Organizations can improve their AWS infrastructure security management by streamlining multiple security dashboards and tools. The integration between Trend Vision One and AWS Security Hub CSPM helps address this, bringing all critical information together in one place and allowing you to respond to security findings in real-time, without wasting time navigating between systems.
Trend Vision One is Trend Micro's unified cybersecurity platform, while AWS Security Hub is a unified cloud security solution at AWS. When integrated, they create a consolidated view of all security findings, enabling your team to detect and respond to events much faster and more efficiently.
To simplify implementation, Trend Micro offers an open-source project on GitHub (v1-server-and-workload-integration-with-aws-securityhub), making it easier for organizations to leverage these benefits.
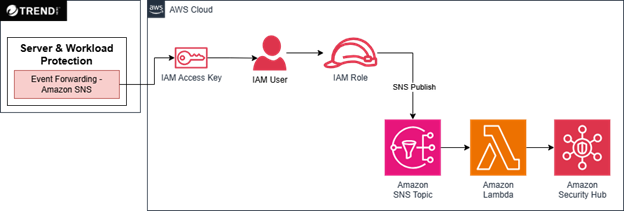
1.How the Integration Works
1.1 Understanding the Components
Before diving into implementation, it's important to understand the main components involved:
Trend Vision One™ Server and Workload Security (SWP): This is Trend Micro's solution for protecting your cloud servers. It offers comprehensive protection against malware, network attacks, vulnerabilities, and much more. Think of it as an intelligent bodyguard for your Amazon EC2 instances and other AWS workloads.
AWS Security Hub CSPM: This is a unified cloud security solution at AWS. It brings together alerts from various AWS services (such as Amazon GuardDuty , Amazon Inspector , Amazon Macie ) and partner solutions (like Trend Micro) in one place. It's like having a "news feed" dedicated exclusively to your infrastructure's security.
The Open-Source Project: Trend Micro created and made freely available on GitHub all the code necessary to connect these two platforms. This includes automated scripts, configuration templates, and detailed documentation - everything ready for you to use and adapt to your needs.
1.2 The Information Flow
From Trend Vision One to AWS Security Hub CSPM: When Vision One detects something suspicious - whether it's malware, an unauthorized access attempt, or a critical security finding, it automatically sends this information to Security Hub CSPM. All important details are preserved: severity level, threat type, affected resources, and remediation recommendations.
2. Putting the Integration into Practice
2.1 What You Need Before Starting
You don’t need to be an expert to implement this integration, but a few prerequisites are essential:
On the Trend Micro side:
- An active Trend Vision One account with Server and Workload Protection functionality enabled
On the AWS side:
- Basic knowledge of how the AWS console works
- Adequate permissions in your AWS account to create resources
- AWS Security Hub CSPM activated in your region
Useful tools:
- AWS Command Line Interface (AWS CLI)
- Git to download the GitHub project
- A bit of patience and willingness to learn!
2.2 Implementing the Integration in 5 Steps
Setting up this integration is straightforward and can be completed in just a few hours. Follow these five steps:
Step 1: Activate AWS Security Hub CSPM Access the AWS console, enable Security Hub in your region. Estimated time: 5 minutes.
Step 2: Execute the Permissions Template Trend Micro provides a ready-made AWS CloudFormation emplate that automatically creates all necessary resources, the integration data are in Output parameters. Execute it and wait for completion. Estimated time: 5 minutes.
Step 3: Configure the Integration in Server & Workload Protection in the Vision One Console, go to Endpoint Security > Server & Workload Protection, select the tenant you want to integrate, go to Administration > System Settings > Event Forwarding.
Enable the option “Publish Events to Amazon Simple Notification Service” and copy and paste the parameters saved in the Secret Manager for integration you have from the preview step. Estimated time: 5 minutes.
Step 4: Validate Functionality. Verify that Vision One alerts appear in Security Hub CSPM. A simple test: locate a recent alert in Vision One and confirm it's visible in Security Hub CSPM. Estimated time: 5 minutes.
Step 5: Optimize as Needed Adjust filters to display only relevant alerts and configure notifications for your team. Estimated time: 30 minutes to 1 hour.
Total Implementation Time: 1 to 2 hours
2.3 Critical Success Factors
Start Small, Scale Fast Implement first in a test environment or in a single AWS account. Validate the results in 1-2 weeks, then expand to production. This approach reduces risks and enables rapid learning.
Ensure Team Alignment This is an initiative that crosses organizational silos. Make sure that:
- The Security team has defined which alerts are priority
- The Cloud/DevOps team is available for technical implementation
- Leadership has approved the necessary resources
Establish Success Metrics Define clear indicators from the start:
- Reduction in detection and response time (goal: reduce by 50-70%)
- Rate of missed alerts (goal: zero critical alerts not viewed)
- Operational efficiency (goal: reduce investigation time by 40%)
Focus on what brings immediate value. The basic configuration already solves most challenges. Evolve the solution incrementally, always anchored in real business needs.
Plan for Sustainability
- Owner: Designate an owner for the integration
- Review: Schedule quarterly reviews of filters and configurations
- Updates: Monitor updates to the GitHub project and official documentation
- Documentation: Maintain an updated runbook for troubleshooting
Expected ROI:Organizations that implemented this integration report, as per customer feedback
- 60-70% reduction in average incident response time
- 50% reduction in time spent switching between tools
- 100% consolidated visibility of security events
- Simplified compliance with faster audits
The operational efficiency gained and the reduction in risk exposure quickly compensate for the implementation effort.
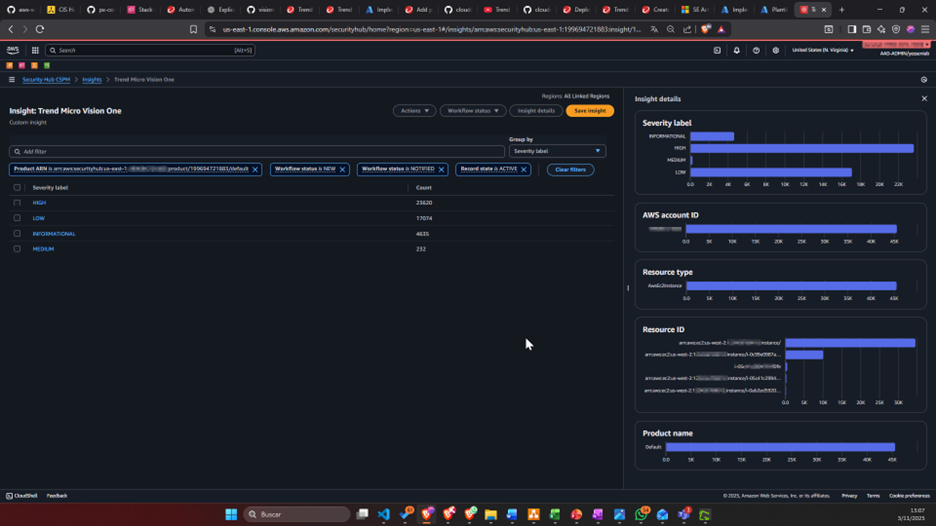
3. Real-World Use Cases
3.1 Unified Security View
Situation: Your company has 50 EC2 instances distributed across multiple AWS accounts. You use Vision One for malware protection, GuardDuty to detect suspicious behavior, and Inspector to find vulnerabilities.
The Problem Before: Your security team needed to check three different dashboards, multiple times a day, to get a complete picture of the situation.
The Solution with Integration: Now, everything appears in one place - AWS Security Hub CSPM. When Vision One detects malware on an EC2 instance, the alert appears alongside GuardDuty and Inspector notifications. Your team has a complete view and can prioritize what's most critical.
Practical Example: Imagine that at 10:30 AM, Vision One detects a trojan on an instance. The alert appears immediately in Security Hub CSPM with all relevant information:
- Which instance was affected
- What type of malware was found
- The severity level (High, Medium, Low)
- Recommendations on how to resolve the problem
3.2 Automated Threat Response
Scenario: Amazon Inspector discovers a critical vulnerability in one of your EC2 instances - a serious security flaw that could be exploited by attackers.
The Automated Flow:
- Detection: Inspector identifies the vulnerability and sends the alert to Security Hub CSPM
- Analysis: The integration verifies if the instance has the Vision One agent installed
- Notification: Your team receives an alert informing that protection has been applied and that definitive remediation should be scheduled
The Benefit: You gain precious time. Instead of being vulnerable for hours or days, protection is applied in seconds, reducing the exposure window.
3.3 Simplified Compliance and Auditing
For companies that need to demonstrate compliance with regulations such as PCI DSS, LGPD, or GDPR, the integration offers significant advantages:
- Complete Traceability: All security events are recorded in a single place, with precise timestamps and detailed information. When an auditor asks, "What happened on day X?", you have all the answers in a consolidated report.
- Evidence of Continuous Protection: The integration automatically documents that you have active 24/7 monitoring, that security findings are responded to quickly, and that vulnerabilities are treated systematically.
- Ready-Made Reports: Security Hub CSPM offers compliance dashboards that come pre-configured with major security frameworks. With the integration, Vision One data automatically feeds these reports.
4. Expanding to Complex Environments
4.1 Multiple AWS Accounts and Regions
Many organizations manage several AWS accounts, typically separating environments such as production, development, and testing. They also operate across multiple geographic regions to improve performance, ensure compliance, and enhance resilience.
The Hub-and-Spoke Architecture: Think of this as a radial network system, where there's a central account (the "hub") and several connected accounts (the "spokes"):
- Main Account (Hub): Receives all security alerts from all other accounts
- Secondary Accounts (Spokes): Send their alerts to the main account
- Vision One: Connects to the main account, obtaining complete visibility of everything
Practical Benefit: Your security analyst doesn't need to log into 10 different accounts. They access a single dashboard and see everything happening across the entire organization.
4.2 Intelligent Alert Filtering
Not every alert needs to be visible in every system or dashboard. This integration enables you to define intelligent filtering rules so that alerts are routed where they matter most. Example Rules:
- By Severity: "Only send alerts of Medium severity or higher to Security Hub CSPM"
- By Environment: "Alerts from development environments don't need to appear on the main dashboard"
- By Type: "Network scan attempts are expected in test environments, don't generate alerts"
The Code Allows Customization: Since the project is open source, you can adapt the filtering logic to your specific needs. For example, you can add rules based on:
- Time (alerts outside business hours can have different treatment)
- Resource tags (instances marked as "critical" always generate alerts)
- History (if the same threat appeared 5 times and was always a false positive, stop alerting)
4.3 Monitoring the Integration Itself
Monitoring your applications is important, but monitoring the integration itself is just as critical. You need to ensure alerts are flowing correctly.Amazon CloudWatch - Your Observatory: Amazon CloudWatch allows you to create visualizations and alerts about the integration itself:
- How many alerts were sent today?
- Are any errors occurring?
- Is response time within expectations?
Monitoring Example: You can configure to receive a notification if:
- No alerts from Vision One reach Security Hub CSPM for more than 1 hour (may indicate the integration stopped working)
- Error rate exceeds 5% (something is wrong with communication)
- Processing time exceeds 30 seconds (there may be slowness)
5. Practical Tips and Lessons Learned
5.1 Start Small, Expand Gradually
Recommendation: Don't try to implement everything at once across all accounts. Start with a pilot project:
- Week 1: Configure the integration in a test account with few instances
- Week 2-3: Observe behavior, adjust filters, familiarize your team
- Week 4: Expand to less critical production environments
- Month 2: Complete rollout to the entire organization
Benefit: You learn from mistakes in a controlled environment, avoiding production impacts.
5.2 Document Your Customizations
The GitHub project is an excellent starting point, but you'll inevitably make adjustments for your reality:
Keep a Record:
- What filters you added and why
- Which alerts were configured differently from the standard
- Changes to permissions and roles
- Custom automated response logic
Why This Matters: When someone new joins the team, or when you need to replicate the configuration in another region, having this documentation saves hours of work.
5.3 Security First
It may seem ironic, but when implementing a security solution, you need to ensure the solution itself is secure!
Credential Protection: Never, under any circumstances, leave your API keys visible in code or configuration files. Use AWS Secrets Manager to store them securely. Think of it as keeping your house keys in a safe, not under the doormat.
Regular Rotation: Just as you periodically change your email password, do the same with API keys. Configure automatic rotation every 90 days. AWS Secrets Manager can do this automatically for you.
Principle of Least Privilege: The AWS Lambda functions that perform the integration should have only the strictly necessary permissions. It's like giving the pizza delivery person only the gate key, not the keys to every room in the house.
5.4 Test Before Trusting
Regular Simulations: Periodically conduct tests to ensure the integration is working:
- Detection Test: Use the EICAR test file (a harmless "virus" used for testing) to verify if malware alerts reach Security Hub CSPM
- Latency Test: Measure how long it takes from detection until the alert appears on the dashboard
- Failover Test: Simulate a failure and see how the system behaves
Alert Validation: In the first months, manually review a sample of alerts to ensure that:
- Severity levels are correct
- Information is complete
- There aren't excessive false positives
5.5 Empower Your Team
The best technology in the world is useless if your team doesn't know how to use it properly:
Initial Training:
- Show where to find Vision One alerts in Security Hub CSPM
- Explain how to interpret each type of alert
- Demonstrate the incident response workflow
Internal Documentation: Create a simple guide with common scenarios:
- "What to do when a malware alert appears?"
- "How to investigate an unauthorized access attempt?"
- "When to escalate to the senior security team?"
Culture of Continuous Improvement: Encourage the team to suggest improvements. Those who use the tool every day have valuable insights on how to make it more efficient.
6. Measurable Benefits of the Integration
After implementing the integration, you'll see concrete results:
6.1 Reduction in Response Time
Before: An alert could take hours to be noticed, investigated, and responded to, as it was "lost" among various tools.
After: With everything consolidated, the average response time can drop from hours to minutes. Organizations report reductions of up to 70% in the time between detection and containment.
6.2 Decrease in Missed Alerts
The Alert Fatigue Problem: When your team needs to check multiple systems, some alerts inevitably go unnoticed.
The Solution: With the unified view, the probability of a critical alert going unnoticed is practically zero. Everything is in one place, prioritized by importance.
6.3 Resource Savings
Fewer Tools, More Efficiency:
- Reduction in the number of dashboards that need to be monitored
- Less time spent switching between systems
- Security team can focus on analysis and response, not on searching for information
Measurable ROI: If an analyst saves 2 hours per day by not needing to search for information in multiple places, that's 40 hours per month. Multiply this by the size of your team and you'll see the real value.
Conclusion
The integration between Trend Vision One and AWS Security Hub CSPM represents a significant step in modernizing cloud security. By unifying alerts, automating responses, and providing complete visibility, it transforms the way security teams operate.
The open-source project made available by Trend Micro on GitHub democratizes access to this technology, allowing organizations of all sizes to implement an enterprise-level solution without additional licensing costs.
Key Takeaways:
- Unified Visibility: All security alerts in a single dashboard
- Automated Response: Protection applied in seconds, not hours
- Simplified Compliance: Evidence and reports consolidated automatically
- Accessible Implementation: Open-source project with all infrastructure ready
- Scalability: Works equally well for 10 or 10,000 instances
Next Steps:
If you're considering implementing this integration, start by exploring the GitHub repository. Read the documentation, test in a controlled environment, and adapt to your specific needs. The community is active, and Trend Micro keeps the project regularly updated.
Remember: effective security isn't about having dozens of tools but about having the right tools working in harmony. The integration between Trend Vision One and Security Hub CSPM is exactly that, two powerful platforms enhancing each other to keep your AWS infrastructure protected.
Additional Resources:
- Project GitHub: https://github.com/trendmicro/v1-server-and-workload-integration-with-aws-securityhub
- Vision One Documentation: Available on the Trend Micro portal
- AWS Security Hub CSPM: Official AWS documentation
- Community: Forums and discussion groups to exchange experiences
Cloud security is a continuous journey, not a destination. This integration is a powerful tool to make that journey more efficient, effective, and, above all, more secure.

