Mind the (Security) Gaps: The 1H 2015 Mobile Threat Landscape
The mobile landscape in the first half of 2015 is highlighted by vulnerabilities found on the operating systems and apps, including ones that came with the devices themselves. A number of notable incidents and cases over the last few months have shown how these vulnerabilities were used as avenues for exploitation. Adware and potentially unwanted apps (PUA) also remain constant threats that expose millions of users to dangers from malicious ads and apps that collect information.
Here are some of the most notable mobile threat stories from the first half of 2015.
MDash-laced apps highlight the perils of online ads
Unwanted online advertisements are not only a nuisance, as they also be used to deliver malware onto mobile devices.
Last February, there were reports of disguised apps that were taken down by Google Play, after it was found that apps laced with ad software development kit (SDK) MDash reportedly infected millions of devices with malware. Detected by Trend Micro as ANDROIDOS_ADMDASH.HRX, the malware family that includes this SDK has the capability to make calls in the background and collect information without the user’s consent, which is then send to a remote server. It then pushes more harmful ads similar to the ones already installed on the device.
 Sample app with MDash SDK
Sample app with MDash SDK
During our investigation, 2,377 app SHA-256 hashes were found on Google Play as of last March 11. Google also immediately investigated the said issue after being notified by researchers.
 Malicious iOS apps used in Operation Pawn Storm
Malicious iOS apps used in Operation Pawn Storm
The use of mobile devices as an entry point for a targeted attack is no longer new. The trend can be attributed to bring your own device (BYOD) and consumerization practices employed by enterprises and large organizations, which come with benefits that can improve productivity and lower costs. Unfortunately, it can also present a number of risks. During this period, we saw a targeted attack campaign that used iOS malware to infiltrate their targets’ networks for espionage purposes.
Operation Pawn Storm is an cyber-espionage campaign that has been known to target government entities such as the White House and member countries of NATO, as well as Ukrainian media and government, among others. Its technique of incorporating iOS malware, detected by Trend Micro as IOS_XAGENT.A and IOS_XAGENT.B, proved that highly specific configurations and operating systems do not necessarily stop threat actors from targeting it.
[Read: Targeted Attack Campaigns and Trends: 2014 Annual Report]
XAgent (IOS_XAGENT.A) gathers information such as text messages, contact lists, pictures, and list of installed apps among others. “Madcap” (IOS_XAGENT.B), which can only be installed on jailbroken devices, is capable of recording audio.
Android ransomware and the Chinese cybercriminal underground
Several young Chinese cybercriminals caused a surge in mobile ransomware in the Chinese underground market after finding widely distributed malware code that they used to make it their own. This indicated how the mechanism at work in the underground cybercrime fuels the proliferation of such threats. In this case, these young cybercriminals (aged 16-21), easily created more than a thousand variants of the Android ransomware detected by Trend Micro as ANDROIDOS_JIANMO.HAT.
Mobile vulnerabilities on the rise
Apart from the growing number of mobile threats, vulnerabilities in apps, operating systems, and devices present another critical security risk to mobile users, the growing number of which provides cybercriminals more avenues to exploit. Here’s a rundown of the period's notable mobile vulnerabilities:
- The open-source malware suite RCSAndroid, which was part of the files that were leaked from the Hacking Team incident, exploits vulnerabilities in the default browsers of Android versions 4.0 Ice Cream Sandwich to 4.3 Jelly Bean. The said malware suite was designed to monitor or spy target victims.
- Trend Micro researchers discovered a slew of vulnerabilities in the Android's mediaserver component that could allow denial of service attacks, cause it to undergo an endless loop of reboots, or cause the device to become totally non-responsive. Moreover, the Stagefright vulnerability, also found in mediaserver, can be exploited to allow the installation of malware via MMS.
- The Swiftkey vulnerability found in Samsung Android devices could allow execution of malicious code on the affected devices to enable man-in-the-middle attacks.
- Apache Cordova vulnerability that resides in the Apache app framework is discovered by Trend Micro researchers. When exploited successfully, it could be used by attackers to change the behavior of apps via clicking a URL.
Mobile threats show steady increase
Despite security vendors’ efforts and security measures that Google put in app permissions, the number of Android threats continuously went up over the first half of 2015. The steady increase in the Android OS market share (78% in Q1 2015) could easily be one of the main reasons for the proliferation of threats. The sheer number of Android devices and users has made the OS a favorable target for cybercriminals and attackers.
Here are some of the most noteworthy numbers that show the Android operating system's market size. (click on image to expand)
As mentioned in the Trend Micro 1H 2014 report, the problem of mobile malware is expected to grow bigger. During our monitoring of the mobile threat landscape, we observed that from last year’s 4.26M, the volume of malware spiked to 7.10M in 1H 2015.
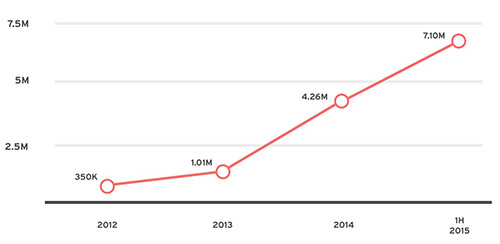
Year-on-year Android malware growth
Interestingly, the data also shows that in 2Q 2015, potentially unwanted applications (PUA) made up half of all mobile malware detected over the period, while 27% of the mobile threats came from adware. While PUAs are not malicious per se, it could be used to deploy harmful ads, or leveraged later for other malicious purposes.
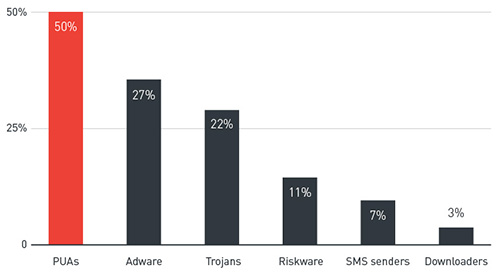
Top Android threat types seen in 2Q 2015
Threats like adware and mobile banking malware come in the form of repackaged apps. While these apps may not necessarily be malicious, they also pose serious risks as they can be used for a number of malicious schemes. Mobile banking malware that steals banking credentials may arrive as trojanized apps, tricking users into thinking that it’s a legitimate app. Based on the data from the Trend Micro Mobile App Reputation Service (MARS), for every 2 online banking apps, there is one malicious or PUA fake bank app.
[READ: How a South Korean group used fake banking apps to steal mobile banking credentials]
Countermeasures and Recommendations
Google has announced that it will release monthly updates in order to address vulnerabilities that can be exploited by both threat actors and cybercriminals. While this can address risks from vulnerabilities, device manufacturers and app developers should also do their share in protecting their devices or making sure that the apps created cannot be exploited to include malicious code. Apart from the risk of malware infection, users should also be more vigilant as information theft is another possible consequence of lax user habits and using outdated software.
Users can also take note of these security measures and best practices to avoid mobile threats on their devices:
- Update Android devices to the latest versions to arm devices against vulnerabilities and exploits
- Avoid app installations from unknown third party sources
- Use a mobile security solution that can detect against exploits and malicious apps
Trend Micro Mobile Security (for iOS and Android) features antivirus and web reputation technologies that can detect mobile malware as well as blocks malicious apps and URLs commonly used by vulnerabilities and exploits. One of its components is the Trend Micro Mobile Application Reputation Service that allows IT to block the use of risky mobile apps based from its real time data.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One