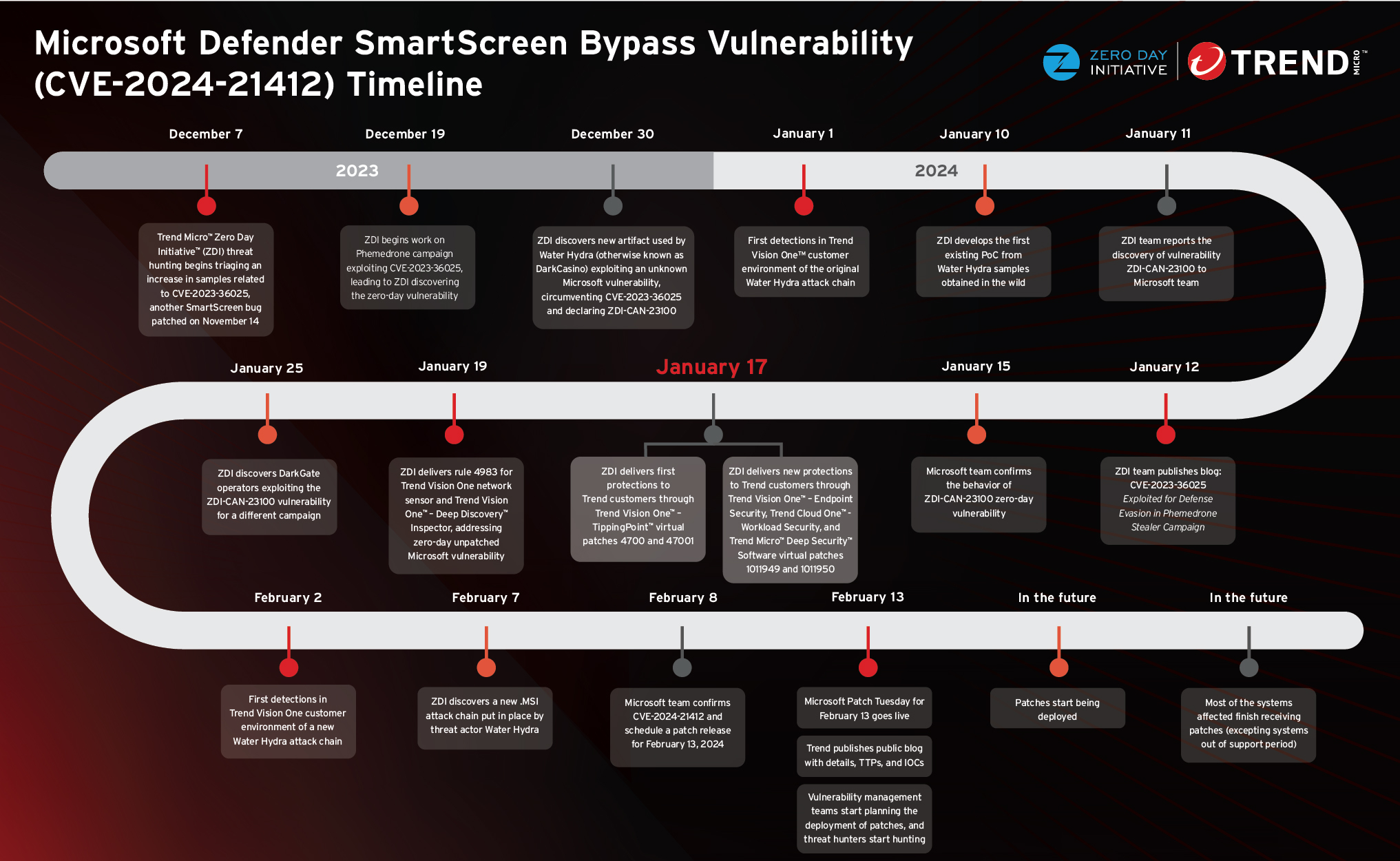
On Feb. 13, 2024, Microsoft issued a patch for CVE-2024-21412, a Microsoft Defender SmartScreen vulnerability revolving around internet shortcuts. Previously, we discovered that an advanced persistent threat (APT) group we track under the name Water Hydra has been exploiting CVE-2024-21412 in a sophisticated campaign targeting financial market traders, allowing the group to bypass Microsoft Defender SmartScreen and infect its victims with the DarkMe remote access trojan (RAT).
Threat actors are constantly finding new ways of identifying and exploiting gaps to bypass security measures. We found that the bypass of CVE-2023-36025 (a previously patched SmartScreen vulnerability) led to the discovery and exploitation of CVE-2024-21412. This highlights how threat actors can circumvent patches by identifying new vectors of attack around a patched software component.
It is important that organizations are able to identify and mitigate vulnerabilities, especially zero-days, in a timely manner to safeguard customers, employees, and systems from attacks that exploit vulnerabilities, thereby minimizing the damage caused by incidents and enhancing overall security resilience.
For over three decades, Trend Micro has been at the forefront of safeguarding enterprises from malicious cyber activities, thwarting both zero-day exploits and N-day vulnerabilities at the earliest stages. Through the support of the Trend Micro™ Zero Day Initiative™ (ZDI), Trend boasts one of the most substantial vulnerability research organizations worldwide. We harness this expertise to fortify our customers against potential exploits, showcasing our commitment to proactive cybersecurity measures.
This entry aims to provide additional context to CVE-2024-21412, how it can be used by threat actors, and how Trend protects customers from this specific vulnerability. It highlights the importance of proactive research in anticipating and defending systems against potential threats, as well as how a dedicated bug bounty program and dedicated vulnerability researchers, both in-house and external, help Trend identify new bugs. This synergistic relationship allows Trend to gain early access to new vulnerabilities and provide customers protections, in many cases prior to the vendor public patch.
Water Hydra’s exploitation of CVE-2024-21412
The Water Hydra APT group (also known as DarkCasino) initially garnered attention in 2021 when it launched a series of campaigns targeting the financial sector by using social engineering in financial trading forums to lure victims. The threat actor engaged in targeted attacks against banks, cryptocurrency platforms, foreign exchange and stock trading platforms, and gambling sites across the globe.
Water Hydra exploits CVE-2024-21412 as a means to gain initial access to victims. This allows the threat actor to perform lateral movement and the later stages of an attack.
The group has shown considerable technical expertise and sophistication, combined with an ability to exploit undisclosed zero-day vulnerabilities for attacks. The threat actor has been using the DarkMe malware, which it uses to gather information from victims, since at least 2022.
As part of our on-going threat hunting process, we discovered that a second group was exploiting the bug in the wild. This highlights that in many cases, it can be difficult to identify how widespread a zero-day vulnerability is being used by threat actors in the wild since it is unknown to the vendor and the public at large. It also highlights the importance of proactive threat hunting for research teams within a security vendor. We will provide more information on this in a future entry.
How attackers can exploit CVE-2024-21412
In Water Hydra’s case, the group used internet shortcuts disguised as a JPEG image that, when selected by the user, allows the threat actor to exploit CVE-2024-21412. The group can then bypass Microsoft Defender SmartScreen and fully compromise the Windows host as part of its attack chain.
A detailed technical analysis of this campaign can be found in our blog entry: CVE-2024-21412: Water Hydra Targets Traders With Microsoft Defender SmartScreen Zero-Day.
Users affected by CVE-2024-21412
CVE-2024-21412 involves Microsoft Defender SmartScreen, a feature that is part of both Windows 10 and 11 (the currently supported Windows client versions). Originally introduced in Windows 8, SmartScreen is an integrated Windows feature designed to warn users if they are accessing a malicious URL or file. As we noted earlier, all currently supported Windows client versions are affected by this vulnerability.
Trend protections against CVE-2024-21412
Aside from the official patch released by Microsoft, Trend customers have been protected from CVE-2024-21412 since January 17 via virtual patching. The complete list of Trend solutions can be found in our Knowledge Base article, which can be accessed via this link.
While many organizations will be scrambling to engage emergency operations to test and deploy the official Microsoft patch, Trend customers do not need to make any changes to their usual patch cadence since they are already protected. Furthermore, in most cases, applying patches usually requires reboots; this is in contrast to using a virtual patch, which doesn’t need a system restart.
The potential impact of a successful CVE-2024-21412 exploitation
Water Hydra uses social engineering to lure victims into selecting malicious links that eventually lead to the exploitation of CVE-2024-21412, allowing the attackers to compromise their victim’s host system and deploy malicious payloads. Water Hydra has been known to be financially motivated, but other threat actors with different motivations can also exploit the vulnerability for their own purposes, such as cyberespionage or sabotage.
In general, the exploitation of vulnerabilities — especially zero-day ones — can pose significant risks to organizations. A data breach is one such risk, wherein threat actors can infiltrate systems, exfiltrate sensitive data, and compromise the confidentiality of critical information. The fallout from data breaches can result in substantial financial losses due to regulatory fines, legal fees, and damage to reputation, among others. Zero-day attacks can also disrupt business operations, leading to downtime, productivity loss, and customer dissatisfaction.
The importance of a proactive research approach
Aside from the available Trend protections for customers, Trend’s proactive approach to identifying emerging tools, tactics, procedures (TTPs), and trends used by threat actors, such as the research on CVE-2024-21412 and the Water Hydra campaigns that were exploiting this vulnerability, can allow organizations to anticipate potential threats and develop proactive defenses.
Finding and fixing zero-days through an agnostic bug bounty program
A bug bounty program allows Trend to identify security vulnerabilities quickly and in turn provide fixes before an attacker can exploit them. These kinds of programs also have access to a higher number of testers and bug hunters, thereby both increasing the chances of finding more vulnerabilities and synergistically leading to the development of customer protections against these vulnerabilities. Our ZDI program has been instrumental in the discovery of numerous bugs over the years and will continue to provide responsible reporting of zero-day vulnerabilities.
In 2023, ZDI provided virtual patches on an average basis of 51 days ahead of Microsoft-sourced vulnerabilities and 96 days ahead of vendor patches for bugs sourced by ZDI.
Conclusion
Given the potential impact of a successful zero-day vulnerability exploitation, it is important that chief information security officers (CISOs) and other decision-makers are able to adopt a multilayered approach to prepare for and address the risks of zero-day vulnerabilities. We recommend that organizations implement best practices in the following areas:
- Vulnerability management. Implement robust vulnerability management processes to continuously identify, prioritize, and remediate vulnerabilities across the entire IT infrastructure.
- Threat intelligence. Monitor threat intelligence feeds and platforms to stay abreast of emerging threats, including zero-day vulnerabilities, and proactively adjust security measures accordingly.
- Patch management. Establish rigorous patch management procedures to ensure timely deployment of security patches and updates from vendors, minimizing the window of exposure to zero-day vulnerabilities.
- Incident response. Develop and regularly test incident response plans to enable swift and effective response to zero-day attacks, including containment, eradication, and recovery efforts.