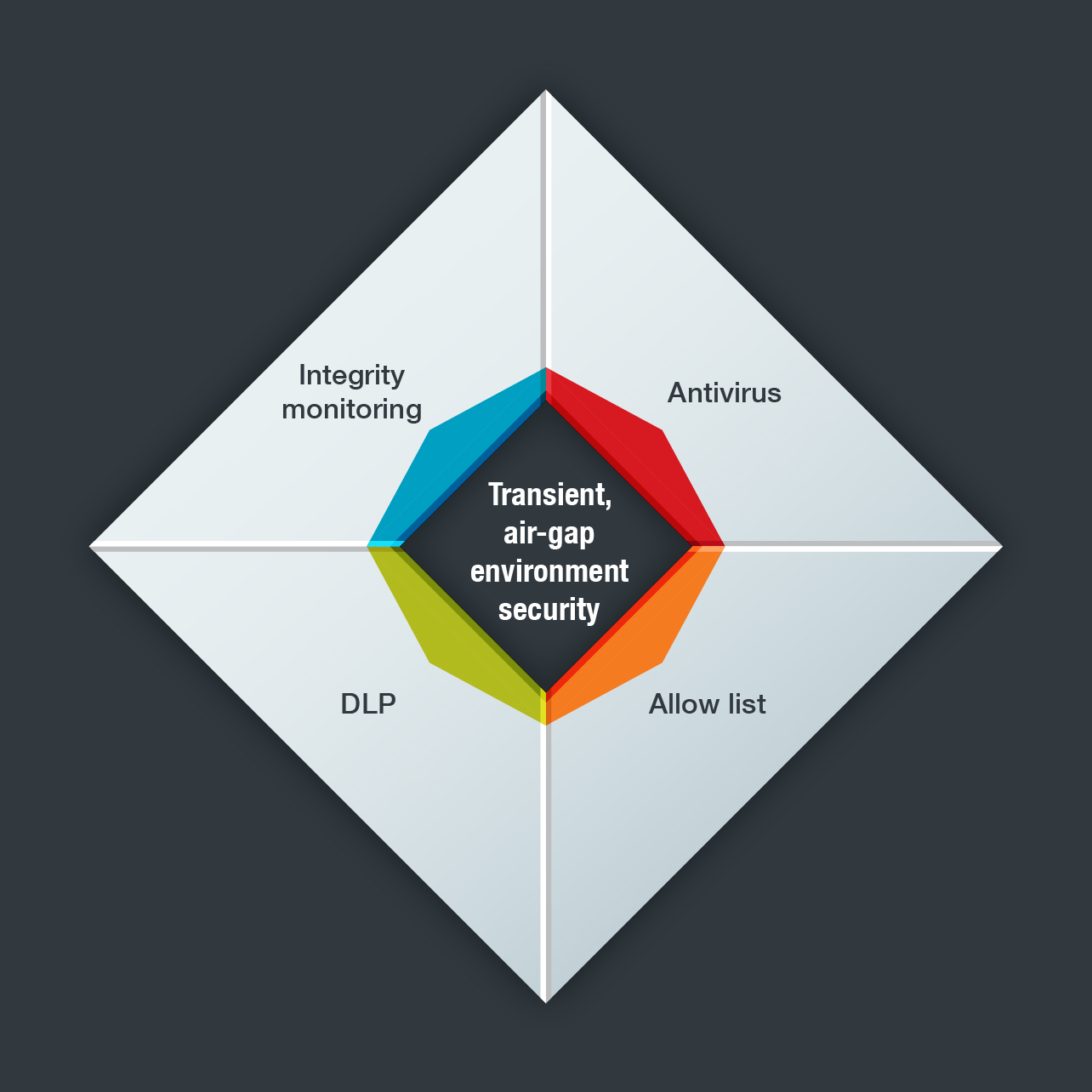
Enterprises also need in-depth protection for ICS environments. This type of security needs to include the following key components:
There is a critical need for enterprises to deploy cybersecurity measures for the protection of ICS environments. Of course, when implementing new tools and policies, there are necessary precautions. All network tools used with control systems should be adequately tested offline before they are employed in real-time OT networks. And the appropriate technologies for ICS environments should be tested in an integrated manner offline, and then online. These technologies include the suite of OT cybersecurity technologies developed by Trend Micro and TxOne Networks.
Dangerous incidents could stem from something as small as an unprotected sensor. Enterprises and industrial facilities, especially those that carry valuable company assets and house thousands of workers, should regularly update and upgrade their security to keep up with constantly evolving threats. A comprehensive security plan that covers all levels of an ICS environment can help keep enterprise assets and staff safe and sound.
Our paper, “A Current View of Gaps in Operational Technology Security,” provides more insights into addressing weak points and reducing cyber risk in ICS environments.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One