New Bait Used in Instagram Profile Hacking Scheme
Insights and analysis by Jindrich Karasek
Last year, we observed attacks launched to steal high-profile Instagram accounts. Now, attacks of a similar nature are on the rise again, this time using new lures to achieve the same goal. Both strikes involve a group of Turkish-speaking hackers who seized Instagram accounts through credential phishing emails posing as legitimate messages from Instagram.
The group exploited their usual targets of celebrities, startup business owners, and other entities that have a sizeable following on a social media platform. Previously, we examined the case of a hacked photographer. This time, the new techniques have been unveiled through the case of a police officer with more than 16,000 followers.
Aside from their use as personal social media accounts, Instagram pages serve as marketing tools for influencers and businesses. Instagram accounts with a large following are then indicative of credibility and clout. In turn, such accounts become an attractive target for threat actors who can use these for different nefarious purposes, such as blackmailing the hacked parties, propagating scams, or simply showing off their capability as hackers.
Same techniques, different baits
Both the previous scheme and the current one rely on a common strategy: harvesting credentials and using these to abuse Instagram’s account recovery process to take control of accounts.
The past campaigns used emails requesting the user to confirm their account so that they can receive a verified badge. However, selecting the “Verify Account” button leads to a phishing page that harvests the user’s email address, credentials, and date of birth. Upon harvesting these, the threat actors have all the details they need to modify the information for recovering a stolen account.
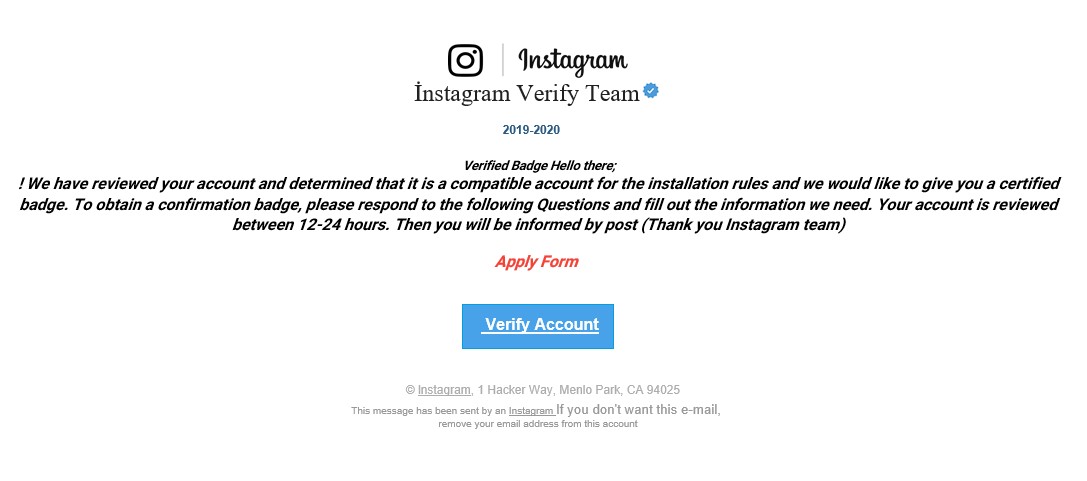
Figure 1. Sample phishing email from the campaign we spotted last year
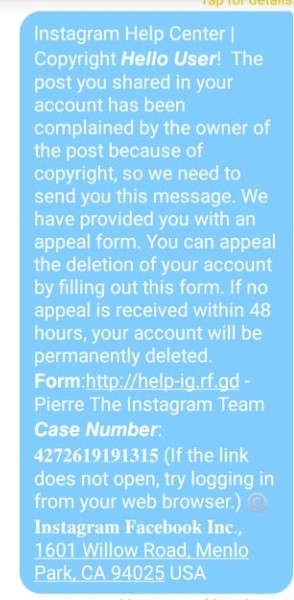
In the new scheme, the message is sent not via email, but through a direct message on Instagram’s platform itself. The message, supposedly sent from Instagram Help Center, claims that a copyright violation complaint has been filed against the account owner whose account, as a result, is now at risk of being deleted. The message also provides a link which masquerades as a form for sending an appeal but which is actually a phishing link.
Opening the link leads to a page where the user will be requested to provide their username. As of writing, the form has no data validation, meaning that any input — even a non-existent account or no input at all — would be accepted.
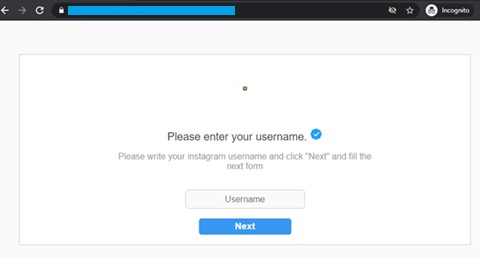
Figure 3. Phishing link requesting for the user’s Instagram username
Once the user selects the “Next” button, another screen appears, this time asking for more information such as known name, password, email, and email password.

Figure 4. Phishing link requesting for Instagram account and email credentials
After the user selects the “Continue as (username)” button, the page redirects to the legitimateInstagram login page. If the user was already logged in to the social media site before tapping the said button, the form then redirects to their homepage. This gives the illusion that the form they filled out is officially connected to Instagram.
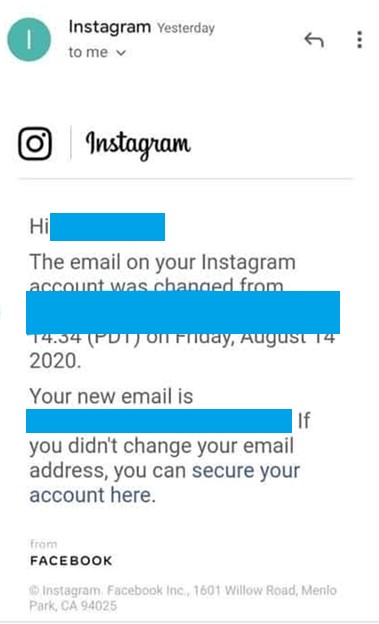
At this point, the hacker can commence taking over the account. The credentials harvested from the phishing link will now be used to change the email linked to the account. The original user will receive an email informing them that the email address linked to their Instagram account has been changed. However, since the hackers already have a hold of the user’s email credentials, they can also take control of the original owner’s email.
Figure 5. An email informing the user that the email linked to their Instagram account has been changed
The hackers will also unlink the original account owner’s cellphone number to the account.
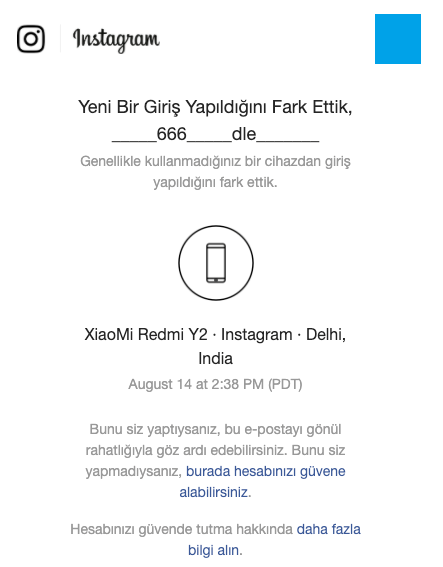
Figure 6. A notification (in Turkish) informing the original account owner of a login from a different device
Refusing the bait of credential phishing attacks
Cybercriminals never seem to run out of novel strategies while still making the most of tried-and-tested ones to enable their credential phishing schemes. However, enterprises and users can avoid being lured by hackers by following these simple steps:
- Be cautious of seemingly legitimate sites that request account credentials for another site (e.g., the fake Instagram site requesting email credentials). This behavior is usually seen in phishing sites.
- Set up two-factor authentication (2FA). This adds another layer of security by ensuring that hackers don’t gain access to an account even if they have the password.
- Never open links or download attachments from suspicious sources. Hover over a URL to check if it reveals a different address other than the expected website.
- Examine message content for ungrammatical constructions and spelling mistakes. Emails or other forms of messages from legitimate companies are often meticulously proofread.
- Inspect the emails used to send messages. They might be entirely different accounts or a spoofed copy of a company’s legitimate email addresses.
- Be wary of messages requesting personal information and credentials. When in doubt, contact the company through other means to confirm if the message indeed came from them.
Here are our recommended security solutions for combatting phishing attacks:
- Trend Micro™ Cloud App Security – Uses computer vision to find credential-stealing phishing sites and threat intelligence to find and block malicious URLs hidden in the message body and attachments.
- Trend Micro™ Worry-Free™ Services – Detects and blocks email threats such as credential phishing from reaching the network. It also employs machine learning with other detection techniques.
Indicators of Compromise
IP address
- 87[.]236[.]16[.]235
URL
- hxxps://www.verified-instagramsupport[.]ml/business/contact/
Other URLs linked to the IP address can be viewed in the appendix.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
HttpContext.GetGlobalResourceObject("ES","RecentPosts")%>
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One