Millions Affected in Anthem Breach, Healthcare Companies Prime Attack Targets

Tens of millions of current and former customers and employees of Anthem Inc., the second largest health insurance provider in the United States, are reportedly affected by a targeted attack. The said attack may have started in April 2014, and used custom backdoors to amass personal information from within the company's network.
As a result, the names, birthdays, member IDs, social security numbers, addresses, phone numbers, email addresses, and employment information of the victims were compromised and likely stolen via unauthorized access.
"Based on what we know now, there is no evidence that credit card or medical information, such as claims, test results or diagnostic codes were targeted or compromised," says Joseph R. Swedish, President and CEO of Anthem, Inc. in a message to its customers and employees.
[Read: What You Need to Know About the Anthem Data Breach ]
Healthcare Companies, Prime Attack Targets
According to the Identity Theft Resource Center (ITRC), four out of ten (42.5%) breaches that occurred from 2005 to 2014 affected the medical or healthcare industry. Coupled with the massive impact of the Anthem breach, this statistic further highlights one crucial fact—medical information is valuable to attackers.
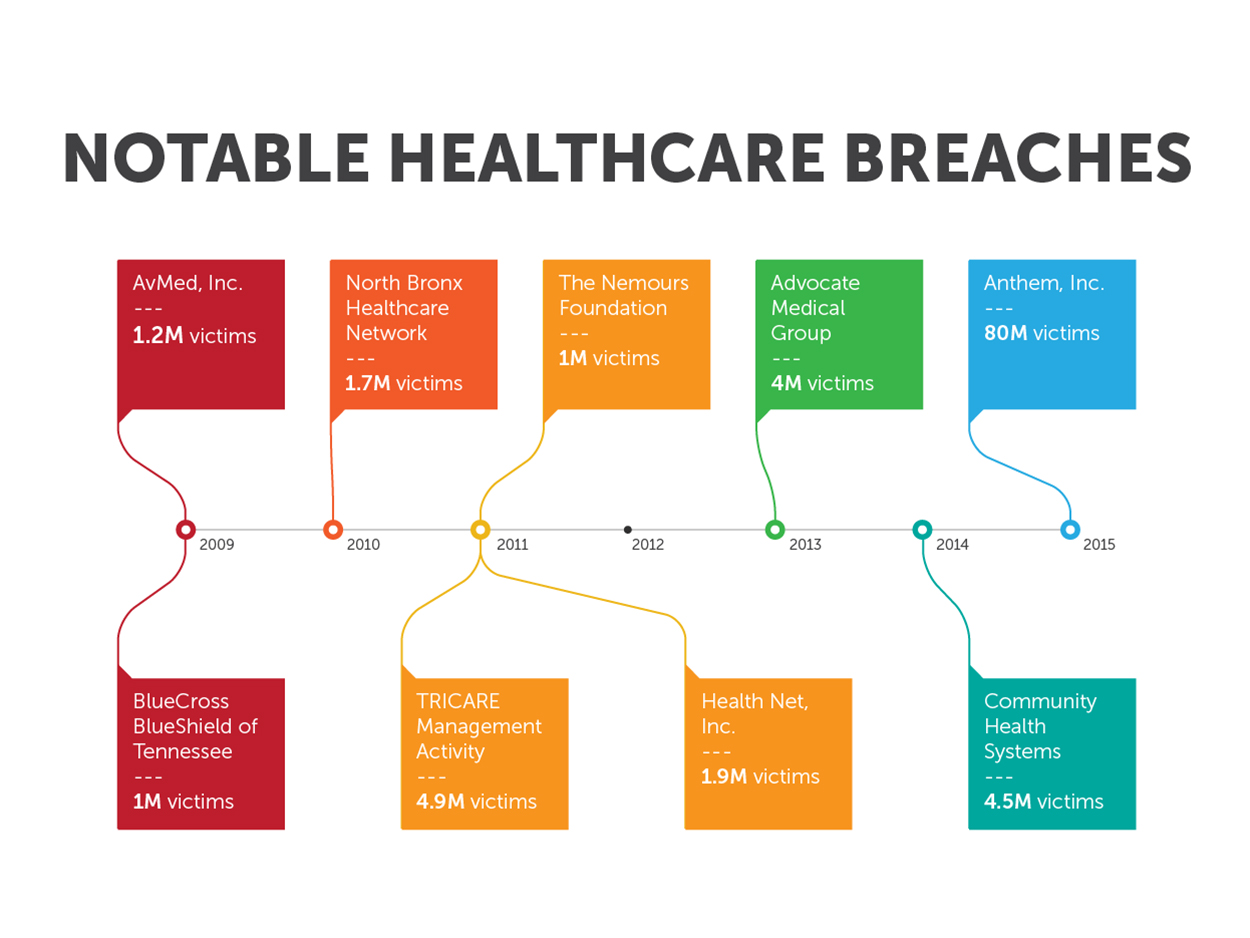
The following timeline shows notable breaches in the healthcare industry:
“Even as we write, the odds are good that the networks of other healthcare organizations have already been breached and that data is being siphoned. The real question is how long it will be before we hear about it,” notes Christopher Budd, threats communications manager at Trend Micro.
[ Read: Healthcare Data in the Cross-Hairs ]
Medical information can be used in a number of malicious activities, like identity theft and reputation damage. Days after the Anthem breach was made public, phishing scams were already found targeting possible victims of the breach.
Apart from private health details, patient profiles kept by healthcare companies may also include a patient’s financial information, like credit card numbers.
Backdoor Use in Targeted Attacks
The specifics of how the backdoors were used in the Anthem breach still aren't clear. Breached organizations rarely release technical information about the attacks. Note that backdoor programs are Trojans "specifically designed to allow malicious users to remotely manipulate affected systems," as defined in the Trend Micro threat encyclopedia.
Backdoors are notorious enablers when it comes to targeted attacks. After looking into the ways attackers use backdoors, researchers have established eight notable techniques: communication with ports, bypassing firewalls, checking for available connections, abusing social media sites, abusing common web services, changing protocols, using custom DNS lookup, and reusing ports.
[Read: 8 Backdoor Techniques Attackers Use to Steal Company Data ]
How to Secure Healthcare Information
Most healthcare breaches result from theft or loss, often from unsecured, unencrypted missing laptops or other devices that contain electronic protected health information (ePHI). At first glance, encryption may seem like a guaranteed solution against attacks; however, arguments exist on why even the strongest encryption may not be enough. This is especially true with sophisticated attackers who aim to steal login credentials and gain privileged access to otherwise encrypted or protected data.
Lack of encryption is not the only problem when it comes to securing healthcare information. Securing healthcare information involves several things: protecting patient portals, proactively preparing against data loss, detecting breaches, auditing for compliance, safeguarding medical devices, and securing legacy systems, and watching out for all possible endpoints that may be attacked. Making sure that all these factors are covered can be a challenge, but it is necessary when considering what's at stake.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
HttpContext.GetGlobalResourceObject("ES","RecentPosts")%>
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One