Phishing Emails Sidestep Microsoft Office 365 Filters Using ZeroFont
An old tactic is being used by cybercriminals to bypass Microsoft Office 365 (O365) filters for phishing emails. The technique, called ZeroFont, involves the manipulation of text font sizes to trick O365’s natural language processing, a tool that identifies malicious emails by checking for text elements commonly used by fraudsters.
According to Avanan, the cloud security company that spotted the use of ZeroFont in phishing attacks, cybercriminals send emails that contain text seen differently by the recipient and by the O365 filters. Random text characters or words were added throughout the email, thus preventing the filters from flagging suspicious words or phrases. These were ![]()
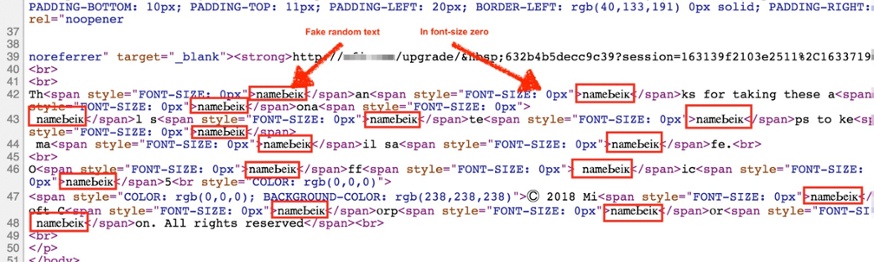
Figure 1. ZeroFont characters in the HTML of a sample email (Image source:
ZeroFont is then able to sidestep O365’s natural language processing, which flags emails that, for example, contain words like “Apple” or “Microsoft” but were not sent from legitimate corporate domains. In one sample analyzed, which was a phishing email under the guise of an O365 quota limit notification, the email was not flagged by O365 filters because the word “Microsoft” was not read amidst the random character strings.
Protect Your Network From ZeroFont
Phishing schemes and methods like ZeroFont are not new in the email threat landscape. ZeroFont
The artificial intelligence- and machine learning-powered Trend Micro™ Cloud App Security™ solution, an advanced security product that protects Microsoft® Office 365™ Exchange™ Online, OneDrive® for Business, and SharePoint® Online platforms, managed to block 3.4 million high-risk email threats in 2017 — apart from the threat scans of O365 using its own built-in security.
Cloud App Security, as well as the Trend Micro™ ScanMail™ Suite for Microsoft® Exchange™ solution, features Writing Style DNA, a new AI technology that formulates the “DNA” of a legitimate email user’s writing style based on past written emails and
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One