Defray Ransomware Sets Sights on Healthcare and Other Industries
 Widespread ransomware attacks are becoming more common, but while the usual “spray and pray” methods allow ransomware to affect the most number of victims possible, other strategies are more discriminatory.
Widespread ransomware attacks are becoming more common, but while the usual “spray and pray” methods allow ransomware to affect the most number of victims possible, other strategies are more discriminatory.
The newly discovered Defray (detected by Trend Micro as RANSOM_DEFRAY.A and RANSOM_DEFRAY.B) ransomware employs a more targeted approach. Reports say that Defray distributors are pursuing healthcare, education, manufacturing, and technology organizations using a tailored social engineering strategy. These industries, healthcare specifically, have always been particular favorites of ransomware authors.
Defray behavior and demands
As with most ransomware, Defray is spread through phishing emails which try and coerce victims into downloading a malicious file. The proliferation of ransomware through email is well-documented. A 2016 report by Trend Micro found that email was the most common entry point, with 79% of ransomware detected coming from spam mail.
Luckily, the Defray attacks have been relatively small, and so far only minor campaigns have been tracked. The phishing emails the authors use are well-crafted—for an attack targeting a hospital, the phishing email was from a “hospital IT manager” and the malicious files were disguised as patient reports. In other emails, the attackers masqueraded as a UK-based aquarium company asking for a quote or order, and the malicious file had an “official” logo attached. The specificity and detail show a definite effort to convince targets of their legitimacy, and the more tailored lures show the attackers are investing in more specific targets.
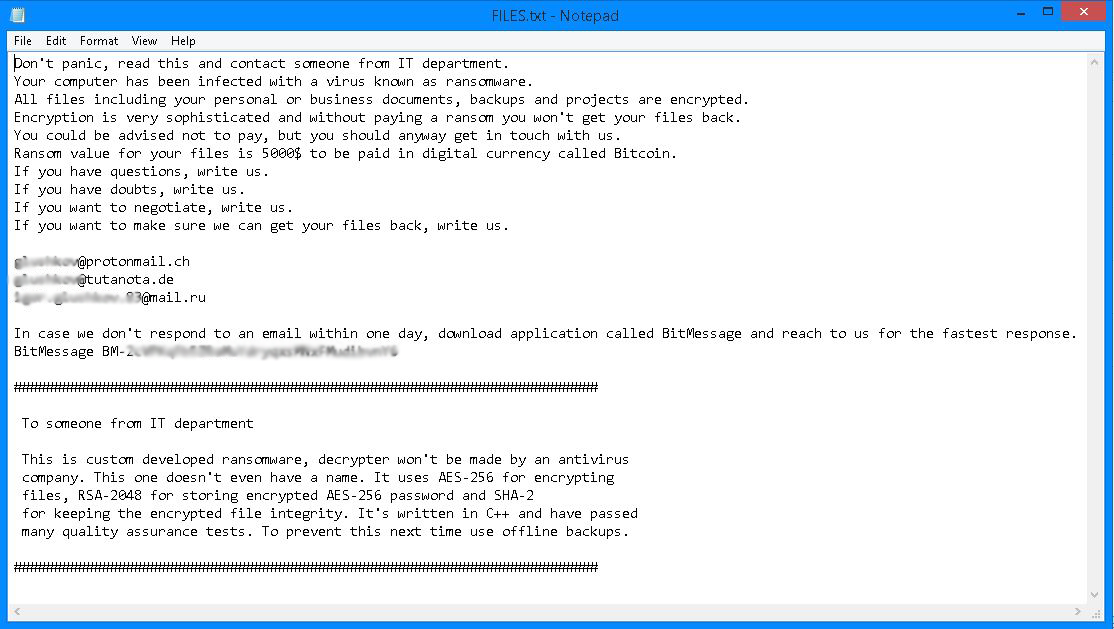
Figure 1. Defray ransom note includes a specific message for IT department
Despite cosmetic changes to the name, the malicious file is the same. Attackers used a Word document with an embedded OLE packager object. If the victim clicks on the OLE file, the ransomware (camouflaged as a taskmgr.exe or explorer.exe file) is installed. The ransom note that follows asks for US$5,000 in bitcoin and also includes three email addresses for contacting the developers. The note actually encourages victims to email them, and even negotiate payment. The authors also provide an alternative communication channel—BitMessage—in case email takes too long. Reports confirm that after encrypting files, Defray will track programs that might interfere with its purpose—task manager or web browsers will be shut down with a GUI.
Solutions and recommendations
Ransomware authors are becoming smarter with their attacks, and as security professionals become more aware of new tricks and techniques they can better defend their organizations and enterprises. There are ransomware best practices that every IT/system administrator should implement, as well as effective multilayered security solutions that can help protect against this threat.
Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. And as we see more advanced malware evade traditional security, Trend Micro Deep Discovery™ Analyzer leverages cross-generational techniques, including Custom Sandbox Analysis, to detect targeted ransomware. At the endpoint level, Trend Micro™ Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat.
Trend Micro™ Deep Security™ and Vulnerability Protection provide virtual patching that protects endpoints from threats that abuses vulnerabilities.
Deep Security™ provides protection via the following DPI rule:
- 1008572-Ransomware Defray
For TippingPoint the applicable rule is:
- 29521: HTTPS: Defray Ransomware Data Exfiltration
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
HttpContext.GetGlobalResourceObject("ES","RecentPosts")%>
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One